April’s OSINT News: Polling Data Hacks, Defrauded Frauds, and Subtle New Phishing Scams


2021 saw record figures for data fraud and leaks, and with personal and corporate data continually finding its way onto black markets, we need to be discussing how it gets there.
The problem is that most stolen data isn’t hacked in the traditional sense; it’s elicited through social engineering strategies which trick or coerce victims into inadvertently giving up their security credentials.
As we take footsteps towards the web3 era, the scope for security threats and data exploration are bound to grow and diversify exponentially. In light of this, analysts must now be ready to adopt the latest methods of investigation such as OSINT to keep up and deal with the increasingly aggressive digital environment.
Let’s have a look at the developments that unfolded in April.
A lot of parties have a vested interest in the analysis of public sentiment. And for many, when the attainment of such data is crucial, the ends may justify the procurement means. So, it should come as no great surprise that voter identities have now become a tradable commodity. And one which is in high demand.
However, what may be surprising is the price. You probably spent more on your last lunch than it would cost to buy the voter identities for an entire state. You can get the entire Florida voter database of 12.5 million individuals for $10, and get hold of equivalent info US for an array of federal states – amounting to 107 million US voters – an average price of $8-15 each.
As of yet, details on whom the individuals voted for is not inclusive, but a selection of other data is. According to the Privacy Affairs research, you can determine which elections each individual voted in, as well as their voter ID, full name, addresses, gender, DoB, and citizenship, which is considerable for analytical purposes.
Of course on one level, such data can be used for antisocial or anti-state purposes: threat actors could use the information in identity fraud or attempts to destabilize regimes. Yet other parties such as politicians also naturally have an interest in understanding the voting demographic. Public policy strategy consultants buy up such databases to analyze public sentiment and build predictive models for the upcoming elections.
Based on voter data and history, analysts can determine who should be targeted for political marketing in a particular state, district, and area. For example, those who tend to vote early or have changed their address may most likely be urged to vote for the ‘right’ candidate via promotion campaigns or door-to-door agitators.
Since the 2008 U.S. elections, political campaigns have become increasingly data-based, and consequently, those who acquire voter information gain a substantial strategic advantage in campaign planning.
Phishing scams have long depended on their ability to be mistaken for legitimate items. Traditionally, they have most commonly taken the form of emails from banks, which look authentic, but are in fact bogus. The latest development on this strategy is a tactic whereby the phishing platform poses as a browser.
It is very difficult for typical internet users to distinguish a browser-in-browser phishing site from a regular browser action window. Believing that they are just logging into google or Facebook, victims unwittingly disclose their login details to the scammers, which can provide access to the sensitive data of individuals or entire organizations.
Social engineering approaches such as Phishing remain the most effective techniques of threat actors. The less tech-savvy but well-positioned a decision-maker is, the more vulnerable they – and their organization – become. And such individuals are widespread. For example, only 4% of IT leaders in Singapore are able to correctly identify phishing SMS and emails, while 47% are unaware of the risk phishing attacks pose to their organization.
The deceitful are often mistrustful, and these days, they need to be. According to BeepingComputer, security analysts have revealed a new type of scam aimed at the hackers themselves. Those who buy malware dissemination tools on the Dark Web risk downloading a ‘clipboard stealer’ – a program that covertly changes the information downloaded to a user’s clipboard.
The scam works as follows. Hackers buy malware systems on the Dark Web to conduct ransomware attacks. Typically they will pay for the program in crypto and receive a link to an archive with a file installer. However, unbeknownst to them, by opening the link, a clipboard stealer is surreptitiously downloaded on their computers at the same time.
Since hackers already know that their victims use crypto, the odds are high that they copy-paste wallet addresses to transfer funds. This is where clipboard stealers enter the game. When users copy crypto wallet addresses to paste them onto an internet page such as a crypto exchange or a private chat, the thief changes the wallet address just before it is pasted. This means that all payments are then siphoned off to their wallet of choice.
The only way to detect the scam is to double-check the address that you have copy-pasted carefully. And since the uninitiated are unlikely to do this, frauds may levy ransom only to be robbed by the frauds who sold them the ransomware systems. A nice racket. Using this tactic, one such hacker gained around $54k in Bitcoin from 422 crypto transactions.
On a more general note, researchers anticipate that social engineering scams will proliferate in the advent of Web3. Playing out in VR environments, metaverses may constitute the next stage in our digital integration through supposedly seamless new modes of communication. With all sorts of credentials linked to crypto wallet addresses, NFTs, and bank accounts floating around the metaverse, such scams are only set to multiply.
The Cisco Talos team has recently stated its view on the potential threats facing Metaverse users. According to their research, Web3 will be an El Dorado for fraudsters, as users are blind to the principles implicit in the new web iteration, and lack the general knowledge for navigating it safely. As a result, early Web3 adopters may well be sitting ducks for social engineering scams.
The servers of Hydra marketplace – a prominent drug-selling marketplace on the dark web – have been shut down by the German police. The government also confiscated 543 bitcoins of profit from the platform – a sum amounting to $25 mln.
At the time of the seizure, Hydra managed 19,000 drug sellers supplying 17 million customers from all over the world. The Central Office for Combating Cybercrime (ZIT) and Germany's Federal Criminal Police Office (BKA) report that Hydra had a turnover of $1.35 billion in 2020, making them the largest drug marketplace in the world.
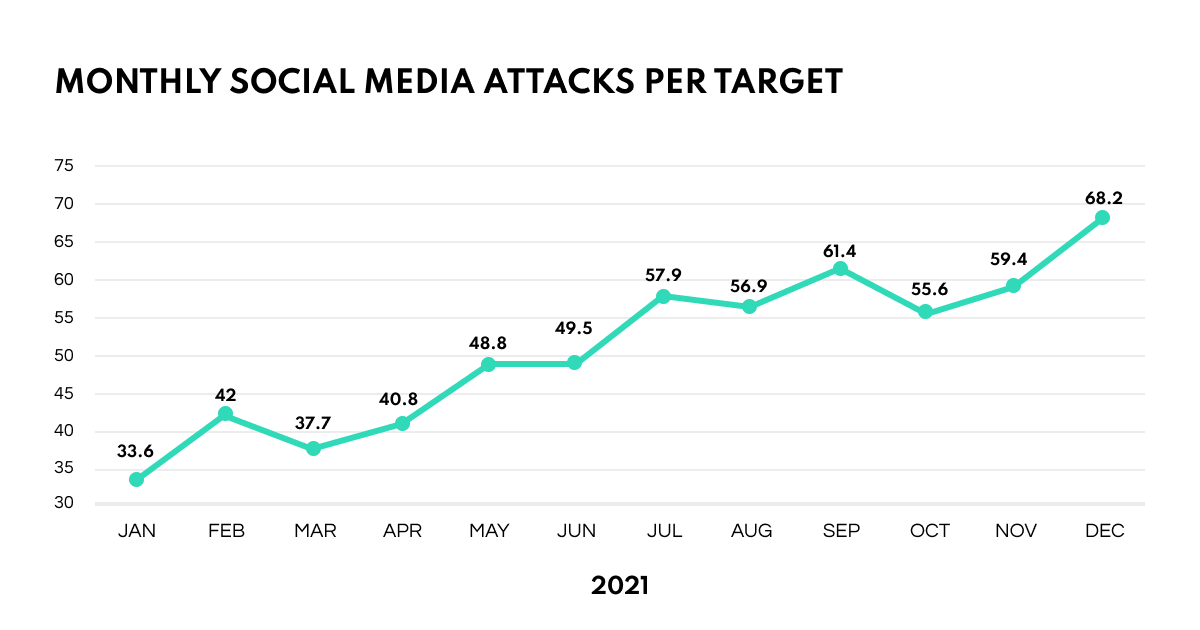
Social media cyber attacks rose by 103% in 2021, making it another record-high year for criminal activities in the cyber domain.
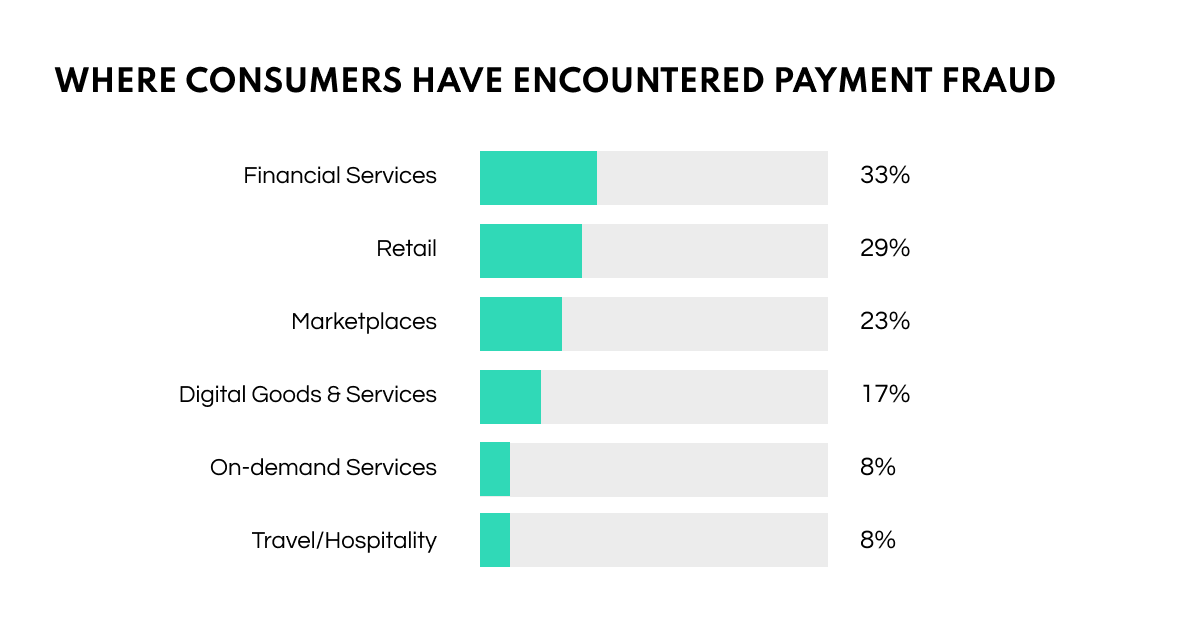
The number of fraud attacks targeting payment processing increased by 70% in 2021, while the volume of fintech transactions surged by 121%.
FBI reports $7 bln Losses through Investment Cyber Fraud in 2021
Investigators consider that the modern state of routine – and personal – cybersecurity is so weak that the number may hit new records in the years to come.
QR Codes Luring the Unsuspecting to Phishing Sites
Few people think twice before putting their camera lenses toward QR codes. However, you never know what might be behind the visual code.
Cybersecurity Magazine Posts Their Top-7 Cryptocurrency Exchange Risks
Among usual phishing and scam issues, the experts highlighted the problem of unregulated cryptocurrency exchanges. However, recent events show that even well-known and regulated crypto exchanges may disappoint their customers.
The OSINT Landscape 2022
Bringing together 12 areas of application and 120 companies, tools, and platforms, our team mapped out the lay of the land so you can make sense of the current OSINT sphere as a whole.
And that’s a wrap for our April Digest. We hope this month’s edition has given you some food for thought. Watch this space for more OSINT-related news.