Advanced Deanonymization Techniques for Law Enforcement and CTI


In today's digital landscape, anonymization is the threat actor’s cloak when carrying out illicit activities. For law enforcement agencies and cyber threat intelligence professionals alike, uncovering the real identities behind pseudonyms has become vital. But while many masks may seem airtight, with the right techniques, chinks can be found in almost any armour.
So in this article, we’re exploring five advanced user deanonymization approaches used by investigators today, including how they work in practice, and what to consider when applying them in the field. On top of this, we’ll look at some legal boundaries, adversarial countermeasures, and where this evolving field is heading.
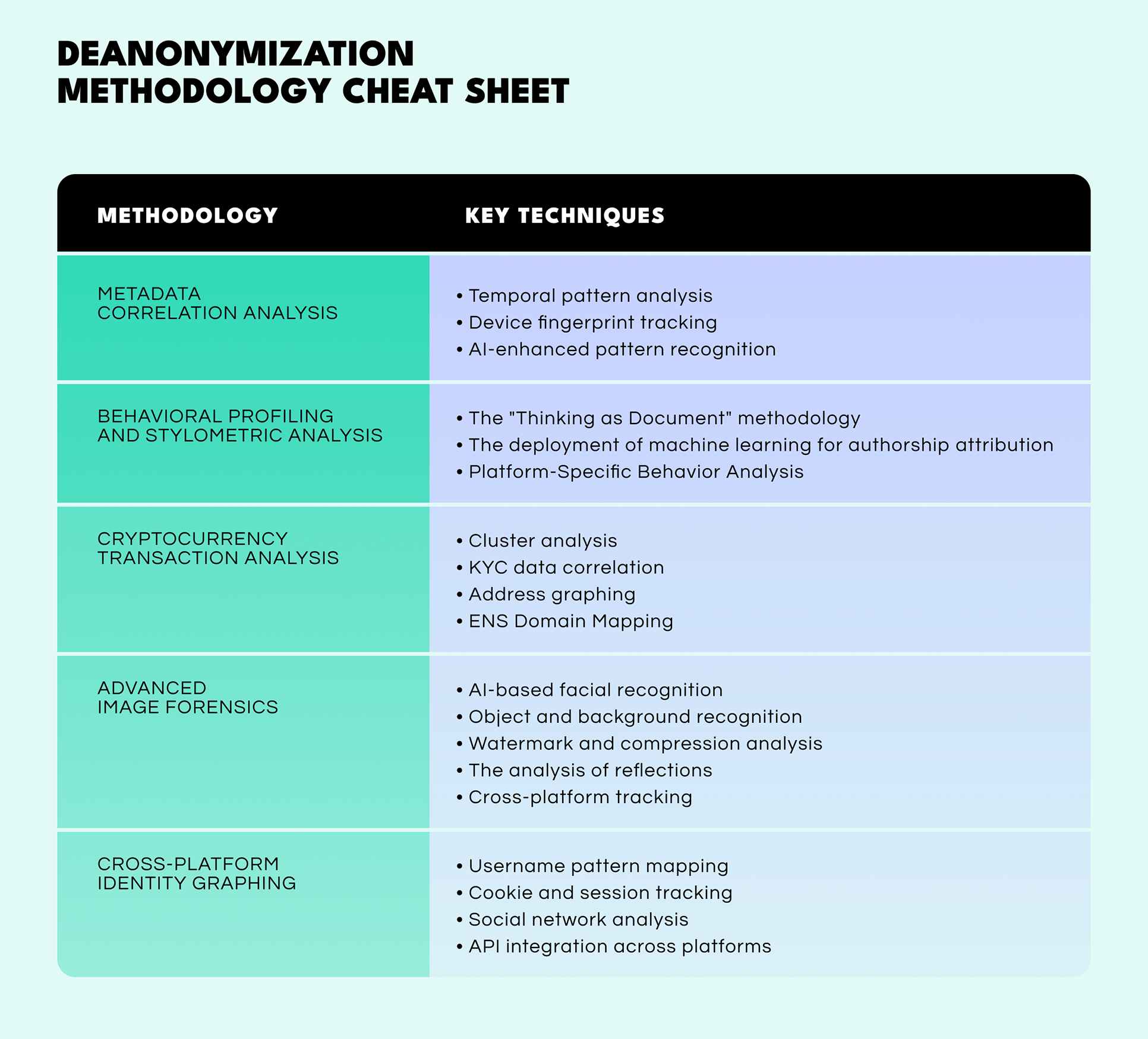
This is a crucial user deanonymization approach that involves systematically collecting and analyzing metadata across multiple platforms and timeframes, and has proven highly effective in a number of high-profile cases.
Key techniques:
Bear in mind: These cyber investigation techniques work best when applied over extended periods and alongside other intelligence sources. They’re especially useful when direct personally identifiable information like usernames or IPs are obscured.
User behavior leaves distinctive patterns that can be as unique as fingerprints. Stylometric analysis—the examination of writing style, vocabulary choice, and communication patterns—enables identification across different platforms even when traditional identifiers are absent.
Key techniques:
Bear in mind: This method is most effective when applied to rich datasets with a clear baseline for comparison. It works particularly well when integrated into NLP pipelines that automate the identification process.
When combined with reverse image search, forensic analysis produces exponentially stronger attribution results, especially in darknet or cyber investigations. If you work with visual content at scale, learn how reverse image search is applied as a standard OSINT methodology across law enforcement, media verification, and intelligence teams in Reverse Image Search: A Proven OSINT Technique.
Despite their reputation for privacy, blockchains ultimately have a transparent nature that provide unique opportunities for deanonymization. According to Arkham Research, up to 72% of Bitcoin wallets can be deanonymized within three hops using their Ultra engine.
Key techniques:
Bear in mind: This approach requires blockchain expertise and works best when combined with off-chain intelligence. It’s particularly useful for financial crime and Dark Web deanonymization.
Modern image analysis goes far beyond basic EXIF data extraction, incorporating machine learning and pattern recognition to establish connections between seemingly unrelated visual content.
Key techniques:
Bear in mind: This field demands trained analysts and powerful software, but the payoff can be high, especially when combined with other methods.
This holistic approach creates a comprehensive picture connecting various aspects of digital exhaust across multiple platforms, often revealing connections that would be impossible to detect when examining individual platforms in isolation. It’s next-level digital footprint analysis.
Key techniques:
Bear in mind: This approach benefits greatly from automation and a robust data architecture. It goes beyond simply naming individuals, helping build a full intelligence picture.
As both a product vendor and professional services provider in the Open-Source Intelligence (OSINT) space, Social Links has extensive experience implementing these deanonymization approaches across various use cases, yielding some key insights:
Individual techniques rarely provide conclusive identification on their own. The most successful deanonymization operations integrate multiple approaches within a unified analytical framework.
While AI and machine learning significantly enhance processing capabilities, human analysis remains essential for contextual understanding and validation of potential matches.
Deanonymization is rarely a one-step process. Our most successful implementations involve iterative cycles of data gathering, analysis, and refinement.
Threat actors are getting smarter—and they're not playing by the rules. To stay under the radar, most of them now employ a range of techniques designed to deceive investigators. Knowing how those methods work is half the battle.
Tor + Privacy Coins. The majority of criminals use the Tor network in combination with privacy-first currencies like Monero to conceal their traffic as well as transactions.
Virtual Machine Isolation. Others go a step further in setting up isolated virtual machines, each with its own environment and hardware security keys, to keep their activity and identities separated.
Metadata Scrubbing. Before and after communication, files and messages are usually scrubbed of metadata in a bid to delete identifying traces.
Platform Compartmentalization. Sophisticated actors compartmentalize their behavior across different platforms and personas, too. But with the right tools, it's still possible to cobble these parts together into a coherent identity.
Deanonymization isn't just about what's technologically feasible—it's about doing it ethically. All investigations must conform to clear legal frameworks and ethical standards.
Local Authorisation. Depending on the country, additional authorisations may be necessary to collect and analyze specific types of information.
Evidence Handling. Proper chain of custody is essential if results are ever likely to stand up to scrutiny in court.
Transparent Methodologies. Investigators should be willing to document their process clearly so that all they do will be subject to independent examination and defence.
With more advanced digital anonymity being developed, the devices and methods used to break it are progressing at an accelerating pace. Here's a taste of what is being developed.
Smart Tech. Quantum computing and neuromorphic chips are offering new potential for recognizing patterns and detecting behavior. Meanwhile, fake data is helping in the training of AI models to recognize hidden relationships better.
Blockchain Breakthroughs. The next generation of crypto analytics tools is pushing deeper into wallet tracing, even in privacy-focused ecosystems.
Faster, Smarter Operations. We’re moving toward real-time attribution and earlier detection, with tools that plug seamlessly into broader threat intelligence systems. The future isn’t just about identifying people after the fact, it’s about spotting threats as they emerge.
As deanonymization techniques evolve, their success depends not just on attribution precision but on how well multiple intelligence layers are unified into a single operational picture. For a deeper look at how identity graphing, data fusion, and social network mapping operate within modern investigative environments, review our breakdown of advanced link analysis in OSINT — a methodology that pairs naturally with attribution, crypto tracing, and behavioral profiling.
Deanonymization is becoming a key capability for intelligence and law enforcement agencies in an effort to uncover deeper, more sophisticated online threats. While anonymization tools are getting more advanced, so are the methods deployed to break through them.
By combining various techniques—including metadata analysis, behavioral profiling, crypto tracing, image forensics, and cross-platform identity mapping—analysts are able to generate a more comprehensive picture of who's behind online behavior. Just remember that these techniques are usually most effectively used in combination, layered one upon the other in a smart adaptive process.
As the digital landscape continues to grow more complex, the strategies we’ve outlined in this article offer a practical foundation for staying effective, agile, and accountable in an ever-evolving landscape.
User deanonymization is the process of linking anonymous or pseudonymous online activity to real-world identities using methods such as metadata analysis, behavioral profiling, blockchain transaction tracing, and OSINT.
Deanonymization combines multiple cyber investigation techniques, including digital footprint analysis, pseudonym attribution, and identity correlation across platforms, to uncover threat actors behind anonymized activity.
Deanonymization is legal only when conducted by law enforcement, intelligence agencies, or authorized security researchers under proper jurisdiction and regulatory frameworks, such as GDPR compliance.
Yes. Dark Web deanonymization is possible by correlating cryptocurrency transactions, metadata, and cross-platform identities. However, it requires specialized tools and legal authorization.
Limitations include strong privacy-focused tools (e.g., Tor + Monero), compartmentalized identities, and advanced obfuscation methods. Still, combining OSINT with technical forensics often overcomes these barriers.
Law enforcement agencies, cyber threat intelligence teams, and forensic investigators primarily use deanonymization to identify cybercriminals, stop fraud, and protect critical infrastructure.
The future includes AI-driven attribution, quantum-based pattern recognition, advanced OSINT integration, and real-time identity correlation in cyber threat investigations.
If you’d like to learn more about how Social Links solutions allow users to conduct advanced and highly effective user deanonymization, follow the button below and we’ll set up a personalized demo where you can see our products in action and as they apply to your particular needs.