November’s OSINT News: New Algorithm for ‘Webcam Peeking’, Festive Phishing, and… Introducing the Social Links Glossary


Welcome to the November edition of our monthly OSINT digest. Over the past month, a number of stories have caught our eye, including the development of a new algorithm for reconstructing display content reflected in the glasses of a webcam subject, and a huge influx of brand impersonation scams that are surfacing as we approach the holiday season. We’re also introducing a whole new section, which will be a permanent fixture of the digest. So, without further ado, let’s jump into it.
Helped along by the Covid-19 pandemic, platforms such as YouTube are now awash with videos of talking heads shot from webcams. From gaming tutorials and presentations to interviews and discussion groups, such content is proliferating at a rate of knots. However, content creators may well be totally unaware that, to the canny analyst, these videos can yield more data about the on-screen subjects than they would care to broadcast.
It seems that people tend to overlook the capacity for betrayal held by reflective surfaces. Mirrors lurking in the background, or attire such as spectacles and watches can provide windows into the computer screen facing the presenter. With the help of image processing tools and techniques, OSINT analysts can view texts and images from the off-screen screen to derive all kinds of useful insights and inferences.
Even though OSINT specialists have been using manual reflected image inspection for a long time, it is still impossible to process large amounts of video material this way, due to human factors. However, according to a recent study, an algorithm has now been developed, which should be able to take care of most of the legwork and greatly accelerate the process through automation.

The academics behind the study were able to demonstrate that their model could achieve an accuracy rate of over 75% when reconstructing 10mm reflected text, shot from a 720p webcam. This is enough accuracy to read the larger fonts used on many websites. Furthermore, the researchers claim that 4K footage could yield legible texts for most web page headers.
This is intriguing technology for OSINT analysts, but could also be harnessed to protect users against optical attacks, in cases where video calls have been hacked into. Many video conferencing platforms already offer rudimentary blurring options, this new algorithm could be used to develop something far more fine-tuned – for example the ability to identify and blur discernable text in the lenses of the speaker’s glasses.
‘Tis the season to be ripped off. As online shopping picks up for the holidays, brand impersonation scammers are looking forward to cashing in with a bout of festive fraud. Here are some of the most popular deceptions to look out for.
In the first half of November, 17% of all email campaigns were considered brand impersonation scams. Deals touting Louis Vuitton items at $100 a pop, for instance, are turning up in countless inboxes, redirecting credulous consumers to dubious ecommerce sites, where you can buy fake goods or simply have your bank card details extracted.
Fraudsters know there’s nothing quite like a good old person-to-person chat to really drive the social engineering home. By calling people up and posing as sales reps, scammers can talk shoppers into visiting malicious sites on the promise of deals that seem way too good to be true. And invariably are.
Another scam in phishing format, this approach takes the guise of holiday giveaways offered by reputable brands as prizes awarded to ‘lucky’ survey respondents. Needless to say, everyone who completes the survey is a ‘winner’. Shipping costs then need to be covered, which seem like a small price to pay considering the value of the prize. Then it’s ‘bank details please’ and you know the rest.
These scams can be carried out on dizzying scales. For example, a malicious Chinese group ‘Fangxiao’ used a network of 42,000 web domains to impersonate over 400 popular brands for traffic generation. Some fraudsters even go so far as to impersonate financial regulators conducting a fraud investigation as a ploy to get their hands on people’s card details.
Those defrauded through brand impersonation are not the only victims here – the brands themselves can suffer significant reputational damage, often translating into huge financial losses.
Welcome to an entirely new section of the Social Links digest – monthly glossary entries. This is a space where, every month, we will define a term from the spheres of either OSINT and cybersecurity. These entries may be technical terms or they may be pieces of slang, but either way, they will be words or phrases that enjoy wide usage in the trade, and will allow non-specialists to chew the fat with tech-savvy folk.
So, to kick things off we’ve chosen a few related terms that touch upon the light and dark sides of the cybersecurity sphere. By this I really mean the good guys and bad guys, and those in-between, aka the ‘white hats’, ‘black hats’, and ‘gray hats’.
Hacking isn’t always an illegal activity. Skilled IT security professionals don’t earn their living by launching unauthorized invasions into private areas of cyberspace; instead they conduct penetration tests to reveal then fix vulnerable places in the corporate cybersecurity system. The general public usually calls this lot ‘penetration testers’, but go to any cybersecurity forum and you’ll frequently see an alternative appellation:
Since open-source intelligence doesn’t involve any kind of hacking, OSINT analysts are sometimes considered white hats. However, this is slightly erroneous since their work is not connected to cybersecurity systems penetration.
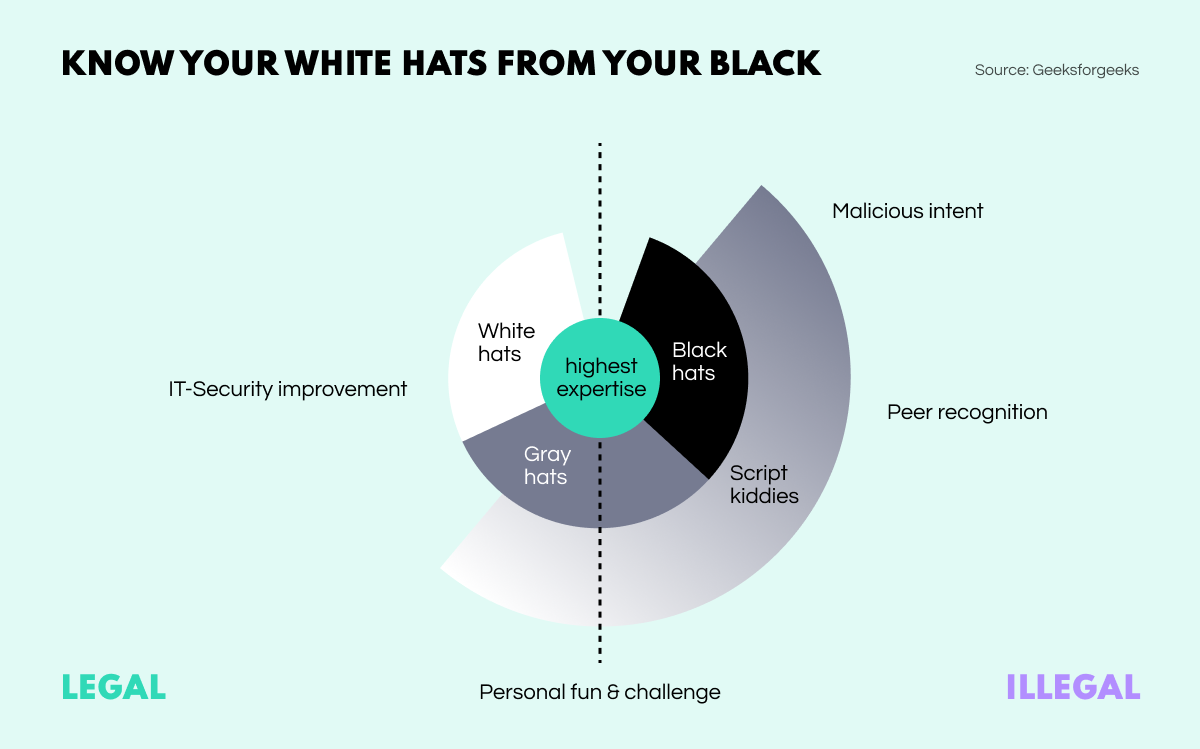
Black hats are more like the ‘genuine’ hackers from popular culture – shadow actors who hide their identity and pursue vulnerability exploitation, cyber extortion and leaked data trade. Many act as lone wolves but can also operate as members of cybercriminal gangs, or organizations with unofficial governmental aegis. Such groups are sometimes referred to as advanced persistent threat groups (APTs).
However, as with many things in our world, cybersecurity specialists cannot be strictly grouped into good and evil camps. Some specialists don’t set out to steal data or ruin corporate systems, yet take part in activities that can hardly be considered purely legal or ethical. These people fall into the category of ‘gray hats’, and they do what they do not so much to cause trouble per se, but to build up a reputation.
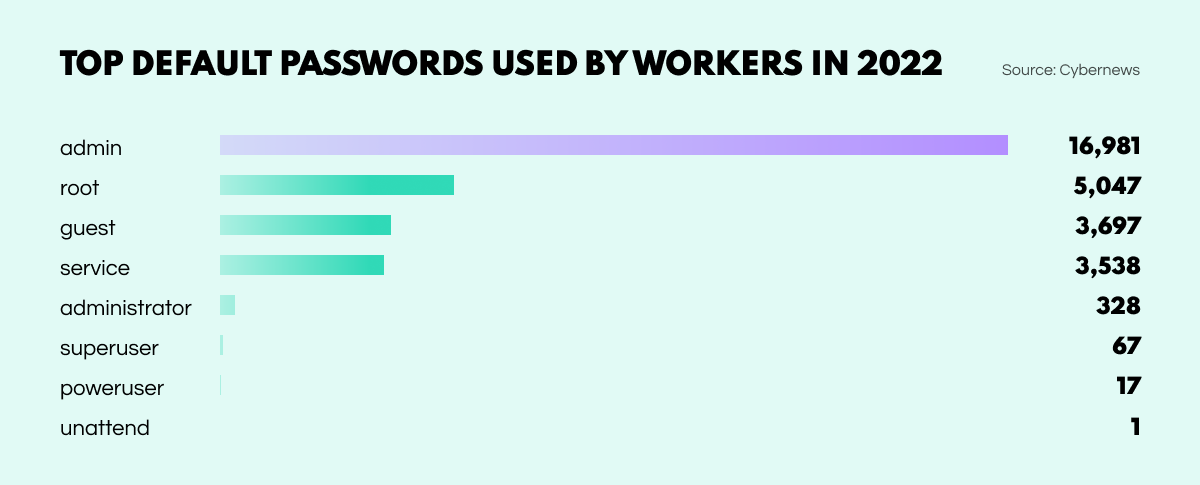
A crazy number of people are still ill-advisedly using passwords that can readily be guessed. Most of these typically consist of expletives, celebrities, cities, or keyboard sequences. Worse still, employees with access privileges seem to be as blasé as anyone else. According to recent research by Cybernews, the top 3 default passwords used by workers were ‘admin’, ‘root’, and ‘guest’.
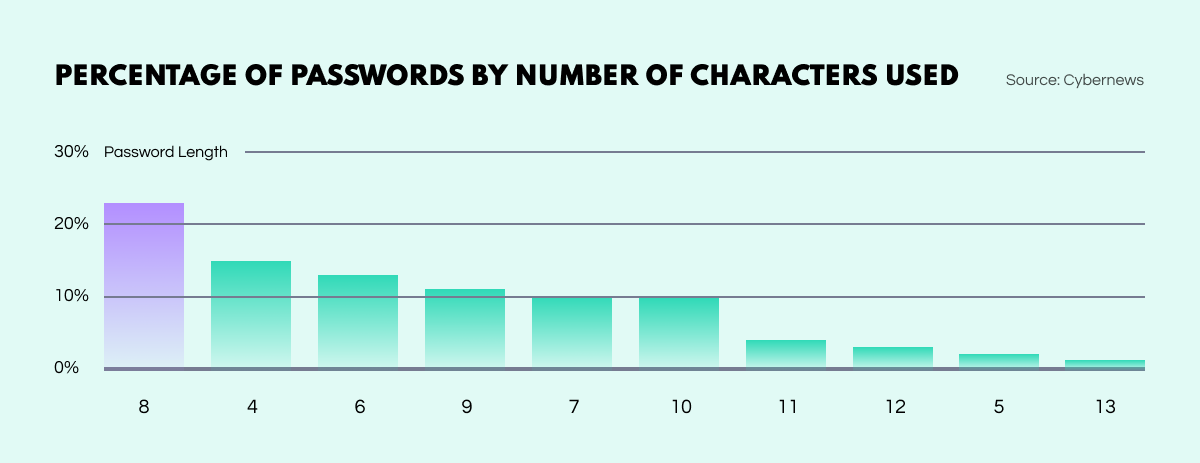
Furthermore, of all the passwords observed by the Cybernews team, just a staggering 1% met all of the criteria recommended by the cybersecurity industry. Only 4% contained 12 characters or more, including letters, numbers, and symbols. 14% used just 4 characters while 48% stretched to the range of 8 to 11.
In a recent statement, the FBI warned of a new type of cyber scam gaining popularity in the United States. The scammers pose as tech support representatives and claim that the annual subscription for their service – costing $300-$500 – is up for renewal in a few hours. The cancellation process involves installing a remote desktop protocol that hands over control of the computer. The scammers then lift funds from digital bank accounts.
The Japanese Ministry of Defense has officially confirmed the country’s member status in NATO’s Cooperative Defense Centre of Excellence. This follows Japan’s consecutive two-year participation in the alliance’s annual cyber war game Locked Shields, which is organized for research and training purposes.
Immersive Labs, a cybersecurity training platform has just closed a third round of investment, taking in $66M. This brings the total amount raised up to $189M.
The success of the startup is partly due to the COVID pandemic, which highlighted a worrying lack of cybersecurity skills among corporate employees.
And that’s all for the November digest! Keep an eye on our blog for all the latest news and insights into the ever-expanding world of OSINT.