What is OSINT (Open-Source Intelligence) in 2025?

It’s a pillar of the modern intelligence cycle, taken very seriously by the national security departments of leading global powers, and is entering the mainstream in various ways. But what exactly is OSINT (open-source intelligence) in 2025?
The truth is that open-source intelligence encompasses a lot, but don’t worry—we’re here to unpack everything. In this article, we’ve broken down the OSINT puzzle into commonly asked questions to cover the most need-to-know basics of the discipline.
So read on and come away with a firm grasp of OSINT!
OSINT, an acronym standing for ‘open-source intelligence,’ refers to the process of extracting, processing, and analyzing data from publicly available sources to generate actionable intelligence. In simple terms, OSINT means information collected from the Internet.
The data derived through open-source intelligence gathering spans a range of formats including text, images, geolocations, videos, speech patterns, etc, and may be used for various investigative purposes, including risk mitigation, data leak detection, digital footprinting, fraud detection, criminal deanonymization, and many more.
Publicly available data is unstructured and truly vast. This means that OSINT practitioners depend heavily on open-source intelligence gathering tools, in order to extract and analyze such data, and ultimately to process the raw information found in OSINT source to generate actionable insights.
Yes, open-source intelligence is legal. As more and more individuals and organizations willingly share their information, the volume of available data for OSINT only continues to grow.
Moreover, information taken from publicly available sources is initially in the public domain and is literally accessible to anyone on the Internet. Hence, OSINT doesn't break legal rules or policies.
These are the online places from which open data is taken. The range and scope of such sources are dizzying and may reach way beyond what people imagine. Here’s a breakdown of some of the most crucial kinds of open sources that OSINT practitioners rely on:
Colossal amounts of open data pour daily into platforms such as TikTok, LinkedIn, X/Twitter, or YouTube. Every tag, like, post, comment, friend, follower, followee, etc., contribute to this ocean of data, which can be harnessed for an incredible range of purposes.
Apps such as Telegram are home to many open groups whose contents are open data. This means the usernames and profiles connected to the comments are also open data. Identifying such connections can often be extremely important in open-source intelligence work.
Much intelligence work is connected to the movement of money, and the perceived anonymity offered by cryptocurrencies means that underhand transactions tend to gravitate to such methods. Yet, blockchains are essentially open data, meaning that they can be hugely informative for investigative work with the correct tools and techniques.
With many illicit activities drawn to the Dark Web's recesses, this domain's sources are crucial to many investigations. They're often perceived as closed platforms but available for all eyes with specific tools (like TOR). Darknet sources that draw much attention from OSINT workers are marketplaces, alternative social media, paste sites, and forums.
Of course, any information in the public domain will also qualify as open data, including news and magazine articles, research papers, telephone directories, court filings, public trading data, public surveys, domain registration data, open corporate databases, and so on.

Let's first mention that in daily life, anyone with access to the Internet might use open-source intelligence. Even when we search for someone on LinkedIn, read a review on some restaurant, or check friends lists to establish if two people are somehow connected, we're in the OSINT domain.
However, some sectors regularly use data from OSINT to contribute to global safety:

Like any form of intelligence gathering, open-source intelligence has its own share of challenges that can make the process demanding:
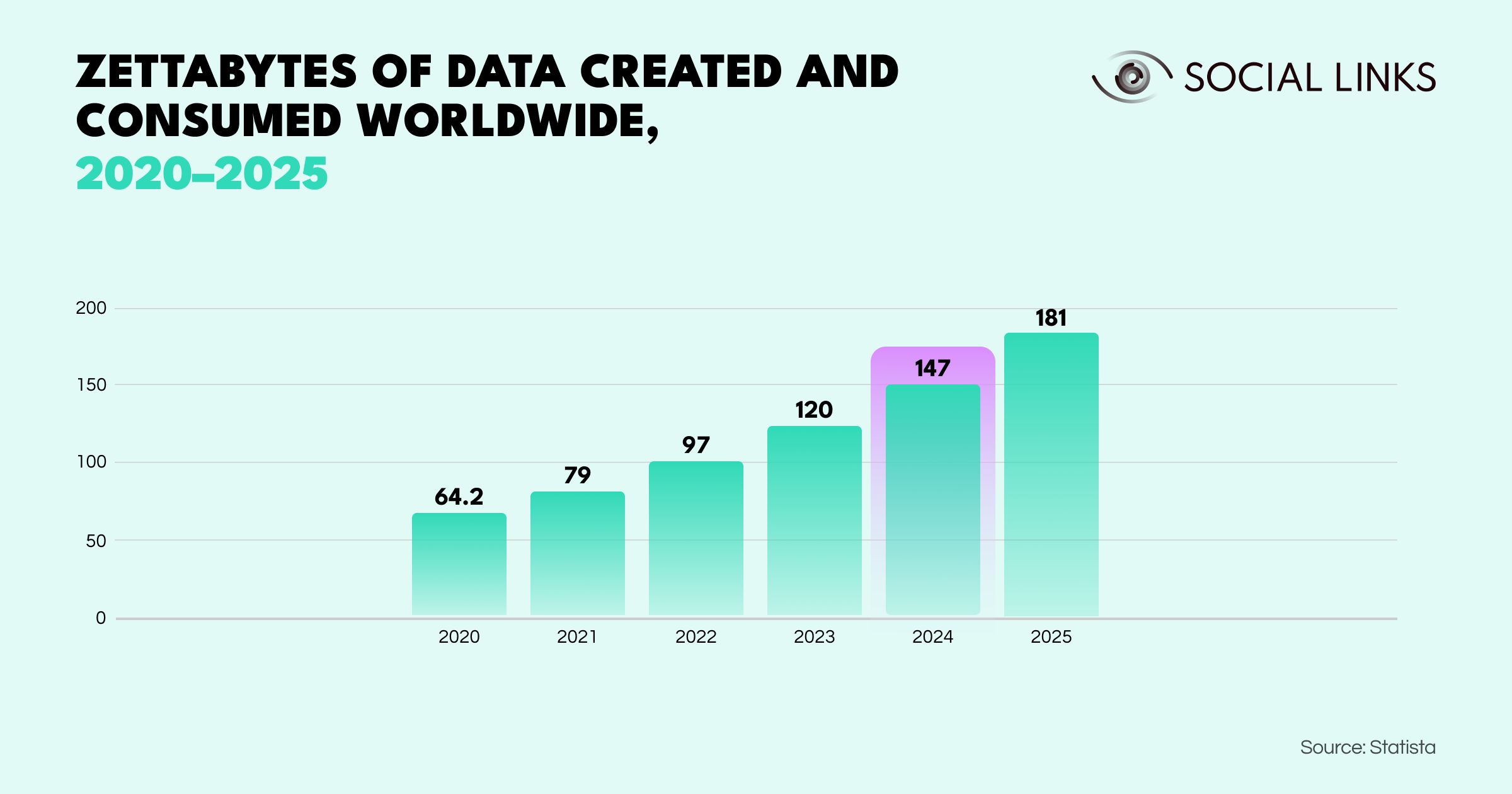
The Internet's data volume is currently around 147 zettabytes. So, the question is: how to generate quality, actionable intelligence out of such oceans of unstructured data? Due to a vast suite of specialized extraction and analysis methods, advanced OSINT tools can dramatically streamline the intelligence cycle. Using AI (artificial intelligence) in combination with ML-driven search features, investigators can gain accurate results in a fraction of the time that wouldn't be possible through manual search.
Although the value that open data can bring to various spheres can’t be denied, what is less clear is the practical side of how such data is used to its best advantage. Data analytics is broadly understood as a technical discipline. Meanwhile, the tools designed to aid the process are often highly complex and require significant training. The reality is that OSINT is also crucial for many who are not IT specialists—police investigators, for example—and these users, the technical leap required to use the tools can be a serious hurdle to realizing open data value.
Data is pouring into the online space at an astonishing rate, with publishing origins continually buried or too numerous to keep track of. In the disinformation age, information can often be misleading by design, but even the one that initially had veracity can quickly become outdated and inaccurate. This is a big issue because when research is based on erroneous data, the results and conclusions themselves are bound to be wide of the mark and ultimately less useful—potentially even counterproductive.
There are certainly many OSINT tools on the market, each with its own purposes and operating style. Here are some of them:

This is a full-cycle OSINT investigation platform that simplifies the entire intelligence cycle, from data extraction across 500+ open sources, through visualization and processing, to the final report. The solution is accessible to users of all levels, from beginners to experts. Its collaborative interface lets users work on cases together. Additionally, SL Crimewall is packed with next-generation extraction and analysis methods, has monitoring capabilities, and easy-to-create reports.
One of the longest-standing intelligence solutions on the market, i2 is definitely worthy of a place on our list of top OSINT tools in 2025. The software consists of an advanced data visualization portfolio, allowing users to manipulate volumes of data into actionable intelligence. The tool empowers users to identify, predict, and mitigate various criminal activities.
Specializing in providing full visibility around counterparties and supply chains, Sayari is the king of due diligence-centered OSINT tools. The company’s analysis solution, Sayari Graph, is an intelligence platform for determining commercial risk. It combines supply chain and corporate data, entity graphing, and intuitive risk identification functions to streamline investigations and due diligence processes.
Here are common methods investigators can employ using open-source intelligence tools to get the results that they want:
The extraction process refers to how this information is filtered out or isolated for further analysis. To do this effectively, investigators need precise search functions (or transforms), enabling them to zero in on the specific data and filter away the rest. The more transforms an OSINT solution offers, the more accurately users can access the information they’re after. For example, SL Crimewall is packed with 1700 ready-made transforms covering over 500 sources.
Link analysis is a process of organizing data as points on a graph interconnected by vertices. The data points could be anything from an email address or comment on social media to a geolocation or cryptocurrency wallet. Using OSINT tools, investigators can map the activities of large-scale criminal operations. This is possible because connections can be established on many levels, linking individuals, groups, organizations, incidents, and activities.
Criminal investigations often hinge on open-source intelligence methods of profiling and link analysis. By combining an individual's interests, connections, affiliations, and modes of interaction, a detailed picture of the subject emerges. Such pictures are digital footprints—digital impressions of a person's behavior that can be used to verify or falsify assertions or identities and embody evidence.
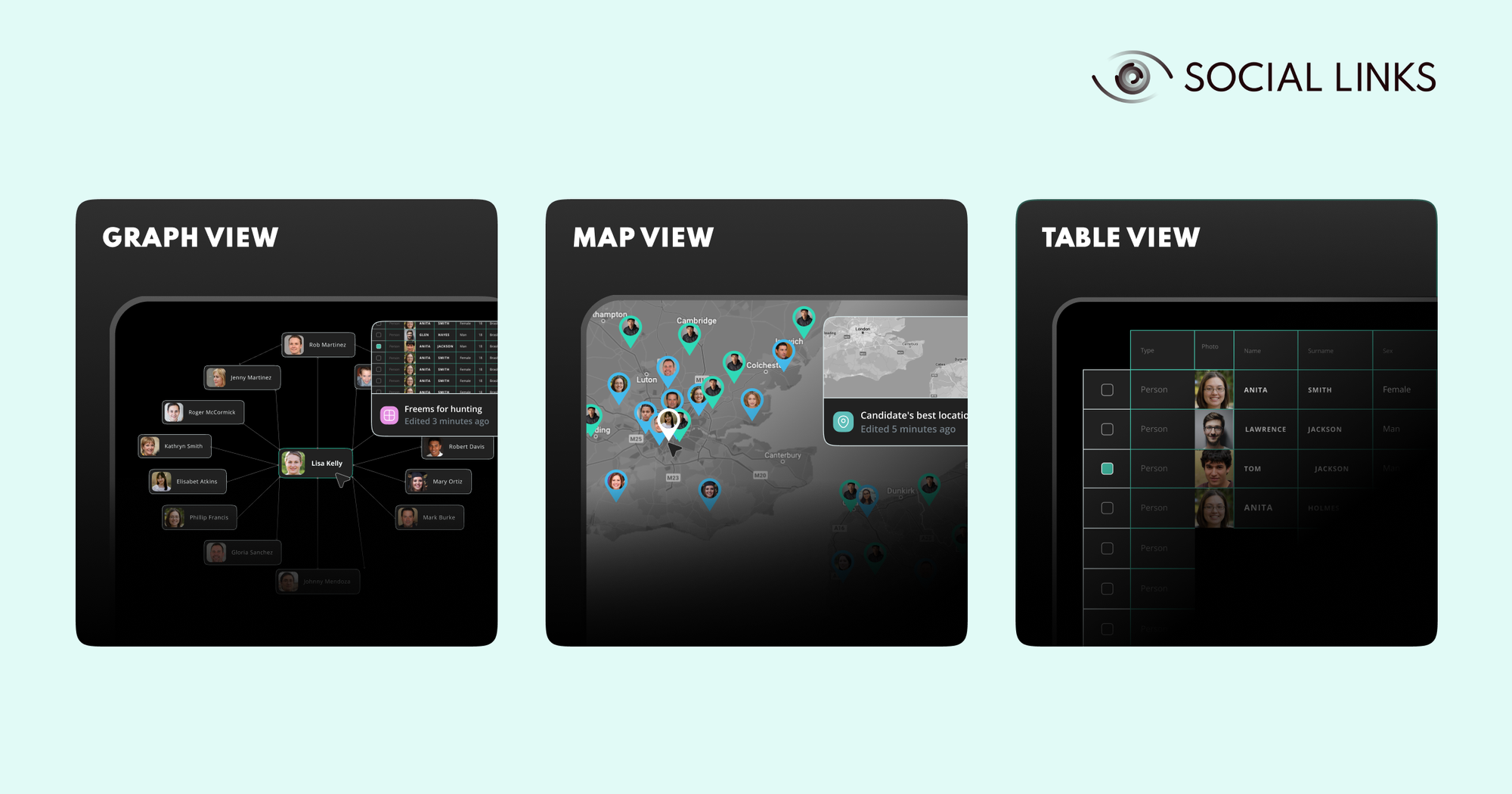
Once you’ve gathered the information you need, you have to find a way to process and analyze it. Here's where the visualization becomes a helping hand. One of its popular realizations is a link analysis that manipulates extensive network structures intuitively and visually. This often allows crucial patterns to emerge and valuable conclusions to be drawn.
While data graphs are a hugely popular visual aid for conducting good data analytics, they are by no means the only one—and depending on the user’s goals, a different form of visualization may be better.
While a lot of data pertains to textual content, it is often crucial to collect information of an image-based nature. It is no surprise that trained algorithms are much more effective at finding such content in the online realm than the human eye. This is where analysts tend to employ AI and ML-driven tools.
A researcher may use an image as an input to find copies or analogs in the open data space. This type of reverse search is often used for facial recognition—i.e., you start with a photo of a person and find out where other subject images appear online (like social media profiles and posts). Alternatively, you can input data as a keyword or phrase and discover relevant images and their source.

With more spheres beginning to understand the value of open data and new technologies driving development, the world of OSINT solutions is evolving quickly and diversely. Let us leave you with a few extracts to think about:
Where will OSINT spread next? Our hunch—the realm of mobile apps. Apps and services such as Clubhouse, Strava, and Spotify offer a mine of untapped open data. Meanwhile, ever more lifestyle apps are continually appearing on the market. Mobile app usage is bound to become part of the average digital footprint, and OSINT vendors will need to provide this data.
The gaming demographic is enormous, with 3.2 billion players worldwide. It is also home to extremist recruitment, financial fraud, and money laundering. The immense volumes of data generated by the gaming sphere all represent useful material for the analyst. Soon, gaming platform analytics will become an essential feature of open-source intelligence solutions.
Leaks containing biometric information, such as facial recognition data, could pave the way for more advanced forms of OSINT investigation. Among the various facial recognition systems, the most efficient now have an accuracy rate of over 98%. These are impressive results, and OSINT systems will doubtless be under commercial pressure to incorporate algorithms matching such accuracy.