OSINT Investigations: Back to Basics


Open-Source Intelligence has become an invaluable tool for countless professionals across a range of industries. Whether it’s law enforcement tracking criminal networks, cybersecurity experts hunting for network vulnerabilities, compliance teams performing due diligence, or companies protecting their brand, OSINT provides a versatile and accessible way to solve complex problems in today’s information-driven world.
So in this article, we wanted to take a broader look at the core principles and methods that drive effective OSINT investigations. Whether you’re just starting out or more experienced but looking to adopt some proven approaches, this article will help you plan and execute investigations effectively, and tap into key data sources to turn unstructured data into actionable insights.
An OSINT investigation isn’t just about finding data—it’s about finding the right data, and processing it efficiently and accurately, so it can make a real difference. By following a clear process, you can systematically gather data, process it into structured information, and then analyze it to obtain actionable intelligence that answers critical questions or solves specific problems.
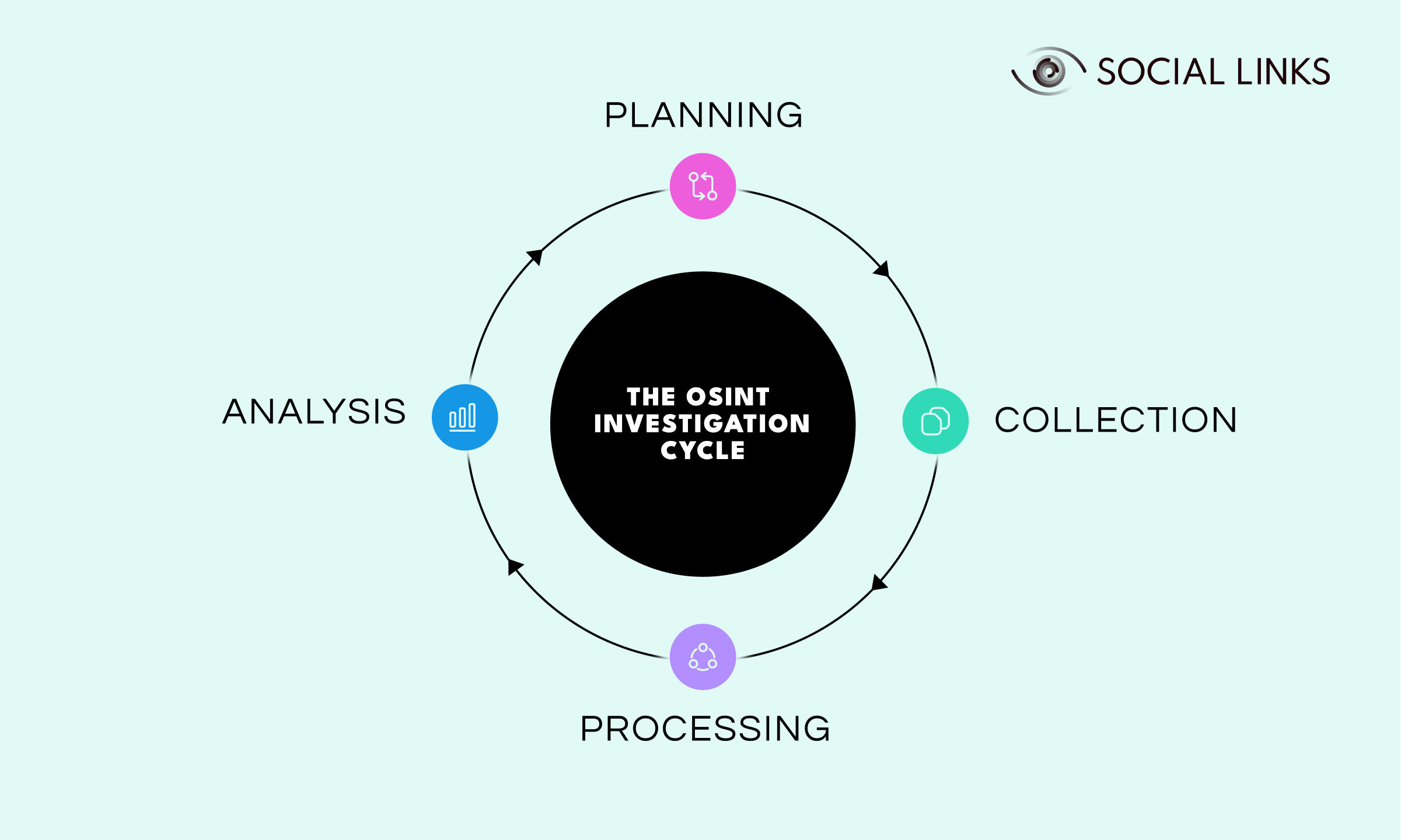
Here’s a closer look at the key methodological aspects of an OSINT investigation:
Every open-source intelligence investigation that can be characterised as "complex" or "multi-component" starts with a strategy, and effective strategies are predicated on clear thinking. This means you need to precisely define what you want to achieve—are you trying to establish connections between organizations, trace the movements of a given individual, or something broader like finding out where public opinion lies on a given topic?
Once you’ve established your overarching goal, think about the component steps and objectives that can feasibly pave the way to this end point. Ask yourself: What data sources are likely to be most relevant for the research? What type of data within those sources are most pertinent? What extraction approaches will help in getting at that information in the most direct and hassle-free way?
Properly formulating goals at the start, and eliminating those that are extraneous, are crucial to streamlining your workflow—a clear objective and roadmap will not only keep you focused but also help you avoid getting distracted or wasting time on details that don’t actually have a bearing on your core goal.
With your plan in hand, it’s time to get stuck into the actual data. This could encompass all manner of sources and extraction processes. Modern OSINT solutions such as SL Crimewall offer an expansive suite of extraction tools that work with a wide range of data sources—the trick is knowing which ones most suit your purposes and deploying them in the context of a planned approach.
Advanced AI-driven features such as facial recognition or sentiment analysis may be crucial when dealing with vast data sets or seeking aggregated results, but precise extraction methods deployed manually may be most incisive in unearthing a specific detail of a given individual. Just as focusing a lens will give you a clearer photograph, being selective and judicious in your extraction will give you a clearer informational picture to work with.
Of course, merely collecting data is only part of the battle. Raw information, no matter how much you have, is unlikely to help you until it’s been coherently structured and organized. When we talk of “processing” data in an OSINT context, we really mean shaping it into the form that serves your analytical purposes.
There is no single approach or tool for arriving at a comprehensible picture from the unstructured data—it entirely depends on your objectives, which could prescribe anything from searching for patterns or establishing relationships to spotting anomalies or identifying a single connection. There are any number of ways to approach a given case, and discussing each is beyond the scope of this article, but you can check out some of our articles here for some detailed examples.
Naturally, a hugely important factor—the driving force behind any investigation—is how you elect to use the data you have extracted and processed. There are a plethora of methodologies spanning this subject but these can be distilled into a basic guiding principle, chiefly: How can your findings effectively inform and influence your next steps?
Maybe you have your route to the data you need meticulously planned out, but if that route is frustrated, you will need to seek workarounds—it can often happen that the emergence of certain details indicate that you need to pivot entirely from your original vision. At the same time, the nugget of information that breaks a case wide open may be an innocuous detail from a niche source that could have been easily overlooked.
The effective investigator keeps their eyes open to relevant developments and follows those leads and hints that can illuminate a path to their end goals. Ultimately, judicious analysis not only informs but also empowers decision-making, whether it involves changing a strategy, solving a problem, or reaching a reliable conclusion.
When it comes to OSINT investigations, finding reliable and relevant data is essential. Your ability to access diverse sources of data determines how effectively you can uncover insights about people, organizations, or events. From social media to corporate registers, each source has its unique benefits. So here’s a breakdown of the most commonly used OSINT sources and why they’re valuable.
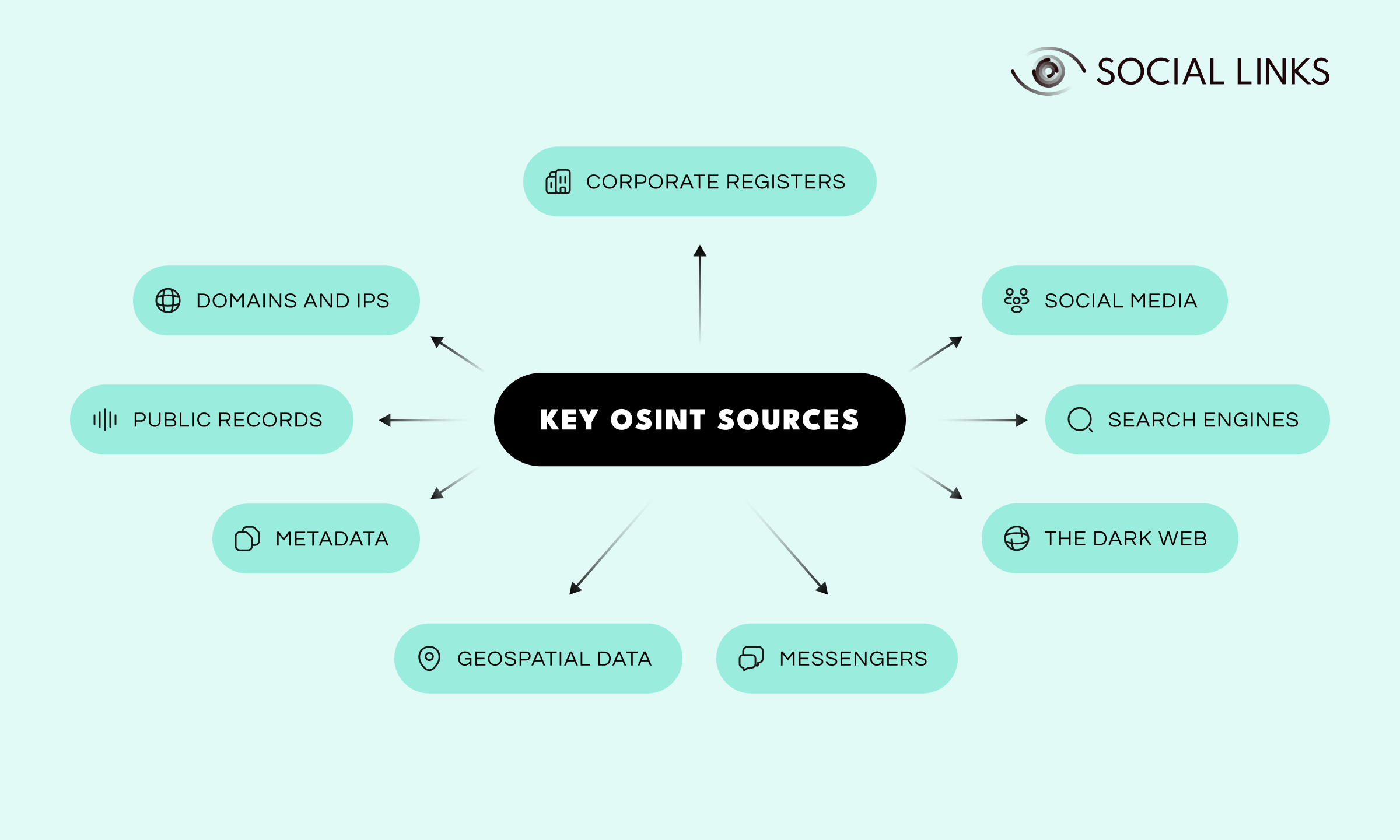
Networking platforms such as X, Reddit, LinkedIn, and many more, are goldmines of publicly available data, which can be analyzed to establish connections between individuals and groups, monitor conversations, study behavioral patterns, and uncover connections between individuals or groups. Posts, comments, tags, likes, check-ins, and so on can reveal a wealth of insights into a subject’s locations, connections, opinions, as well as broader network structures and public sentiment.
Public or semi-public groups on messaging apps like Telegram and Discord are rich with real-time discussions and shared content. These platforms can be studied to identify trends, analyze group dynamics, and gather intelligence on specific communities, and critically, to deanonymize target users.
With a lot of murky activity gravitating to this heavily encrypted domain, the Dark Web is often a crucial hunting ground for the OSINT specialist. By exploring different forums, marketplaces, paste sites, and alternative social media, investigators can uncover data leaks, discussions of illicit activities, illegal product listings, and much more.
Government databases, court filings, property records, and other registries contain verified information essential for tracing histories, confirming identities, or validating claims. These resources are key to building timelines, identifying connections, and uncovering legal or financial details.
Databases that document business operations hold critical company details such as ownership structures, financial filings, and stakeholder relationships. Such records are vital for mapping corporate networks, conducting due diligence, and uncovering ties between organizations.
Hidden data embedded in media files, images, and documents—timestamps, geolocation, and device information, etc.—can be extracted to valuable effect. By extracting timestamps, geodata, and other details, investigators can gain significant insights into the authenticity, origins, or context of a given piece of media.
Analyzing photos, videos, and other digital content can reveal or confirm locations. Techniques include studying landmarks or contextual clues to verify claims, track movements, or cross-check information.
Investigating websites and email addresses often starts with domain and IP lookups. These can provide details about ownership, hosting providers, and linked infrastructure, helping to trace origins, or uncover relationships between entities.
However you employ OSINT in your work, we hope that this overview will give you some fruitful guidance and successful results. If you’d like to learn more about our flagship solution SL Crimewall, and how it can greatly facilitate your investigative work, follow the link below and we’ll set up a personalized product demonstration for you.