Risk Assessment for Cyber Security: Aligning Security with Strategy


Cybersecurity risk now extends far beyond IT environments. It directly affects business operations, regulatory compliance, data protection, and institutional resilience. As organizations rely more heavily on cloud infrastructure, interconnected systems, and digital workflows, a single vulnerability can translate into operational disruption, financial loss, or reputational damage. A structured risk assessment for cyber security enables organizations to understand exposure, evaluate credible threat impact, and prioritize risks that require immediate attention.
In this article, we explore how cyber risk assessment supports cybersecurity risk management, how the assessment process identifies vulnerabilities and credible threat scenarios, and how security teams use structured analysis to strengthen security posture, protect sensitive data, and support informed, risk-based decision-making.
A risk assessment is a structured analytical process used to identify threats, evaluate vulnerabilities, and estimate the potential impact of cyber incidents on systems, sensitive data, and business operations. Its objective is not to produce a checklist of technical issues, but to deliver a prioritized and operationally relevant view of organizational exposure.
A comprehensive security risk assessment focuses on three core dimensions:
This model grounds analysis in real-world conditions rather than theoretical worst-case scenarios. Unlike static audits, assessments must be continuous. Infrastructure evolves, vulnerabilities emerge, and threat actors adapt—risk visibility must evolve accordingly to remain decision-relevant.
Organizations collect vast amounts of security data, yet visibility alone does not improve resilience. Without a structured evaluation process, security teams often address low-impact weaknesses while high-impact exposures affecting sensitive data and operational continuity remain unresolved.
A well-executed cyber risk assessment enables organizations to:
More importantly, it connects information security activities to operational priorities. When risk levels are clearly defined, leadership can allocate resources, approve mitigation plans, and align cybersecurity initiatives with strategic objectives. Without this linkage, assessments become documentation exercises rather than operational guidance.
Most organizations perform assessments. The distinction lies in how the findings are used.
In compliance-driven environments, assessments are periodic, heavily documented, and archived for audit purposes. Reports satisfy regulatory requirements, yet infrastructure decisions, budgets, and security operations continue unchanged. In this model, assessment becomes a reporting function rather than a strategic input.
In risk-informed environments, the same analysis functions as decision intelligence. Findings directly influence security investment, architecture design, and incident response planning. Cloud configurations, identity controls, and network segmentation are shaped by documented exposure rather than assumptions. This shift closes the gap between analysis and action and embeds cyber risk assessment into core governance processes.
Effective evaluation is built on interconnected pillars that transform fragmented technical data into actionable insight.
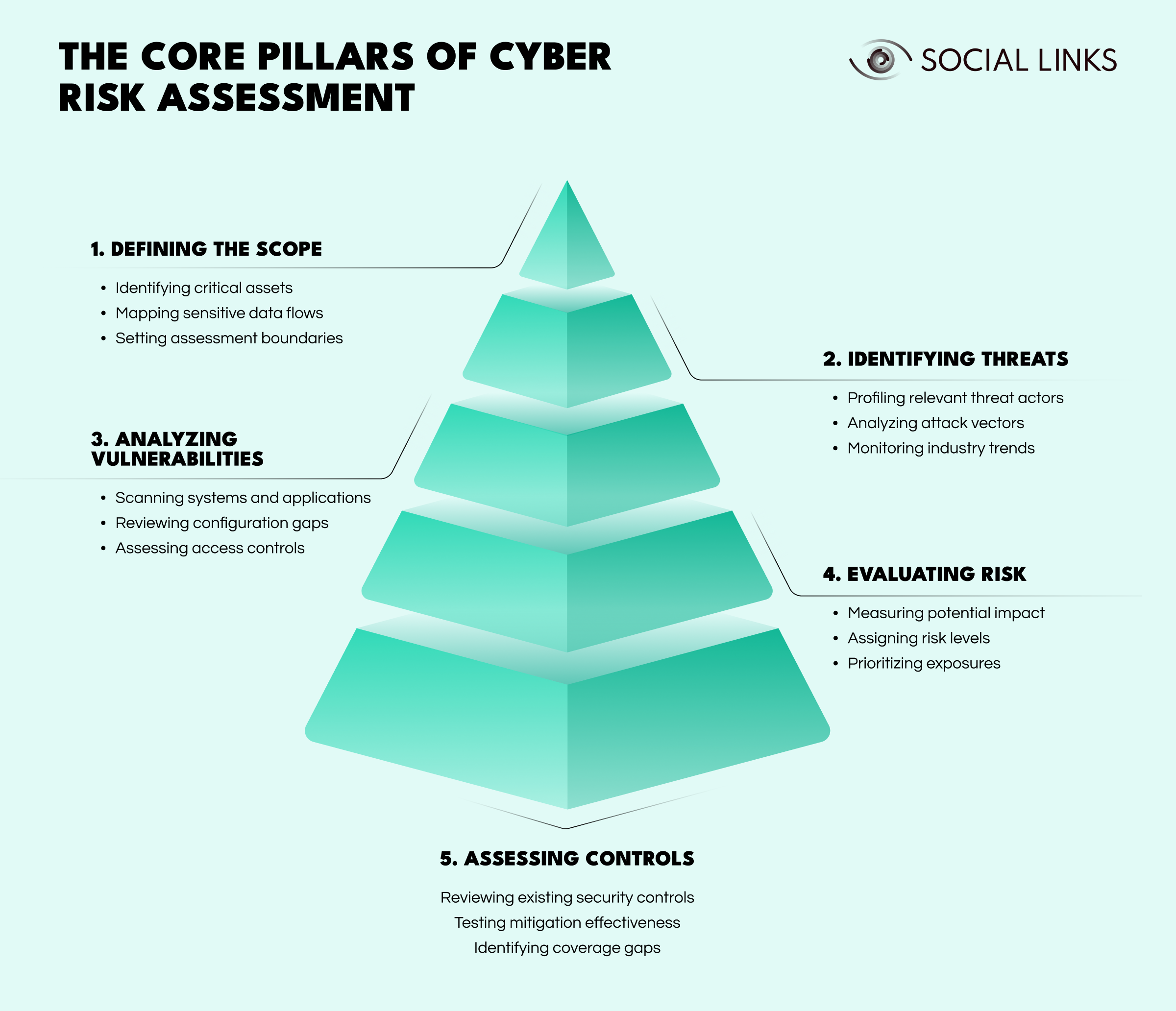
The process begins by establishing clear boundaries across infrastructure, applications, third-party systems, and data environments. This includes identifying critical assets, mapping sensitive data flows, and understanding operational dependencies. Poorly defined scope leads to blind spots, especially around high-value systems that support core business operations.
Threat identification involves profiling relevant adversaries and credible attack vectors, including cybercriminal groups, insider threats, supply chain compromises, and opportunistic attackers. Aligning analysis with documented threat behavior ensures the assessment reflects realistic exposure rather than hypothetical scenarios.
This stage evaluates technical and procedural weaknesses across cloud, on-premise, and hybrid environments. It includes configuration reviews, access control analysis, and exposure mapping. A weakness only becomes a material risk when it intersects with a capable threat actor and a valuable target.
Risk evaluation combines likelihood and impact to assign meaningful priority. For example, a misconfigured cloud storage environment containing sensitive data presents both high operational impact and high likelihood due to automated threat scanning.
Conversely, an isolated internal system may carry technical severity but lower operational risk.
This risk-based approach ensures remediation is aligned with business consequences rather than technical scoring alone.
A comprehensive assessment also evaluates whether existing security controls effectively mitigate identified threats. This includes detection capabilities, identity governance, incident response readiness, and preventive safeguards.
Control validation ensures defenses reduce actual exposure rather than creating a false sense of security.
Established frameworks provide structure and consistency for performing a cybersecurity risk assessment within governance and compliance environments.
The NIST Cybersecurity Framework organizes activities into five core functions: Identify, Protect, Detect, Respond, and Recover. Within this model, assessment plays a central role in defining exposure and guiding control implementation across the security lifecycle.
NIST SP 800-30 provides formal methodology for threat identification, vulnerability analysis, and impact evaluation, emphasizing that assessment should support organizational decision-making rather than exist as standalone documentation.
ISO/IEC 27001 integrates security risk assessment into information security management systems, requiring continuous evaluation of risk and documented treatment strategies.
Collectively, these standards position assessment as a governance function, not merely a technical exercise.
Despite differences in infrastructure and sector, several recurring risk scenarios appear across organizations.
Ransomware continues to target operational systems and disrupt business continuity.
Credential-based attacks enable lateral movement through legitimate accounts, often bypassing traditional defenses.
Cloud misconfigurations frequently expose sensitive data due to overly permissive access policies.
Supply chain dependencies introduce indirect exposure through third-party software, vendors, and integrated services.
Understanding these patterns allows security teams to prioritize mitigation based on realistic threat landscapes rather than generic vulnerability lists.
A risk assessment for cyber security is not a compliance formality or a technical checklist. It is a structured decision-support process that converts fragmented security data into prioritized, operational intelligence.
When embedded into cybersecurity risk management, assessment enables organizations to move from reactive incident response to proactive risk reduction. By evaluating threats, vulnerabilities, and security controls together, decision-makers gain a clearer view of organizational exposure—supporting actions that protect sensitive data, ensure regulatory compliance, and maintain operational continuity.
A risk assessment for cyber security identifies threats, vulnerabilities, and potential impacts affecting digital systems and operations. It helps organizations prioritize mitigation efforts and improve security posture by focusing on risks that have real operational and business consequences.
A cyber risk assessment focuses specifically on digital infrastructure and information security risks, while a broader security risk assessment may include physical, operational, and organizational threats alongside cybersecurity considerations.
At minimum, organizations should conduct assessments annually, with additional reviews after major infrastructure changes, incidents, or significant shifts in the threat landscape. Continuous monitoring further improves risk visibility.
Widely used frameworks include the NIST Cybersecurity Framework, NIST SP 800-30, and ISO/IEC 27001. These provide structured methodologies for identifying vulnerabilities, evaluating risk levels, and aligning security controls with governance requirements.
Cyber security risk management is the ongoing process of identifying, analyzing, prioritizing, and mitigating cybersecurity risk to protect sensitive data, systems, and business operations through continuous monitoring and strategic decision-making.
Want to see how structured intelligence platforms support cyber risk assessment and security posture analysis in complex environments? Book a personalized demo with one of our specialists and discover how SL Crimewall helps security teams identify vulnerabilities, correlate multi-source data, and prioritize cybersecurity risk through a unified, compliant analytical workflow.