OSINT vs Social Media Threats: A Cybersecurity Playbook

Social media has become a double-edged sword. While it connects billions of users worldwide, it also presents a growing risk landscape. Phishing scams, misinformation campaigns, and brand impersonation are just a few of the cyber threats that thrive on social platforms.
Yet the same data that makes social media a prime target for attackers also represents a valuable resource for those who wish to safeguard themselves against its attendant threats. And so in this article, we're looking at how OSINT is essential for two stalwart strategies of effective response in the context of social media—Cyber Threat Intelligence (CTI) and Digital Risk Protection (DRP).
Amid the birthday wishes and trending memes, it may not be obvious to all that social media has in fact become a lucrative hunting ground for cybercriminals. With over 5.24 billion users worldwide, each juggling an average of 6 to 7 platforms, the global digital attack surface has exploded. From phishing scams and fake profiles to deepfake videos and misinformation campaigns, the threats have grown in both scale and complexity.
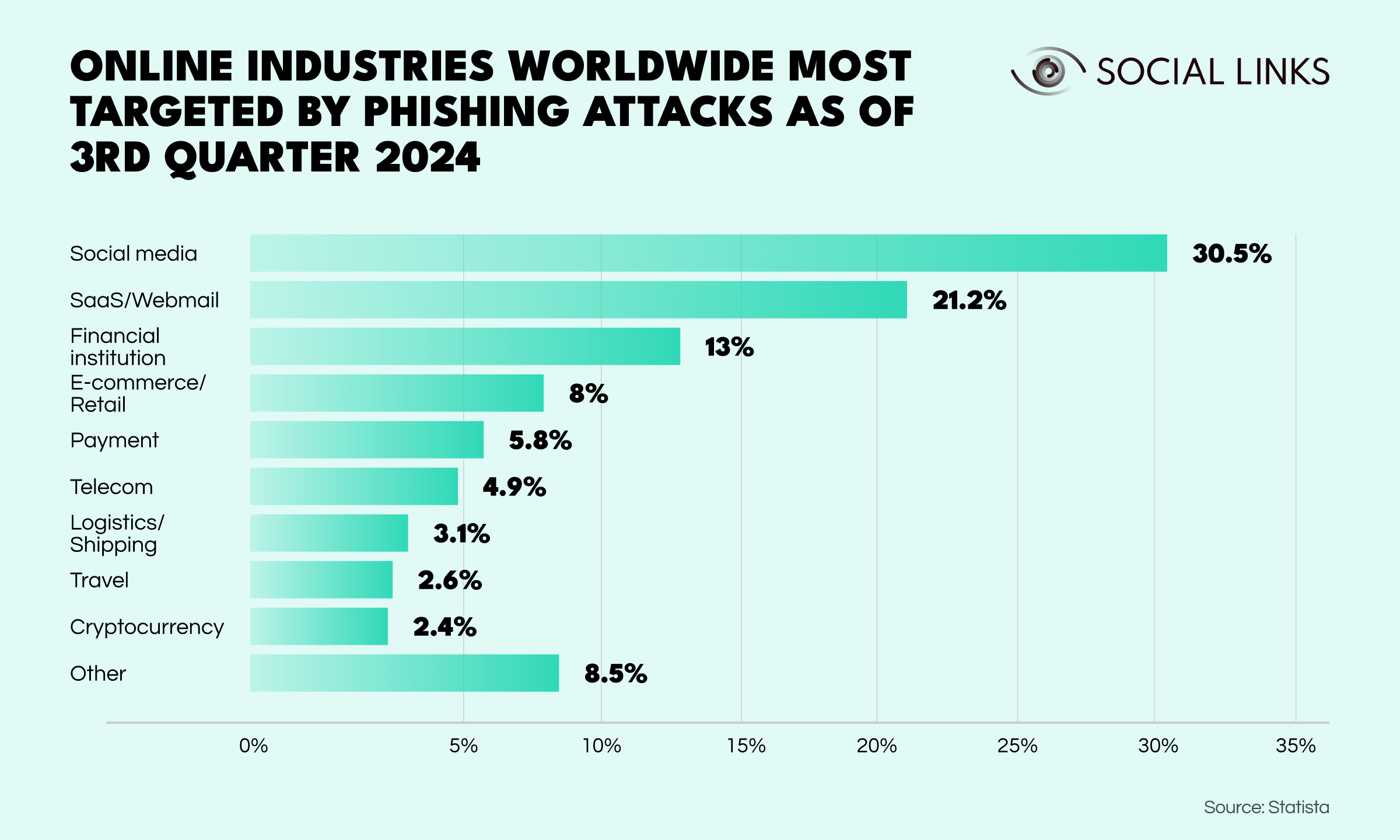
So it should come as no surprise that, according to Statista, social media accounted for a staggering 30.5% of all targeted phishing attacks as of Q3 2024. The explanation is simple: where there’s data, there’s opportunity, and public profiles, personal updates, and shared connections all offer attackers a rich stream of information to craft personalized, convincing lures.
What makes these threats even more dangerous is how convincing they’ve become. Advances in AI and generative technologies are fueling a new wave of sophisticated scams—ones that can mimic speech, replicate writing styles, and create realistic fake content at scale. For the average user, spotting a scam is getting harder by the day. For businesses, the stakes are even higher, as reputational damage and data leaks can snowball into a full-blown crisis.
This is the new reality of social media: always-on and highly targeted. And the threat landscape evolving at a speed that demands something more than just vigilance—it requires strategy.
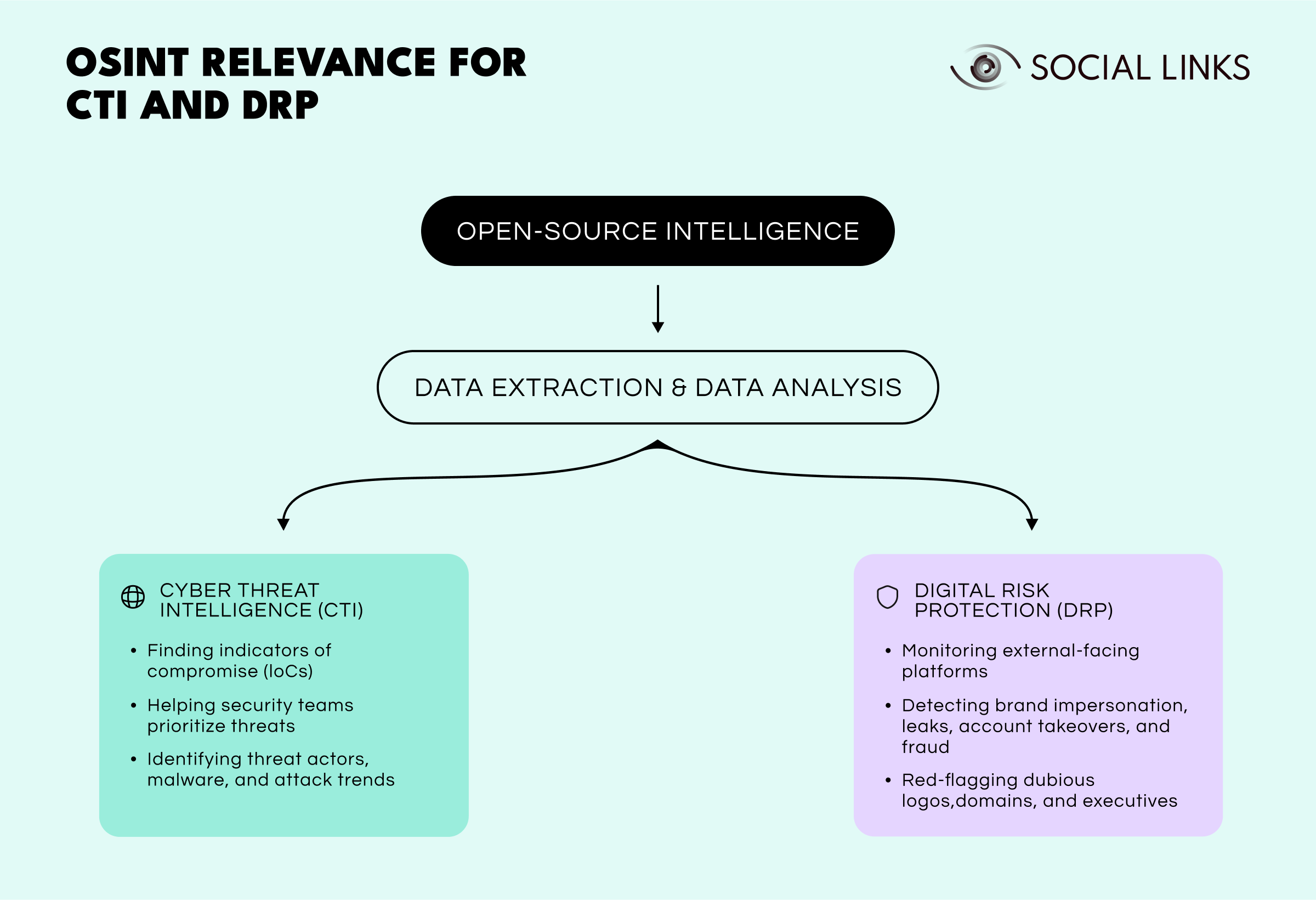
To stay ahead in this high-stakes environment, organizations can't afford to play defense alone—they need to be proactive. That’s where Cyber Threat Intelligence (CTI) and Digital Risk Protection (DRP) come into play. These two disciplines offer an approach to identifying, understanding, and neutralizing threats before they cause real damage.
CTI focuses on detecting threats at their roots. It involves collecting and analyzing data on attacker behavior, emerging malware strains, or shady domains—often before an actual breach occurs. Think of it as the radar system of cybersecurity: always scanning, always alert, and feeding organizations the insights they need to prepare and respond.
DRP, meanwhile, casts a wider net. Instead of looking solely inside the perimeter of an organization’s network, DRP is concerned with scanning the broader digital landscape—especially the open platforms where bad actors operate. Whether it’s a spoofed account impersonating a brand, sensitive data leaked on a forum, or a malicious hashtag campaign gaining traction, DRP helps businesses maintain visibility beyond their firewalls.
What ties CTI and DRP together is their reliance on open-source intelligence—publicly available data gathered from the very spaces where these threats live and breathe. From social media chatter to breach forums, such data provides the context and evidence that fuel effective threat detection.
In a world where cyberattacks often begin with a tweet, a post, or a fake profile, deploying both CTI and DRP isn’t just smart—it’s essential.
Open-source data refers to any publicly available information that can be collected, analyzed, and used to detect potential threats. Unlike classified intelligence or proprietary databases, open-source data is readily accessible to anyone with the right tools. These tools—such as Maltego, Shodan, SpiderFoot, or SL API—help cybersecurity professionals sift through vast amounts of data to uncover malicious activity.
Threat actors use social platforms to spread misinformation, run phishing scams, distribute malware, and impersonate individuals or brands for fraudulent purposes. Its the very openness of social media—a quality designed to connect people—that also makes it an easy target for those looking to exploit personal data.
At the same time, this transparency is what makes open-source data so valuable to security teams. By monitoring public posts, suspicious links, or unusual account activity, investigators can spot threats as they emerge, rather than reacting after the damage is done.
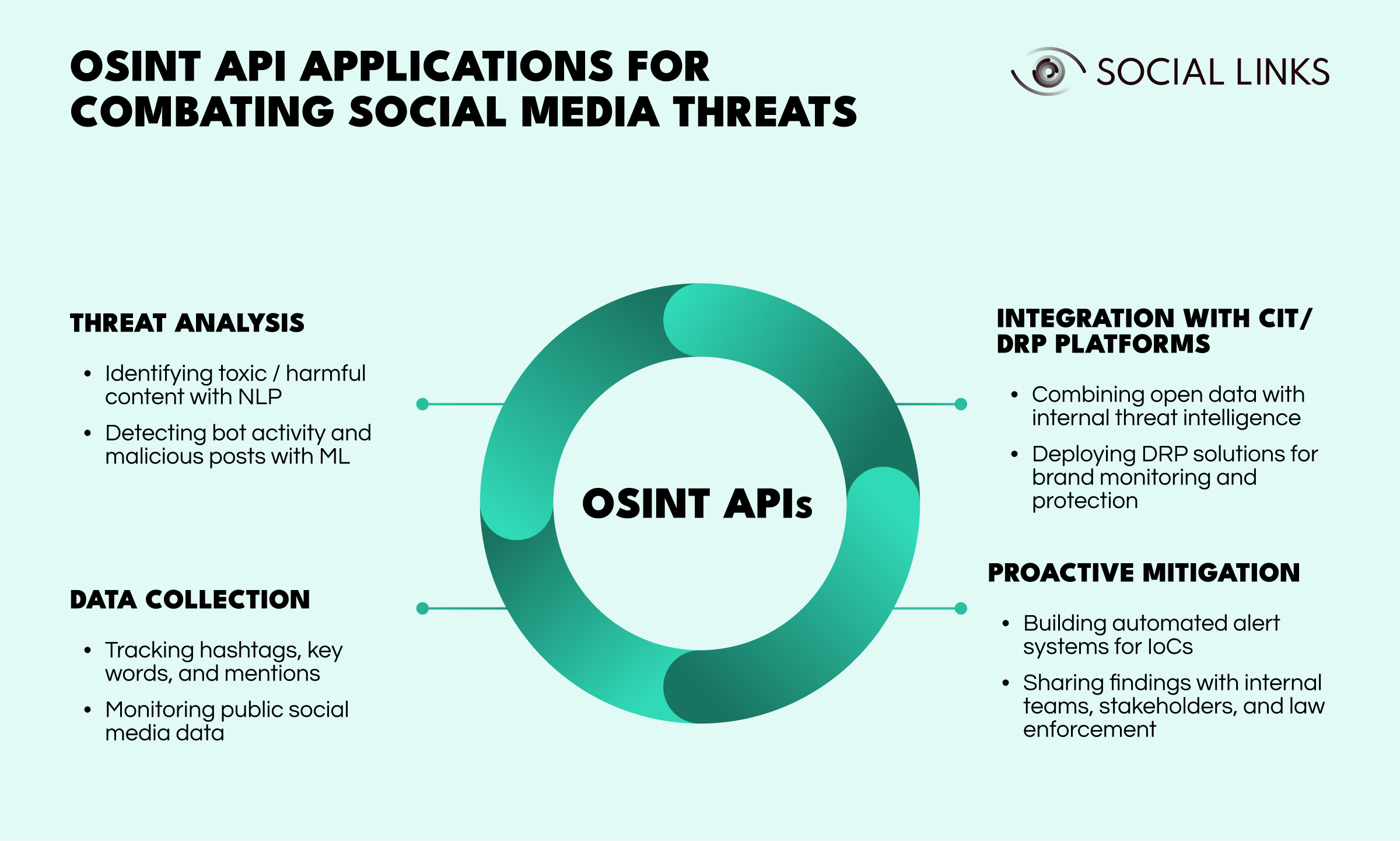
Given the varying nature of cybersecurity objectives from one team to the next, the apparatus of response tends to be of a specific set-up. In light of this reality, the OSINT API has emerged as a go-to solution for seamlessly integrating open data extraction and analysis with the existing in-house system and processes.
This enables cybersecurity teams to reach new levels of efficacy in their perennial work of countering the ever-evolving threat landscape. Here’s a quick breakdown of some of the most common threats currently to be found on social media, and how open-source data can help detect and respond to them effectively:
False narratives can damage brands, influence elections, and incite panic. Open data monitoring tools make it possible to track where these campaigns start, how they spread, and who’s amplifying them, allowing organizations to step in with counter-messaging or mitigation before reputational harm takes hold.
Fraudulent links shared through DMs, comment sections, or fake support accounts can lead to credential theft or malware infections. Open-source tools can flag risky URLs, identify high-risk accounts, and spot the early signs of phishing campaigns.
Fake profiles mimicking public figures or brands are used to steal information, push scams, or spread disinformation. OSINT platforms can detect changes in account behavior, identify lookalike accounts, and alert teams before followers are compromised.
Sometimes, it’s not hackers breaking into accounts—it’s employees leaking things out. Credentials, product roadmaps, or internal emails can end up on forums, paste sites, or shared accidentally on public channels, due to simple lapses of attention or more intentional activities of company personnel. Open-source data scanning helps detect exposed assets before threat actors do.
From hashtag manipulation to encrypted chat groups, social media is a coordination space for threat actors. OSINT tools can help map out networks, connect dots across conversations, and identify the infrastructure supporting these attacks.
Cyber threats don’t live in silos—they thrive in the open. By tapping into open-source data through OSINT APIs, security teams gain critical context and real-time visibility into threats as they develop.
Whether it’s a phishing scam gaining traction or a fake profile trying to hijack your brand, acting early can mean the difference between containment and crisis. And this is just the capability that the intelligent integration of open-source data can provide.
If you want to learn how Social Links API can take your business’ security to the next level, we’d love to help you get there. Get in touch with our experts through the link below and we’ll set up a totally personalized demo to answer all your OSINT questions and show you how Social Links API can change your approach to open data.