Maltego Part 7: On a black-black night, on a dire Darknet, one shady account


Learn how to how to perform OSINT data search on the Dark Net
Darknet. Oh, how much there is to say. Both pathos, horror, and misunderstanding at once. Especially from the side of the media and others who are not very into it. The Darknet is the same Internet, but it exists in its original, pristine state, which has no corporate or government regulation.
And today, we'll talk about how to perform OSINT data search using this same part of the World Wide Web.
For the correct demonstration of the methods, I will use working examples already known to find information. They are not fully real but still too representative. All information given in this article is for information purposes only. Well, let's be honest: OSINT on the Darknet forums is not the same as searching for your former classmates on VK and not what you will do in the framework of standard OSINT cases anyway.
This article will describe methods from my personal experience where I turned to the Darknet to do my search.
Sometimes an employer, especially a large one, has reasonable questions: "Do my employees trade insider information?" or "Is our new candidate for the position of X entirely in the clear"? Here comes the test of both the employee's biography and their behavior in social networks. But sometimes, to answer the questions above, you need to dig even more profound. And here, Maltego can come to our aid.
We will check a specific individual, Tina Thomson (Tina Tomson), from Berlin, for illegal dealings. First, we take the known information about the employee and fill it into the form. We know the location (Berlin), Name and Surname (Tina Thomson), and her email address (tin.ka0186@gmail.com).
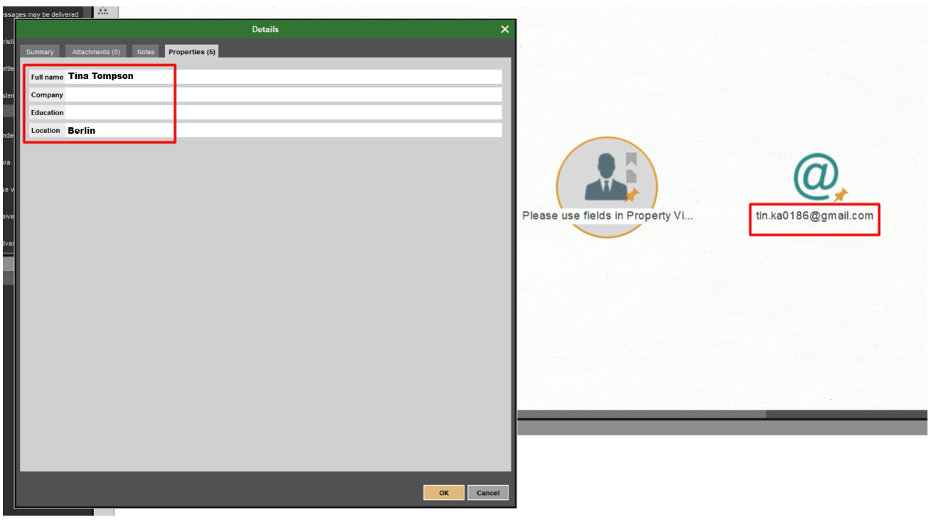
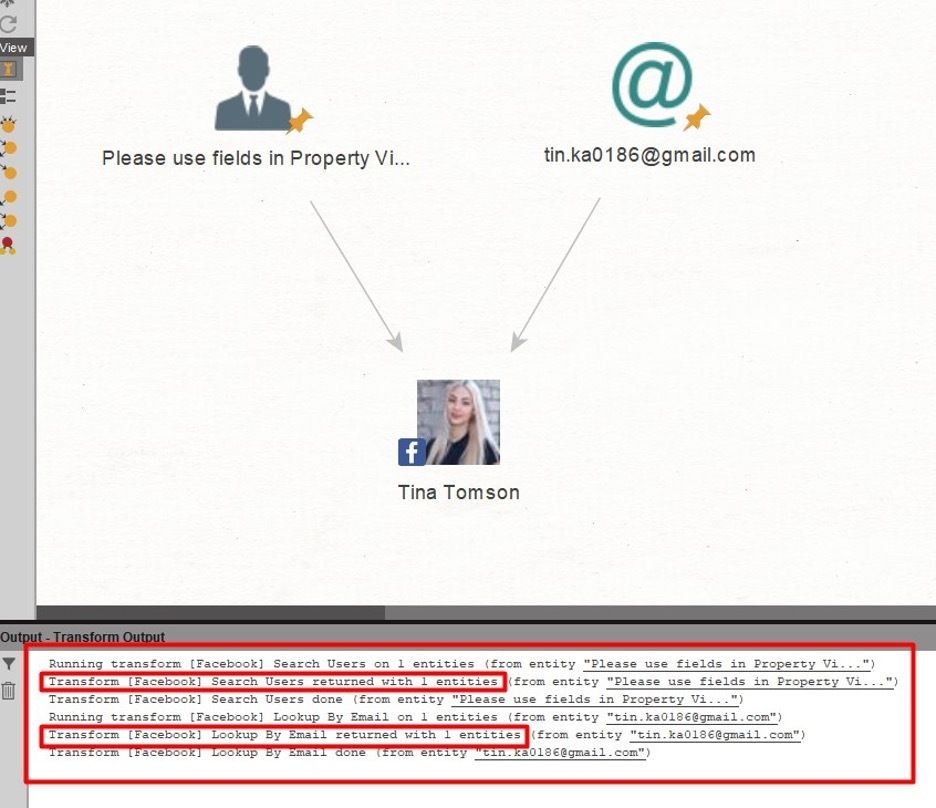
Using 'Entity: Search Person,’ we launch 'Transform: [Facebook] Search Users' and get Tina's Facebook account.
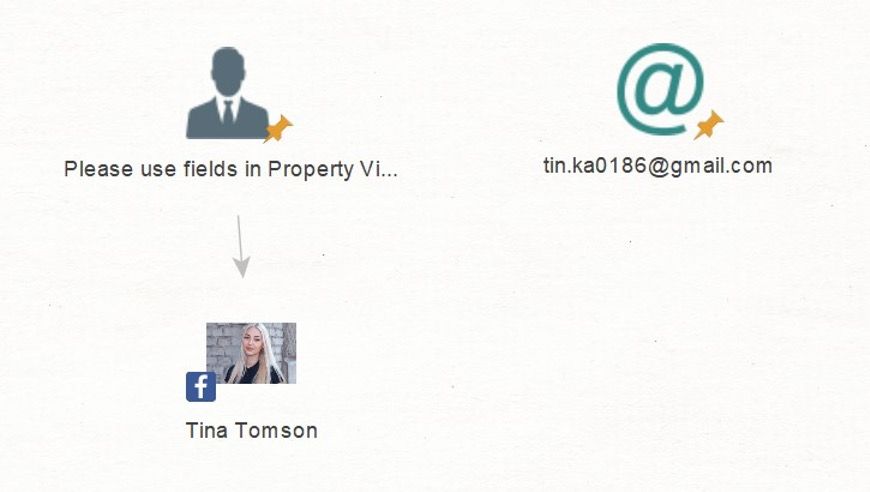
For 'Entity: Email Address', we'll run 'Transform: [Facebook] Lookup By Email'. Maltego faithfully finds the same account then confirms that this is the right person.
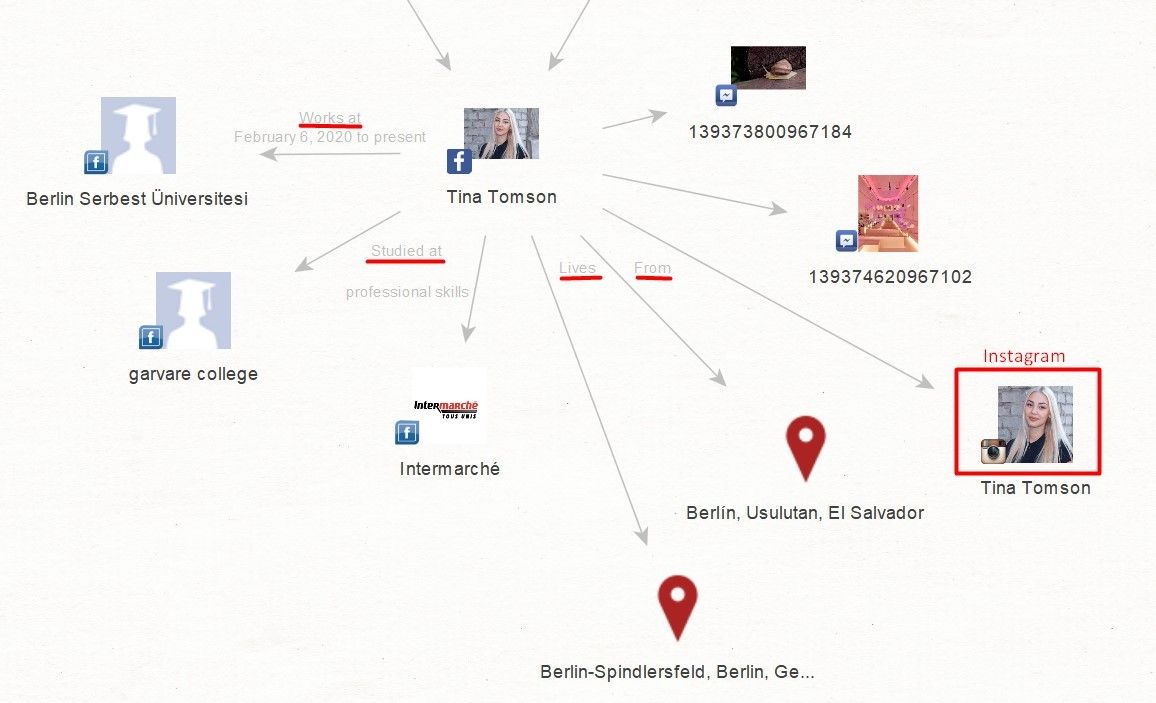
We move on and make a query for all the data from her Facebook page to be put in one graph by running 'Transform: [Facebook] Get User Details.’ We get additional information about her workplace, study, or residence (if this information is on her Facebook profile). The bonus is her Instagram account.
Now I will show you a jibe that I have already demonstrated in my previous article. We will need to process both accounts by running 'Transform: [Convert] To Entities From Profile' and get the assumed aliases of a person.
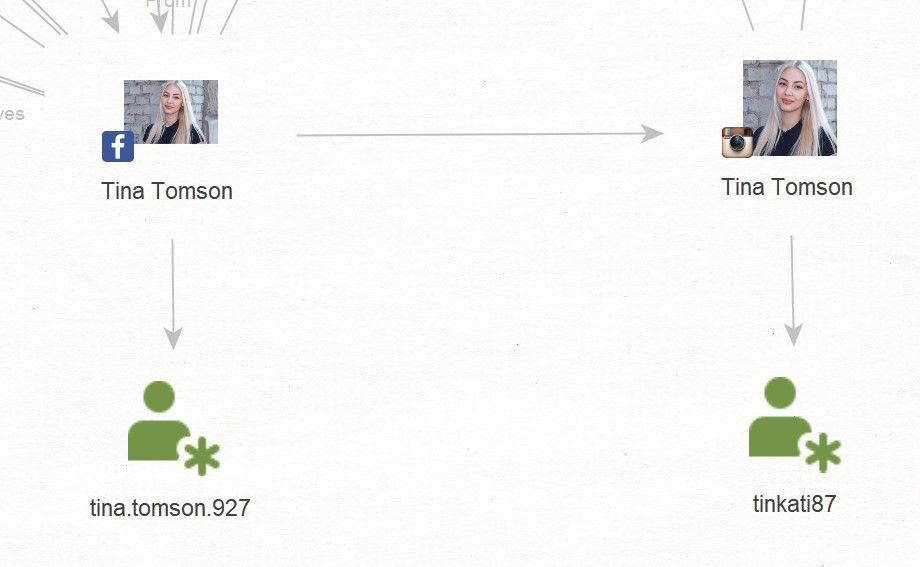
Now we have the first two starting points with which we can search in forums on the Darknet – these are users with the nickname tina.Tomson.927 and tinka87.
Run 'Transform: [Darknet] Search User' for both aliases and see the result.
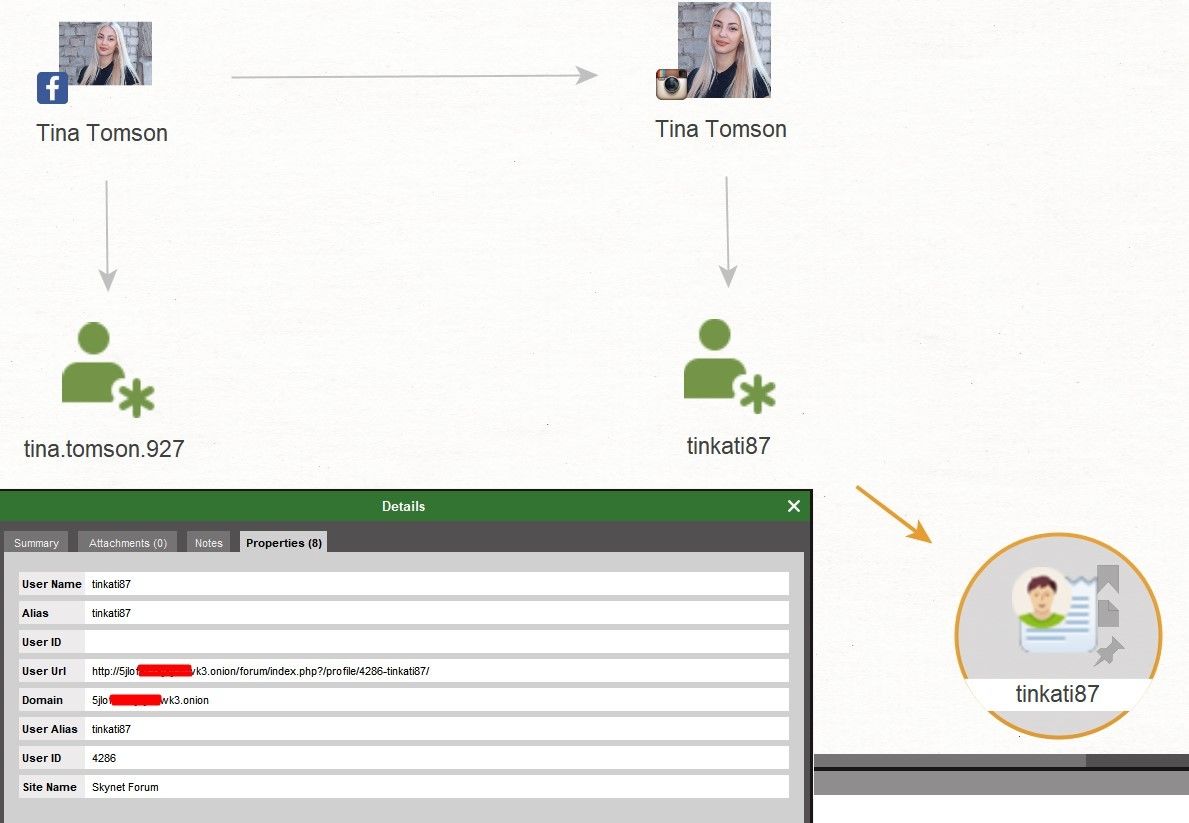
Here's the user. On a specific Skynet Forum, there is a user with the nickname tinkati87 at the following address: 5jloxxxxxxwk3.onion (changed because it is a bad idea to throw around links to the Darknet forums). This is already suspicious!
Let's check what this user is writing. To do this, run 'Transform: [Darknet] User Posts'.
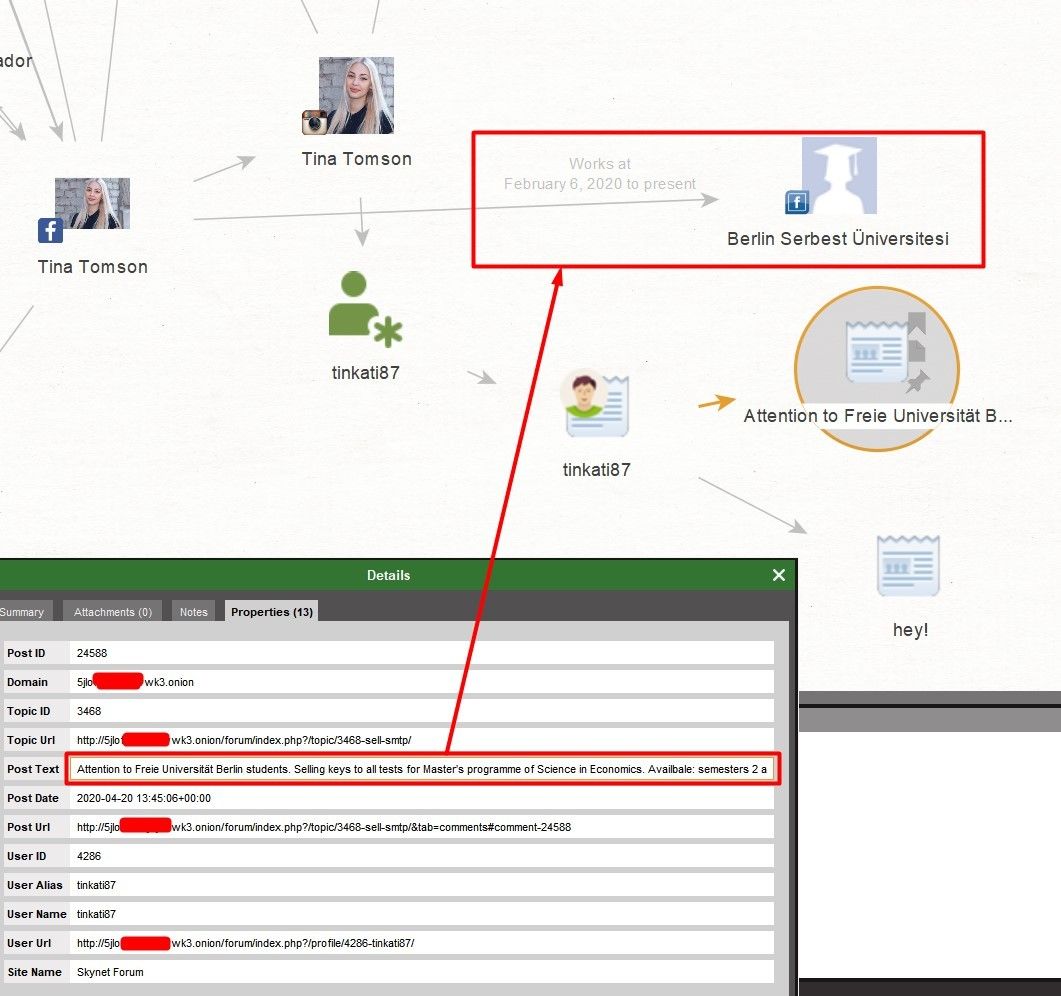
Here's the proof. A user under the nickname tinkati87 on the Skynet Forum sells answers to exam tests at the University of Berlin. And as we have already established earlier, this is where she works. And she is on Instagram under the same nickname. We can also download the forum topic to the graph and retrieve the accounts of those other users who participate in the discussion so that in the future, we can try to identify students who may have bought the answers to the test from her.
Another exciting feature is the ability to download the entire forum web page directly from Maltego. And please note, we were able to do the entire investigation without visiting this forum or *.onion sites even once.
There is one common practice on the Darknet, which is to use PGP keys to encrypt emails. However, these keys can play a dirty trick to the owner if they fall into the wrong hands.
You may ask how? Simple! The PGP key often contains information about the email address that it is attributed to. Can you see where I am leading you in relation to the Dark Net? For this case, in particular, I generated such a key. Upload it to 'Entity: PGP Open Key' and do the magic by 'Transform: [Convert] PGP To Email'.
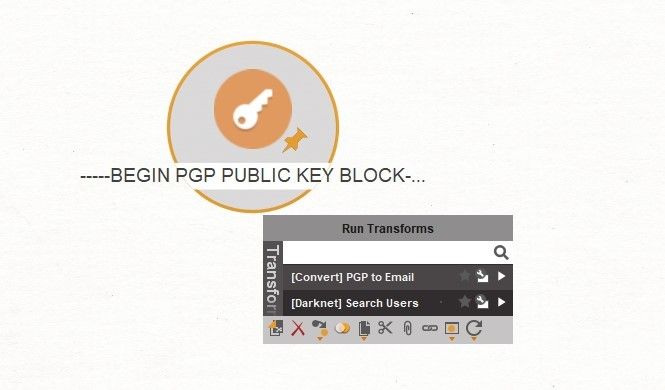
Voila! We have an email address.
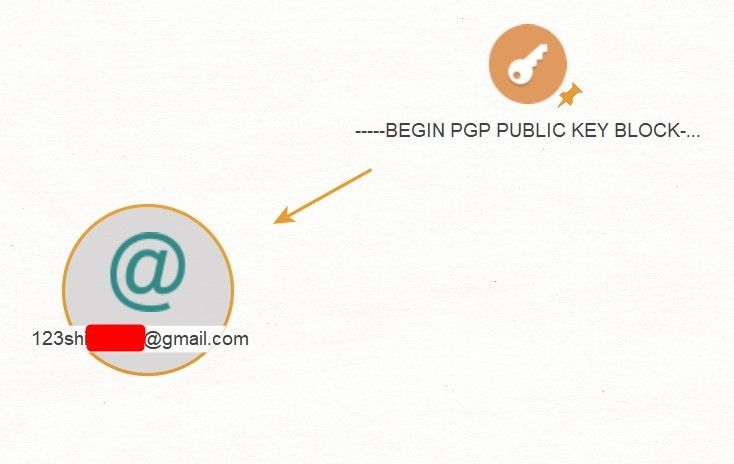
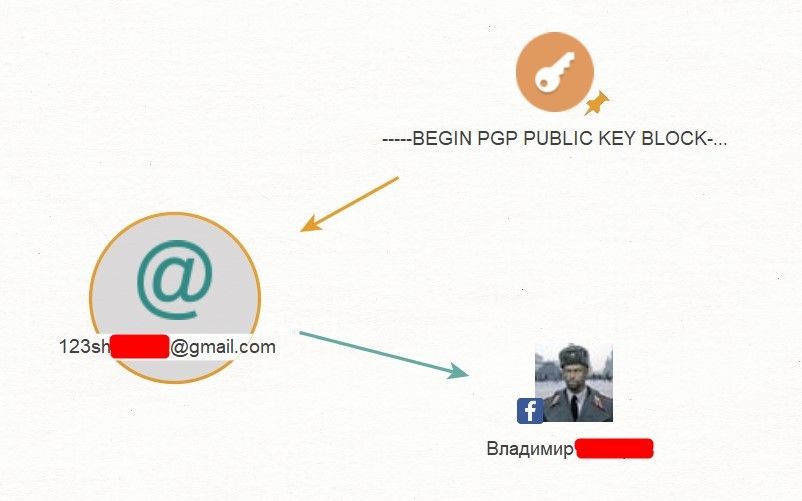
What should we do next? Let's look for the same account on Facebook. Run 'Transform: [Facebook] Lookup By Email' and, as a result, we get a Facebook account.
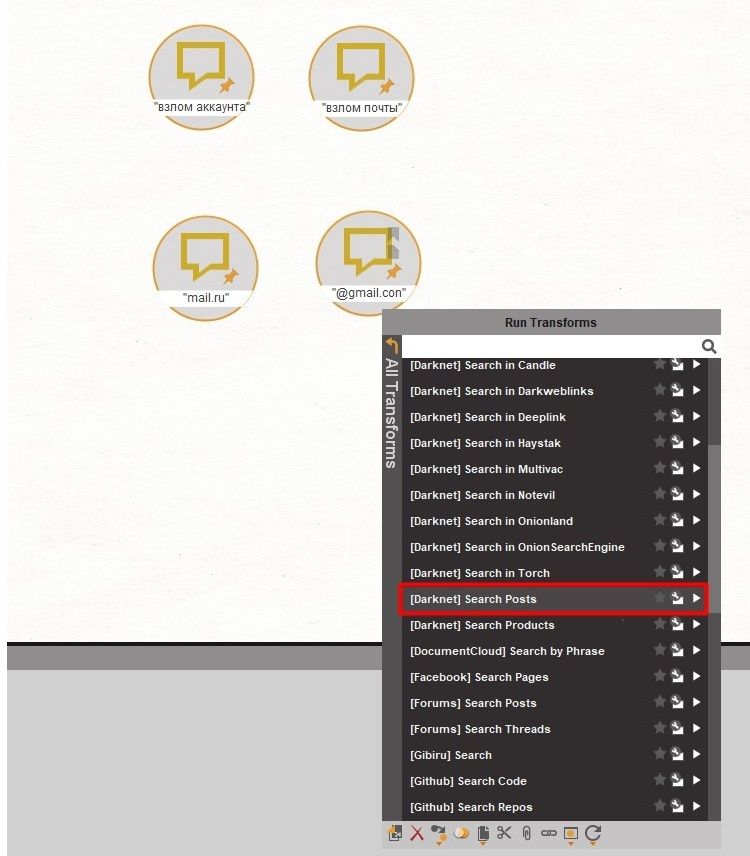
Now let's get down to something more interesting – search for information by given keywords. It's like Google. Take 'Entity: Phrase' and set the required word/sentence there. Apply 'Transform: [Darknet] Search Posts' and get various posts on various forums that contain this phrase.
In addition to forum searches, you can also do product searches on relevant sites. The same Entity will help us here, but now we will run 'Transform: [Dark Net] Search Products.’ In search results, we will get links to the 'items.'
You can also search for products using 'Entity: Location.’ Here we can use Transforms to search for delivery to the location or from it. [Darknet] Search Products (shipping from) and [Darknet] Search Products (shipping to).
As always with the Darknet – there are goods for all tastes. From firearms to cash.
That's all for today. Don't forget that the Darknet can be a great source of information, as much as Google. The main thing is to know how to search.