OSINT in Arms Trafficking: Mapping Illicit Networks

Arms trafficking networks no longer operate only in hidden warehouses or remote border crossings. Increasingly, they rely on public digital infrastructure. While enforcement concentrates on ports and customs checkpoints, traffickers coordinate on social media, advertise through online marketplaces, register shell companies in public databases, and move shipments along traceable maritime routes. The illicit arms trade has expanded into the open internet. Detection strategies must adapt accordingly.
This article explores how open-source intelligence strengthens anti arms trafficking efforts. We examine how digital signals expose illicit supply chains, how analytical methods turn fragmented data into investigative leads, and how law enforcement agencies use publicly available information to support cross-border disruption.
Arms trafficking refers to the illegal trade, transfer, or diversion of weapons in violation of national laws or international regulations. Unlike licensed defense exports, trafficking relies on concealment—circumventing customs controls, falsifying documentation, and exploiting weak oversight.
Modern trafficking typically combines three overlapping channels:
Physical diversion. Weapons legally manufactured or sold are redirected through false paperwork, corruption, or weak stockpile management.
Cross-border smuggling. Illicit transport occurs across land, maritime, or air routes.
Digital facilitation. Online platforms enable coordination, brokerage, and communication that support physical movement.
Today’s system is hybrid. Digital tools handle coordination and deal-making, while physical networks handle transport. That overlap creates patterns—patterns that can be analyzed.
Firearms complicate the problem further. They retain value and functionality for decades. A single diversion event can ripple across regions and conflict zones long after the original transaction.
Traditional enforcement focuses on seizures—intercepting cargo or arresting individuals after a transfer. Necessary, but incomplete.
Stopping one shipment does not dismantle the network behind it.
Intelligence-led approaches shift focus from individual transactions to infrastructure. They support:
Because these networks operate across jurisdictions and digital platforms, visibility must extend beyond physical borders. Publicly available data provides that broader perspective.
Trafficking is rarely a single exchange between a seller and a buyer. It is a layered system designed to fragment responsibility and obscure origin. Each layer adds distance—legal, logistical, or digital—between the original source of the weapons and the final recipient.
Below is a simplified structural model:
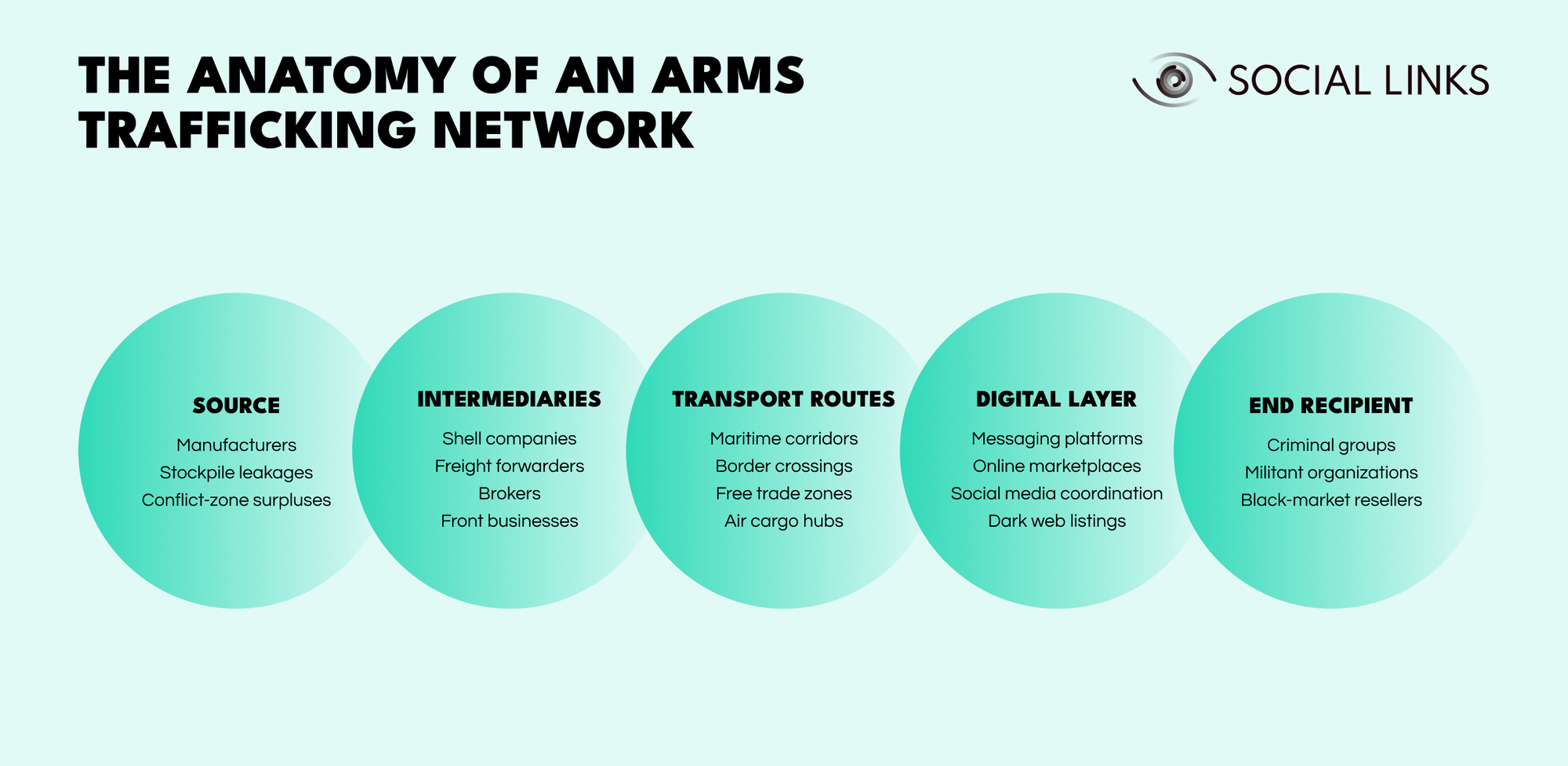
The model outlines five connected layers. Understanding how they interact is critical for mapping illicit networks.
Weapons originate from legitimate manufacturers, poorly secured stockpiles, or conflict-zone surpluses. In many cases, diversion does not begin as an overtly illegal act. A shipment may move through legal procurement channels before documentation is falsified or inventory controls fail. The earlier the diversion point, the harder downstream attribution becomes.
This is the insulation layer. Shell companies, brokers, freight forwarders, and front businesses create contractual and financial distance between supplier and buyer. Ownership structures may be deliberately opaque, with shared directors, nominee shareholders, or short-lived corporate entities. On paper, transactions resemble lawful trade activity. In practice, this layer enables deniability.
Logistics provides the physical backbone of the network. Maritime corridors, border crossings, free trade zones, and air cargo hubs are used to move goods across jurisdictions. Traffickers often rely on indirect routing, repeated transshipments, or transit through weak enforcement environments. These patterns are rarely random—they reflect deliberate route selection designed to reduce scrutiny.
Coordination increasingly happens in open and semi-open digital environments. Messaging platforms facilitate negotiation. Online marketplaces connect buyers and brokers. Social media supports recruitment, signaling, and coded listings. Dark web forums provide additional anonymity. This layer does not move weapons physically, but it enables everything else—matching supply to demand and coordinating logistics.
Weapons ultimately reach criminal groups, militant organizations, or black-market resellers. By this stage, tracing origin requires reconstructing the chain backward through multiple jurisdictions and corporate veils.
Investigations rarely uncover the entire chain at once. They usually begin with a single anomaly: an unusual shipping route, a suspicious company registration, or a marketplace listing. That initial signal typically exists in one layer only.
Effective intelligence work connects that signal horizontally across the others.
For example:
Publicly available data is especially powerful in the intermediary and digital layers, where corporate registries, shipping databases, and online activity leave observable traces. These layers often provide the connective tissue that links physical movement to identifiable actors.
The network only becomes visible when the layers are analyzed together.
Open-source intelligence focuses on publicly accessible signals. It does not replace operational methods, it helps prioritize them.
Key contributions include:
On their own, these signals may seem minor. Viewed together, they reveal structure.
The value lies in correlation.
The digital layer often produces observable patterns, even when intent is concealed.
Individually, none prove wrongdoing. Collectively, they suggest coordination.
Public data becomes meaningful only when structured methods are applied.
Network analysis maps relationships between brokers, logistics providers, and corporate entities.
Link analysis visualizes shared infrastructure—emails, domains, shipment routes, ownership structures.
Pattern recognition identifies recurring operational behavior.
Entity correlation connects identities across filings, platforms, and registries.
These methods turn scattered signals into actionable insight.
Law enforcement agencies use this visibility in two ways.
Because public-source findings can often be shared more widely than classified material, they provide a common analytical foundation across jurisdictions.
Naturally, this approach is not without limits. Key challenges include:
Correlation does not equal causation. Documentation and validation remain critical. Public data alone cannot dismantle networks. Effective disruption requires integration with customs inspections, financial tracing, human intelligence, and coordinated law enforcement action.
OSINT analysis cannot:
Its strength lies in early detection and structural mapping.
Arms trafficking thrives where investigations are fragmented and data remains siloed. Digital coordination has not made networks invisible—it has redistributed their traces.
When corporate records, shipping routes, and online coordination intersect, structure emerges. The advantage is not access to data. It is the discipline to connect it before weapons move.
It involves collecting publicly available data—marketplace listings, corporate filings, social media activity, shipping records—and applying structured analysis to identify suspicious patterns and connections. These findings help direct deeper investigative efforts.
It provides early visibility into routes, intermediaries, and digital coordination, complementing traditional enforcement and enabling cross-border collaboration.
No. It generates insight and prioritization, but disruption requires integration with operational law enforcement and international cooperation.
Examples include coded listings, repeated seller migration, shared corporate directors, unusual shipping routes, and cross-platform identity reuse.
They use it to verify identities, trace infrastructure, reconstruct timelines, and support evidence-backed investigations.