Online Background Checks: Getting the Full Picture


Online background checks now sit at the center of how organizations manage hiring, compliance, and operational risk. As teams expand across remote workforces, global contractors, and digital-first operations, background checks are no longer limited to criminal records or employment verification.
Today, companies use background check software to understand how a person or business actually shows up online—whether their identity is consistent, where their digital exposure exists, and what risks may surface before onboarding employees, partners, or vendors.
In this article, we look at how online background checks work in practice, how modern tools differ from traditional background verification companies, and where open-source intelligence fits into digital screening. We also explore what makes a screening tool effective and what teams need to consider around compliance and governance.
An online background check brings together publicly available and authorized data to help organizations evaluate identity, behavior, history, and potential risk. In business settings, this typically supports employee screening, contractor onboarding, compliance reviews, and internal investigations.
Traditional screening usually relies on sources such as:
These sources still matter. But they capture only part of today’s risk landscape. Much of modern exposure lives in digital behavior: social platforms, online marketplaces, technical infrastructure, leaked credentials, media coverage, and public corporate records. Digital background screening expands visibility into how identities operate across connected online environments, not just what appears in formal registries.
This is where OSINT starts to matter in practice. Open-source intelligence collects and connects publicly available data across the web, platforms, registries, and infrastructure. When these signals are correlated properly, they reveal patterns and context that static databases cannot. A modern online background check becomes less about isolated lookups and more about building a connected picture of how an identity evolves over time.
The financial impact of weak screening is real. A bad hire doesn’t just waste recruiting time—it creates rework, slows teams down, and often pushes organizations back into the hiring cycle without addressing the underlying problem.
Industry estimates cited by Business.com suggest that a bad hire can cost up to roughly 30% of an employee’s first-year salary once recruiting, onboarding, and lost productivity are factored in. In many cases, the true impact climbs higher when replacement hiring, retraining, and team disruption are included.
Beyond the direct costs, hiring mistakes quietly erode morale and operational momentum. Teams absorb the friction of repeated onboarding, delayed projects, and lost confidence. Over time, those effects compound across departments and workflows.
Because the consequences ripple outward, many organizations invest more heavily in consistent, defensible screening processes. When done well, background checks reduce avoidable churn, lower the likelihood of preventable incidents, and support decisions that teams can confidently justify later—especially in fast-growing or distributed environments.
Background check solutions automate large parts of data discovery, normalization, and analysis while keeping investigators in control. In practice, most platforms follow a similar operational flow.
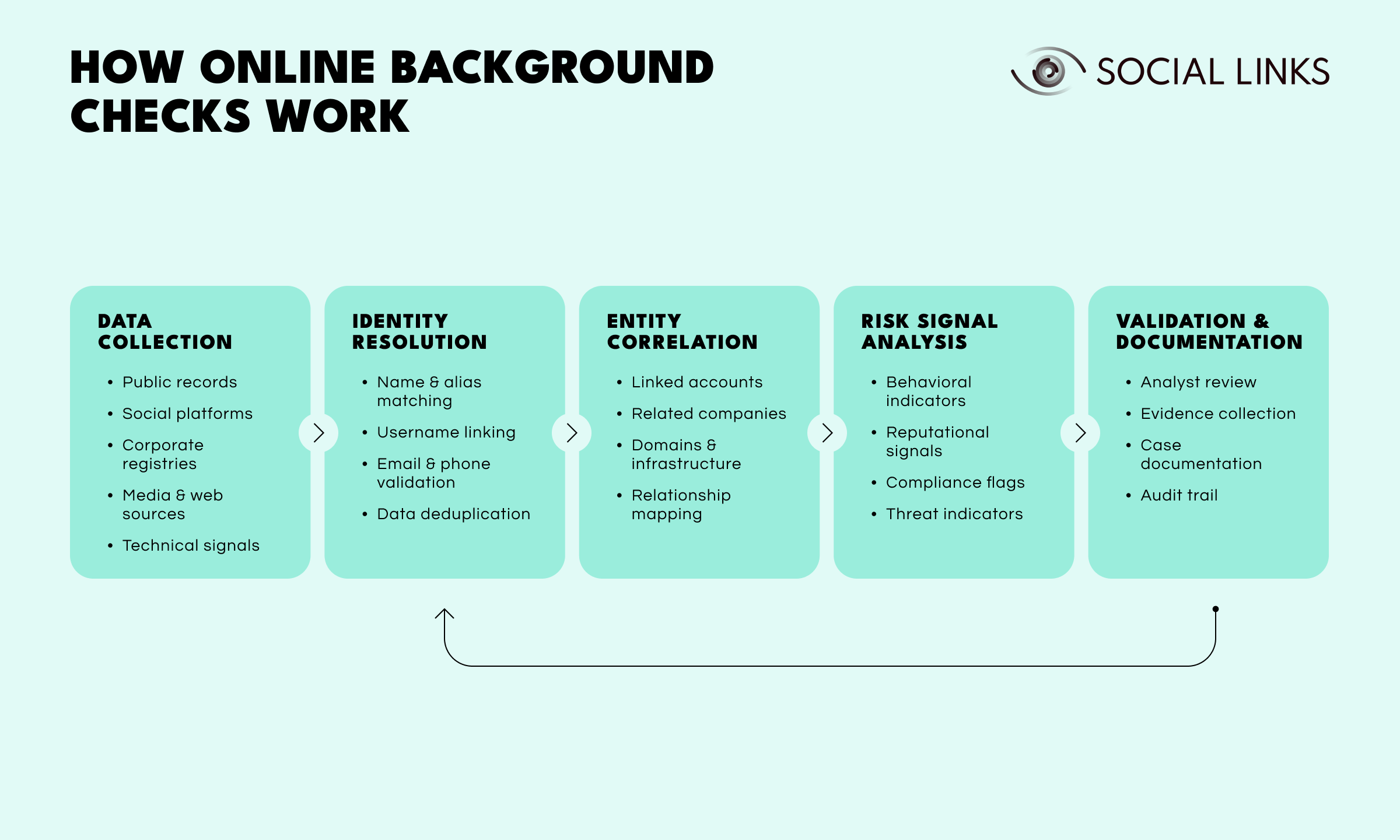
Data collection. Public records, professional networks, social platforms, corporate registries, sanctions lists, and technical sources are continuously collected and standardized. Automation reduces manual research effort and improves consistency across regions and datasets.
Identity resolution. Names, aliases, usernames, emails, phone numbers, and employment references are validated and deduplicated to reduce misattribution. This step strengthens identity verification and helps surface early fraud indicators.
Entity correlation. Related accounts, companies, domains, and digital assets are linked together so teams can see how identities interact across systems instead of reviewing fragmented records.
Risk signal analysis. Behavioral indicators, reputational signals, compliance flags, and threat intelligence signals are evaluated to surface potential hiring risk or regulatory exposure.
Validation and documentation. Investigators validate findings, document evidence, and escalate issues through structured workflows that support auditability and defensibility. In practice, this validation step often feeds back into identity resolution—newly confirmed aliases, corrected records, or disproven assumptions refine the underlying profile and improve future correlation and monitoring.
Strong background check software balances automation with human judgment. Fully automated scoring can introduce blind spots, bias, or false positives. Hybrid systems allow analysts to interpret context, challenge assumptions, and validate conclusions rather than relying solely on algorithmic output.
Once organizations understand what effective screening actually requires—continuous data ingestion, identity resolution, correlation, analysis, and defensible review—the next decision becomes structural: whether to build this capability internally using software tools or outsource it to background verification companies.
Most organizations choose between operating background checks internally using dedicated platforms or outsourcing checks to background verification companies.
Background verification companies typically provide:
This model works well for regulated or low-volume screening but becomes restrictive when organizations need faster turnaround, ongoing monitoring, or investigative flexibility.
Background check platforms, by contrast, offer:
Instead of outsourcing the investigative layer, teams retain operational control and institutional knowledge internally while maintaining compliance and traceability.
Many enterprises ultimately adopt a hybrid model. Verification companies handle formal regulatory checks, while background check tools support digital screening, internal investigations, and workforce due diligence.
Not all background check solutions deliver meaningful operational value. For teams evaluating available platforms, several capabilities matter most.
Broad data aggregation. Coverage should extend beyond single datasets to include public records, platforms, registries, media intelligence, and technical sources.
Entity correlation and identity resolution. Linking aliases, usernames, domains, and corporate entities prevents fragmented analysis and missed relationships.
Investigation workflow support. Case management, evidence tracking, audit trails, and collaboration tools improve consistency and defensibility.
Real-time monitoring and trend detection. Continuous monitoring helps teams detect changes in risk posture rather than relying on static point-in-time checks.
Compliance controls and access governance. Data retention policies, access permissions, and auditability support regulatory requirements and internal accountability.
A capable screening tool improves decision quality—not just data volume.
Online background checks support a wide range of decisions across hiring, compliance, security, and risk management. The real value is not simply confirming facts, but identifying inconsistencies, exposure, and behavioral signals early enough to act responsibly.
Hiring decisions carry long-term operational consequences, especially for roles involving system access, financial authority, sensitive data, or public representation. Beyond verifying resumes and credentials, digital screening helps teams assess identity consistency, online behavior, and potential reputational exposure before onboarding.
Common signals reviewed during screening include:
This reduces misrepresentation, insider risk, and costly post-hire remediation.
Extended workforces introduce indirect access to systems and data that traditional screening may miss.
Digital background checks support:
For investigations, connected digital screening supports timeline reconstruction, identity linkage, and defensible evidence handling.
Regulated organizations must continuously monitor exposure to sanctions, financial crime, and regulatory violations.
Digital screening supports compliance teams by:
This enables continuous visibility rather than periodic review cycles.
Modern fraud often exploits fragmented digital identities rather than single credentials.
Online background checks help by:
This reduces fraud exposure and accelerates response.
Risk does not stop after onboarding.
Continuous screening enables:
Across these use cases, the goal remains the same: replace fragmented signals with connected insight and move from assumption-driven decisions to verifiable evidence.
Background screening is no longer a one-time transaction or a simple procurement exercise. It is an operational capability that touches compliance, security, HR, legal, and risk teams simultaneously.
Choosing the right background check software requires aligning tools with workflows, governance requirements, and long-term scalability—not simply comparing feature lists.
Key considerations include:
Background screening should be treated as operational infrastructure, not a checkbox.
Online background checks are no longer simple verification exercises. Business risk increasingly emerges from digital behavior, interconnected platforms, and evolving identity signals. Effective background check software must support investigation, context, and accountability—not just automation.
Organizations that combine OSINT data sources, entity correlation, and structured investigation workflows gain stronger visibility into operational risk while maintaining compliance and trust. The value lies not in collecting more data, but in making better decisions backed by transparent evidence.
An online background check combines public records, digital data, and automated screening tools to assess identity and risk. Most organizations blend automation with analyst review for accuracy.
Background check tools provide direct access, workflow control, and real-time monitoring. Background verification companies outsource research and reporting but offer less flexibility and transparency.
Strong coverage, entity correlation, investigation workflows, compliance controls, and scalability are critical for operational success.
Digital screening correlates online identities, behavior patterns, and risk signals to uncover hidden exposure relevant to AML, KYC, and fraud prevention.
Yes. Continuous monitoring allows organizations to track evolving risk rather than relying on static point-in-time checks.
Want clearer visibility into digital risk during hiring and onboarding? Book a personalized demo to see how SL Crimewall helps teams investigate digital footprints, correlate identities, validate exposure, and manage background screening workflows inside a single, compliant intelligence platform.