Investigating Illegal Content on the Dark Web with Stealer Logs


Unfortunately, abuse material has been a persistent issue since the advent of the internet, with its circulation only becoming more difficult to combat as technology advances. However, the emergence of infostealers—a new type of malware—has given investigators an effective new tool for combating this ongoing issue.
So, in this post we’re going to explore what infostealers are and demonstrate how they can be effectively applied to deanonymize distributors and consumers of illegal content. Let’s take a look.
The Dark Web, especially when accessed through browsers such as TOR, has provided a haven for those involved in the production and consumption of illegal content. This is because such browsers provide highly effective anonymization features with which users can cloak their activities, making it incredibly challenging for law enforcement agents to identify and apprehend offenders.
However, a new hacking tool has emerged that has the potential to aid investigations. Around five years ago, the deployment of a new type of malware known as infostealers became widespread, through two popular iterations of the tool in particular—RedLine and Racoon stealers.
Designed to steal information from infected devices, infostealers have been widely sold on the Dark Web, and subsequently deployed on a huge scale. This has resulted in millions of infected devices worldwide, and vast quantities of stolen data being leaked.
The data extracted through infostealer deployment are known as stealer logs, and these can provide the investigator with an array of highly useful information, such as personal credentials, session cookies, hardware data, and more.
The value stealer logs held for various cybersecurity purposes was perhaps to be expected—but what was unexpected was the immense potential they held for identifying individuals involved in the consumption and distribution of abuse content. These logs can provide highly detailed personal information, enabling investigators to build comprehensive profiles of offenders on an unprecedented scale.
So, how does all of this work from our side? Using Crimewall, we can conduct an advanced search through the stealer logs, with a focus on a relevant domain, then identify the individuals whose data indicate activity within these domains.
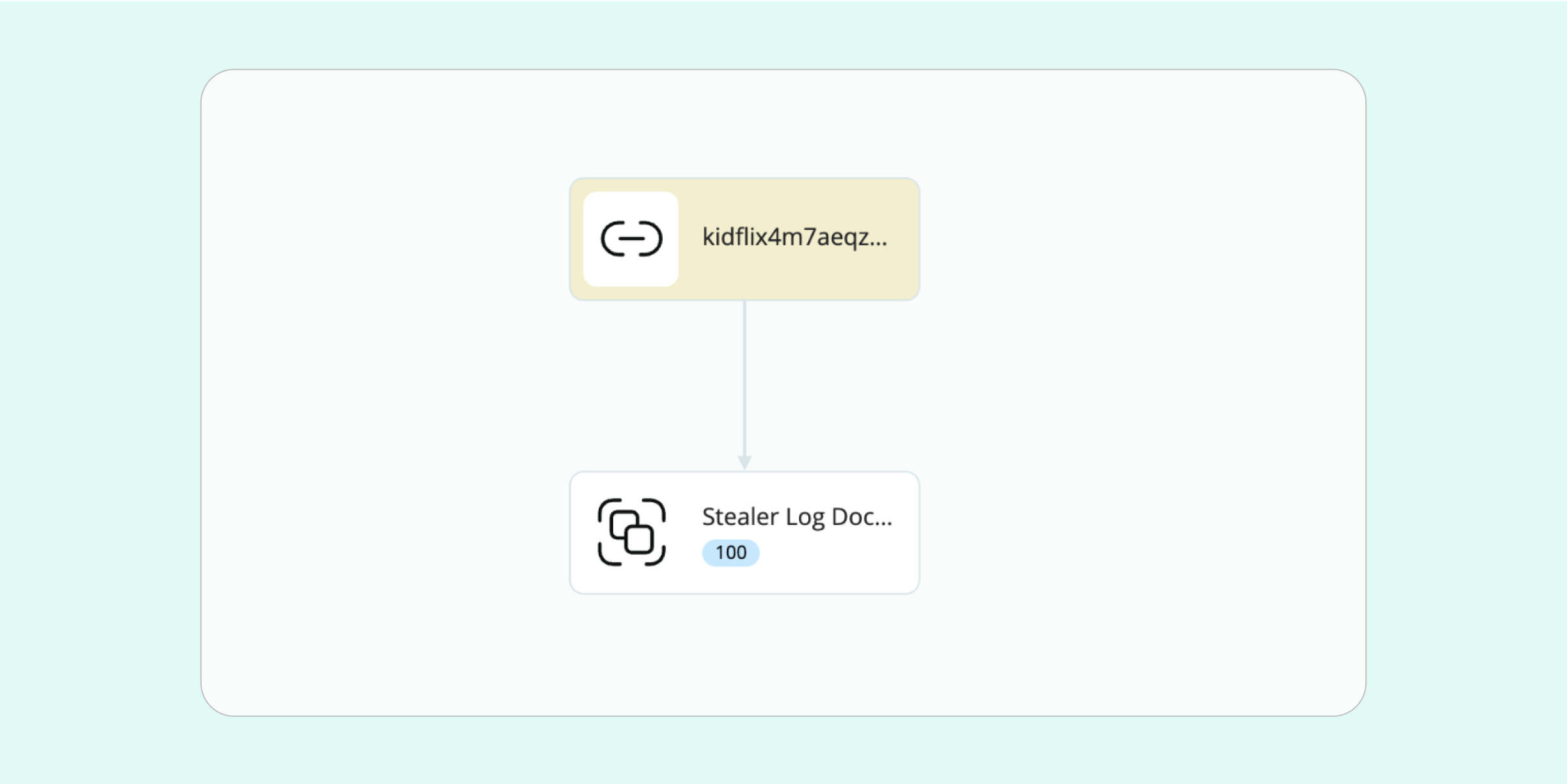
Typically, on Dark Web platforms, the only identifiers investigators can go on are a mere username, which is usually insufficient to fully trace their identity. The stealer log approach gets around this difficulty, because by searching for domains associated with these illegal platforms, we can relate the name of the user to a specific and unique device serial number.
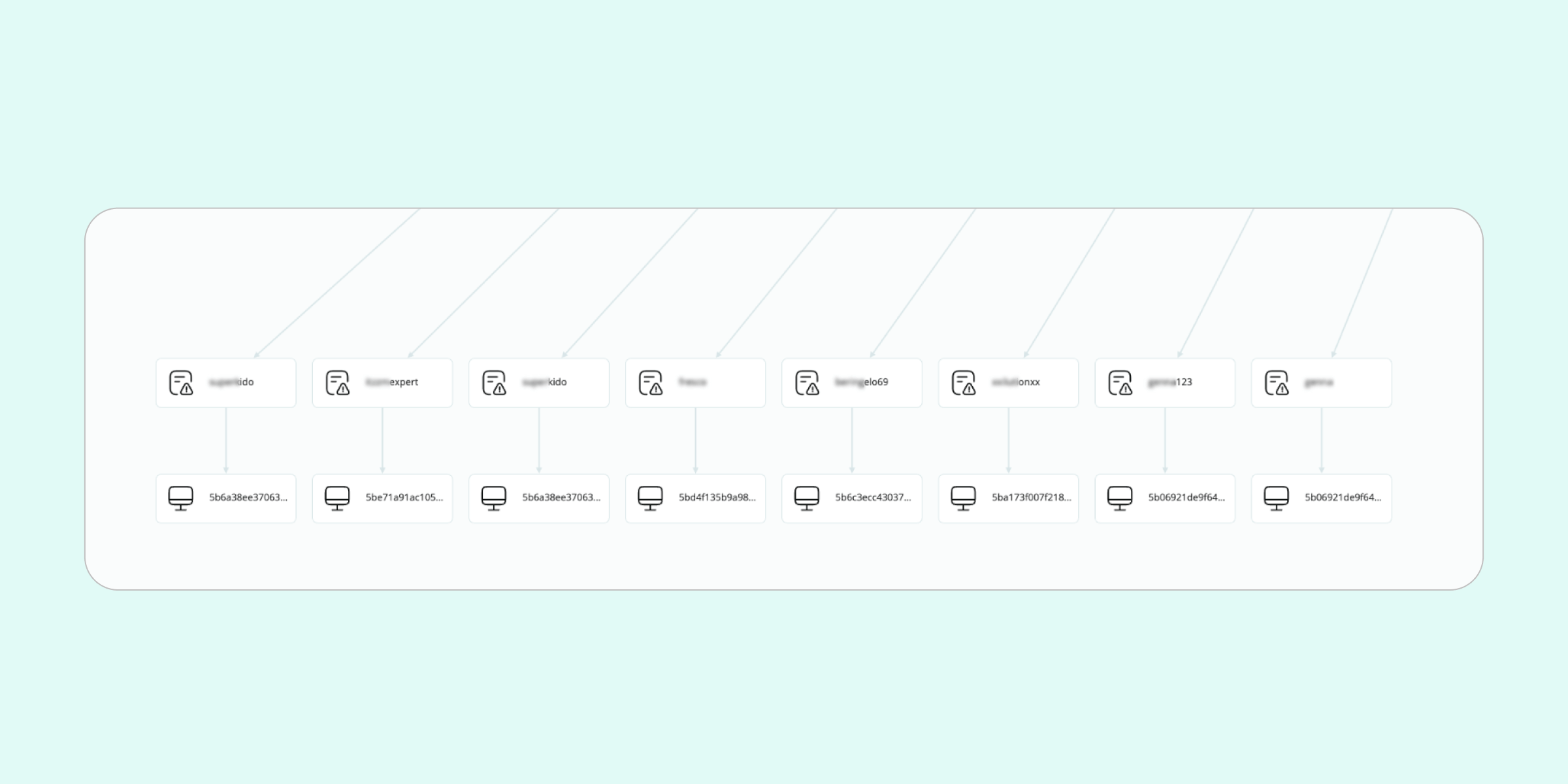
This not only provides a more reliable path to making connections, it also casts a wide net, finding multiple suspects at once. And once you have a suspect’s device serial number, you’re “over the hump”—now by investigating around the device in question, you can soon gain a range of identifiers for further profiling, and elaborate a full picture of your suspect.
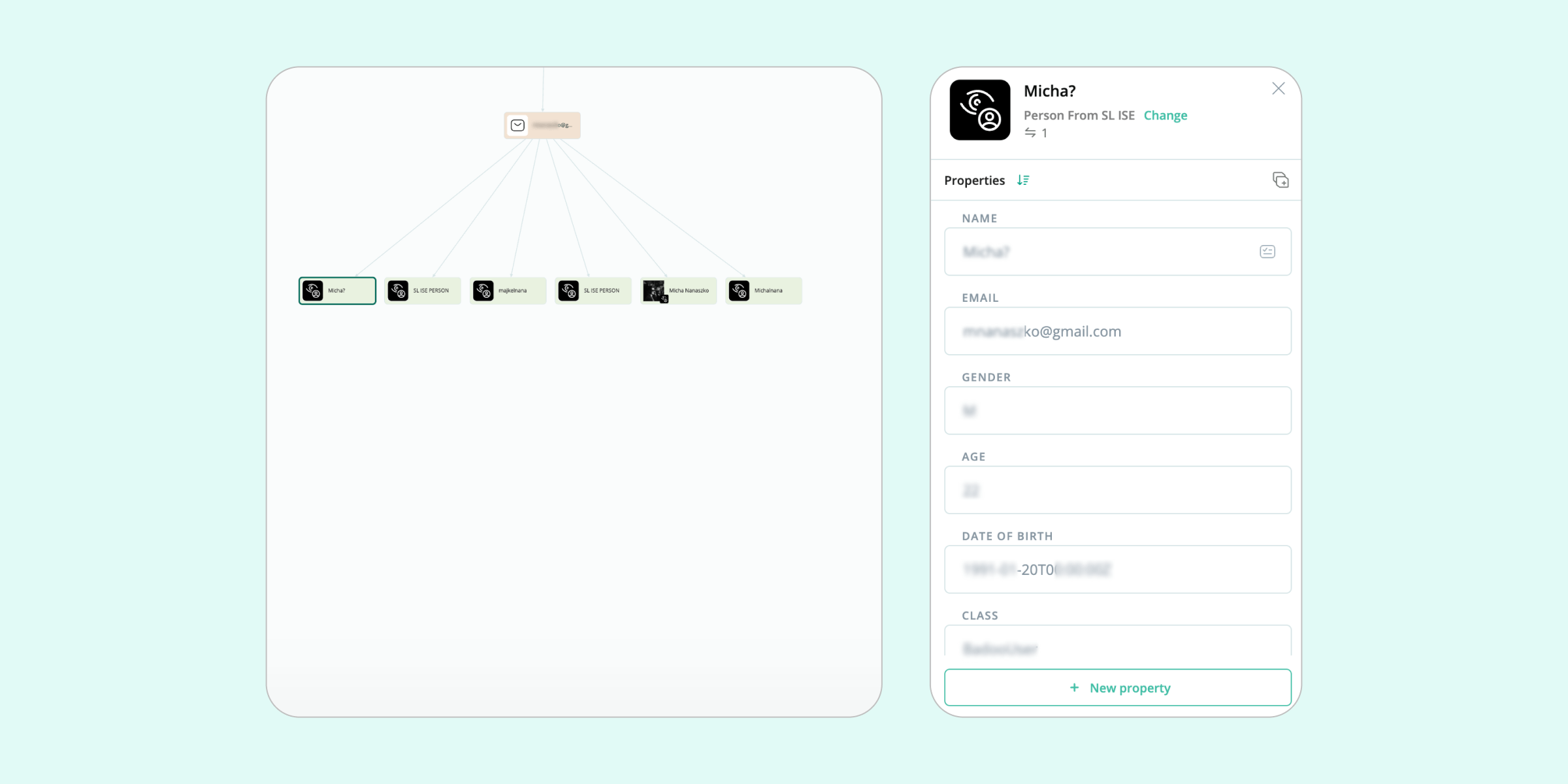
After we have extracted personal identifiers from the stealer logs—such as email addresses, actual addresses, national forms of ID, phone numbers, or even full names—we can proceed with a standard profiling process. This is the stage where we gather additional information about the suspect through various investigative methods.

For example, using Crimewall’s suite of “Get” methods, we can run searches from all available emails and phone numbers to find connected profiles. This can then be followed by facial recognition searches to identify images of the subject, profile retrieval from different social media platforms or other sources, and information cross-checking with all kinds of publicly available or leaked data.
This approach enables us to build a comprehensive profile that can link a real-world identity to their online activities, and potentially to the consumption or distribution of illegal content on the Dark Web—a result extremely difficult to achieve without leveraging stealer logs. By building on stealer log data to find personal identifiers and social connections, we can significantly enhance the chances of accurately identifying and apprehending offenders.
If you’d like to learn more about how the stealer log features of SL Crimewall can transform investigations into illegal content on the Dark Web, get in touch. Simply follow the link below to arrange a meeting with one of our specialists, where you can get answers to any questions you have and receive a personalized demonstration.