iPhone to iFortress: Using OSINT to Secure your Device


When people think about iPhone security, they usually imagine theft—someone grabbing the device off a table or slipping it out of a pocket. But in the world of Open-Source Intelligence (OSINT), the real danger isn’t just losing the phone itself. It’s what can be seen, linked, or inferred from the data inside it. Every message, photo, and login leaves a digital trace that can be collected, cross-referenced, and weaponized.
This article explores practical OSINT-based techniques to take your iPhone security to the next level. By understanding how threat actors analyze data, you can see your device the way they do—and protect it before they ever get the chance to exploit it.
The numbers speak for themselves. Only 26.5% of passwords analyzed in recent studies meet modern security standards. The rest rely on predictable patterns like “password,” “123456,” or “admin.” Among corporate credentials, weak-password rates range from 71% to 92%, making internal access one of the easiest targets for attackers.
AI has made the situation worse. According to a study by Deloitte, the rise of AI-driven phishing campaigns has led to a 1,265% increase in phishing attacks, with over 80% of phishing emails now being gen-AI productions. These scams are smarter, faster, and eerily personal— mimicking human language and exploiting weak or reused logins with frightening precision. Experts estimate that AI-related fraud will grow from $12.3 billion in 2023 to $40 billion by 2027.
In short, the weakest link when it comes to security is the human element—the predictable patterns, lazy passwords, and forgotten settings that open the door. Strengthening your digital hygiene is not just about privacy; it’s about denying attackers the building blocks they need to reconstruct your life.
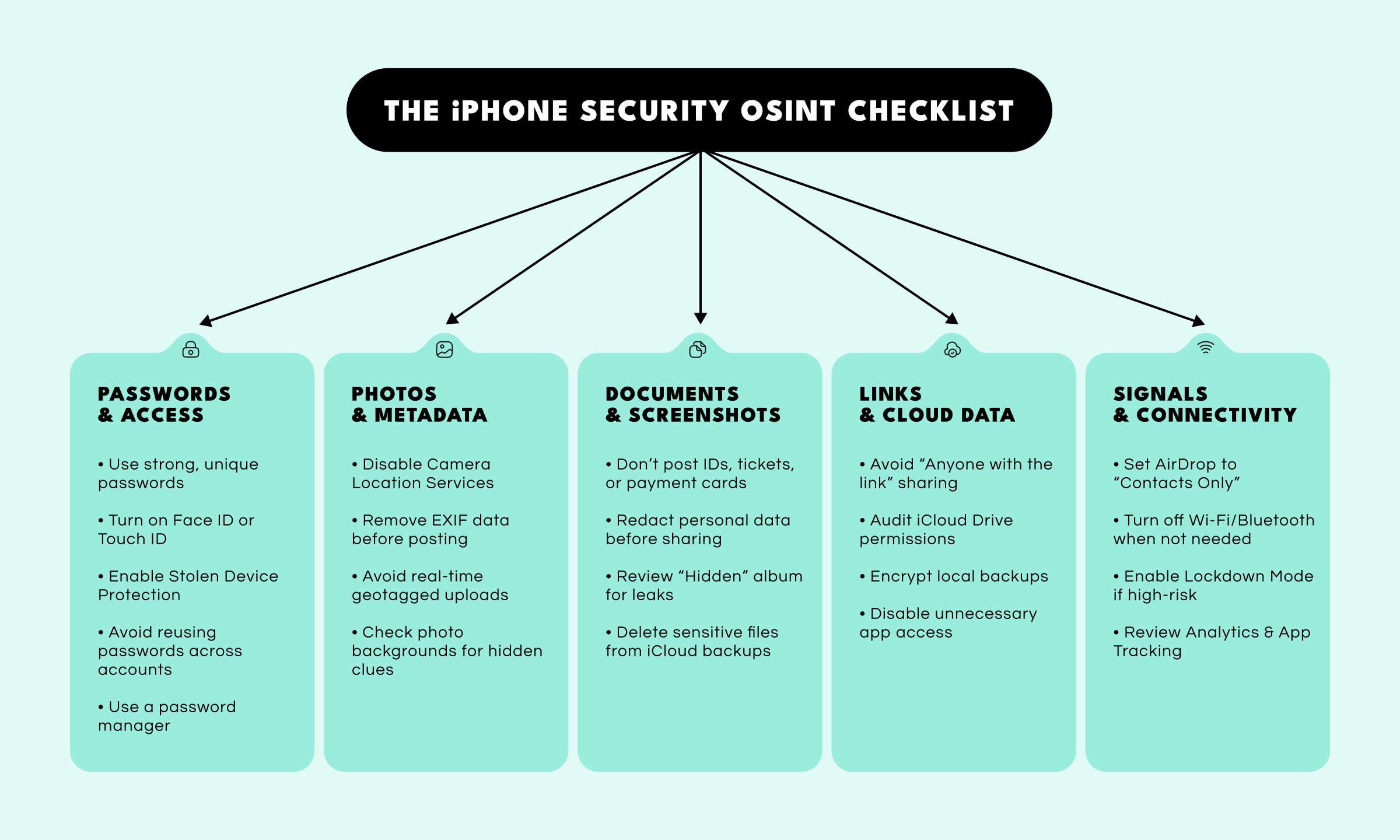
Your passcode is the gatekeeper of your digital identity. Weak or reused credentials are among the easiest ways for attackers to gain access, especially when they combine public breach data or social media clues to guess your password.
Photos of documents, cards, or even cropped screenshots can reveal more than you expect. Modern OCR tools and AI-powered vision systems can read blurred or partially obscured text with alarming accuracy.
Shared links are one of the most common yet overlooked sources of leaks. iCloud Drive, Notes, and shared albums can all expose data publicly if permissions are too broad.
Your iPhone constantly emits signals—Wi-Fi networks, Bluetooth devices, AirDrop visibility—that can be tracked or correlated with your movements. These breadcrumbs can reveal patterns of life or expose your device to proximity-based exploits.
OSINT isn’t just a tool for investigators—it’s a mindset. Understanding how data connects is the first step toward protecting it. The same methods analysts use to uncover digital footprints can help you recognize and close your own exposure points.
Want to see how OSINT principles can enhance your digital security and investigative workflows? Book a personalized demo with one of our specialists and discover how Crimewall helps analysts visualize, correlate, and protect data across open sources, all within one unified platform.