OSINT in Brand Intelligence: Safeguarding Company Value

In an era when personal data is pouring into platform upon platform, all employees of an enterprise are ultimately part of a company’s image or brand. If a company executive, for example, makes an unwise post, the consequences can be far-reaching and even lead to a stock value drop-off. Here’s looking at you, Elon.
And this is just one issue among many. With data spilling out from everywhere and threat actors at large, it’s not easy to safeguard an organization against reputational—and, in turn, financial—loss. So today, we’re taking a look at the role of OSINT in brand intelligence, from the various brand-related challenges that companies face to the solutions open data can provide.
Let’s get into it!
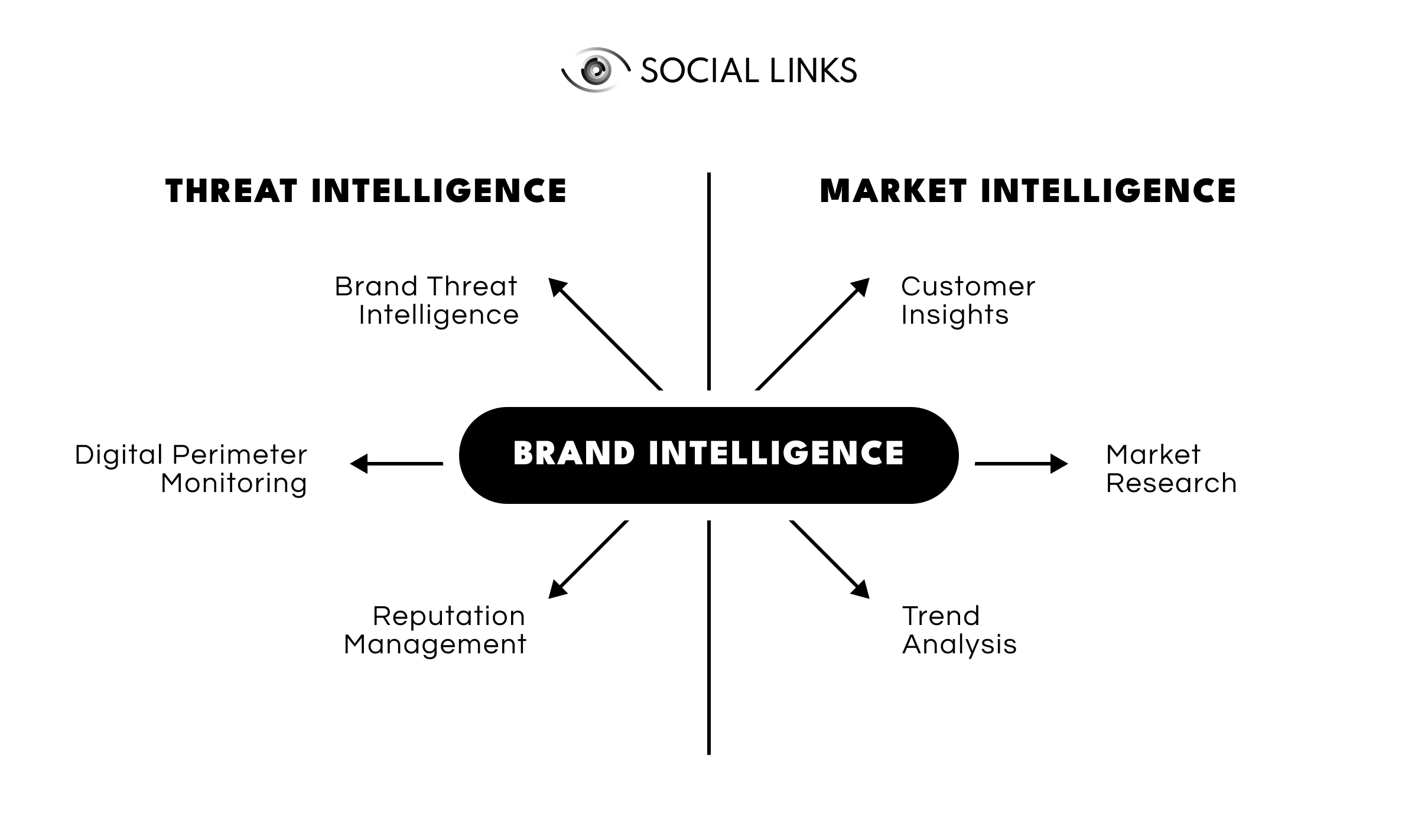
So, first things first, let’s define brand intelligence. Google the term, and you may come away with the idea that it’s solely about gathering data to protect a company's image from cyber threats. And while this is definitely a big part of it, it’s not the whole picture. As a type of threat intelligence, it may also cover undesirable information that has slipped out inadvertently instead of through some malicious actor.
At the same time, brand intelligence may be used in ways that don’t concern threats at all but rather tie into market and business intelligence more than threat intelligence. So, what is brand intelligence? In a nutshell, it’s collecting and analyzing data taken from all digital platforms to identify risks or public attitudes relating to the company brand, and inform protection measures or marketing approaches.
To make all of this less abstract, here are some disciplines that fall under the brand intelligence umbrella:
Brand Threat Intelligence. A brand's dangers in the big bad digital world are legion (more on these later), ranging from spoofed domain attacks and phishing schemes to data leaks and impersonation fraud. By scanning the entire digital environment, security teams can promptly weed out such dangers to greatly mitigate potential losses.
Digital Perimeter Monitoring. While malicious actors certainly pose significant threats to the brand, so may an organization's personnel. With so many people interfacing with the digital world, sensitive data can emerge unintentionally or through social engineering. Alternatively, the actions or posts of company representatives may impact the company's image. By continually monitoring online surfaces, security officers can quickly identify and fix—or even prevent—instances of inadvertent data spillage or image detraction.
Reputation Management. An organization’s name is a priceless asset. Customer opinions hold a significant influence on the company's profitability. Effective reputation management involves actively addressing customer feedback and concerns through relevant apps or platforms or indirectly by monitoring what people are saying using SOCMINT (social media intelligence) techniques.
Customer Insights. Identifying unique associations, such as a product linked to a specific holiday, can be a powerful marketing strategy. Savvy teams capitalize on these opportunities with techniques such as sentiment analysis to understand the users, tailor their campaigns, and enhance customer engagement.
Market Research. Understanding the evolving needs and desires of the target demographic is paramount. Thorough market research with NLP (natural language processing) techniques provides ideas and insights that form the foundation of a strategic approach, ensuring alignment with consumer expectations.
Trend Analysis. Anticipating and adapting to industry movements is vital for sustained success. Looking at trends enables companies to align their products, services, and marketing strategies with their audience's current and future preferences.
Gaining a foothold in an industry is never easy. A company often forks a small fortune on brand-building efforts so consumers know who they are. And these costs are on the rise. B2B marketing budgets in the US grew to $3.74B in 2023, up from $3.5B in 2021, and are projected to hit almost $4B in 2025.
With such investment pouring into brands, it should be no surprise that companies are keen to protect what they’ve built. But malicious actors are always waiting in the wings, evolving ever-new techniques to cash in on the current climate or efforts of others—activities that tend to leave a certain amount of wreckage in their wake.
For example, during the pandemic, when public attention had turned to health issues, cybercriminals started to impersonate research centers and government bodies to steal ordinary people’s personal information. Palo Alto Networks said vaccine-related phishing attacks increased by 530% between December 2020 and February 2021.
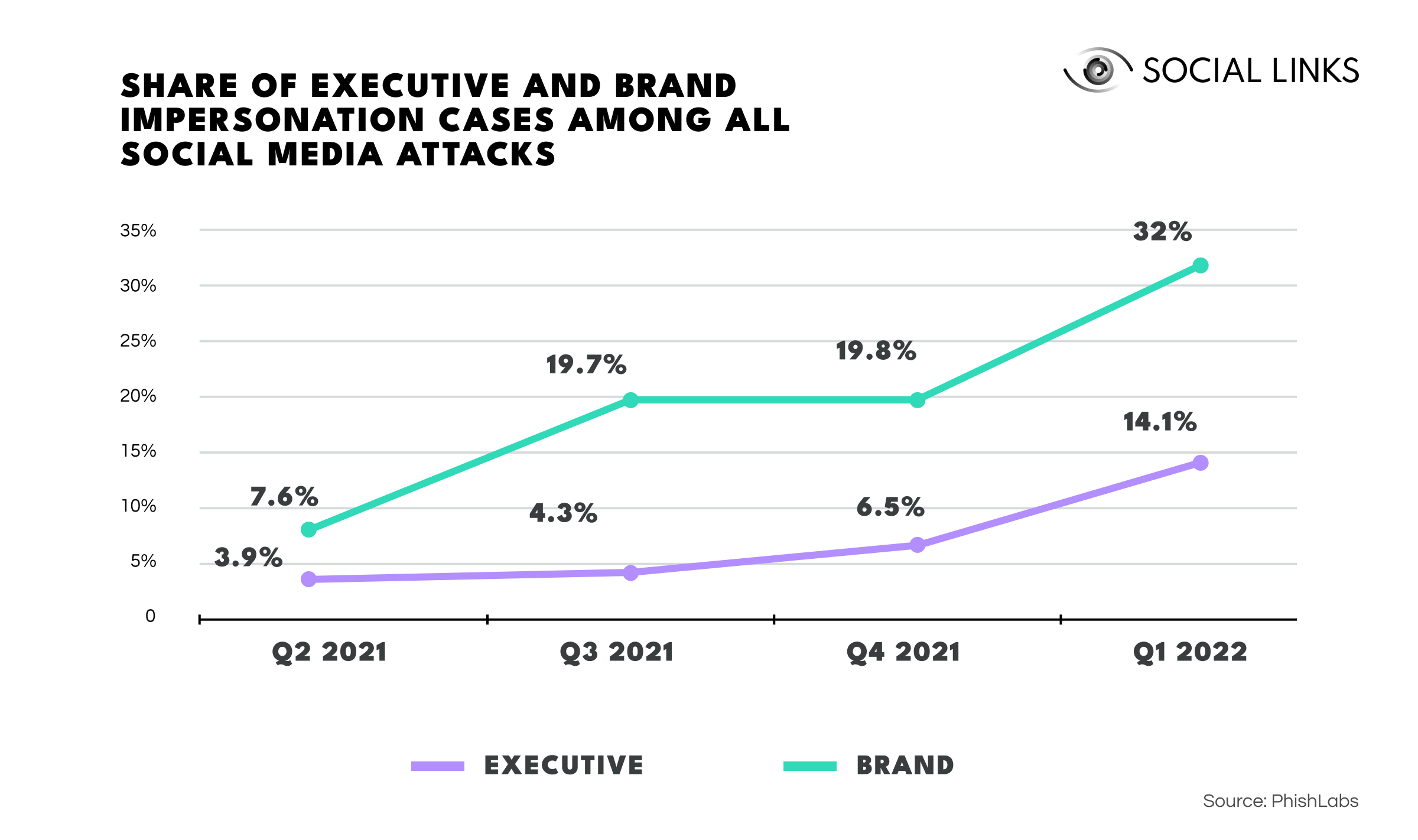
However, with the pandemic in the rearview mirror, threat actors have returned to their old ways. According to a report by PhishLabs, from 2021 to 2022, executive imitation schemes on social media saw a 273% increase, and brand impersonation cases soared by 332%. Such figures reflect a mounting problem that current measures cannot address effectively.
With malicious brand-based attacks spiraling out of control, finding a more efficient way of mitigating or preventing them is crucial. Enter open-source intelligence. Here are some common brand threats and OSINT-based responses that can keep them under control or eliminate them entirely:
Threat: The unauthorized use of a brand’s identity, usually for fraudulent purposes.
Solution: Staple OSINT approaches, such as social media monitoring, are often central to identifying copycat accounts impersonating the brand. AI-driven reverse image search is also a great method for finding misappropriations of the company logo and online discussions negatively misrepresenting the company itself.
Threat: The act of registering, using, or selling a domain to profit from a trademarked brand. Luckily, open-source intelligence provides a way forward in such situations.
Solution: By tracking domain registrations and conducting WHOIS searches, OSINT analysts can identify who owns the offending URL. Moreover, forums and marketplaces can serve as valuable data sources as many threat actors tend to put such websites up for sale.
Threat: The creation of deceptive domains to mimic legitimate websites, often for phishing scams or other fraudulent purposes.
Solution: Investigators can use OSINT techniques to look up domain name variations through WHOIS databases, monitor DNS records for any unauthorized changes, and analyze SSL certificates for inconsistencies with the genuine domain.
Threat: The production of imitation goods to deceive consumers, often with fraudulent intent.
Solution: As such products have to be listed somewhere, specialists can search through e-commerce platforms for unauthorized sellers and find online reviews and discussions about fake products. Furthermore, analyzing social media to promote such sellers can allow investigators to deanonymize malicious actors.
Threat: Pretending to be a high-ranking executive to deceive employees, partners, or customers.
Solution: The role of open-source intelligence in these scenarios is primarily to monitor the fake profiles that the threat actors create. Using SOCMINT techniques such as cross-checking and digital footprinting, investigators can often deanonymize the cyber criminals behind such attacks.
