Center of Excellence Column: Investigating Fake Profiles with OSINT

This week, in our Center of Excellence Column, we’re revealing threat actors who hide behind phony social media accounts with OSINT techniques. To demonstrate the use in practice, we share a real case study involving a scammer conducted entirely in our standalone OSINT solution, SL Crimewall.
So, let’s go to the investigation!
Our case starts with the social media account of Adrian Smith, a suspected X (formerly Twitter) scammer. According to the available data, Adrian has used his social channels to promote the sale of stolen information. Based on the nature of his activities, there’s a strong chance that the initial profile is fake. Hence, our primary goal is straightforward:
First thing, we checked the suspect’s social media profile, and unsurprisingly, it was closed. Typically, this would be a considerable obstacle for many people. But luckily, OSINT techniques help overcome such hurdles.
Even if a profile is private, we can access three crucial pieces of information—a name, an alias, and a photo. Immediately, something caught our attention: the name displayed on the account was Adrian Smith; however, the alias was p.rothman.
Our next step involved using Adrian’s name and photo to search through social media platforms. For this, used the [Twitter] Search by Face and Name from Search Object transform to handle the process efficiently. This method used the profile picture we extracted from the private account as input.
Facial recognition gave us a second closed account registered to Adrian Smith. At this point, the connection between Adrian and p.rothman became very intriguing. Luckily, our search gave us many leads to expand our inquiry.
Next, we focused on the photos from the second Adrian Smith profile we found. To expand our search, we used the Get Photos Tagged In method and extracted all the pictures the suspect was tagged in.
The results were quite surprising. We got a new face with a tag, leading to a new account— Peter Rothman. It looked like we identified the alias p.rothman we found initially. So, at this point, we needed to verify if the suspect’s name was Adrian or Peter.
To dig deeper, we focused on the tagged Peter Rothman account from the previous step. We ran another round of facial recognition with the [Twitter] Search by Face and Name from Search Object transform. Without it, linking the profiles would be incredibly difficult.
The results showed that Peter Rothman was indeed a real person. In a twist, however, the photos on Adrian’s and Peter’s accounts showed the same individual, but the pictures differed. With this information, we were ready to finalize the investigation.
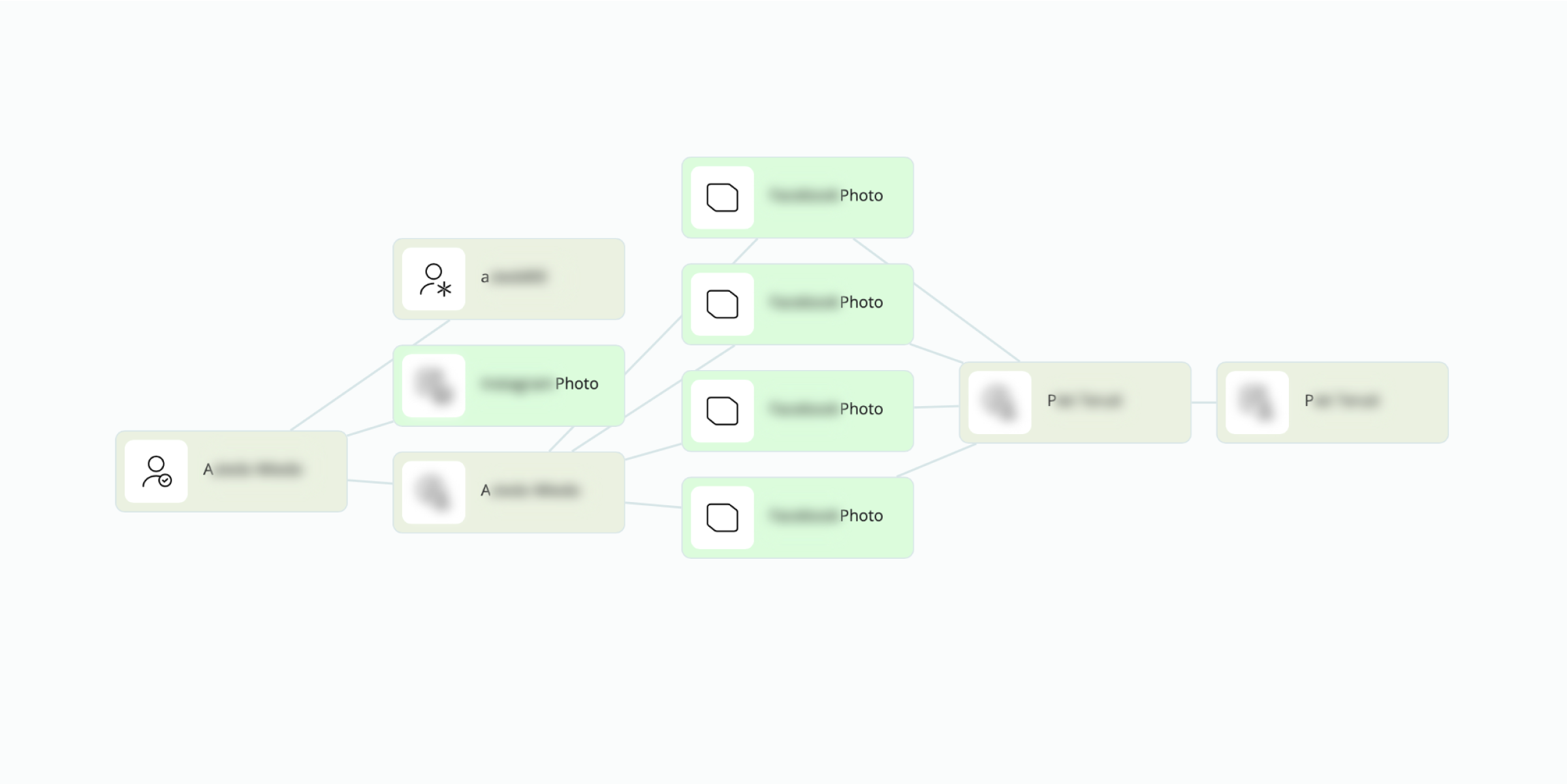
For our final step, we put everything together—information from the first two accounts registered to Adrian Smith and the third profile, which belonged to Peter Rothman, along with the photos. Then, we used our final transform: [SL ISE] Search Person, which helps uncover associated online accounts, aliases, and more.
So, after the Internet-wide search for our suspect, we finally had concrete evidence that Adrian Smith was a fake identity used by Peter Rothman. In addition, SL ISE gave us two phone numbers registered in Peter’s name.

So, a quick recap:
Our investigation allowed us to deanonymize a social media scammer using OSINT tools to analyze his fake profiles. Following Peter's breadcrumb trail throughout his accounts, we uncovered two phone numbers he owned and verified his real name.