Behind Financial Fraud: How Schemes Operate


Financial fraud continues to evolve faster than detection systems. As financial institutions digitize operations, fraud increasingly exploits fragmented controls and siloed data. Detection models built for isolated events struggle against coordinated campaigns. What once appeared as discrete incidents now operates as interconnected schemes spanning identities, accounts, and infrastructure—often remaining undetected until significant losses force action.
In this article, we examine how modern fraud schemes operate in practice, why traditional fraud detection and transaction monitoring approaches struggle against coordinated attacks, and how financial threat intelligence enables earlier, more defensible detection. We also explore the role of investigative workflows, data correlation, and open-source intelligence in identifying early warning signals, supporting internal investigations, and strengthening fraud prevention and regulatory reporting at scale.
Financial fraud refers to deliberate acts of deception intended to obtain money, assets, or financial advantage through misrepresentation, impersonation, or abuse of financial systems. These activities affect individuals, businesses, and financial institutions, and they frequently serve as gateways into broader financial crime activity.
Unlike compliance errors or operational mistakes, financial fraud is intentional and adaptive. It relies on stolen identities, synthetic profiles, compromised accounts, and manipulated transactions. In practice, fraud rarely presents as a single suspicious event. Instead, it unfolds across multiple touchpoints—accounts opened legitimately, transactions that appear normal, and infrastructure reused across cases.
Modern financial fraud is defined less by individual anomalies than by coordination over time. The operational challenge is not recognizing fraud after the fact, but identifying when legitimate-looking activity begins to form a pattern that requires investigation.
Financial fraud schemes rarely exist in isolation. In real investigations, multiple techniques often overlap within the same operation, with attackers combining identity abuse, social engineering, automation, and laundering to maximize impact and evade controls. While terminology varies, the following categories appear consistently across enforcement actions and internal investigations.
Payment and Card Fraud involves unauthorized transactions, credit card misuse, and compromised payment credentials. Individually low-risk events often scale rapidly through automation and reuse, especially when controls focus on transaction value rather than behavioral patterns.
Identity Fraud and Account Takeover rely on stolen or fabricated identities to open or access accounts, followed by fund extraction, payment redirection, or laundering. Synthetic identities frequently bypass basic verification controls and surface risk only through longitudinal behavioral analysis.
Business Video and Voice Compromise extends traditional business email compromise by using synthetic media and deepfake technology to impersonate executives or vendors during live interactions. These schemes exploit sensory trust in real time to authorize high-value transfers or disclose sensitive information.
Agentic Fraud is an emerging model that uses autonomous AI agents to execute multi-step attack chains, such as navigating banking portals, interacting with customer support, or adapting to defensive feedback. Unlike static scripts, these agents can persist and scale with limited human oversight, increasing operational resilience for fraud actors.
Investment Fraud promotes false opportunities using fabricated credentials, endorsements, or performance claims. These schemes rely on coordinated digital presence across platforms to simulate legitimacy, social proof, and urgency.
Money Laundering and Related Financial Crimes frequently intersect with fraud operations, obscuring illicit proceeds through layered transactions and cross-border movement. This intersection complicates AML compliance and KYC processes when visibility is limited to isolated systems rather than end-to-end activity.
Most fraud programs are built to detect anomalies, not operations. Coordinated fraud is designed to remain within acceptable thresholds while exploiting fragmentation across systems.
Financial fraud schemes emerge gradually. They move from weak signals to coordinated activity as fraudsters test controls, reuse infrastructure, and scale behavior. Detection failures usually occur not because signals are missing, but because isolated events are never connected into a broader picture.
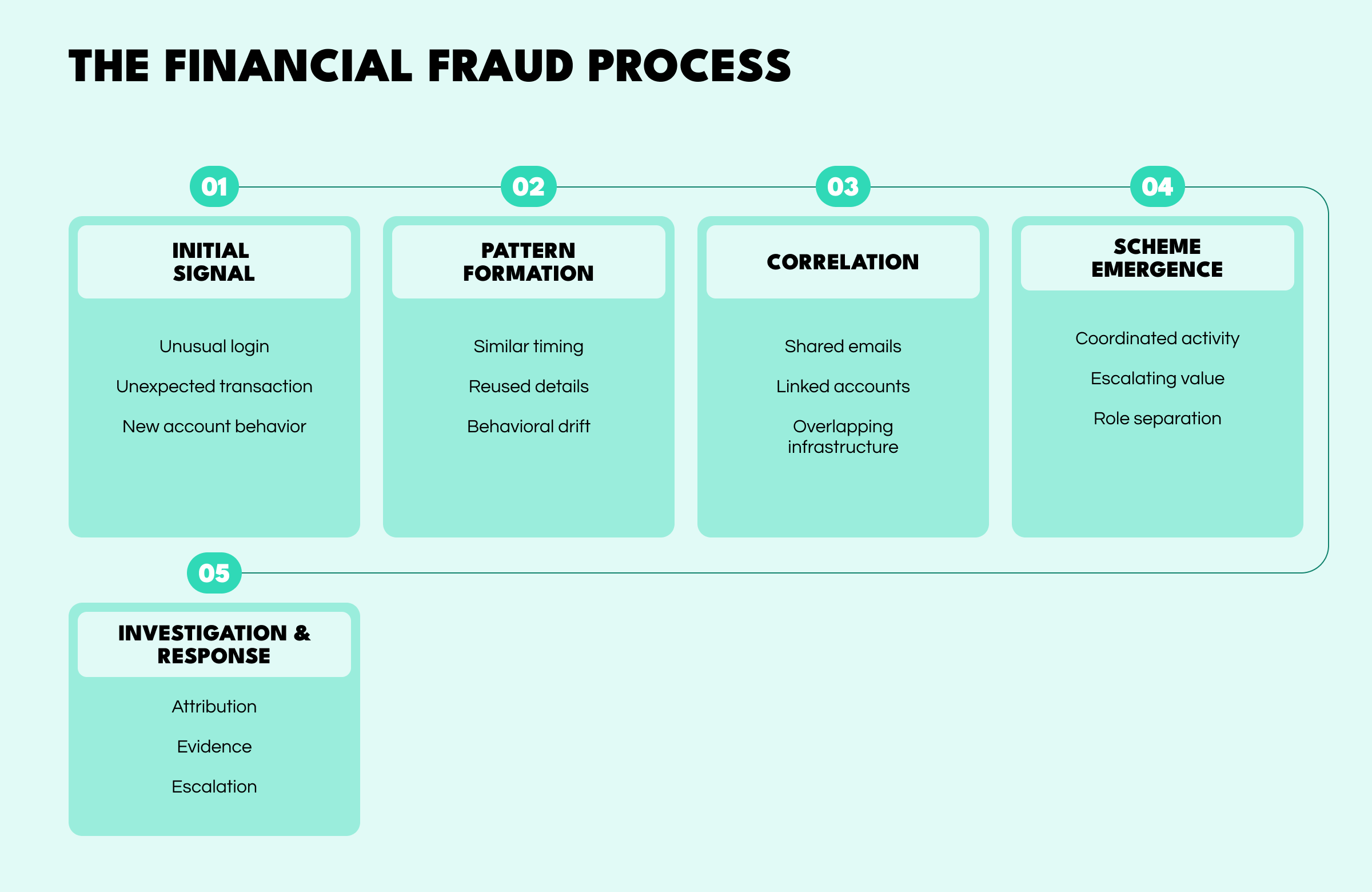
The process typically begins with a minor anomaly—an unusual login, an unexpected transaction, or unfamiliar behavior on a new or modified account. These events are common and often indistinguishable from legitimate activity.
At this stage, detection systems may generate low-confidence alerts or none at all. The risk lies in dismissing early signals as noise without tracking recurrence.
As activity continues, patterns begin to emerge. Transactions align in timing, details are reused across accounts, and behavioral drift becomes noticeable. Individually, these indicators may appear benign. Collectively, they suggest intent.
Visibility is often lost here. When monitoring remains account or channel-specific, emerging schemes stay fragmented.
Correlation is the point at which fraud becomes identifiable as coordinated activity. Shared email addresses, linked accounts, reused devices, or overlapping infrastructure reveal relationships that were previously invisible.
Without entity correlation and link analysis, organizations see transaction volume but miss the structure behind it.
Once correlated, the scheme becomes clear. Activity is coordinated rather than incidental. Transaction values escalate, roles within the network separate, and behavior aligns with known fraud patterns.
At this point, losses often begin to accumulate. The window for prevention narrows, and response increasingly becomes damage control.
Effective response requires structured investigation. Attribution analysis identifies responsible actors, while evidence collection supports internal investigations, AML compliance, and regulatory reporting.
Organizations that reach this stage without sufficient context often struggle to explain what happened, why controls failed, and how similar risk will be mitigated.
Most fraud programs invest heavily in detecting initial signals while underinvesting in the stages that follow. Financial threat intelligence and investigative workflows enable teams to move from signal detection to scheme disruption.
Early detection is not about generating more alerts. It is about recognizing when behavior transitions from anomaly to pattern, from pattern to scheme, and from scheme to reportable risk.
Traditional fraud detection asks whether a transaction violates a rule. Financial threat intelligence asks whether activity reflects coordinated behavior.
This distinction determines whether institutions detect fraud early or discover it after losses accumulate. Coordinated fraud exploits fragmentation, creating familiar operational problems: missed early warning signals, rising false positives, invisible suspicious activity patterns, and investigations triggered only after impact.
Financial threat intelligence addresses these gaps by shifting detection toward behavioral and relational analysis. It enables institutions to track early signals across accounts, identify emerging patterns, correlate identities and infrastructure, and prioritize response using contextual risk scoring.
By aligning detection capabilities to the stages of fraud progression, early detection becomes an investigative capability rather than a reactive alerting function.
No single system prevents financial fraud. Effective prevention depends on combining automation with investigation and governance, with each capability supporting a different stage of the fraud process.
Fraud Detection and Monitoring Systems provide scale and support early signal identification but require contextual enrichment to avoid overwhelming analysts with false positives.
Transaction Monitoring and Risk Scoring connect individual events to broader behavioral trends, helping teams prioritize cases during pattern formation and correlation.
Investigative Workflows and Case Management support attribution, evidence collection, and regulatory reporting, ensuring decisions are traceable, defensible, and repeatable.
Fraud prevention systems should reduce investigative noise. Technology accelerates detection, but investigation determines outcomes.
Internal data alone rarely explains coordinated fraud. External context is often what reveals reuse, attribution, and intent—particularly during the Correlation and Scheme Emergence stages.
Open-source intelligence and digital investigations provide visibility beyond institutional boundaries, enabling capabilities that internal systems cannot deliver independently.
Entity correlation connects identities, accounts, devices, and infrastructure by linking seemingly separate accounts through shared contact information, digital fingerprints, or behavioral patterns visible in public and commercial datasets.
Network analysis exposes coordinated fraud rings by mapping relationships between multiple actors, accounts, and entities to reveal the organizational structure behind fraud operations.
Link analysis uncovers hidden relationships by identifying connections that bypass traditional detection, such as shared social media profiles, business registrations, domain ownership, or leaked credential databases.
Attribution analysis connects observed activity to known fraud patterns by matching behavior to documented fraud tactics, threat actor profiles, or previously investigated schemes.
Evidence collection supports enforcement and compliance actions by gathering documentation from public sources, regulatory filings, and digital platforms to enable internal investigations and external reporting.
OSINT bridges gaps created by platform silos and jurisdictional limits. When combined with internal data, it transforms isolated alerts into actionable intelligence that supports internal investigations and regulatory scrutiny.
External intelligence is particularly critical when fraud spans multiple institutions, jurisdictions, or platforms—contexts where internal visibility ends but fraud operations continue.
Despite advances in fraud detection, several structural challenges persist. Automated systems generate alerts faster than analysts can validate them, leading to alert fatigue, rising false-positive rates, and missed early warning signals. At the same time, fraud actors continuously adapt tactics, exploiting gaps between detection model updates and control changes.
Data silos across business units and platforms further limit visibility, preventing effective correlation and allowing coordinated schemes to remain hidden across organizational boundaries. Regulatory complexity compounds this problem: AML and KYC requirements evolve steadily, while fraud tactics often adapt faster than regulatory frameworks can respond.
Institutions must also balance speed, accuracy, and customer experience. Aggressive controls introduce friction for legitimate users, while lenient controls increase exposure. Financial fraud cannot be eliminated entirely—it can only be managed through layered controls, continuous refinement, and alignment between detection systems, analysts, and governance. Organizations that treat fraud prevention as an ongoing process rather than a static control set are better positioned to adapt as threats evolve.
Financial fraud has evolved from isolated incidents into coordinated operations that exploit fragmentation, automation, and scale. Detection models built for single transactions or accounts struggle against schemes that distribute activity across identities, infrastructure, and time.
Effective fraud prevention requires understanding the full progression from early signals to coordinated schemes. Organizations that invest in correlation, intelligence-led detection, and investigative workflows—supported by OSINT and external context—identify fraud earlier, reduce losses, and strengthen regulatory compliance.
The institutions that succeed stop asking “Is this transaction suspicious?” and start asking “Is this behavior part of a larger operation?” That shift defines the difference between detecting fraud and preventing it.
Financial fraud refers to deceptive acts intended to obtain financial gain, while financial crime is a broader category that includes fraud, money laundering, and related offenses. Fraud often serves as an entry point into wider criminal activity.
Financial institutions rely on fraud detection systems, transaction monitoring, behavioral analysis, and financial threat intelligence to identify early warning signals before losses escalate.
Open-source intelligence provides external context, helping investigators correlate identities, infrastructure, and networks involved in fraud. This supports attribution and evidence-based decision-making.
Automation improves speed and scale, but human investigation remains critical. Analysts validate findings, interpret context, and ensure compliance with regulatory requirements.
Fraud detection supports AML compliance and KYC processes by identifying suspicious activity patterns, high-risk entities, and evolving exposure over time.
Want to see how financial threat intelligence strengthens fraud detection and investigations? Book a personalized demo with one of our specialists and discover how SL Crimewall helps teams correlate identities, uncover coordinated fraud schemes, and support defensible investigations—all within a single, compliant intelligence platform.