OSINT: A Weapon against Insurance Fraud


The insurance sector is dogged by inflated identities and fraudulent claims that result in severe financial losses every year. At a time when getting a true picture of a potential client has never been more pressing, OSINT has come to the fore as an accessible but powerful tool in truly verifying that someone is who or what they say they are.
So today, we’re going to briefly discuss the extent of the issue and the part that OSINT has to play, before looking at an authentic case study from one of our clients, showing how SL Crimewall was used to great effect in gaining an accurate profile of an applicant for a large life insurance policy. Let’s take a look.
Fraud and identity theft in the insurance sector have become a truly colossal problem. According to Forbes, in the US alone, insurance fraud losses run in at around $308B every year, with fraudulent claims pouring in for healthcare, property, and auto insurance to name but a few.
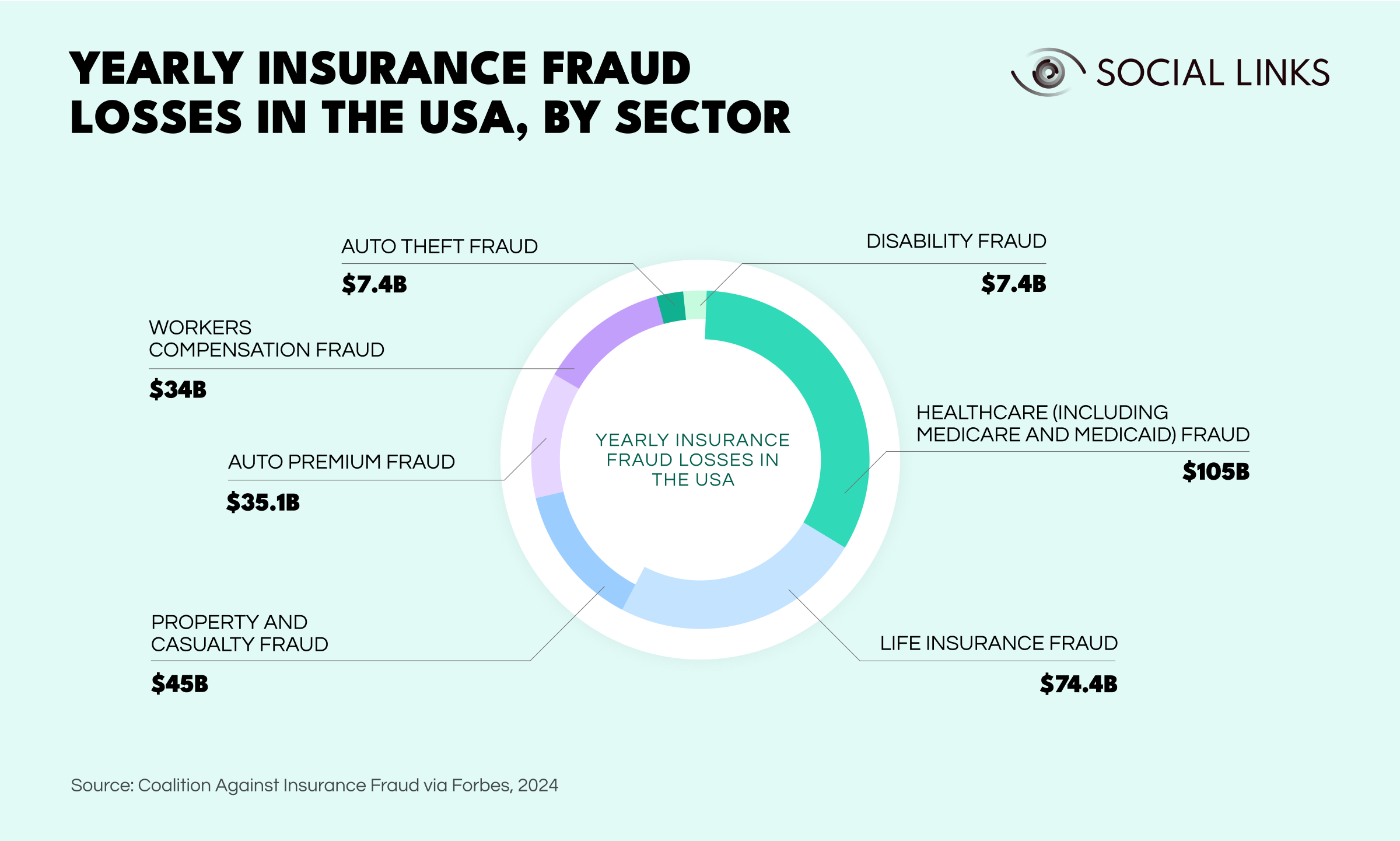
In such a climate, insurance companies have become extremely wary of who they dish premiums out to, resulting in background checks far more thorough-going and data-driven than those of the past. And the ingredient that’s driving this new, in-depth breed of background check? OSINT.
While public registries and government databases still play a part, modern background checks may involve cross-checking a subject’s employment history, financial records, and personal details with all manner of publicly available data sources, such as social media, news reports, public registries, the Dark Web, and more.
This is where OSINT solutions are becoming a go-to tool for a great many insurance company client checks. With their wide-reaching data access, advanced gathering methods, and intuitive link analysis tools, OSINT solutions are raising the bar for data verification, allowing companies to ensure compliance with regulations, manage risk effectively, and safeguard themselves against fraudulent claims.
In January 2024, the private insurance firm ZenziSure Insurance began onboarding a new client, Kwame Adebayo, for a high-value life insurance policy. Adebayo, a well-off man in his early 40s, applied for a $5M policy, listing his job as a financial consultant at a private firm called Banbu Financial Group.
While the application seemed routine, the value of the policy that was planned to be taken out prompted ZenziSure to initiate thorough KYC (Know Your Customer) and background checks, as part of their standard procedure to manage risk and ensure regulatory compliance.
The point of departure for the background check was the basic enrichment of Adebayo’s digital identifiers. A ZenziSure employee in contact with the customer, had Adebayo’s phone number to hand. Using this as input data, the company was able to gather information about the subject, from an input they could be sure belonged to him.
Having run a selection of search methods on the number, the most fruitful source appeared to be from data breaches (SL ISE), where the number appeared in two records, disclosing an email address and Facebook ID.
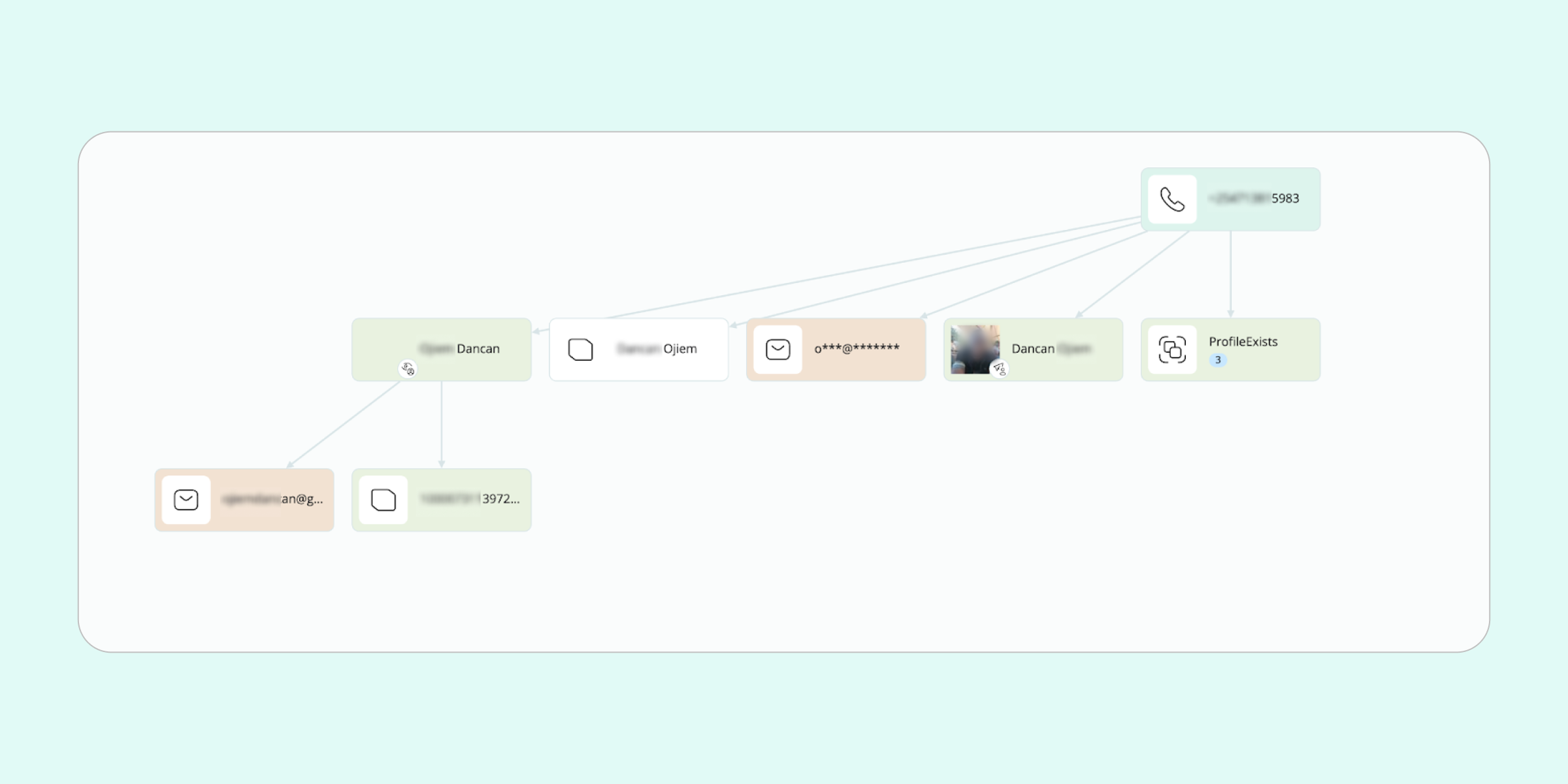
Armed with the extracted email address, the investigator was able to zero in on an LinkedIn profile unquestionably belonging to the subject. By extracting the details from this bona fide profile, it became clear that Adebayo did not, in fact, work as a consultant at the Banbu Financial Group, but actually served as Chief Clerical Officer in the government administration.
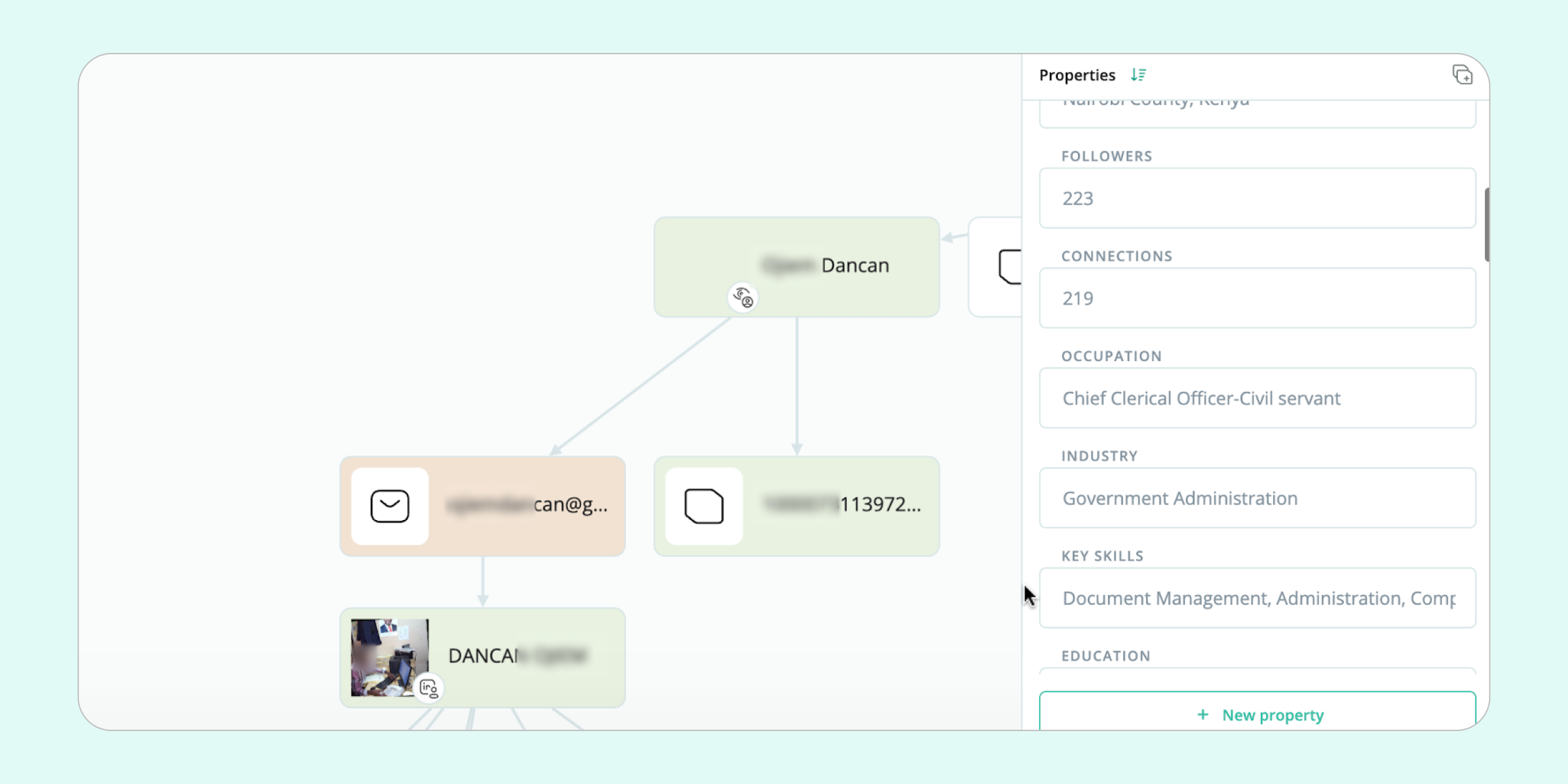
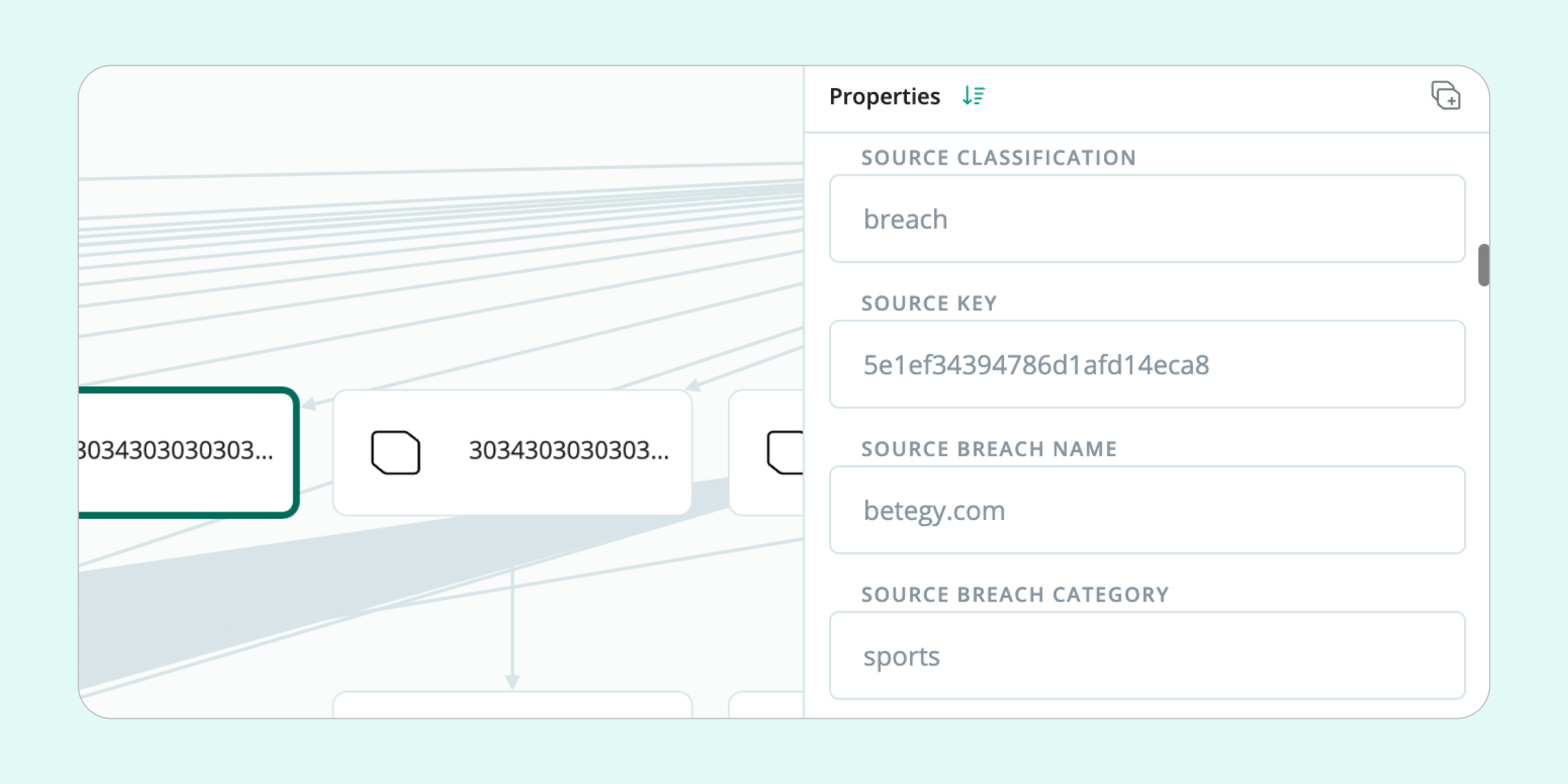
Further in-depth analysis of Adebayo’s social media pages further supported the hypothesis of a low income and a relatively average standard of living. What’s more, by reviewing breached data, the investigator unearthed further red flags regarding the subject’s financial reliability—the email was registered with online casinos and sports betting shops.
In the region in question, public sector salaries are typically lower than those in the private sector. Realizing that declaring his true occupation could raise red flags resulting in a rejection or highly limited policy, Adebayo hoped that presenting himself as a high-earning consultant could bag him a policy beyond his actual means—a favorable outcome for him, but not for the insurance company.
Ultimately, by comparing Adebayo’s profile as elaborated through SL Crimewall and OSINT techniques with the one he presented himself, major discrepancies became evident. The client’s claims of a high income and financial stability were contradicted, leading the insurance company to reject the application and avoid a potentially very costly policy issuance.
The above case illustrates one approach using SL Crimewall and the results that were delivered. However, there are multiple possible approaches which may yield optimal results depending on the case. So here’s some more general recommendations.
A crucial initial step for elaborating an expansive digital footprint. Find social media accounts unquestionably connected to the subject by enriching verified input data. If someone is trying to mask aspects of their social media, duplicate accounts may exist, so beginning a check from data of known ownership is a good approach. Remember that data breaches from darknet sources may unearth leads that Surface Web sources can’t.
Social Media sources are often major contributors to an accurate subject profile. Research relevant social media profiles and activity to check the veracity of the subject’s claims. Does the lifestyle that emerges tally with the asserted income level and job position? Is there anything important that the client conveniently failed to mention? LinkedIn is a valuable source for verifying work-related claims.
Understanding a subject’s social network can be vital for checking claims. Through social media sources, look into the closest connections and family ties of the subject family connections. Again, do they support information provided by the subject or are there discrepancies? Does the subject have connections in common with the organization they purportedly work for?
Corporate sources and registries are not to be overlooked. Go through corporate registries as well as the social media of the company in question. Do any of these sources substantiate the claim that a given individual works there? Does the company seem as credible and stable as is claimed?
Data breaches can be an incredible resource for unearthing relevant profiles or connections. While connections and accounts might be invisible through traditional searches in the Surface Web, they may have been part of a leak, giving investigators the opportunity to elaborate a far more expansive digital footprint, and one that can often lead to telling revelations.
With fraud losses spiralling, the insurance companies of today are obliged to carry out thorough-going and reliable background checks to policy applicants across the board. While outsourcing KYC and due diligence work may be a painful expense, OSINT solutions can deliver superb results at a relatively low cost, while allowing firms to keep all such processes in-house.
On top of these considerations comes the issue of data quality. By harnessing the power of open data in combination with traditional background check sources, OSINT solutions allow insurance firms to leave no stones unturned in getting to the bottom of someone’s true credentials and determining their actual level of reliability.
With such tools at hand, firms can rest assured they are doing all they can to avoid losses through fraud, remain compliant with regulations, and protect their reputation. Insurance for insurers indeed!