February/March OSINT News: Evolving Valentine’s Scams Set New Records, Hydra Closure Guts Darknet Market Revenues, and More


This time around, we’ve put together a bumper digest including February’s news as well as March’s. And it’s been an interesting couple of months. From new breeds of romance scams and a huge lull in darknet marketplace activity, to the announcement of the USA’s five-pillar cybersecurity strategy, not to mention our usual glossary entry of the month, there’s a lot to get through. So, let’s jump in.
For social engineering scammers, Valentine’s Day is simply irresistible. While there’s a fair amount of dismissiveness about this quasi-romantic day, it can have a pretty widespread impact on the feelings of the unattached or lonely. For many, this is a good reason to play down the whole thing, but for some cynical individuals, it’s an opportunity to extort money through manipulation.
According to the American Federal Trade Commission, 2023 has been a record year for Valentine’s-day hoodwinking, with 70,000k people reporting incidents, total payouts amounting to a whopping $1.3B, and an overage loss-per-scam around the $4.4k mark. If these figures surprise you, remember that individual scam payouts have been as high as $15k, while a single scamlord has been recently reported as bagging $9.5M.
Such figures suggest that fraudsters are employing techniques more sophisticated than mere spamming. And indeed they are. To start with, social media means that con-artists have the chance to do their research on their victims. They can determine the hopes and tastes of their contact, and pose as the perfect match, which gives them a better chance of success right off the bat.
After making initial contact through social media or dating apps, scammers may spend weeks winning over the affections and confidence of their victims. There’s usually some solid lie as to why they can’t meet up, such as being posted in some far-flung location such as an oil rig or military base. Then comes the inevitable crisis: ‘My dear friend is in trouble, can you please help me out with some money?’
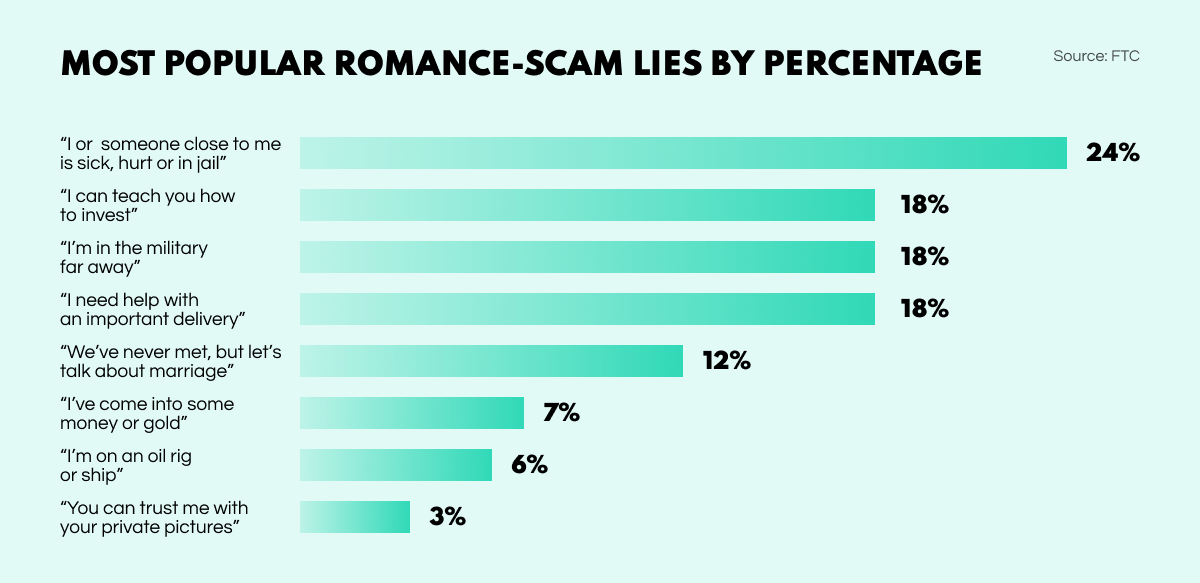
While many sweetheart scammers go after individuals and their personal bank accounts, some have their sights on larger, corporate targets. You might wonder how a company can be the victim of a romance scam, but it can happen through a technique that has been dubbed catphishing—a hybrid of ‘spear phishing’ and ‘Catfish’, which was the profile name of the scam’s originator.
Catphish scammers are aware that an organization’s data security is only as strong as that of the individuals that make up the personnel. So, these crooks gain the trust of an employee through romantic allurement in order to wheedle out of their victims sensitive company information, such as login details. Gaining access to internal systems, they can then cause all kinds of trouble—from data theft to ransomware—to extort money.
Recent times have also seen the rise of another mutant—the elegantly named pig-butchering scam. Unlike the scams already discussed, trust is won, not to ask for a financial favour, but to appear legitimate in offering one. Needless to say, the financial opportunity is in fact bogus. The name comes from the concept of fattening up a pig before slaughtering it to milk it for all it’s worth.
Here’s how it works. Romance is again leveraged by the scammer to win over someone’s trust. In the course of their communication, the con-artist mentions that they’ve made a small fortune through some investment, and there’s a great opportunity for their new-found friend to also make some money. Are they interested?
Having set up a phony website with all the bells and whistles such as attractive infographics and a working UI, the fraudsters convince their victims to invest some money. Just a bit to start with. Then by controlling the site themselves they show the would-be investor immediate returns, and allow them to even withdraw these funds.
When the victim seems convinced that the scheme is indeed ‘lucrative’, the scammer begins ‘fattening up’ their prize, encouraging them to invest more and more, including life savings and borrowed funds. Once the poor investor has been totally bled dry, the fraudster drops off the radar, the website lies dormant, and all the money is of course lost. Thus is the ‘pig’ butchered.
Along with other forms of internet fraud, romance scams have become a real threat to society. It is becoming ever more difficult to identify the crooks, while their sophisticated schemes allow them to drain their victims and rake in the profits. The police need a radically new approach to fight such scams before the losses become overwhelming. In helping analysts promptly identify fraud scenarios, OSINT tools and techniques can tackle this threat at an early stage and nip scam campaigns in the bud.
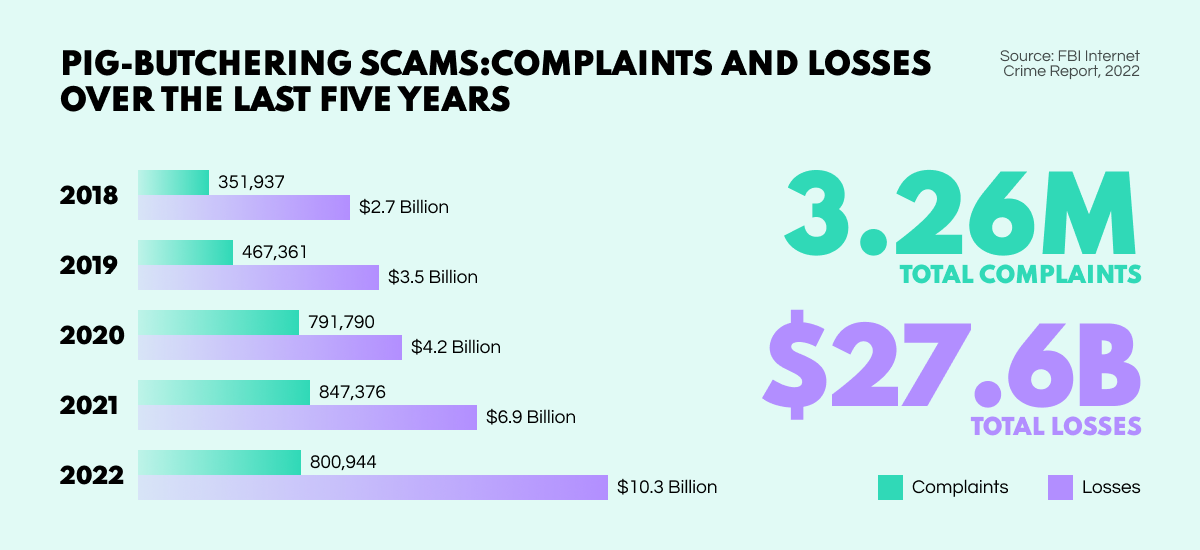
When the world’s most popular darknet marketplace was shut down last April, it was immediately seen as a triumph for LEAs in the fight against illegal trade. But, only after reviewing darknet market revenue statistics for the months following Hydra’s seizure has the extent of its impact been more clearly understood.
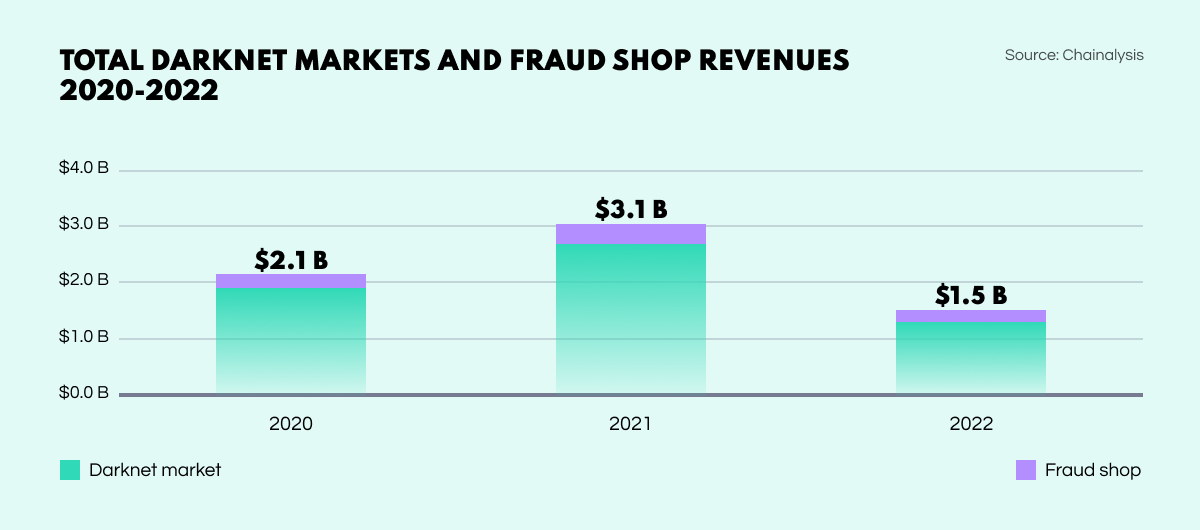
According to a new report by Chainalysis, darknet marketplace revenues fell by 50% in 2022 as a direct result of Hydra’s seizure, with a dramatic drop across the board from 2021’s $3.1B to last year’s $1.5B. In the immediate wake of the marketplace’s closure, the daily average revenue collapsed from $4.2M to just $447k.
However, experts are now seeing a rise in activity on other drug marketplaces such as Mega Darknet Market, Blacksprut Market, and OMG!OMG! Market, leading to predictions that the market volume may recover to some extent this year. Meanwhile, money laundering services previously offered by Hydra have been emerging on other darknet marketplaces. Vendors are also beginning to establish their own marketplaces to get around fees, and control procedures themselves.
While the closure of Hydra was a significant counteraction to illicit trade, such activities will inevitably continue—and probably in a more complex form. From the ashes of a collapsed central platform, a more fragmentary criminal landscape could easily emerge, with police facing the challenge of tracking new illegal marketplaces and tracing crypto transactions from multiple sources. A lot of work for Dark Web investigators.
This is one you’ve probably seen crop up in cybersecurity articles. A distributed denial of service—or DDoS attack— is a form of server or system sabotage, whereby the target is overwhelmed by a flood of internet traffic and disabled—the service it is supposed to provide is no longer possible.
Any device or system connected to the internet can be potentially turned against the service provider as a receptor of attack traffic. Malicious actors can achieve this by hacking into systems and installing specific types of malware, turning each device into a remotely controlled ‘bot’ or ‘zombie’. Collectively, these become ‘botnets’.
Once the botnet is established, it can be focused on the target network to deliver masses of internet traffic. Since every bot is a real device, filtering out the cluttered traffic can be extremely difficult. With the server being totally flooded, the saboteur can watch as things start to go wrong.
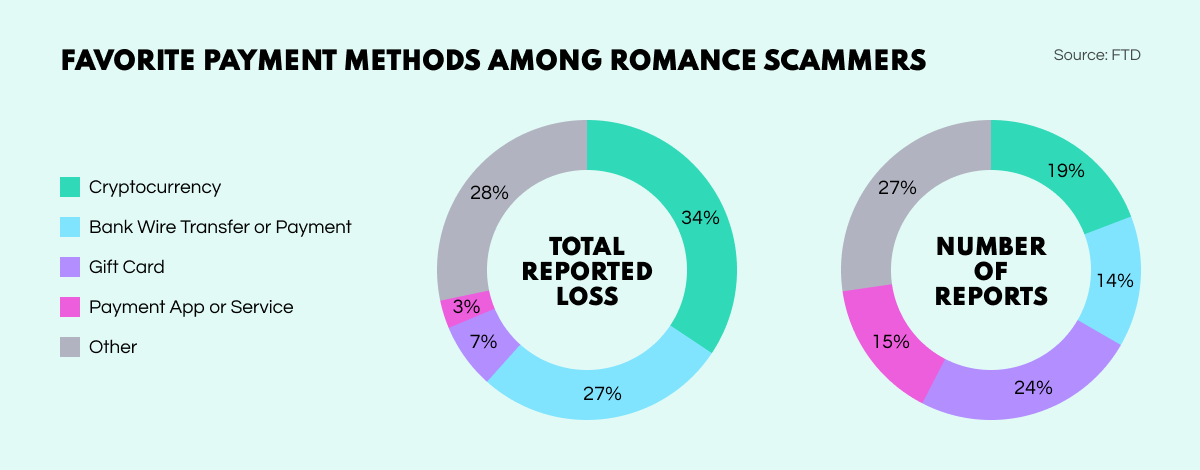
Sweetheart scammers are favouring cryptos and gift cards as payment methods—no doubt in the interests of preserving their anonymity. Crypto tops the list in terms of dollar amount, while gift cards account for most instances.
The White House has announced a new national cybersecurity strategy to replace the Trump administration’s 2018 offering. The new strategy lays out the various difficulties the U.S. is facing, and proposes a range of measures for dealing with them. The approach has five pillars: to defend critical infrastructure, target and disrupt threat actors, improve security and resilience, invest in resilience, and enhance international partnerships.
The Asia-Pacific territories saw the most cyber attacks for the third year running in 2022. According to a report by IBM Security, 31% of global cybersecurity incidents were recorded in the region, with backdoor deployment accounting for 31% of cases, and Ransomware next on the list at 13%.
With the help of the AI-driven analysis service Gender Analyzer V5, Trend Micro determined the gender of 50 randomly selected users of the hacking discussion sites XSS and Hackforums, finding that 30% from the former were female, and 36% from the latter. Interesting figures for investigators, who need to understand that gender biases can cloud their judgment.
Belgium is establishing a nationwide safe harbor to protect ethical hackers from legal action. The Centre for Cyber Security Belgium (CCB) is putting in place a new framework meaning that individuals and organizations cannot be prosecuted for discovering gaps in cybersecurity perimeters, providing certain conditions are met.
The extraordinary popularity of gaming consoles has attracted the attention of all kinds of hackers and scammers, suggesting gamers need to game in a more secure manner. According to a survey conducted by Infosecurity magazine, 87% of Xbox users had been faced with an instance of hacking, while 62% of PlayStation users complained of such experiences, and 61% of Nintendo gamers.
And that wraps up our digest for February and March—we hope you enjoyed the read. Be sure to keep an eye on our blog for OSINT news, updates, trends, insights, and more.