OSINT in Sexual Abuse Investigations: From Data to Justice


The Internet has revolutionized accessibility in many ways, ranging from shopping and education to banking and more. Yet, this digital realm has also given birth to secondary online personas, where individuals can transform into entirely different characters. While many people harness these digital identities for creation and connection with others, some exploit them for murky purposes.
In this article, together with the Social Links Center of Excellence, we dive into the sensitive topic of sexual abuse and discuss how using open-source intelligence can help investigate such cases. Starting from a current situation, we move to proven OSINT techniques that help collect situation anamnesis quickly and deanonymize perpetrators.
So, let's get started.
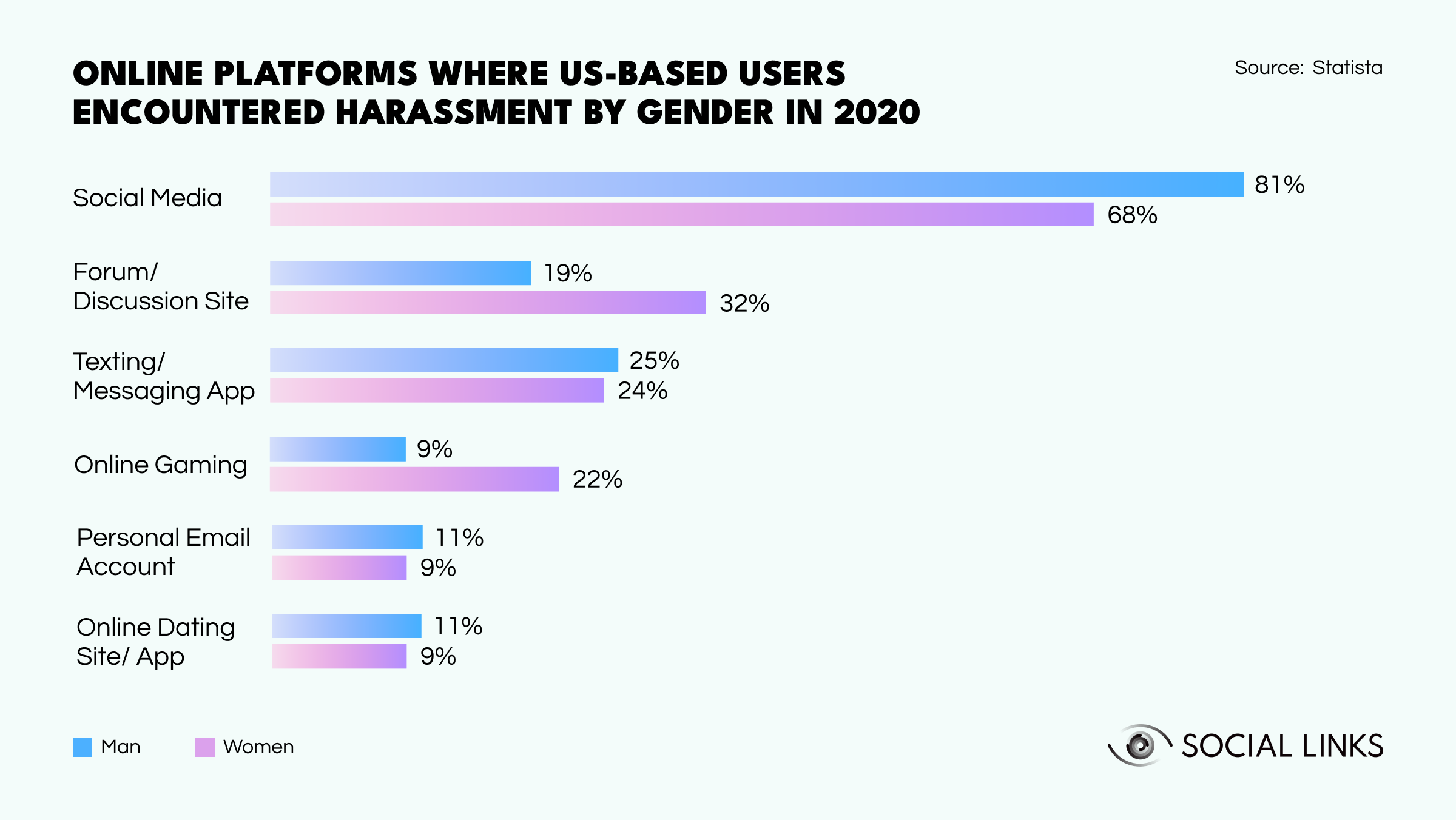
Following the COVID-19 pandemic, cybercrime saw a massive surge, and unfortunately, sexual abuse remains a significant concern with some disheartening statistics. According to Statista, a staggering 81% of women in the United States encountered harassment on social media. Interestingly, 68% of men have reported similar experiences.
Sadly, abusive situations continue to affect people of all ages. NSPCC reports that in the UK alone, in the period from 2018 to 2022, there has been an alarming 80% increase in online child grooming crimes. In the meantime, IWF detected a 1000% uptick in online sexual abuse cases involving primary school children since 2019. This surge has also seen a rise in what's known as 'Category A' materials, which include explicit content involving children as young as 7 to 10 years old.
Another example demonstrates that nearly one in six US young adults experienced at least one type of online sexual abuse. Unfortunately, such figures highlight that technological developments not only brought a breakthrough in communications but also allowed darker impulses to explode. With more people becoming victims of online sexual abuse, it's clear that the current safety measures are not enough. It’s vital to acknowledge the gravity of this issue and take necessary actions to address it effectively.
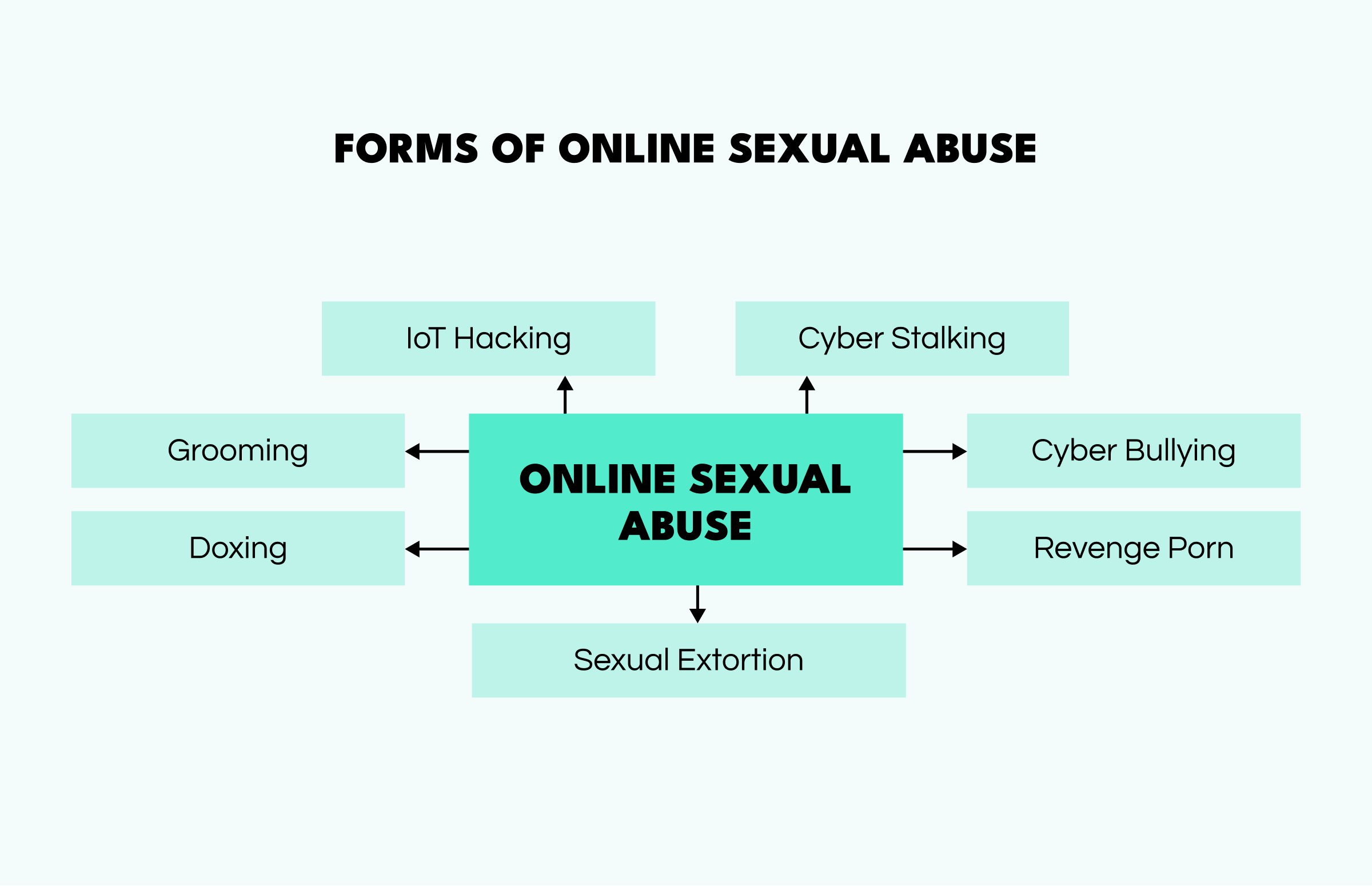
Abusive behavior can manifest in many forms, making it tricky to notice red flags in time. As most methods involve a lot of manipulation, perpetrators disguise abusive behavior as casual conversation. So, with this in mind, let's look at some ways that offenders engage in sexual abuse online.
Luckily, there’s a solution. Open-source intelligence provides a lot of techniques that come in handy when investigating predatory and problematic online behavior. While preventing abuse is the preferred goal, sadly, that’s not always possible. In such cases, authorities can turn to OSINT to increase investigation effectiveness.
So, let’s get to the practice part. For illustrative purposes, we're introducing a character, Brandon Smith, an OSINT investigator at a law enforcement agency (LEA). He's monitoring the Dark Web to track and combat criminal activities. In a routine check, he stumbles upon a new darknet marketplace that became a hub for illicit content, including revenge porn and child sexual abuse material (CSAM). Concerned by the gravity of the situation, he decides to take action and gathers evidence using various OSINT techniques. And here they are.
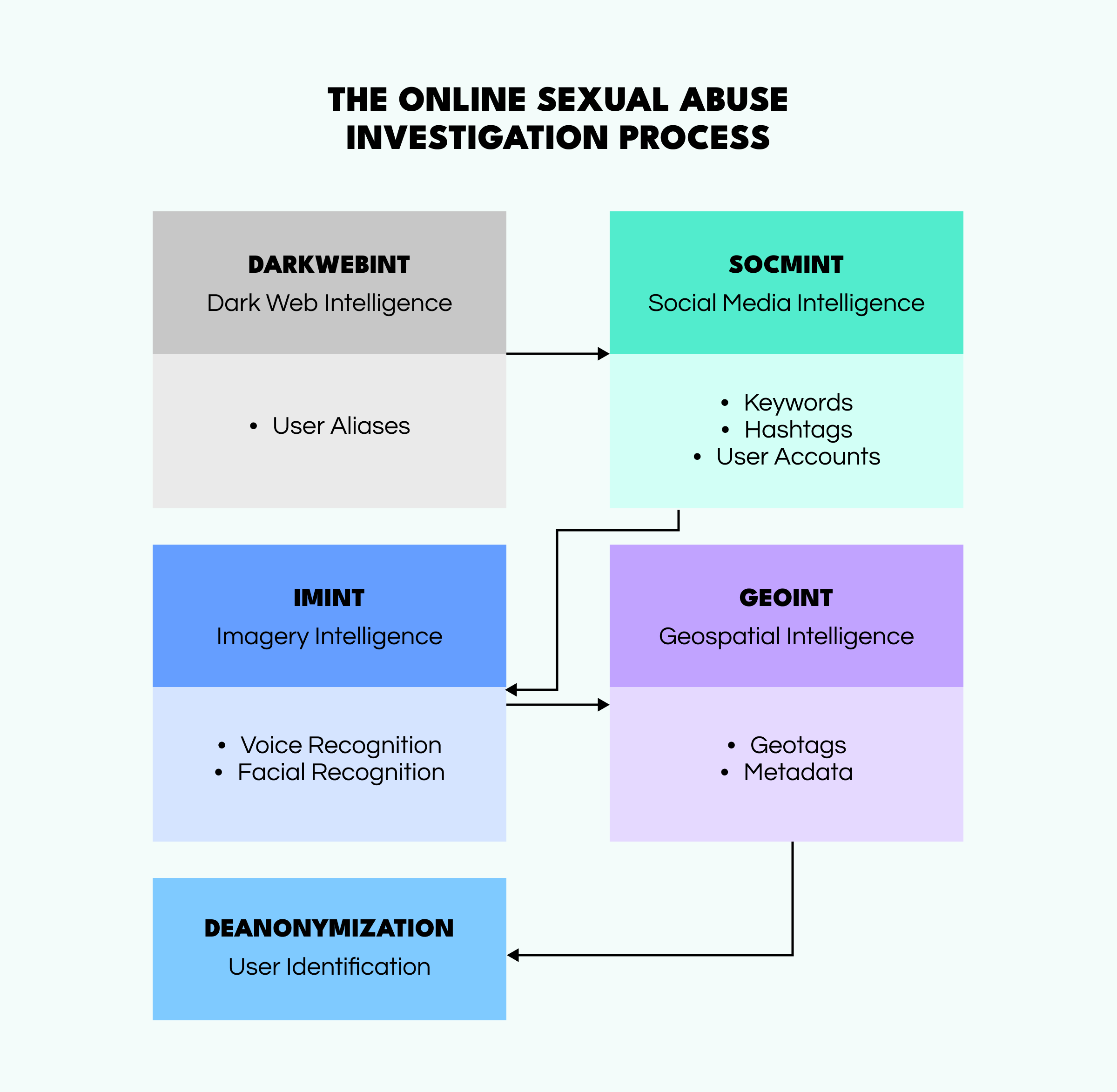
Brandon's investigation starts with the Dark Web monitoring. To do this, he uses SL Professional and its Darknet Pack, created in collaboration with DarkOwl. First, the investigator begins scanning darknet marketplaces and forums, searching for any traces of illegal content and services associated with the criminals behind this platform. He manages to find a considerable amount of sexual abuse content (videos and photos) that the offenders are trying to sell.
As Social Links' extension provides a vast amount of darknet content, Brandon accesses a bulk of aliases relating to potential threat actors that he can analyze further.
Brandon decides to dig deeper using data he gathered from the darknet marketplace. He scrutinizes social media platforms such as Twitter for any matches with darknet aliases. After identifying several accounts, he starts looking into the keywords, hashtags, and geotags related to the users. This technique helps Brandon uncover discussions that may contain trigger words or acronyms.
Brandon then starts looking into the users' content on social media for any identifiers (tattoos, scars, faces, voices, etc.) that appeared in the sexual abuse materials he found previously. Matching such characteristics can help reveal the threat actors' identities.
When the needed data is found, it becomes obvious—manual analysis will take ages. Luckily, Brandon knows a way around this obstacle. He employs ML-powered methods, such as facial and voice recognition, to identify users. Moreover, some techniques extract geodata from pictures or videos based on background details and metadata.
With multimedia analysis yielding essential information, Brandon focuses on tracking locations. By scrutinizing content shared on social media, he gathers insights into the criminals' lifestyles and habits. The investigator knows that even when specific geolocation data is unavailable, users often tag or mention locations or share photos and videos that provide clues about their whereabouts.
To finalize his investigation, Brandon brings together all the puzzle pieces he found during the process. For such purposes, OSINT tools are time savers and helping hands, allowing analysts to summarize all the evidence properly and not miss any details.
Following the detailed inquiry, Brandon finally has a list of real names, emails, and IP addresses from metadata of the sexual abuse materials found at the beginning of the investigation. He forwards all of his findings to his colleagues from LEA, who will take the case into the real world and build a legal claim against the malicious actors.
Sexual abuse is a very sensitive topic that requires in-time (or even preventive) actions. Modern OSINT solutions help in it. Want to learn how? Simply follow the button below, and we will arrange a personalized demo for you. During the call, we’ll discuss your case, answer burning questions, and show you how open-source intelligence can speed up investigations.