OSINT in Criminal Investigations: Methodologies and Best Practices


The landscape of criminal investigations has undergone a fundamental transformation over the past 15 years. As criminal enterprises increasingly operate across both physical and cyber-domains, law enforcement agencies must adapt their methodologies to effectively counter these evolving threats and challenges.
In this climate, open-source Intelligence (OSINT) has emerged as a critical discipline for conducting modern criminal investigations. At the same time, the emergence of OSINT as one of the go-to disciplines in investigative work has raised important considerations regarding methodology, legality, and ethics.
This article examines the application of OSINT in law enforcement investigations targeting serious and organized crime, transnational criminal networks, and cybercriminal activities. Drawing from extensive operational experience, we present a comprehensive framework for integrating OSINT into the investigative process, paying particular attention to advanced analytical techniques and technological solutions that enhance investigative outcomes.
Open-source intelligence encompasses data from publicly available sources, such as social media platforms, forums, blogs, news outlets, public records, and corporate registries. For law enforcement agencies confronting sophisticated threats, the deployment of OSINT in criminal investigations represents an invaluable resource that complements traditional investigative methods.
According to the United Nations Office on Drugs and Crime (UNODC), there are four core phases comprising the open-source intelligence process: Identification, Validation, Analysis, and Production.
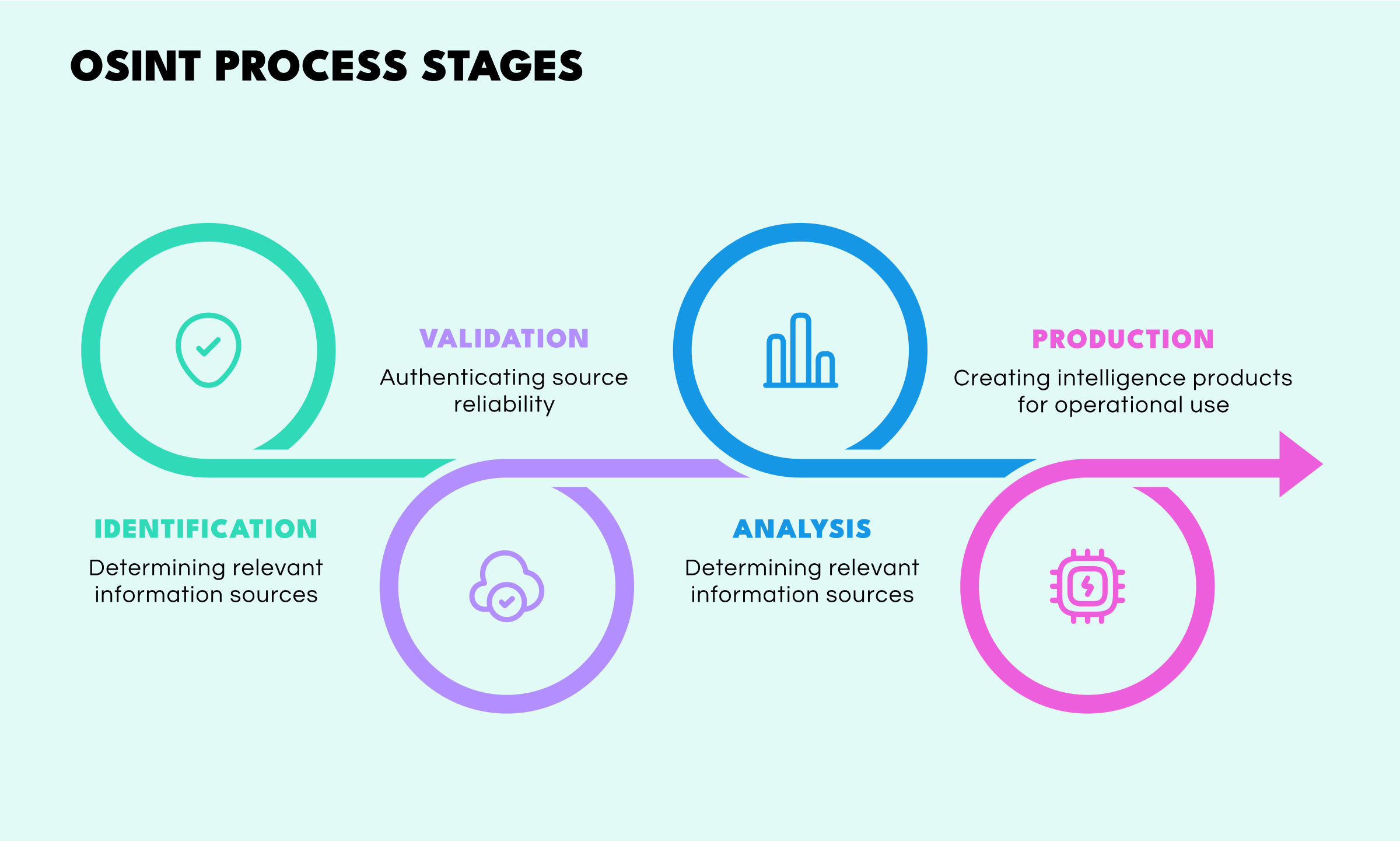
Through the deployment of this systematic approach, disparate open-source data can be structured into coherent information that is further used to produce intelligence, which, in turn, can drive investigative decision-making, especially regarding the investigation of complex criminal networks that operate across multiple jurisdictions.
Organized Crime Groups (OCGs) rely on complex networks of associates, facilitators, and enablers. The adoption of modern OSINT methodologies, particularly Social Network Analysis (SNA), allows investigators to map these relationships with unprecedented precision. By identifying key nodes within criminal networks, law enforcement can prioritize High-Value Targets (HVTs) and "Gatekeepers"—individuals who, if affected, would maximally disrupt criminal operations.
Social Links' SL Crimewall platform exemplifies this very approach, offering advanced data visualization tools that transform fragmentary data points into comprehensive network maps. These informational pictures can often reveal crucial insights that would otherwise remain obscure, such as inter-suspect ties, network hierarchies, and operational patterns.
Research from academic institutions has demonstrated how SNA-focused OSINT can reveal:
To deepen this methodology further and see how network mapping applies beyond criminal analysis, explore our Social Network Analysis guide, which explains how graph modeling reveals hidden structures, hierarchies, and behavioral clusters across digital ecosystems.
While criminal actors are increasingly adopting advanced technological tools to mask their identities, even sophisticated criminals leave "digital exhaust" that, when properly analyzed, can lead to their identification. OSINT provides multiple ways to deanonymize suspects in cybercrime investigations, including:
Such OSINT techniques have proven particularly effective in cybercrime investigations, where suspects cloak their true identities behind pseudonyms. By correlating information across multiple platforms and tapping into the "Human Mistake Factor"—instances where criminals inadvertently reveal identifying information—investigators can link masked threat actors to real-world identities.
To explore a deeper range of unmasking methodologies — from linguistic attribution to cross-platform metadata correlation — you can review our advanced deanonymization techniques for law enforcement and CTI, which showcases how attribution workflows connect anonymous digital personas to real-world identities in cybercrime investigations.
This is a domain where Social Links' products and methodologies excel—allowing users to automatically identify connections between seemingly disparate online personas, thereby revealing the individuals behind criminal activities and shining light into a range of cybercrime investigations.
While social media intelligence is perennially important, to be as effective and comprehensive as possible, OSINT in criminal investigations needs to draw information from a range of domains:
Criminal organizations frequently establish legitimate business fronts to launder proceeds and facilitate operations. By analyzing corporate registries, investigators can:
Social Links' integration with corporate registry databases allows investigators to seamlessly incorporate SOCMINT information into broader network analysis, revealing how criminal enterprises intersect with legitimate business structures.
The proliferation of data breaches has created vast repositories of previously private information. When properly leveraged, this data can provide critical leads in criminal investigations by providing:
Intelligence tools like Social Links' SL Crimewall plus Darknet Pack integrate data leak intelligence within a structured analytical framework, ensuring these sources can be properly authenticated and documented to embody evidence.
Visual content shared across open data sources frequently contains valuable intelligence, including:
Advanced OSINT platforms now incorporate machine learning algorithms that can analyze large volumes of visual data. These not only significantly reduce routine work, saving time and resources—they can also outperform the human eye, flagging up elements that would’ve escaped manual review.
The volume of open-source data relevant to criminal investigations has expanded exponentially, creating both opportunities and challenges for law enforcement. In this climate of proliferating data, artificial intelligence tools are now proving to be force multipliers for open-source intelligence processes, allowing investigators to process and analyze information at scale.
It is crucial to emphasize that AI-driven open-source intelligence represents an investigative support function rather than a form of "AI policing". In this capacity, these systems can:
While these AI capabilities are advanced, they do not replace human agency but rather can enhance professional judgment—the investigator remains the critical decision-maker. Social Links has pioneered this balanced approach, developing AI-assisted intelligence tools that amplify investigative capabilities while keeping trained professionals at the center of the process.
A significant obstacle to the adoption of OSINT in law enforcement has been the so-called "Secrecy Bias"—the received perception that information derived from open sources is inherently less valuable than classified intelligence. This misconception has long limited OSINT's integration into investigative workflows.
Contemporary research has conclusively shown this bias to be unfounded, with the UNODC noting that "open-source information often provides critical contextual understanding and leads that would remain undiscovered through classified channels alone." This is a truth reflected in the operations of forward-thinking law enforcement agencies, where a balanced approach is taken, incorporating both open and classified sources.
Effective open-source intelligence demands specialized knowledge and methodological rigor. Unlike traditional intelligence disciplines with established tradecraft, OSINT is a relatively young field that continues to evolve rapidly. To stay up-to-speed and effective in this shifting landscape, law enforcement agencies must invest in comprehensive training programs that cover:
Social Links' educational resources and training programs have helped agencies develop these capabilities, ensuring that investigators can fully leverage available open-source intelligence tools within appropriate operational frameworks.
As the reach of open-source intelligence expands, law enforcement agencies must navigate increasingly complex legal and ethical terrains in ensuring that operational effectiveness is balanced with respect for privacy, civil liberties, and procedural requirements.
OSINT investigations are naturally constrained by relevant legal frameworks, which vary by jurisdiction but generally address:
Agencies must develop clear policies governing how open-source information is collected, processed, and retained to ensure compliance with relevant laws.
For OSINT to support successful prosecutions, agencies must maintain rigorous documentation and chain of custody procedures. This includes:
Social Links open-source intelligence platforms incorporate robust audit trails and documentation features specifically designed to meet evidentiary requirements across multiple jurisdictions, ensuring that intelligence successfully transitions to evidence as a matter of course.
Beyond legal compliance, agencies must consider the broader ethical implications of OSINT in law enforcement operations, and:
By developing comprehensive ethical frameworks for OSINT operations, agencies can maintain public trust while effectively combatting serious and organized crime.
As the open-source intelligence landscape continues to evolve rapidly, we can see the emergence of trends that are likely to shape the application of OSINT in criminal investigations moving forward:
The integration of text, image, video, and audio analysis within unified analytical frameworks will enhance investigative capabilities. Social Links is pioneering these integrations, developing solutions that can process multiple data types to produce actionable intelligence.
Transnational criminal investigations increasingly require the coordination of OSINT operations across multiple jurisdictions. The standardization of methodologies and information-sharing protocols will facilitate these collaborative efforts, allowing agencies to more effectively combat criminal networks that operate globally.
As disinformation and synthetic media proliferate, rigorous verification procedures become essential to filter out the authentic from the fake. Next-generation OSINT tools will incorporate advanced authentication capabilities to distinguish genuine information from manipulated content.
Open-Source Intelligence has transformed from a supplementary resource to a pillar of modern criminal investigations. For law enforcement agencies confronting serious and organized crime, transnational networks, and cybercriminal threats, OSINT provides critical ways to identify, analyze, and disrupt criminal activities.
By adopting tried-and-tested OSINT methodologies, leveraging advanced analytical tools such as those developed by Social Links, and maintaining appropriate legal and ethical frameworks, agencies can significantly enhance their investigative effectiveness. As criminal enterprises continue to evolve, effective response will increasingly hinge on the deployment of OSINT in law enforcement, whereby more targeted, efficient, and successful criminal investigations can be conducted.
For law enforcement agencies to remain effective moving forward in a shifting landscape, they need to successfully navigate the information environment where criminals operate. And it’s those that develop sophisticated OSINT capabilities today who’ll be best positioned to counter tomorrow's criminal threats.
If you'd like to learn more about Social Links industry-leading solutions and how they can revolutionize a wide range of OSINT processes for criminal investigations, get in touch. Just follow the button below and we can set up a free, personalized demonstration with one of our specialists, and show you first hand the difference our tools can make in your workflows.