Dark Web Intelligence: A Security Essential


The Dark Web—that notorious part of the internet that runs on hidden networks like Tor and I2P—has become a real-time barometer for gauging future cybercriminal attack. Dark Web Intelligence is the structured collection, analysis, and use of data from these hidden spaces. It shows when stolen logins are for sale, when a ransomware crew is recruiting, and when a new exploit kit is spreading fast. And it gives security teams a critical head start.
When done well, Dark Web monitoring combines automated data gathering with skilled human analysis. It supplements open-web threat feeds and, most importantly, drives measurable results: faster incident response, reduced fraud losses, and stronger regulatory compliance. So today we’re looking at what Dark Web Intelligence really means, why it matters, and how to build a mature program as well as the challenges you’ll face, trends shaping the field, and the best practices to get it right.
Before diving into the “how”, let’s first clear up some basics. The Deep Web comprises any online content excluded from commercial search engines. While the Dark Web is the smaller slice within it, requiring special tools like Tor, I2P, or Freenet to access—often with vetting to get inside. Europol’s latest Internet Organised Crime Threat Assessment notes that these hidden spaces are hubs where ransomware gangs, data brokers, and access sellers plan and coordinate their activities.
Dark Web Intelligence then, is the structured collection, enrichment, and use of data from these hidden services. This can include chat logs, market listings, escrow transactions, paste dumps, and even chatter about upcoming takedowns. Analysts then pair such content with open-source data and internal telemetry to build context.
Regulators now see this visibility as part of basic cyber hygiene. Europe’s NIS 2 Directive, for example, explicitly lists “continuous vulnerability and dark-web monitoring” as a required security measure. ENISA, the EU’s cybersecurity agency, has reinforced the point, urging boards to document how underground intelligence feeds into their risk management.
So why should companies care about the goings-on of the Dark Web? Because it can often spell the first signs of trouble—the information that surfaces in this domain can be critical for safeguarding data and implementing effective responses. Here are a few examples:
Stolen data doesn’t stay hidden for long. In June 2025, a BleepingComputer investigation found the forum, Russian Market, advertising more than 5 million new login pairs every week. Also, according to CyberScoop, infostealer malware harvested 2.1 billion credentials in 2024 alone. These figures illustrate the massive scale of the threat. By using Dark Web threat intelligence to spot these leaks early, teams can force password resets before criminals turn them into bigger attacks.
Europol’s May 2025 take-down of three darknet drug markets led to 270 arrests and the seizure of servers that also served as ransomware-as-a-service recruiting hubs. This shows how closely extortion gangs and market operators are connected.
The 2024 State of the Software Supply Chain study shows that attackers often exploit third-party providers before moving to their main targets. Stolen build-system secrets frequently surface first on Tor-based whistle shops.
After the Snowflake breaches, stolen customer data quickly appeared for sale. Public reporting showed how fast shareholders and privacy regulators respond once a dataset hits underground channels. Keeping evidence that your company monitored these spaces—and acted quickly—can reduce financial loss and reputational damage.
Dark Web intelligence becomes more powerful when it is combined with structured investigation workflows and OSINT methodologies. Analysts can amplify attribution by correlating darknet data with identities, credentials, and behavioral traces across public platforms. To understand how this type of systematic investigation works in practice, read our guide on the OSINT Framework, which explains how structured collection and enrichment transform raw data into actionable insights.
So we’ve established that darknet content can be of vital importance for all kinds of security disciplines. But how do you actually put Dark Web Intelligence into effective practice? A strong program usually has four moving parts:
Combine automated and manual data sourcing. The question of coverage and Dark Web monitoring is a good place to start. Automated crawlers can be effective for Dark Web data collection, being able to scan hundreds of Tor sites and paste bins at scale, many communities instantly spot bots and shut them out. That’s where human analysts come in—by adopting vetted personas, the savvy plain-clothes investigator can blend in and gain entry. Recent research into infiltration strategies confirms this tactic remains essential.
Analyze marketplaces. Marketplace data—like prices, vendor ratings, and escrow feedback—can give crucial context. Academic studies even show these signals can predict which forums will survive law-enforcement crackdowns.
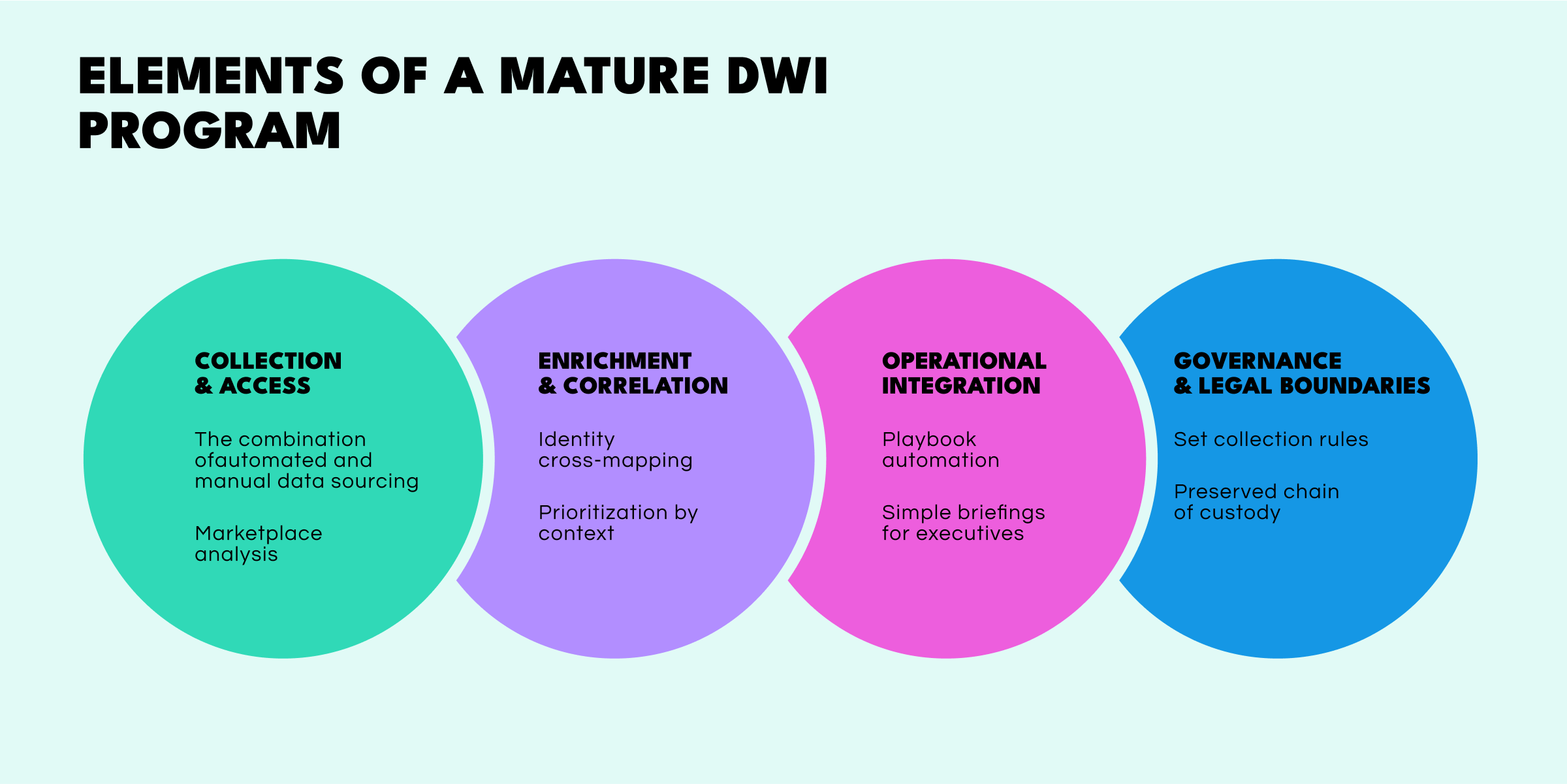
Cross-map identities. Use Dark Web intelligence platforms to link underground nicknames with known malware-builder GitHub accounts, leaked Jabber IDs, or Bitcoin wallets.
Prioritize by context. Combine Dark Web data collection with external vulnerability scans. For example, a credential leak linked to an unpatched VPN is a Tier-1 alert, but the same leak for a long-disabled account becomes a watch-list item.
When underground data is combined with graph analysis and social attribution, hidden structures become visible. Linking darknet aliases, vendor accounts, bitcoin wallets, and OSINT identities creates a comprehensive actor profile instead of isolated indicators. Platforms like Crimewall automate this enrichment and pivoting process, pulling darknet intelligence into unified network graphs. If you want to understand how network-level analysis strengthens attribution, explore our deep dive into Social Network Analysis.
Automate your playbooks. When you feed alerts into your Security Information and Event Management (SIEM) or Security Orchestration, Automation, and Response (SOAR) workflows, the system takes over—credential resets happen automatically, DMARC protections enforce themselves, and legal takedowns fire without delay.
Brief executives simply. Maintain a simple “watch board” for executives, where you track metrics like underground mentions of the company brand, average asking price for stolen credentials, and time-to-detect versus publication.
Set collection rules. Create a collection policy that forbids viewing illegal content, such as CSAM, or interacting with sites beyond passive observation unless cleared by legal counsel.
Preserve the chain of custody. Record provenance—time, location, and access path—for every piece of collected data. This record becomes essential if evidence needs to be shared with law enforcement.
Dark Web Intelligence isn’t an easy disciple. The landscape changes quickly, and mistakes can waste crucial time and resources. Here are some of the main hurdles—and how to handle them.
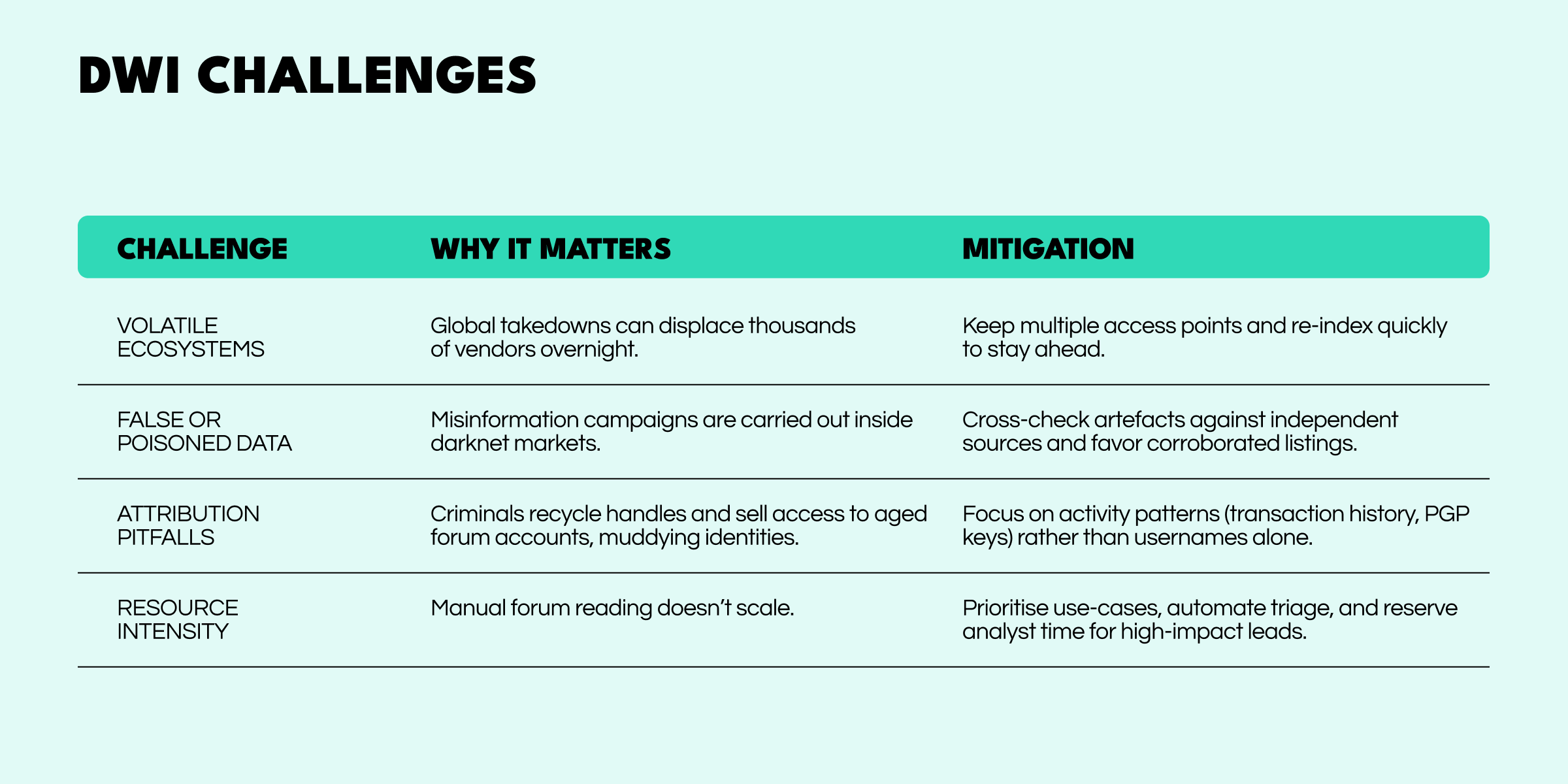
The Dark Web never sits still. As new tools pop up, markets rearrange themselves overnight, law enforcement comes down hard, and regulations keep changing. Let’s look at the trends that really matter and what your team should look out for to stay ahead.
Underground projects like WormGPT sell unrestricted access to AI language models for creating phishing lures and malware code. Analysts should employ Dark Web threat intelligence to keep an eye out for these services, as they can turn into ready-made spear-phishing kits that need no prompts.
ResearchGate-hosted data shows that dark marketplaces reorganize straight after law enforcement seizures, meaning a near-continuous flow of stolen logins is maintained and underground threat intelligence becomes a perennial necessity.
International operations now combine arrests, infrastructure seizures, and financial sanctions. The U.S. Treasury’s action against a darknet administrator earlier this year is a clear example.
As EU countries adopt NIS 2, draft national guidelines are already citing Dark Web monitoring as proof of proactive risk management.
Cybercriminals are busy launching attacks, so you should be busy mounting your defenses. You need to start smart, stay focused, and track what actually makes a difference. Here are the best practices for building an effective Dark Web cyber intelligence strategy in your organization.
Kick-off with a focused, outcome-driven plan. Organizations often get the most value by first watching for leaked employee credentials and fake domains impersonating the brand. Keep it narrow—don’t try to cover everything at once.
Blend automation and human judgement. Use crawlers to cover lots of ground quickly. Save your human analysts for closed, high-value communities outside the reach of bots. Automation is for scaling; people bring critical thinking.
Integrate, don’t silo. Make sure alerts from underground markets feed into the same incident-response routines as any other critical warnings. Don’t let these signals sit in isolation—they’re only useful if they trigger action.
Track business impact. Track metrics that actually matter—like how many stolen credentials you reset before they go public or how much potential fraud you blocked. Numbers show if your program actually works.
Carry out quarterly reviews. Check in at least every three months. Update watch lists, prioritize sources, and refresh legal guidance. The underground ecosystem changes fast; your practices should too.
Dark Web content rarely stands alone — its investigative value increases exponentially once it’s correlated against image metadata, user aliases, behavioral fingerprints, and cross-platform identifiers. Reverse image search is a practical example: combining darknet imagery with OSINT reverse lookup can help analysts tie underground personas to surface web identities, geolocate environments, or spot reused media assets. To see how this methodology works in real investigations, review our article on Reverse Image Search as a Proven OSINT Technique.
Dark Web Intelligence isn’t just some exotic tool for elite cyber teams; it’s a practical, measurable layer that shortens detection windows, cuts fraud losses, and proves to regulators you’re serious. The tools you need are within reach: combine scalable collection methods with skilled human expertise, and feed findings into daily security routines.
The web’s darkest corners can be your early-warning system or an after-the-fact autopsy—you decide. Start listening sooner, and your team gains more time to stop the next breach before it becomes tomorrow’s headline.
What is Dark Web Intelligence?
Dark Web Intelligence is the process of collecting, analyzing, and using data from hidden online networks such as Tor and I2P. It helps organizations detect stolen credentials, monitor ransomware activity, and prevent cyberattacks before they escalate.
How does Dark Web monitoring work?
Dark Web monitoring uses automated crawlers and human analysts to track marketplaces, forums, and hidden communities. It detects exposed data such as leaked passwords, credit card details, or insider threats, providing early breach discovery.
What is the difference between threat intelligence and Dark Web threat intelligence?
General threat intelligence focuses on cyber risks from all sources, while Dark Web threat intelligence specifically analyzes underground platforms where criminals trade stolen data and plan attacks.
Why do companies need a Dark Web intelligence platform?
A Dark Web intelligence platform centralizes data collection, enrichment, and analysis. It integrates alerts into existing SOC or SIEM tools, helping companies respond faster and improve cybersecurity resilience.
What are Dark Web intelligence tools?
Dark Web intelligence tools include crawlers, AI-driven analytics, and secure access methods to underground forums. They enable investigators to discover leaked data, monitor ransomware groups, and analyze threat actor behavior.
Is Dark Web data collection legal?Yes, collecting publicly available data from the Dark Web is legal when done passively and ethically. Companies must avoid engaging in illegal activities and should comply with privacy and regulatory requirements.