Breaches and Stealer Logs: Darknet Goldmines


The value of the Dark Web as a resource for criminal investigations is widely understood. After all, the domain’s reputation as a breeding ground for nefarious activity is well-founded—with its supposedly watertight encryption possibilities, the Dark Web attracts shady actors who think they can operate while keeping their anonymity. So, investigations into these actors naturally focus on the domain itself.
However, to think of the Dark Web as a resource for exclusively looking into those that are operating in that particular stratum of the internet (illegal drug purveyors for instance), is to only recognize part of its utility. The truth is far more wide-ranging and has implications for almost any type of data intelligence you care to imagine, from criminal cases to cybersecurity and brand protection.
So in this article, we’re going to give a fuller picture and look at two data resources that are abundant on the Dark Web yet indispensable for modern data intelligence work: data breaches and stealer logs. What are these resources exactly? Where does the data come from and how? And in what way are they game-changing for all kinds of investigation? Read on to find out.
For the uninitiated, let’s quickly distinguish between data breaches and data leaks. While both refer to private information that has become available to the public in some form, leaks refer to such occurrences as a general phenomenon, while breaches are leaks that have been carried out intentionally and maliciously. That said, both breaches and leaks could ultimately contain the same data sets.
From the perspective of data security, breaches represent an ever-present scourge that is almost impossible to eradicate. But what compounds the issue more, is how pervasive and commonplace it all is. According to a 2024 study, 61% of Americans have had their personal data breached at least once, and 44% of respondents reported it had happened to them multiple times.
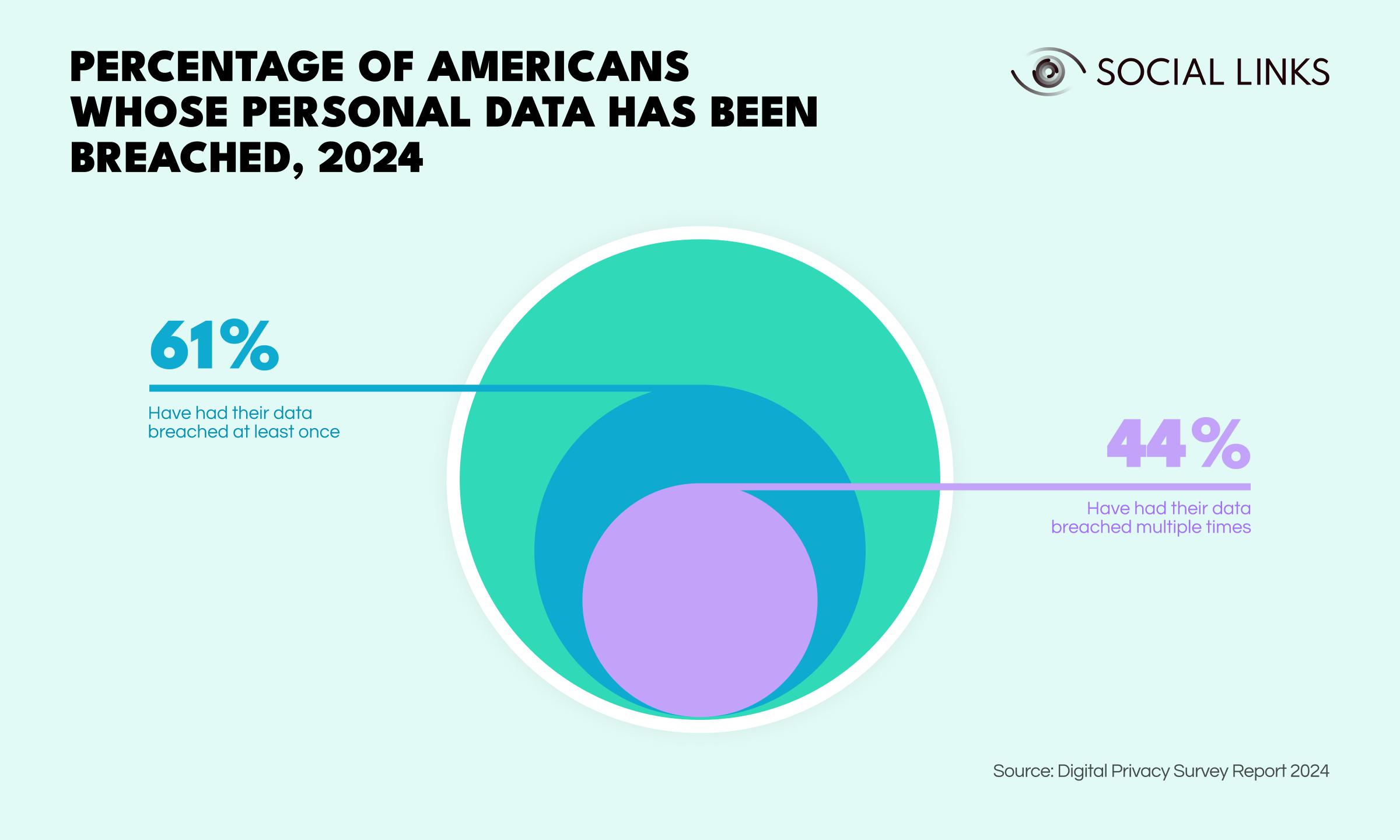
Broadly speaking, if you’ve ever signed up to an online platform (and who hasn’t?), the chances are that your data has been breached. This is not a comfortable reality, and one that waves a red flag over the nonchalant attitude many of us have towards our online activities. But for the OSINT practitioner, it’s good news—breached data can open new horizons for data-driven investigations, providing breakthroughs, leads, and connections that would be inconceivable with regular approaches.
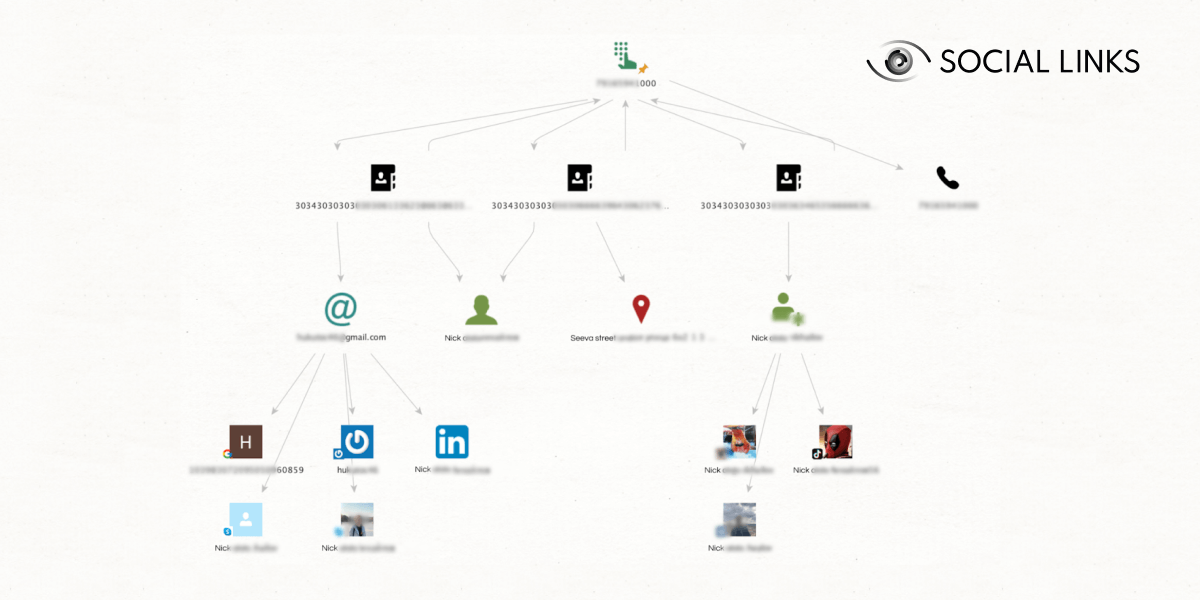
The key thing to understand about breaches is that users enter more than one type of data when signing up with an online service or platform, which can allow investigators to pivot into new areas of investigation—a single isolated data fragment can soon become an extended digital footprint.
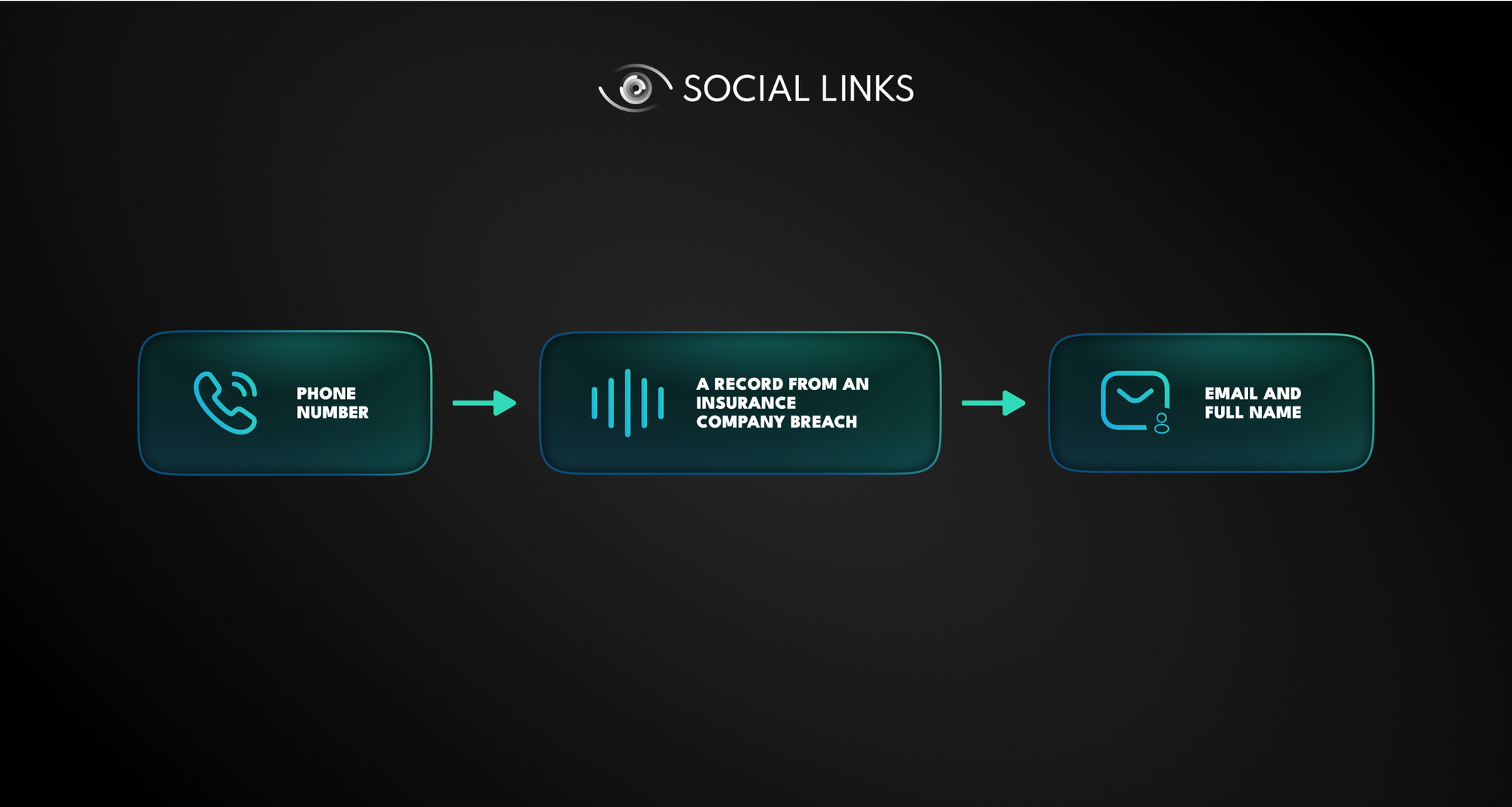
Let’s take a food delivery service as an example. Most such services require users to enter their phone number, email and delivery address. Now let’s say you’ve stumbled upon a phone number in the course of your work, which cannot be linked to any account provided by Surface Web data. Yet, you really need to unpack this fragment as it seems crucial to the progress of the case.
Without the resource of breaches, this would be the end of the matter—a deadend would’ve been reached. But it turns out that your subject once signed up (with the phone number in question) to a food delivery service that underwent a breach. Suddenly, the roadblock dissolves—you’re able to extract your subject’s breached account, allowing you to identify a relevant email, which has been used to sign up with other platforms. A whole new area of investigation has opened up.
It’s also important to note that details may be breached from almost any subscription, whether it’s a tiny website used on a one-off occasion ten years ago or a major social media platform with hundreds of millions of daily users. This means that practically no one (whether darknet user or not) is immune to this type of data enrichment—not even users who take care to cover their tracks. This in turn means that any number of roadblocks can be overcome.
So firstly, what are they? Infostealers are a type of malware, typically downloaded inadvertently via email, that infect a device and set about stealing the data within. Meanwhile, stealer logs are darknet repositories where the data taken by infostealers is stored. So, infostealers extract the data from devices, stealer logs are where the looted data is made available (by someone else).
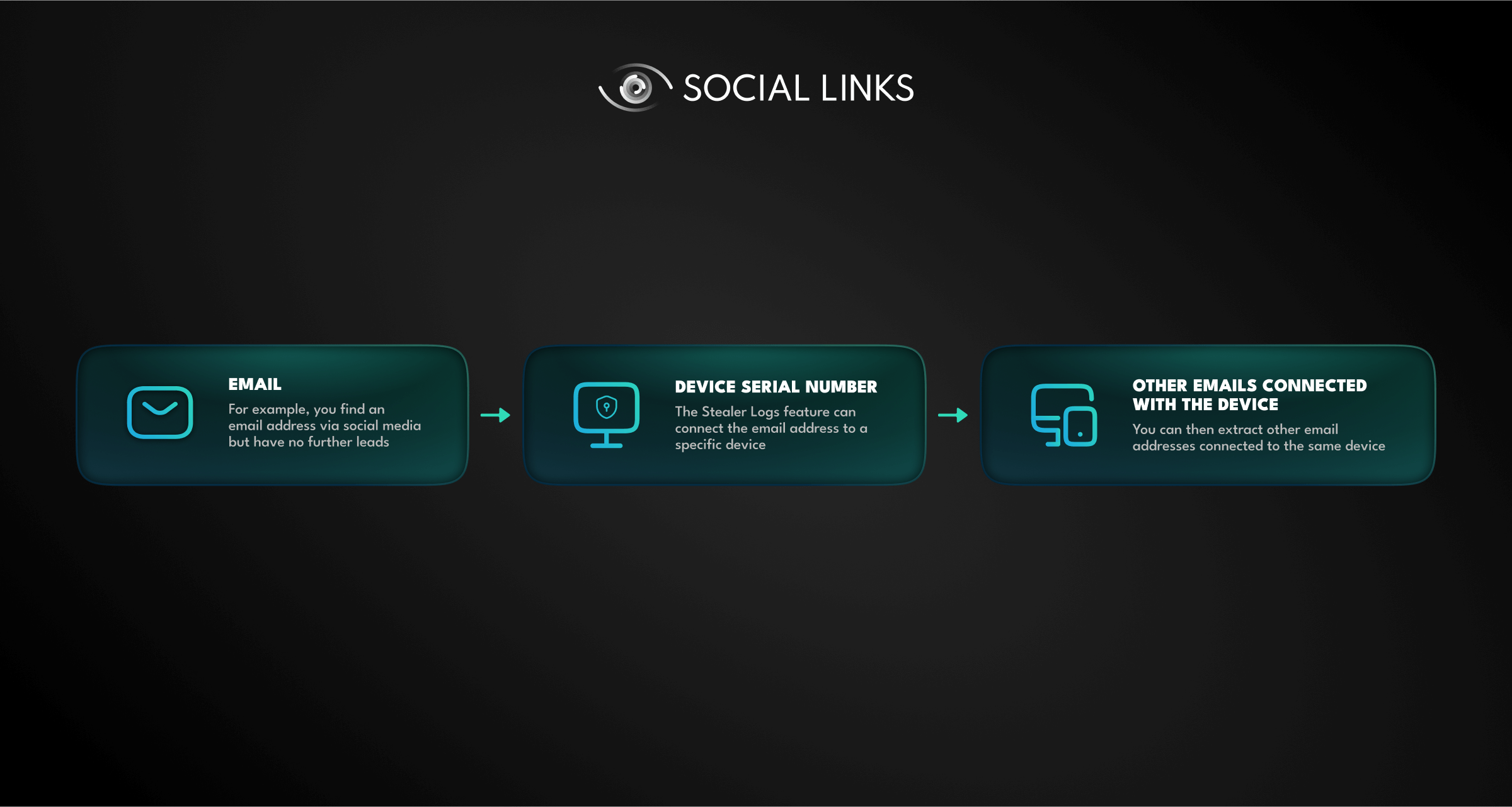
Given where stealer log data comes from, it tends to be far more compromising than the data found in breaches—since they contain the ill-gotten gains from hacking into a system, they essentially provide a snapshot of a device. This includes very significant information such as browser histories, device serial numbers, login details (email addresses, usernames, passwords), and other forms of sensitive data.
Perhaps counterintuitively, the cybersecurity industry is most affected by infostealers, as tech savvy specialists from the sphere have a tendency to use cracked software that have a higher risk of infection. IT admins are also a high risk demographic here—they are often targeted as they hold the keys to data of an entire company’s personnel and beyond.
If a subject you’re looking into has suffered an infostealer attack at some point, this obviously opens huge opportunities for profiling a suspect and tracking their activity, offering incredible investigative scope that could close a case fast. For example, investigators might be able to link certain email addresses to a given device, or see all the X (Twitter) profiles a user has accessed.
While on the surface, stealer logs represent a huge data security concern, the silver lining is that they can also be used to counteract data compromise—corporate and cyber security teams can (and do) monitor stealer logs to understand whether any compromising company data has indeed been leaked, or system hacked, so that the incident can be responded to promptly, greatly mitigating the attendant damage.
Although stealer logs and breaches are often lumped together under the umbrella term of ‘breached data’, there are distinctions that need to be recognized. While breaches are very commonplace and really can befall just about anyone, stealer logs—thankfully—are not so wide-reaching. This stands to reason, as clearly most devices are uninfected. But when they are, the nature of the data stolen is very compromising indeed.
Both of these resources are incredibly helpful for investigators and security teams, although they have slightly different nature. Breaches can provide data connections for a truly immense number of users, helping all kinds of cases progress. Stealer logs don’t come in handy as often, but when they do, they utterly transform an investigation. Taken together, these resources are an indispensable part of the investigator’s toolkit!
Social Links products have powerful darknet features, enabling users to make the very most out of breached data and enhance a wide range of investigations and use cases.
This is a hugely innovative transform that’s an industry first—nowhere else can you combine these forms of data in a single investigative space. This transform will be a gamer-changer for exposure checks and regular surface web investigations.
[SL Darknet] Search in Stealer Logs can be run from alias (username), person (name), email, device serial number, URL, or email domain entities. Once the transform has been run, apply [Extract] Entities for your results, which will appear in structured form on the graph.
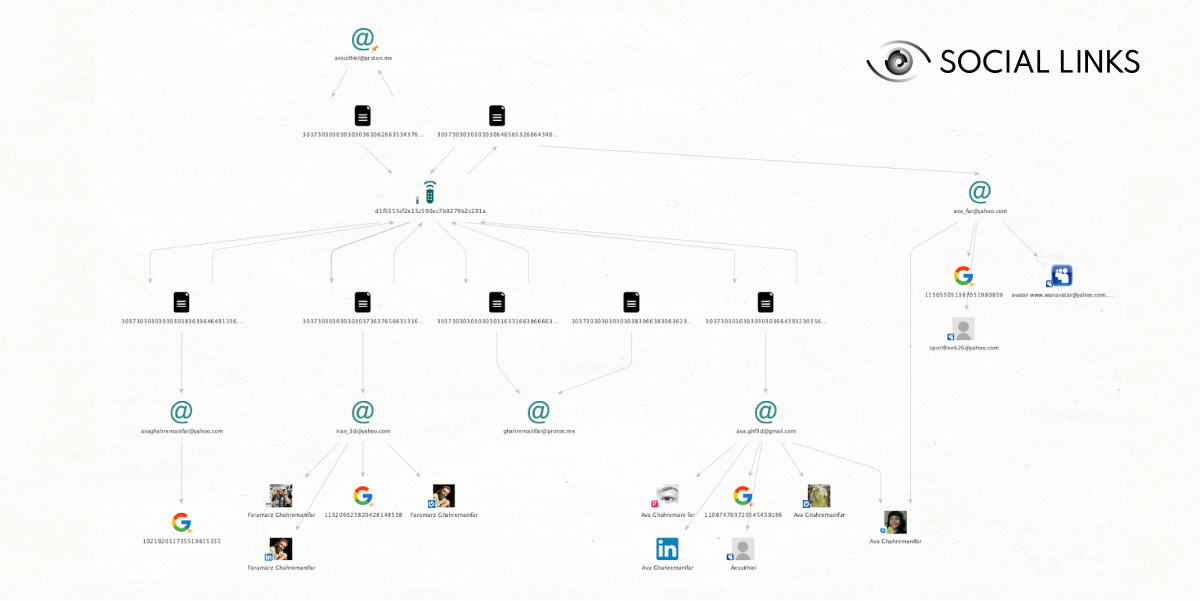
This transform can revolutionize exposure checks and surface web cases—even when the subject isn’t a darknet user.
The data for this transform comes from a provider who specializes in data leaks. This means the data itself is not only extensive, but also well-structured, significantly raising the chances of finding the information you need to wrap up a case.
[SL Darknet] Search in Leaks can be run from phone number, alias (username), email, cryptocurrency, IP address, person (name), and email domain entities. You then need to run [Extract] Entities to view your results.
When used in combination with OSINT techniques, breaches and stealer logs offer incredible potential in two main areas:
Roadblocks can be extremely frustrating, yet they are a natural aspect of the investigation process. These darknet resources have the breadth and scope to be of use for a dizzying range of cases—you never know what seemingly innocuous subscription by your subject may transform a case from a stagnant deadend to an expansive and revealing footprint.
Organizations of all kinds from public sector services, through corporations, to SMEs all run the persistent risk of data compromise, which can have potentially disastrous consequences. By keeping a close eye on all that is being breached, organizations stand a much better chance of being able to effectively safeguard themselves against data security failure, and respond promptly if an incident does occur.
Want to find out more about how breached data can transform your intelligence work? Follow the link below to arrange a call with one of our specialists, and we’ll demonstrate the huge benefits of these resources to you in person and in relation to your specific needs.