Military Intelligence: Operational Intelligence in the Multi-Domain Era


Modern defense operations depend on timely, reliable intelligence. Military intelligence transforms fragmented data from multiple domains into structured insight that informs strategic decisions. In an environment where threats span physical and digital terrain, this capability is foundational to effective command and control.
In this article, we explain how military intelligence works in practice, how the intelligence cycle supports operational planning, and how a military intelligence agency integrates collection, analysis, governance, and decision-making. We also explore military intelligence analysis tools, cyber intelligence military capabilities, military police intelligence, and the role of military intelligence websites in modern information environments.
Military intelligence is the collection, processing, analysis, and distribution of information that supports defense operations and national security. Its purpose is to reduce uncertainty and help leaders act with confidence at strategic, operational, and tactical levels.
At its core, this function supports:
Unlike many civilian intelligence activities, this discipline operates under tight timelines and in contested environments. Information must be accurate, relevant, and delivered quickly. Delays or gaps can directly affect mission outcomes.
It combines signals intelligence, geospatial intelligence, open-source intelligence, network intelligence, and human reporting into a coordinated system designed to support armed forces in real time.
To understand how the system operates, it helps to view it as a layered model—the military intelligence stack. This framework shows how four interconnected layers work together: governance, collection, analysis, and decision-making.
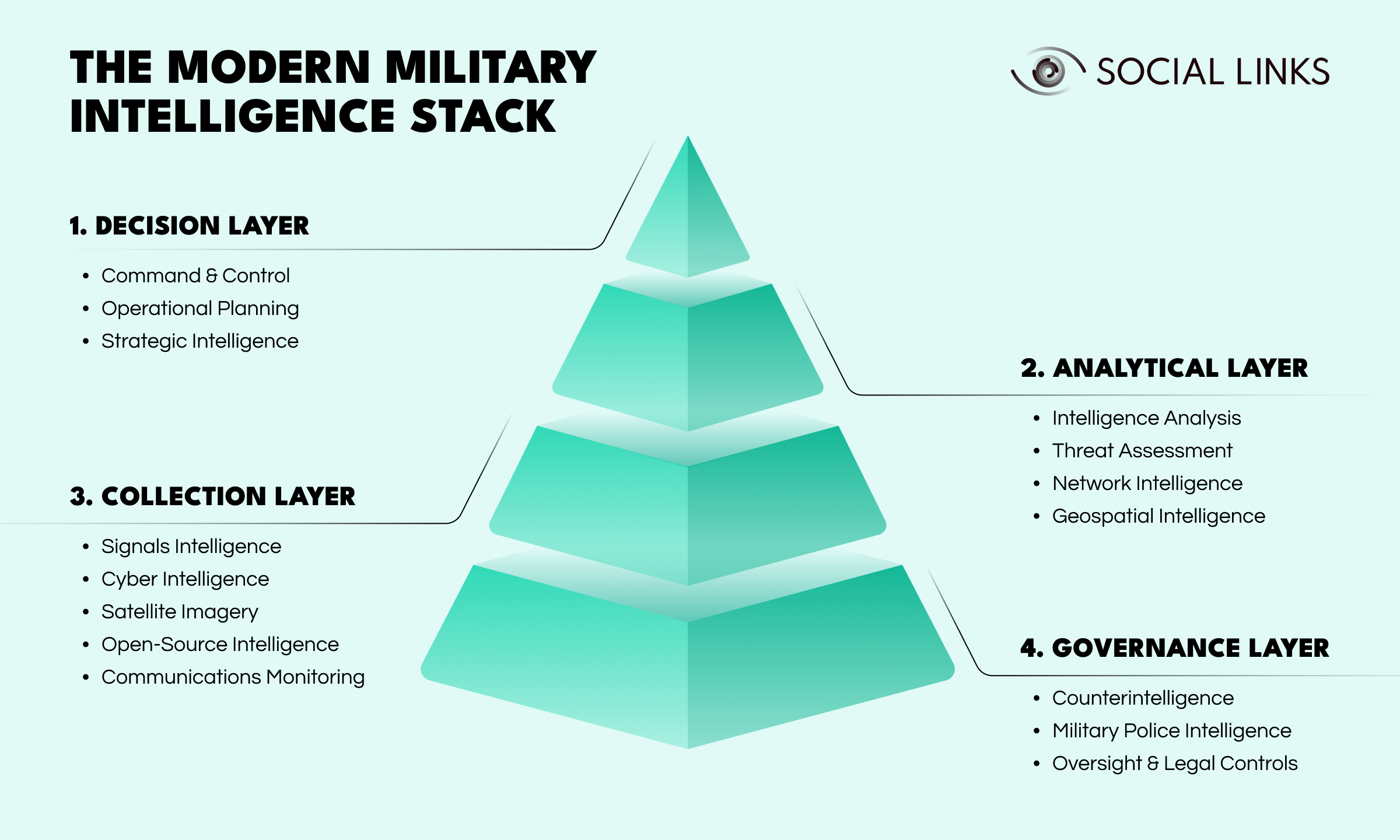
The governance layer ensures internal security and accountability. It includes counterintelligence, military police intelligence, and oversight controls.
This layer protects classified systems, reduces insider threats, and ensures intelligence activities comply with legal and ethical standards. Without governance, even technically strong systems can become liabilities.
The collection layer gathers data through:
Effective collection aligns with mission requirements. Gathering more data does not automatically improve quality.
The analytical layer turns raw inputs into usable insight. Through intelligence analysis, threat assessment, network intelligence, and geospatial intelligence, analysts identify patterns, assess risks, and produce operational conclusions.
This is where information becomes understanding.
At the top of the stack is the decision layer. This supports command and control, operational planning, and strategic direction. Intelligence has value only when it informs action. Analysis that does not reach decision-makers in time does not shape outcomes.
Agencies operate across all four layers, and effectiveness depends on how well these components function together.
While the stack explains structure, the intelligence cycle explains process. It describes how information moves from requirement to decision. Although terminology varies across doctrines, the stages generally include:
Commanders define intelligence requirements aligned with mission objectives. Clear direction prevents collection from becoming volume-driven rather than purpose-driven. Requirements shape activity across all layers.
Information is gathered through:
This stage aligns closely with the collection layer of the intelligence stack.
Raw data is translated, decrypted, structured, or formatted for analysis. Automation increasingly supports this stage due to large-scale sensor and network data. Processing connects collection to analysis.
Analysts assess reliability, identify patterns, and evaluate likely outcomes. This corresponds directly to the analytical layer.
Core tasks include:
Findings are delivered to decision-makers in formats suitable for command environments. Effective dissemination ensures insight reaches the decision layer in time to matter.
Operational outcomes refine future requirements and collection priorities. Feedback strengthens the system over time.
The cycle describes the flow of information. The stack describes how the capability is organized. Together, they explain how structured intelligence supports operational clarity.
A military intelligence agency exists to provide decision advantage to armed forces and defense leadership.
Typical responsibilities include:
For example, in the United States, Department of Defense components coordinate with organizations such as the Defense Intelligence Agency (DIA). Similar structures exist across NATO and allied systems.
An agency functions across the entire stack by:
Coordination often presents greater challenges than collection itself. Classification rules, operational security, and national caveats influence how information is shared across organizations.
Modern defense operations generate large volumes of data from sensors, communications monitoring, satellite imagery, and public data sources. Structured methods and military intelligence analysis tools are essential to manage this scale.
Common approaches include:
These methods reduce bias and improve consistency in assessments.
Military intelligence analysis tools support:
These platforms accelerate processing and collaboration, but judgment and credibility assessment remain human responsibilities. Analysts evaluate context, credibility, and operational relevance.
Modern systems increasingly integrate cyber threat intelligence feeds, satellite imagery layers, communications metadata, and open-source intelligence into unified platforms.
Cyber intelligence military capabilities are central to defense operations because modern armed forces depend on digital infrastructure.
Core functions include:
Cyber operations can disrupt communications, logistics, and command systems before physical engagement begins. Cyber capability extends situational awareness into digital environments where adversaries operate without physical presence.
Military police intelligence operates primarily within the governance layer and focuses on internal security and military law enforcement.
Key responsibilities include:
While other disciplines focus outward, this function strengthens institutional integrity from within.
Open-source intelligence now provides measurable operational value in modern military planning.
Military intelligence websites and public data sources can provide:
Open-source intelligence complements classified collection by providing scalable context and independent validation. It strengthens the collection layer when properly evaluated.
However, public sources require verification and structured analysis before incorporation into operational assessments. Open-source material cannot replace classified intelligence for time-sensitive operational planning or access-restricted environments.
Military intelligence faces structural challenges:
It also operates within legal and ethical constraints, including domestic law, international humanitarian law, and formal oversight mechanisms.
The governance layer ensures compliance and accountability. Effective intelligence balances operational necessity with legal discipline and institutional oversight.
Military intelligence functions as an integrated system connecting collection, analysis, governance, and decision-making. Its effectiveness depends less on data volume and more on integration quality.
In modern defense operations, intelligence must move efficiently from sensors to analysts to commanders. When these layers align, uncertainty drops and decision speed improves across domains.
It provides threat assessment, situational awareness, and structured analysis to support operational planning and command decisions. By integrating collection, analysis, governance, and decision-making, it reduces uncertainty across domains.
A military intelligence agency collects, analyzes, and distributes information relevant to national defense. It supports strategic intelligence, battlefield intelligence, counterintelligence, and coordination across defense structures.
Military intelligence analysis tools integrate data from signals intelligence, geospatial intelligence, cyber intelligence military systems, and open-source intelligence. They help analysts visualize networks, identify patterns, and support command and control decisions.
Cyber intelligence military capability focuses on network intelligence, digital surveillance, and cyber threat intelligence within military systems. It complements traditional battlefield intelligence by extending visibility into digital infrastructure.
Military intelligence websites can provide useful open-source material and contextual data. However, they should be evaluated carefully and corroborated through structured analysis to ensure reliability and operational relevance.
Want to see how structured intelligence platforms enhance situational awareness across complex defense environments? Book a personalized demo with one of our specialists and discover how SL Crimewall supports intelligence analysis, network mapping, and multi-source data fusion—helping teams move from fragmented information to coordinated decision advantage.