May's OSINT News: NFT Troubles, The Rise of Ransomware-as-a-Service, and Internet ‘Balkanization’


The digital realm has never been more insecure than it is today. It seems we readily embrace new technologies and services without question, whether it’s blockchains, NFTs, or the so-called metaverse. However, all technology has its flipside – digital assets are far more vulnerable than is generally accepted, while the metaverse could potentially be leveraged to train combatants and collect behavioral data in a way that undermines privacy rights. The brave new digital world will certainly cut both ways.
NFT’s are prone to a number of security issues, which investors should probably take seriously.
There’s a general assumption that owning an NFT means you own the content it’s connected to. Unfortunately, this is not the case. In fact, NFTs do not provide you with sole ownership of an item, but rather a mere indication of the item on a single blockchain. Such securities only contain a link to an asset that is stored elsewhere, and the owner has no control over the place – or server – where it is actually stored.
While the blockchain itself is essentially immune to alteration, this does not make NFTs secure assets. This is partly because thieves have no need to mess with the blockchain, they can appropriate assets by simply infiltrating the servers where they are downloaded from.
The only evidence of your right to an NFT is its key. This means the securities are more in the nature of a type of access as opposed to real ownership – if your key is stolen, there is practically no chance that you’ll be able to claim ownership of the asset. This is why NFTs are called tokens - they are exactly that. Like chips in a game of poker, they are mere representations of the assets rather than assets themselves. So, to continue the analogy - you can’t claim your actual winnings in a casino if you’ve lost your chips.
Also, social engineering - especially phishing - is a notoriously effective method for stealing NFTs. As a recent example, Todd Kramer, the owner of an art gallery in Chelsea recently lost $2,3 mln worth NFTs in a phishing scam.
Furthermore, NFTs can actually be frozen by the marketplaces on which they are being traded, providing the said marketplace is controlling the relevant blockchain. This is another potential pitfall of investing in these assets. There have been reports of investors unwittingly buying stolen NFTs, only to have them frozen shortly thereafter.
An NFT can be exclusive only on a single blockchain. However, an unlimited number of blockchains can be created on the market, and you can never be sure that there isn’t the exact same object being traded as an NFT on another platform. For example, the Rarible marketplace simultaneously maintains four blockchains for NFTs, leading to numerous cases of copycat assets - around 80% of NFTs are in fact plagiarism, fraud or spam.
Since it’s practically impossible to distinguish between original NFTs and their plagiarized counterparts, this greatly diminishes the value of NFTs in mass culture.
The figures on ransomware are becoming alarming. The FBI’s Cyber Division has recently reported that between 2019 and 2021, the number of ransomware complaints rose by 82%, while the number of ransomware payouts more than quadrupled (449%).
Meanwhile, in Palo Alto Networks’ Unit 42 2022 ransomware threat report, it was announced that 2021 saw the average ransom demand rise 144% to $2.2 million, with average payout amounts increasing by 78% to $541,010.
With the statistics spiraling, it’s well worth asking what the drivers are here, and it seems that one significant factor is the emergence of Ransom-as-a-Service (RaaS) packages, which almost anyone can purchase on Dark-Web marketplaces. These are essentially start-up and support kits for anyone who fancies a foray into digital extortion. And they come in different varieties. Sugar, for example, demands a low ransom of $4 dollars-worth of Bitcoin and is moreover used to target individuals or small enterprises. And then you have the big dogs such as BlackCat, that can set the ransom at any amount from two thousand to three million dollars in crypto.
At the recent 2022 CyberUK conference, technical director of the UK’s National Cyber Security Center Ian Levy said that we might be heading towards global fracturing of the internet into independent ‘nation-states’ – that is, partially or fully sovereign internet domains with their very own defense or expansion policies.
Clearly a reference to the break-up of the former Yugoslavian state, the term balkanization was coined by political scientists and journalists to refer to a collapse of a united organization into independent parts that each have the means necessary to fight for independence and maintain their self-determination.
Firstly, with political and military concerns becoming ever more embedded throughout the cyber domain - from electoral hacking and Twitter diplomacy to direct cyber warfare such as denial-of-service sabotage: some countries invest more in their own cyber defense solutions because they can necessarily trust that solutions from global corporations will share their security concerns.
As we all know, China has been building its own cyber infrastructure both physically and digitally for a long time now, and with the Belt and Road Initiative the Asian superpower is expanding its digital empire. China is bankrolling infrastructural development across Asia, Africa and even the Balkans, which, for these countries, can come at the cost of technological and financial dependence. Meanwhile, other powers such as Russia and India are developing their own sovereign cyber infrastructures for digital autonomy.
The tech domination of America is apparently waning. While the global digital infrastructure was once provided mostly by US corporate giants such as Cisco or Microsoft, we are now witnessing two disrupting trends. Firstly, the growing popularity of open-source software and development frameworks allows independent studios to produce their own products of a sufficient quality. Secondly, Chinese corporations such as Huawei are successfully competing with their American counterparts with around 80% of the chairs and vice-chairs in telecom equipment standard bodies representing Chinese firms.
William Gibson’s cyberpunk stories with the cyberspace divided between the superpowers doesn’t appear as far-fetched as it seemed in the 1980s.
The ‘Metaverse’ may still feel like a slightly hazy buzzword, some of its central concepts are having a distinct influence on the way military training is being carried out in the modern world. While 3D computer modeling and battle simulations will be familiar to anyone who’s played a first-person shooter, such scenarios are now being extended into AR and VR environments for training military forces.
Large-scale operations can now be carried out in the most sophisticated and realistic virtual simulations to hone the skills of infantry, fighter pilots, and even generals. Meanwhile, AI is being harnessed with algorithms that learn from every outcome of an offensive to improve military tactics with every iteration.
The US army is now in the middle of building its own metaverse with the help of top VR/AR developers - both corporations and startups. DARPA, or, the Defense Advanced Research Projects Agency, is anything but underfinanced, and have consequently been able to develop a host of bleeding-edge combat simulation set-ups. These have included the first VR dogfight, and pilots in real Berkut jets are using augmented reality to practice complicated maneuvers such as mid-flight refueling.
At the same time, military VR developer Red6 is collecting an array of data of the specs of military machines and geospatial and climatic information to model perfect simulations of military operations. Full-scale battles are then fought out in a virtual environment against an adversary whose reactions and strategies are controlled by AI.
Such simulations can include up to 10,000 combatants, with some being controlled by human agency, and others are AI-manipulated. The data of combatants’ behavior can then be analyzed to instruct officers and soldiers to be more effective on the battleground and inform overall tactics. In essence, entire wars can be fought virtually to test the waters before any actual military power is deployed.
Furthermore, Palantir, a prominent developer of analytic platforms, is investing in such firms, including Red6. Global defense lead at Palantir told WIRED that such systems are the key to data-driven military strategy and the corporation is going to implement these data sources in its own platform.
And finally, the UK government has implemented a secondary school program which includes the teaching of open-source intelligence.The course is called Cyber Explorers, and aims to educate some 30 thousand secondary school pupils between the ages of 11 and 14 on a range of cybersecurity skills, including open-source intelligence (OSINT), digital forensics and social engineering.
The program is being carried out in an online format with pupils learning the basics of cybersecurity, recognising potential career paths in the digital sphere, such as social media marketing and analytics.
The initiative is a part of a national cyber strategy geared towards developing cybersecurity competence and skill-sets among UK citizens in the cybersecurity sphere to the UK citizens, and was launched on 23 February, 2022.
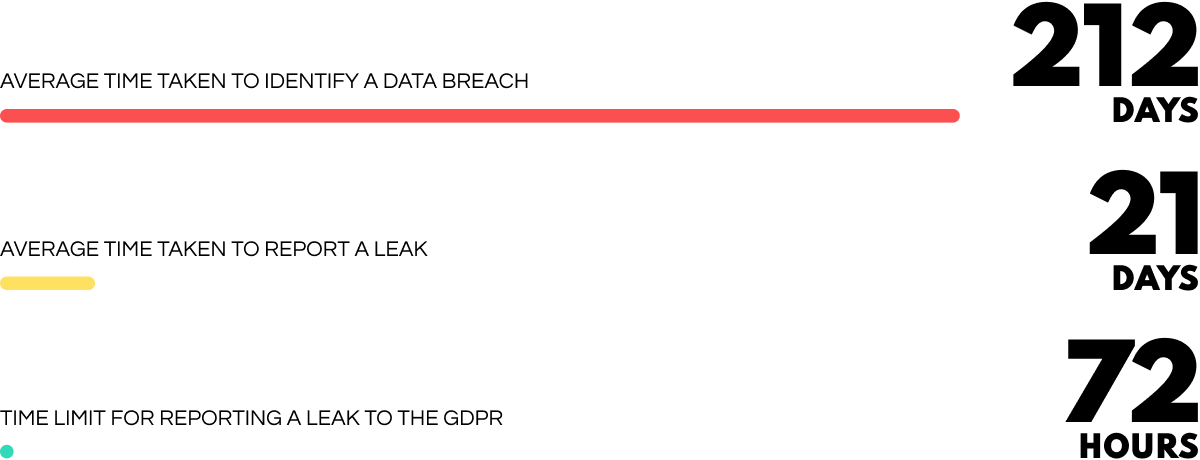
The cost of data leaks is hitting new highs. On average, breach lifecycles under 200 days cost $1.26 million less than those which exceed 200 days. By the time organizations realize a leak has occurred that time has already passed. Furthermore, by failing to report the leak within the regulatory time, organizations often have to fork out a further €10 million or 2% of annual global turnover.
YouTube is one of the biggest sources of fake news and political disinformation. In a recent example, WIRED has demonstrated that YouTube propaganda and misinformation helped the current Philippines president win in the elections, while the previous government controlled public opinion through the same platform by recasting their own unappealing biographies.
The EU is working on a law to allow private chat scanning. While this law is positioned as a countermeasure to the circulation of illicit content, it raises significant questions about privacy rights. If the law is passed and put into effect, it will end the era of end-to-end chat encryption that has been an essential aspect of modern messaging apps (sorry Telegram).
Discord has become a new place for crypto ransomware activities. You should tread carefully with regards to what links you follow.
New Research: The top 100k websites may collect everything you type without even hitting return. A multitude of websites are using keyloggers to record what you typed whether you entered it or not.
UK introduces its national cybersecurity strategy for a nuclear energy program. The UK sets out cybersecurity plans for a civil nuclear sector, with a focus on testing, security, and collaboration.
British thugs are studying the basics of crypto to get more out of their muggings. Cyber-savvy gangs are extorting crypto payouts via threats.
And that rounds of the Social Links digest for May. We hope you found it all to be of interest, and keep your eyes peeled for next month’s edition!