Online Dust: A Deep Dive into Digital Footprint Investigations


Imagine throwing a handful of glitter at a party. Days later you’ll still find specks on your clothes, your sofa, maybe even your dog. Every click, post, like, purchase, and late-night Google search is the internet equivalent of that glitter—tiny, persistent markers that stick around long after the fun (or panic-scroll) ends.
Your digital footprint is the trail of data you leave behind whenever you interact with the internet or any networked device. Some crumbs are deliberate—your LinkedIn bio, your company blog, that proud post about finally getting a certification. Others are accidental—metadata in photos, old forum posts, quietly ticking ad-tracker IDs. Together they create a mosaic that can be shockingly detailed and—for investigators and bad actors alike—pure gold.
So today we’re taking a close look at these remarkable digital artifacts, including why they are so important for both security and investigation purposes, the tools that are instrumental working with them, recommended investigation approaches, and more. Let’s jump in.
These days, most companies sink real money into hardening the plumbing: hiring a star-power CISO, spinning up a round-the-clock SOC, layering EDRs like a cybersecurity baklava. And yes, that perimeter armor is essential and non-negotiable. But the human attack surface, the stuff attackers harvest from stray digital footprint, keeps getting a free pass.
These days, most companies sink real money into hardening the plumbing: hiring a star-power CISO, spinning up a round-the-clock SOC, layering EDRs like a cybersecurity baklava. And yes, that perimeter armor is essential and non-negotiable. But the human attack surface, the stuff attackers harvest from stray digital footprint, keeps getting a free pass.
Some of the biggest breaches on record started right here: the 2020 Twitter admin-panel hijack, Target’s 2013 POS meltdown, even Colonial Pipeline’s 2021 shutdown all kicked off with social-engineering bait crafted from public footprint intel. When an adversary already knows your help-desk script or your intern’s gamer-tag, forging a lethal phish is basically paint-by-numbers. To avoid this, try to cover with some measures:
Attack-Surface Mapping. Threat actors profile targets by scraping public info first. If you don’t know what’s out there, you can’t defend or disavow it.Brand &
Executive Protection. CEOs often leak more intel via their twenty-something girlfriend’s Instagram than through press releases. If you don’t believe me, have a chat with Pavel Durov.
Due Diligence & Hiring. Recruiters run silent footprint sweeps; so do VCs before wiring a cent. And they may find that old social media account where you posted some “not very nice” comments.
Litigation & Incident Response. A well-timed screenshot of an employee’s Telegram rant can nuke “we had no idea” as a legal defense.The bottom line:
digital-footprint investigation is OSINT’s pragmatic cousin—less cloak-and-dagger, more spreadsheet-and-strong-coffee.
The good news is you don’t need classified access—just curiosity, some knowledge and an internet connection. The bad news? you do need a plan, or you’ll drown in data. Here’s a simple playbook investigators can follow. Each point will be discussed in more detail later:
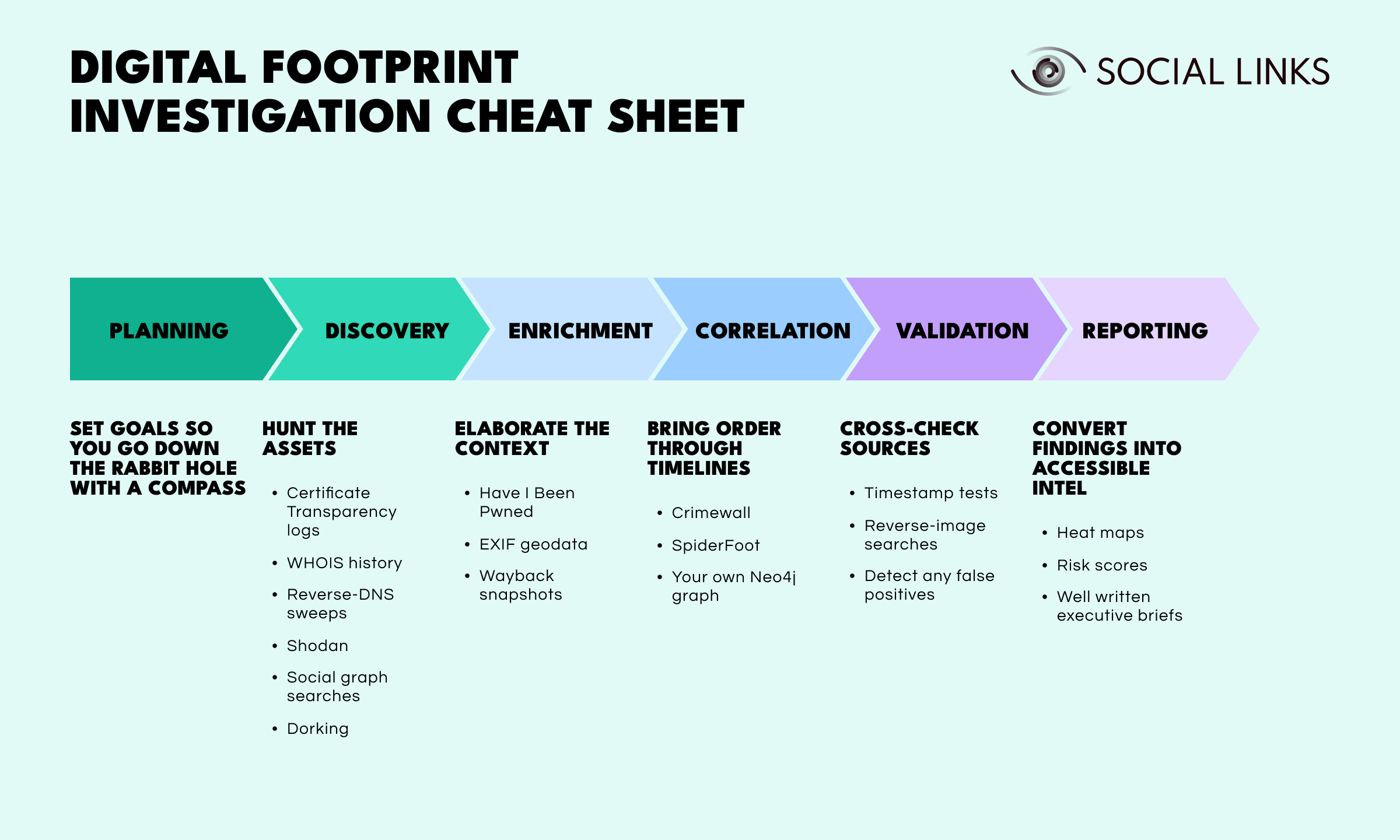
Social media are the loudest part of any digital footprint, but also the most volatile—stories vanish, usernames mutate, platforms die (RIP Vine). Pro tips:
Archive Fast. Use tools like Nitter (for X/Twitter) or InstaLoader to grab content before it’s scrubbed.Mind the Hashtags. They’re OSINT tripwires: they link events, communities, and sometimes geolocation data.Watch the comments. Often more revealing than the post itself: business emails, insider gripes, “DM me for quote” offers, links.
After collecting terabytes of crumbs, you must rank them. It’s a good idea to deploy:
Entity-resolution algorithms for merging duplicate identities (Jonathan Smith ≠ Jon Smith ≠ jsmith87).
Risk-scoring models for weighting sensitivity (PII, creds) against exposure (public vs semi-public).
Temporal analysis for spotting activity spikes—was that domain registered right before a phishing campaign?
Graph visualization for bringing hidden clusters and correlations to light.
When entity resolution and graphical mapping merge with deanonymization workflows, attribution becomes dramatically more precise. Anyone working with digital footprints in investigative contexts should understand how modern deanonymization is performed using metadata, blockchain traces, and cross-platform behavior mapping. For a deeper dive into these layered attribution methods, explore Advanced Deanonymization Techniques — it demonstrates how OSINT, crypto analytics, and behavioral profiling are fused to unmask real-world subjects at scale.
One-off audits age like milk. Online digital footprint tracking should be continuous, and include:
Monitored keywords on paste sites, dark-market chatter, code repos.
TLS/SSL watchers for sketchy cert registrations in your brand’s name.
Attack-surface-management (ASM) platforms that ping infra 24/7 and yell when someone spins up old-dev-test.prod.yikes.
Employee security awareness, remind staff every side project on GitHub is a potential breadcrumb.
Your digital-footprint investigation isn’t a one-time spa treatment; it’s dental hygiene for the internet age. Map it, monitor it, and keep a toothbrush (a.k.a. your OSINT toolkit) handy and updated.
Because on the web, the glitter never really disappears, it just moves to someplace you’re not looking. Blink, and that innocent sparkle could light the way for the next phish, dox, or headline-making leak.
Stay curious. Stay lawful. And for the love of opsec, check your privacy settings before that next celebratory post.
If you’d like to learn more about how Social Links industry-leading OSINT solutions can revolutionize your social media intelligence workflows, click the button below and we’ll set up a personalized demo for you with one of our specialists.