OSINT and Lawful Interception: Two Pillars of the Modern Investigation

There’s a common misconception that OSINT work encompasses eavesdropping into private communications, such as messages exchanged via WhatsApp or Instagram. The truth is that, while OSINT can be profoundly insightful, it is ultimately limited to publicly available data extracted from open sources, meaning that private conversations, including encrypted messages, lie beyond the reach of OSINT tools.
The access of private communications for investigative purposes requires legal authorization and goes by another name—lawful interception. And in this piece, we want to look at what this process is exactly, including how it differs from OSINT, but also how it is a crucial aspect of modern cases that complements open-source disciplines, and can be used in tandem to optimize the scope and reach of a given investigation.
In a nutshell, lawful Interception is when telecommunications companies or service providers provide authorized officials—such as law enforcement or intelligence agencies—access to specific communications. This process is totally legal and typically used in investigations involving—but not necessarily limited to—serious crimes, such as terrorism, child exploitation, or organized crime.
A typical workflow runs as follows. A warrant is issued, obliging service providers to hand over communications data to law enforcement agencies. Specialized systems are then employed to collect, store, and analyze this data. Through examination of the intercepted communications, investigators can gain valuable insights into a suspect’s network, which can progress a given case or embody evidence related to criminal activities.
A growing impediment to successful lawful interception is the shift in communication patterns away from traditional providers to encrypted messaging services, many of which operate outside the jurisdiction that the warrant is issued within, making it increasingly difficult for law enforcement to access the data they seek. Additionally, interception technology can sometimes be misused to carry out unauthorized surveillance—the “Greek Watergate” scandal being a case in point.
As communication technologies evolve, it’s essential that regulations governing lawful interception are suitably—and continually—modified to address these emerging challenges.
When lawfully intercepting communications tied to a given phone number, investigators can typically retrieve the following information:
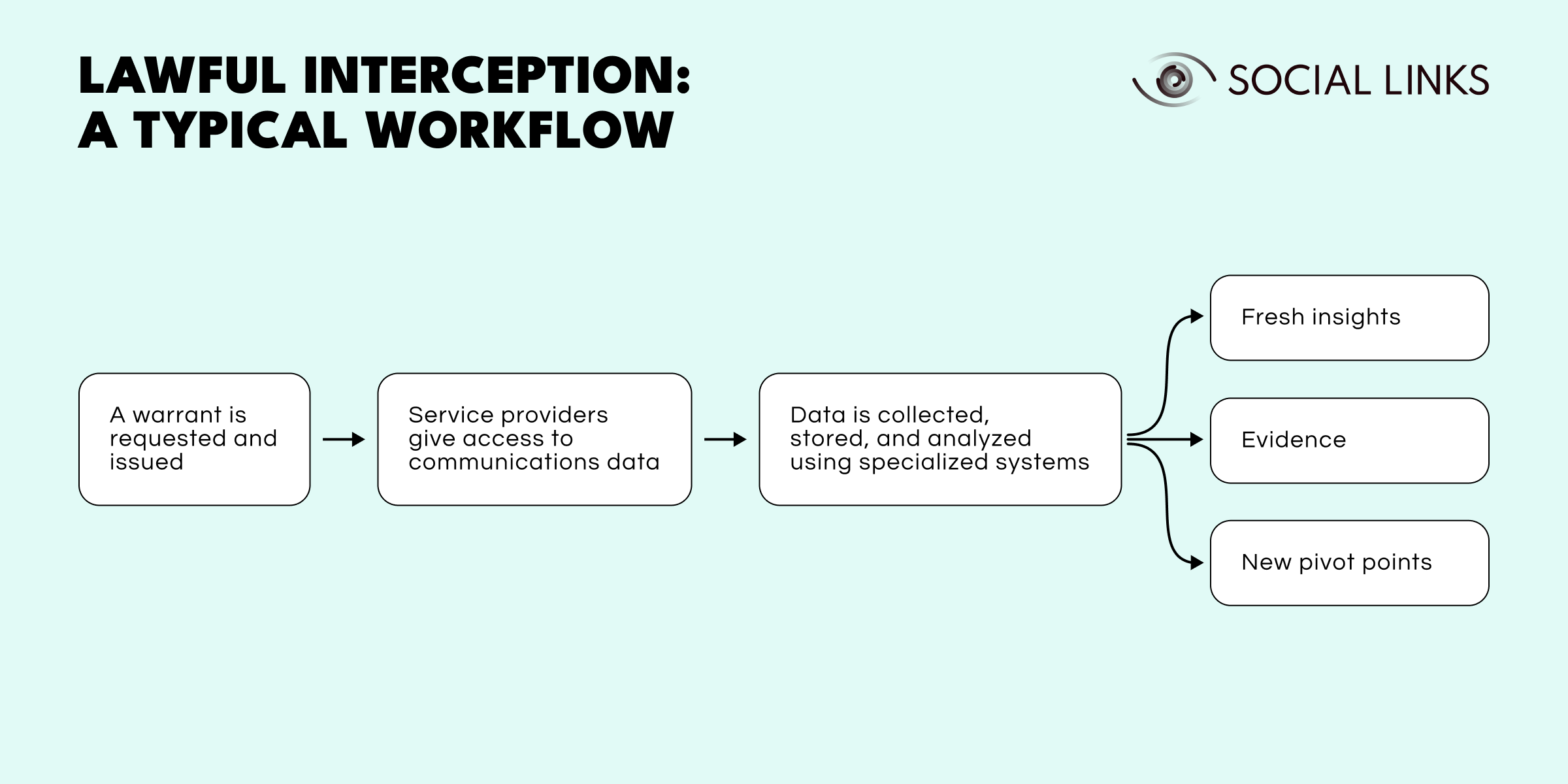
Lawful interception does not just involve a single approach—methods can be active, passive, or hybrid.
Active Interception. This approach can be thought of as cherry-picking the specific data that’s needed, and involves integrating interception capabilities directly into the network infrastructure. Network elements (such as routers and switches) are then controlled to pick out specific communication data, which is then sent to the monitoring center for analysis.
Passive Interception. This is a more hands-off method in which network elements send a copy of all network traffic to the interception system. The system then filters out irrelevant data, isolating the targeted communications before forwarding them to investigators.
Hybrid Interception. As the name suggests, this method combines elements of both active and passive interception, offering flexibility depending on the investigation's needs.
So, what does all of this imply about the relationship between OSINT and lawful interception in the context of investigation or intelligence processes?
OSINT and lawful interception are two components of LEA work that go together exceptionally well—far from cancelling each other out in terms of utility, they mutually boost the effectiveness of one another. By definition, there are things that can be identified with Lawful Interception that cannot be identified with OSINT, and vice versa.
While these processes naturally feed into one another and can overlap in terms of how they are deployed, they strikingly excel at different stages of the intelligence cycle, giving investigators very strong disciplines to tackle different challenges.
The importance of OSINT approaches tends to increase the more a given case develops in complexity, meaning the discipline (and its subdisciplines) take on more significant scope and power at the analytical stages of the process. Meanwhile, lawful interception can be seen as offering unique opportunities for making incisive headway at the extraction stages of an investigation.
In just the last decade—or even five years—we’ve seen a dramatic proliferation in the types of information out in the digital realm that tie into, and have a significant bearing on, OSINT work. As new forms of open-source data continually emerge, so new, logical pivot points between such data take shape across the technological landscape.
In this climate, forward-thinking investigators and intelligence officers will understand that lawful interception is not merely an isolated forensic weapon to be wheeled out for this or that case, but one part of an entire tapestry of disciplines for dealing with—and tapping into—the ever-evolving informational space.