How to Boost OSINT Investigations with Google Dorking Techniques


The verb “to google” has been a fixture of the English dictionary for some time now, highlighting just how synonymous the engine’s proprietary name is with the action of finding information online. And considering Google processes a staggering 5.9 million searches every minute, this linguistic status should come as no surprise to anyone.
Yet despite its immense popularity, most users only scratch the surface of what the search engine can do. So in this week’s Center of Excellence article, we’re looking at Google Dorking—a range of approaches that leverage Google to its full extent, allowing OSINT specialists to refine their searches, unearth hidden information, and discover security vulnerabilities.
Most people use natural, straightforward language and phrases to enter Google queries. However, those who have more technically demanding goals in their sights can employ built-in advanced operators to conduct precise searches, which would not be possible via regular requests.
Also known as Google Hacking, Google Dorking refers to the collection of search methods that employ these built-in operators—typically in combination—to strategically filter results. By using the right stack of filter words, the user can refine their searches to return results of specific file types, containing particular word sequences, and much more.
Google has a set of built-in search operators that help refine results and are deployed as textual inserts to a given search query. Here are some examples of the most useful ones:
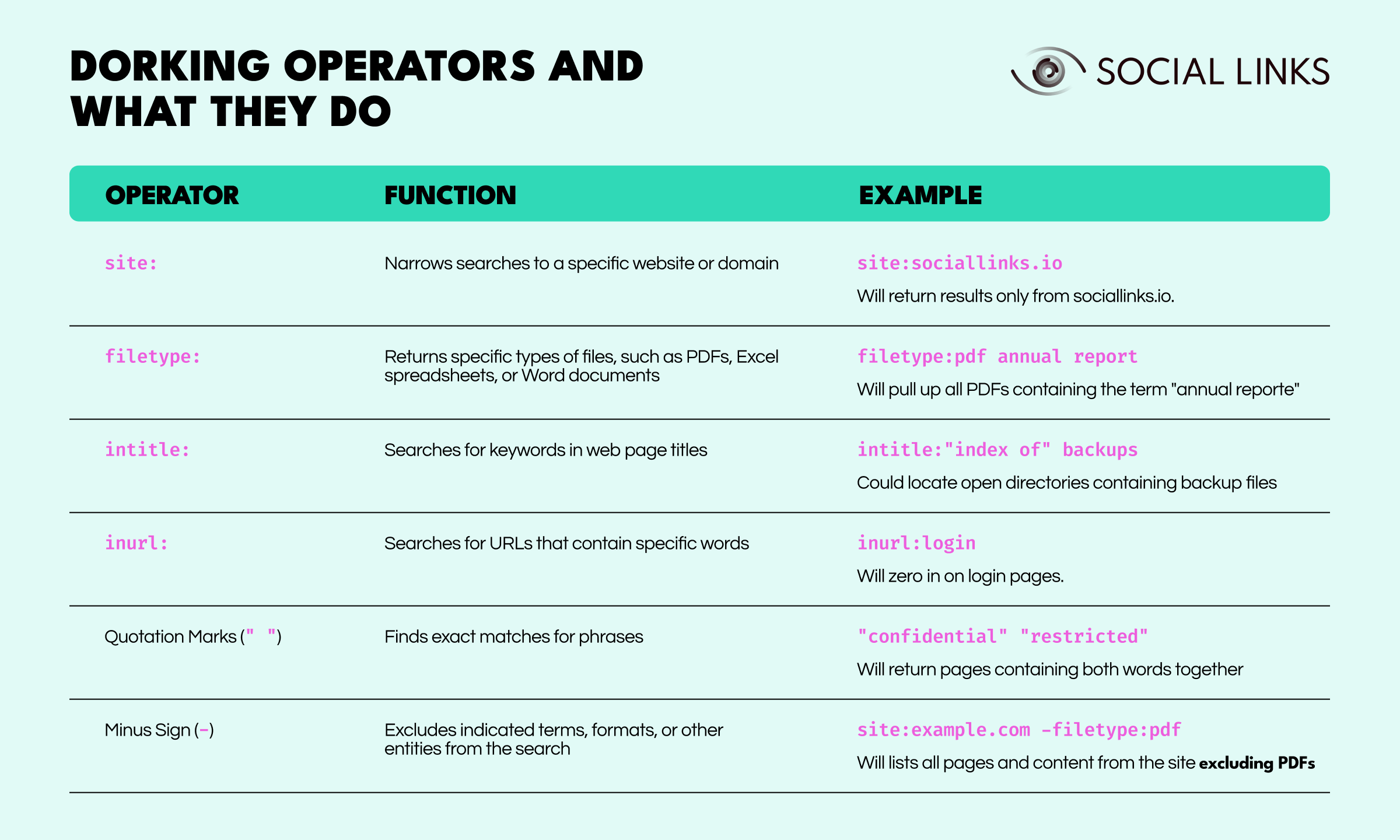
While these operators may all be useful on their own, Google Dorking techniques tend to deliver more finely-tuned—and therefore incisive—results when the operators are judiciously deployed in combination. For instance: site:gov filetype:xlsx budget would return all publicly accessible government spreadsheets related to budgets.
Google Dorking techniques are a highly effective weapon in the armoury of an OSINT practitioner. In fact, it could make the difference between spending hours looking for a single name and jumping straight to a eureka moment. Here are some approaches that you can try out today in any browser to extract specific information:
It’s not unusual for files containing sensitive data—server credentials, API keys, login details, etc.—to wind up online by mistake. Finding such data may have many crucial applications, from safeguarding a company or investigating a suspect.
Understanding an organization’s infrastructure can be crucial in a range of OSINT investigations.
It can happen that documents of a sensitive nature intended to remain private are inadvertently indexed by Google. Weeding out such loose ends can be essential for maintaining corporate security.
Exposed databases can be a major cybersecurity risk.
Another major benefit of SL Crimewall is that a google dorking functionality is natively incorporated into the solution itself, meaning it can be deployed in the context of an ongoing project and all within one platform, as opposed to jumping between a browser and a data visualization tool.
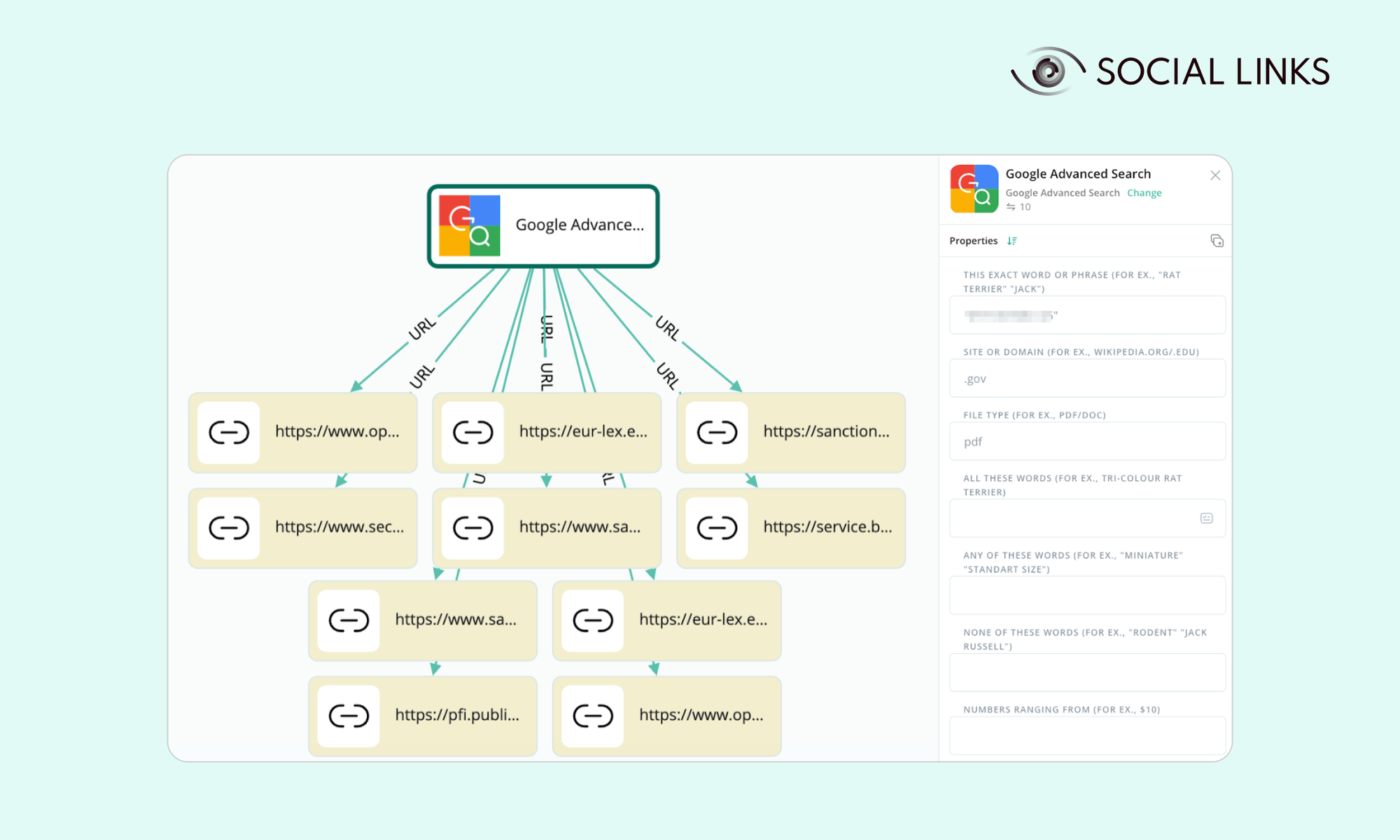
What’s more, dorking from within Crimewall is actually easier and more intuitive than through a browser. Having launched the Google Advanced Search feature, you’ll see a properties tab on the right (see below). This gives you the major operators as fields where you can simply input the combinations and commands relevant to your search—a super easy way to conduct a highly refined google search, right from within the investigation platform.
Here are some examples of dorking queries that can be launched directly from with SL Crimewall:
Query: "name" filetype:pdf site:.gov
This query will return PDF documents from government websites (.gov) that include a specific individual’s name. This can be useful for locating official reports, court filings, or publicly available records that reference the person in question.
Query: intext:"proftpd.conf" "index of"
This dork looks for indexed directories containing the text “proftpd.conf”—the configuration file for the ProFTPD FTP server. If found in a publicly accessible directory, this could mean that server credentials, user permissions, and operational settings have been exposed, posing a potentially costly security risk.
Query: intitle:"SSL Network Extender Login" -checkpoint.com
This search is linked to CVE-2024-24919, a major vulnerability affecting Check Point Security Gateway devices, whereby attackers can read arbitrary files on affected devices. This may put local password hashes and other sensitive data at risk of exposure.
By excluding results from checkpoint.com, this dork focuses on third-party or self-hosted instances, where security updates might not have been applied. This allows security specialists to identify potential vulnerabilities and take action before they develop into breaches.
While Google Dorking is a more expansive practice than the applications we’ve outlined today, we hope these examples serve as a good starting point for integrating a truly valuable set of techniques and extraction methods into your investigation approaches.
If you want to learn more about SL Crimewall, follow the link below and we’ll set up a personalized demo with one of our specialists, where you can see the benefits the platform can bring to your specific workflows.