December’s OSINT News: The Tracing Game is on after FTX Fiasco, and FBI Employs Geofencing for Capitol Riot Investigation

Cyber security news has really ramped up as we approach the New Year. While the FTX story has understandably drawn a lot of attention, there have been plenty of other recent developments in the sphere.
In our final digest of 2022, we give our slant on the elephant in the room (the FTX collapse), alongside other news that has had less coverage in the mainstream media, including the FBI’s use of geofencing in investigating the Capitol riot, chartered qualifications for UK cyber professionals, and a string of cyber attacks on nuclear facilities around the world. Let’s jump in!
Amid all the speculation surrounding the mysterious implosion of the crypto exchange FTX, there is a consequence that seems more than likely from the fallout – OSINT investigators are going to have their work cut out getting to the bottom of it all.
What is known is that in the immediate wake of its seismic collapse, the disintegrating exchange found itself in a further $663M hole. FTX officials claimed that these funds had been stolen in one fell swoop as the result of a hack, and immediately urged users to delete their apps, which were then ostensibly deemed to be malware.
However, due to the open-source nature of blockchains, analysts are not necessarily obliged to take these statements at face value, and independent inquiry has already yielded conflicting accounts. The blockchain analysis and crypto-tracing firms Elliptic and TRM Labs put the stolen assets at $477M and $388M respectively, with the remainder of the $663M purportedly being moved to the exchanges' own storage wallets.
Despite these discrepancies, there is apparent consensus on one point – the spoils of the heist have been moved to just a few cryptocurrency addresses. And so now the entire crypto-tracing industry, including blockchain analysis firms, LEAs, and a myriad of private crypto investigators and enthusiasts, are all poised to start digging the second these addresses show any activity.
For the thieves, this level of attention makes cashing out problematic, to say the least. Gone are the days of unassailable anonymity. For instance, even crypto mixers, which can be used to launder money through the fragmentation and scattering of transaction data, are no longer immune to tracing. Advanced OSINT systems can reconstruct blockchain data that has passed through a mixer.
The now-retired founder of FTX Sam Bankman-Fried saw his $16B net worth evaporate as a result of the FTX crash. Still, the FTX heist is not the first – and nor will it be the last – of its kind. This year alone has seen hackers steal $540 in crypto assets from the Ronin Bridge, and a New York couple arrested for laundering $4.5B in crypto. Going further back, Mt. Gox, the first crypto exchange, ceased to exist in 2014 after a $500M exit scam.
While crypto exchanges largely have quite thorough security policies towards their clients in the form of various KYC and AML-control procedures, there appears to be an astonishing laxity with regards to their own operators. This needs to be urgently addressed to minimize the potentially catastrophic risks of data breaches, insider fraud, and infrastructure intrusion.
After the Capitol riot on January 6, 2021, independent OSINT researchers were instrumental in helping the FBI swiftly identify the participants. Now, the bureau is harnessing geofencing technologies and warrants to retrieve geodata on the 5,723 devices that were used within the territory of the Capitol building, on the day in question. 900 people have already been charged, and with the help of geointelligence, this count may go up to 1,535.
The geofence warrants allow analysts to search for users within a four-acre area. By combining the geoposition data extracted from Google services with GPS, Wi-Fi, and Bluetooth signals, the investigators can collect enough evidence to substantiate claims in court. Meanwhile, users who had their geolocations turned off during the riot but were known to be in the area before or after also fell under suspicion and were investigated further.
However, experts claim that even such a complex and multilateral geofencing approach only has a 70% probability of hitting upon the right outcome. Nevertheless, geofence has been cited as evidence in 100 court hearings connected to the riot, and in 50 cases was the means by which suspects were identified.
Open-source intelligence often plays a crucial role in various stages of a criminal investigation. However, when human lives and prison sentences are at stake, investigators must always strive to use all sources of evidence at their disposal, including human interaction and police interception.

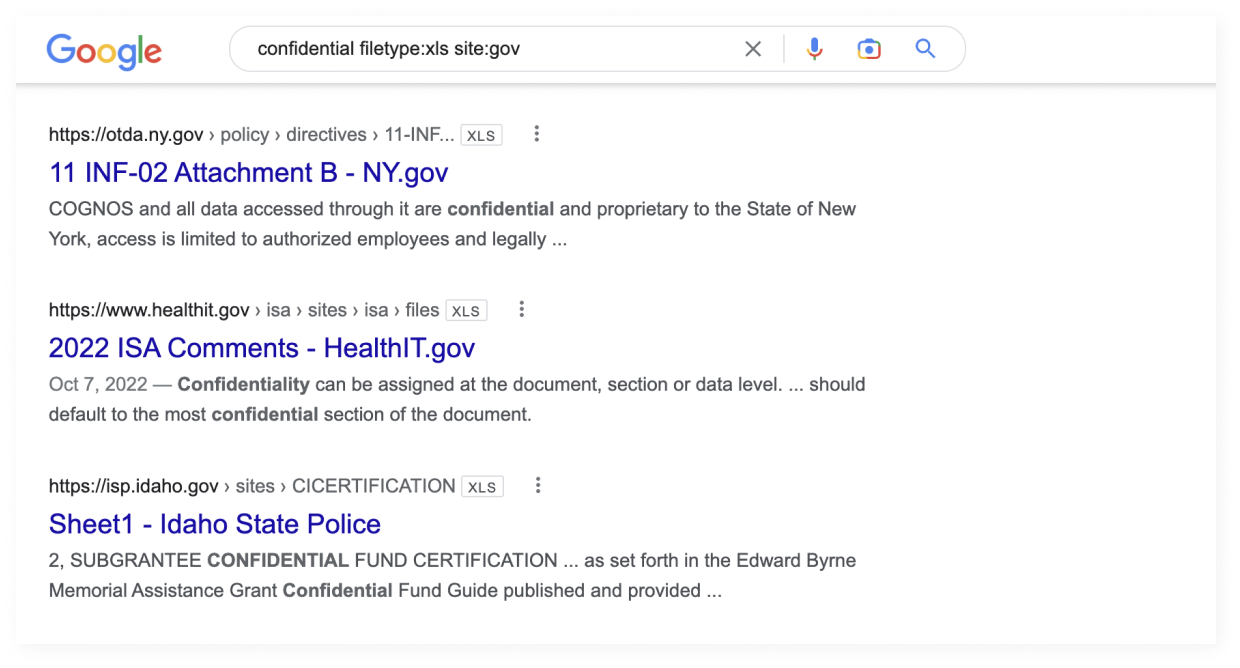
Not all information extraction techniques require sophisticated tools. Sometimes, regular search engines can provide cybersecurity specialists with enough data to conduct penetration testing or find crucial – perhaps even sensitive – information inadvertently published by its owner.
In this sense, people can be divided into amateur and professional googlers. Most people use natural, straightforward language and phrases to enter Google queries, for example, “William Gibson Neuromancer buy on Amazon”. However, those who have more technically demanding goals in their sights often use advanced search engine operators and methods to conduct precise searches, which would not be possible via regular requests. This technique is known as Google Dorking.
Many dorking activities consist in unearthing information that website administrators mistakenly consider hidden from the public, and can include personal details, security data, database access, and other sensitive technical information. Since all of this information is technically in the public domain, it is fair game so far as the OSINT analyst is concerned.
Yet, despite the object being open data, some still wrongly refer to Google dorking as ‘hacking’. That said, in most cases, the data is made public unintentionally, giving dorking an opportunistic character that arguably places it in an ethical gray zone rather than a pristine white.
Sensitive information on 322 million eBay users, including email addresses, full names, physical addresses, and dates of birth, are currently up for sale on the Dark Web for 799 BTC. The last eBay leak happened in 2014, compromising the data of 145 million users.

The UK Cybersecurity Council has announced a certification program for cybersecurity professionals based on official professional standards. The qualifications are represented by three titles depending on the depth of professional expertise. Specialists can now be classified as an Associate, Principal, or Chartered Cyber Security Professional.
As one of the most digitally integrated countries in the world, the Netherlands values its computer systems, which have become the cornerstone of everyday life and work for many Dutch people. Unlike its counterparts, the Dutch cyber security strategy favors the protection of the digital society over the militant defense. Personal security issues such as cyber security awareness play a decisive role in the strategy.
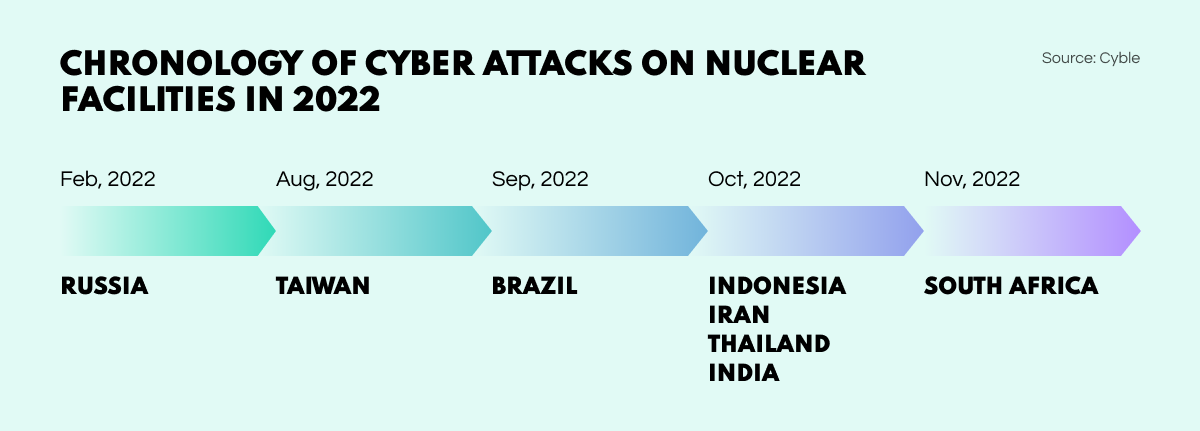
Cyber Researchers have noticed a disturbing rise in cyber attacks on the nuclear industry in 2022. The issue has been worldwide and affected facilities in various countries including Russia, Taiwan, Brazil, Indonesia, Iran, Thailand, India, and South Africa. Hackers have been targeting vulnerable IT/OT devices to gain unauthorized system access and steal sensitive data.
While Qatar has been hosting the world’s most prestigious football tournament, citizens of the Middle East have seen a 100% rise in malicious emails. Using FIFA-related impersonation tactics, scammers have been urging recipients to conduct two-factor authentication procedures, then stealing their credentials.
And that rounds off the December digest! Stay up to speed with all things OSINT by keeping an eye on our blog, where we publish all kinds of the latest news and industry insights relating to the sphere.