Digital Forensics in Cyber Security: From Incident to Evidence


Security tools aim to detect unusual behavior. Digital forensics aims to explain it. In modern environments—where activity spans cloud systems, endpoints, identity platforms, and hybrid infrastructure—detection alone does not provide enough clarity. Alerts indicate that something may be wrong, but they do not establish scope, reconstruct timelines, or preserve reliable evidence. Without forensic capability, organizations may contain an incident without fully understanding its impact or root cause.
In this article, we explain how digital forensics in cyber security works in practice and why it is necessary for turning alerts into verified findings. We cover common investigation types, structured workflows, core analytical methods, and the broader value of forensic capability, along with the operational limits that affect modern investigations.
Digital forensics in cyber security is the structured collection, preservation, analysis, and interpretation of digital evidence after a security incident. Its goal is to establish what occurred, measure exposure, and document conclusions suitable for executive, regulatory, and legal review.
While monitoring tools focus on detection, forensic investigation focuses on verification and explanation. It addresses questions such as:
Detection highlights risk. Forensics clarifies facts.
Monitoring systems identify suspicious signals. Forensics provides context and measurable impact.
An alert may flag malicious activity on a single system. Forensic analysis reconstructs how the attack began, how access was maintained, and how it progressed. This establishes whether the incident lasted minutes, days, or months.
Without a reliable timeline, organizations may underestimate exposure or delay required reporting.
Detection may isolate a single device or account. Forensic investigation determines whether other systems were involved, whether credentials were reused, and whether data was accessed or removed.
Scope directly affects remediation cost and regulatory risk.
Monitoring reveals anomalies. Forensic review examines techniques, infrastructure, and tools to assess whether activity aligns with known attack patterns.
Attribution is rarely absolute, but structured analysis increases confidence and supports informed response decisions.
Cyber security programs focus on prevention and detection through tools such as endpoint protection, SIEM platforms, and network monitoring systems.
Digital forensics begins once suspicious activity is identified. Investigators review logs, memory data, file systems, and other artifacts to determine what occurred and why.
Together they form a feedback cycle:
Without forensic review, detection remains incomplete. With it, alerts become documented findings.
Digital forensics includes several specialized disciplines. Each addresses different technical questions.
This involves examining disk images, registry entries, scheduled tasks, and system logs. It helps determine how access was gained, how persistence was established, and whether activity was automated or manual.
Endpoint analysis is often central to understanding phishing-based compromise or unauthorized remote access.
Memory analysis focuses on volatile data stored in RAM. It can reveal active processes, fileless malware, encryption keys, or command-and-control activity that may not be written to disk.
This is especially important when attackers avoid leaving persistent traces.
This discipline reviews packet captures, flow records, and network telemetry. It helps determine whether data left the environment, how systems communicated, and whether external infrastructure was reused across incidents.
Network evidence can confirm whether exfiltration actually occurred.
Investigators review authentication logs, cloud audit records, and identity system events to trace account activity across distributed systems.
In hybrid environments, no single log provides a complete picture. Reviewing multiple sources helps determine whether activity involved a single compromised account or broader identity misuse.
This involves examining suspicious binaries or scripts to understand how they functioned, what permissions they required, and how they maintained access.
Malware review helps distinguish commodity attacks from targeted operations and identifies control weaknesses that allowed execution.
Each discipline contributes part of the picture. A complete investigation combines these perspectives into a coherent sequence of events.
Digital forensic work follows a structured process designed to preserve evidence and support defensible conclusions.
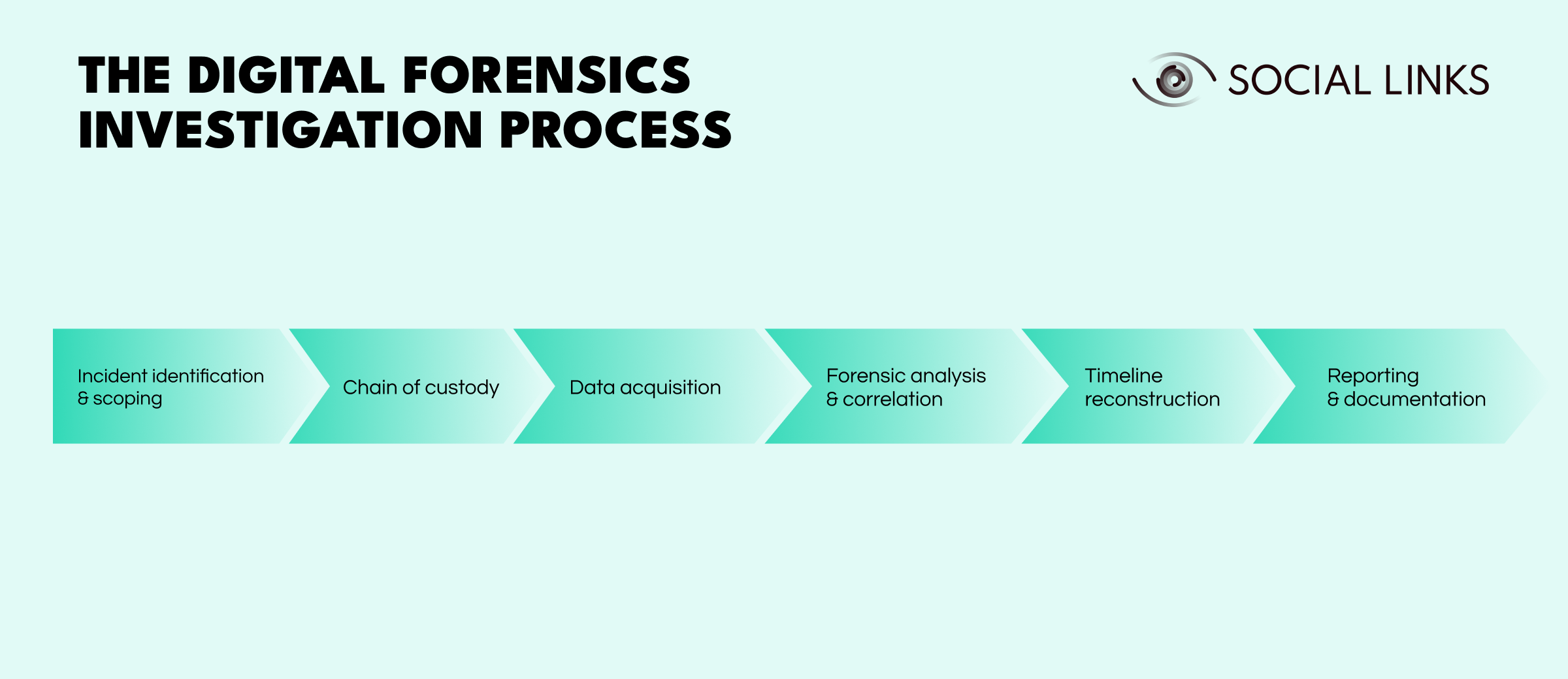
Investigators define which systems, accounts, and data may be affected. Clear scoping prevents both missed evidence and unnecessary expansion of effort.
Evidence handling is documented from the moment collection begins. Records show:
Proper documentation protects the integrity of findings during audits or legal review.
Investigators collect data from endpoints, servers, network devices, and cloud platforms. This may include disk images, memory captures, log exports, and cloud audit data.
In cloud environments, rapid collection is often required because logs and workloads may be short-lived.
Artifacts are examined to identify patterns, persistence mechanisms, lateral movement, and infrastructure reuse. Findings from different systems are reviewed together to identify relationships and sequence.
Events are organized chronologically to determine:
A clear timeline defines duration and impact.
Findings are documented in a structured format suitable for technical teams, leadership, regulators, and legal counsel. Reports must explain what occurred and provide supporting evidence.
Forensic investigations rely on specialized tools and disciplined methodology.
Common capabilities include:
Methods include timeline reconstruction, behavioral analysis, and identifying shared infrastructure across incidents.
Tools accelerate data processing. Analysts provide interpretation. Effective investigations require both.
Modern cloud environments increasingly require API-based data collection rather than traditional disk imaging alone.
Digital forensics is not limited to breach containment. It supports long-term risk management and accountability.
Structured review identifies logging gaps, control failures, and weaknesses in detection logic. Lessons learned can be applied to prevent recurrence.
Forensic procedures support insider threat cases and policy violations by ensuring evidence is documented and defensible.
Clear documentation and preserved evidence demonstrate due diligence during audits or legal proceedings. This reduces uncertainty and potential liability.
Leadership often needs clear answers: When did the incident start? What data was affected? Were controls functioning properly? Forensic findings provide a factual basis for those decisions.
Investigation results often lead to improved logging, refined monitoring rules, and stronger identity controls.
Forensics helps organizations use incident data to improve controls and monitoring.
Digital forensics operates under real constraints.
Modern systems generate large volumes of data, increasing analytical workload. Encryption and short-lived cloud resources can limit available evidence. Sophisticated attackers may delete logs or manipulate timestamps. Multi-cloud environments introduce inconsistent logging formats and legal considerations. Skilled forensic expertise remains specialized and resource-intensive.
For these reasons, many organizations invest in forensic readiness—designing logging and retention policies with investigation in mind.
Digital forensics is becoming more integrated into security architecture rather than treated as an afterthought.
AI-assisted analysis can help process large datasets more efficiently, but human review remains essential. Automated tools can identify patterns quickly, but conclusions require validation.
As defensive capabilities improve, attackers continue to develop anti-forensic techniques. Investigation remains an ongoing technical discipline rather than a static capability.
Detection identifies potential incidents. Digital forensics determines what actually occurred.
Without forensic investigation, organizations may resolve alerts without understanding full impact. With structured analysis, they can reconstruct events, preserve evidence, and strengthen controls based on verified findings.
In modern cyber security, explanation is as important as detection.
It is used to reconstruct incidents, preserve evidence, determine impact, and support regulatory or legal action. Beyond containment, it provides defensible explanations for what occurred and why.
Cyber security focuses on detection and prevention. Digital forensics investigates and validates incidents. Together they create a continuous improvement loop that strengthens monitoring and response.
It is a structured process for collecting, preserving, analyzing, and documenting digital evidence to produce defensible conclusions after a security incident.
Investigators use specialized tools for disk imaging, memory analysis, log correlation, network traffic review, and malware investigation—all designed to preserve evidence integrity.
It transforms alerts into evidence, validates response decisions, supports compliance, and improves long-term defensive posture based on verified findings.
Want to strengthen your digital forensics and investigation capabilities? Book a demo to see how SL Crimewall supports security and forensic teams with advanced entity resolution, timeline reconstruction, and multi-source intelligence correlation—enabling faster, more comprehensive investigations across complex digital environments.