OSINT, Threat Models, and Executive Protection


In a world of ceaseless—and at times ruthless—competition, individuals who wield influence in either political or commercial spheres are continually finding themselves in the firing line. When online smear campaigns, internal intrigues, or even plots of elimination are not mere abstractions, being a figure of eminence can be a dangerous occupation.
At first glance, it may seem that OSINT is not a discipline that has a huge bearing on personal security work. But in fact, it does. So in this article, we’ll look at the important role of OSINT in executive protection, reflecting on the areas in which these disciplines overlap, and how they can help security teams safeguard their charges effectively.
Like any kind of systematic security deployment, executive protection manifests as a process—and one which can be logically broken down into constituent parts. Among these, the core component most suited to the application of OSINT tools and techniques is that of threat model construction.
While threat models are widely associated with cybersecurity or infosecurity spheres, they’re also created—in one form or another—for national security, public safety, corporate risk management, logistics security, and high-net-worth individual security, all of which may involve varying combinations of tactical and operational methods reaching well beyond the framework of cybersecurity.
A threat model may be a dynamic tactical element incorporated into a given security strategy, which should, in turn, represent an element of the overall strategy of an organization.
So what makes a tactical element ‘dynamic’? This really means that it should be adaptive and adjustable to emerging variables in the environment. Furthermore, any adjustments made should be based on the experience gained through each specific iteration within the overall security process, as well as more wide-scale factors, such as technological innovation, which will most definitely affect the tactics, techniques, and procedures (TTPs) of potential threat actors.
By definition, the process of building a threat model means running an audit on all target systems, including human ones—for instance, the personal infrastructure surrounding a High Net Worth Individual. Such an audit may necessitate approaches that fall under the definition of OSINT. These may include: assessing online exposure and threats, identifying relevant leaks and malware on devices, and modelling attacks.
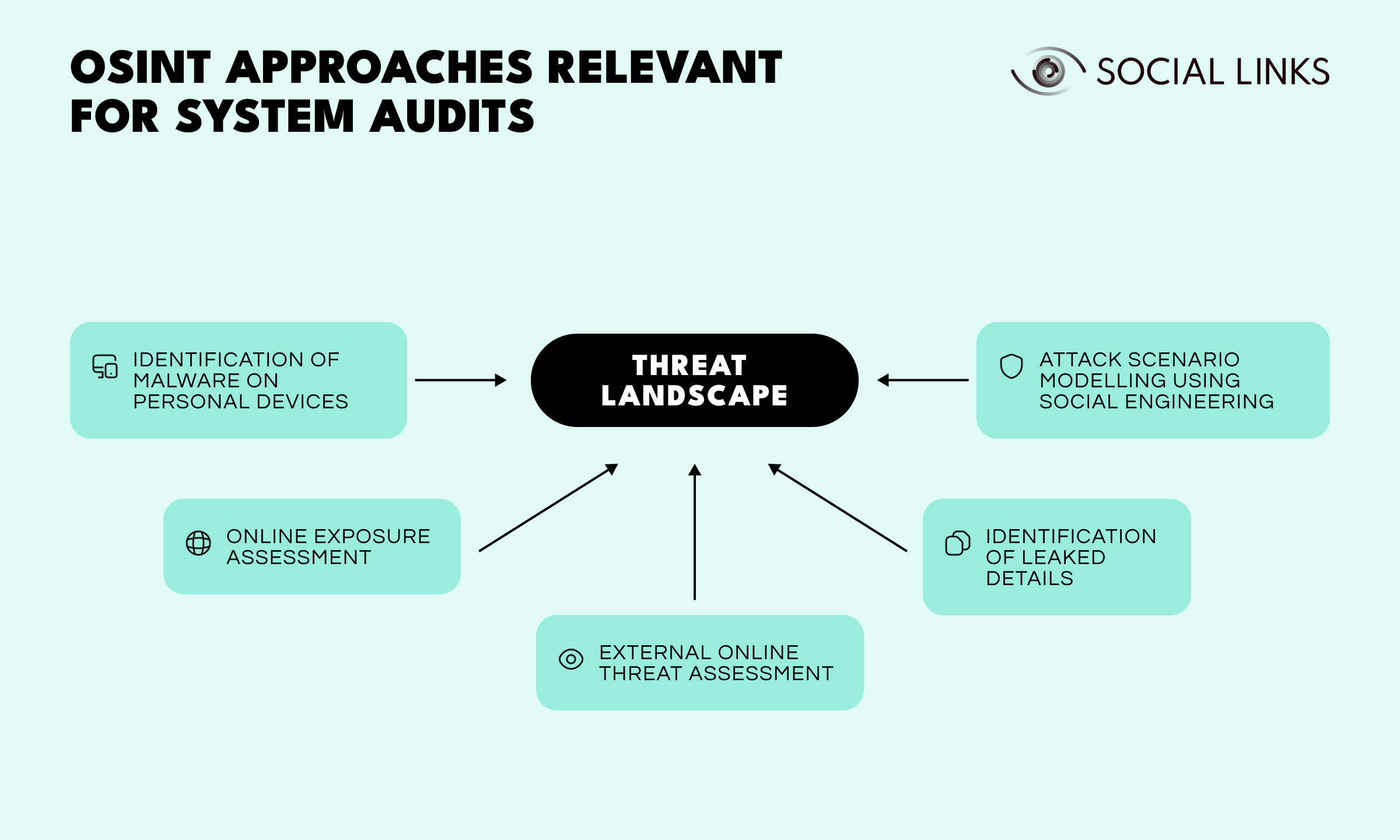
Within the context of the threat assessment cycle, OSINT deployment can be considered in response to three formative questions:
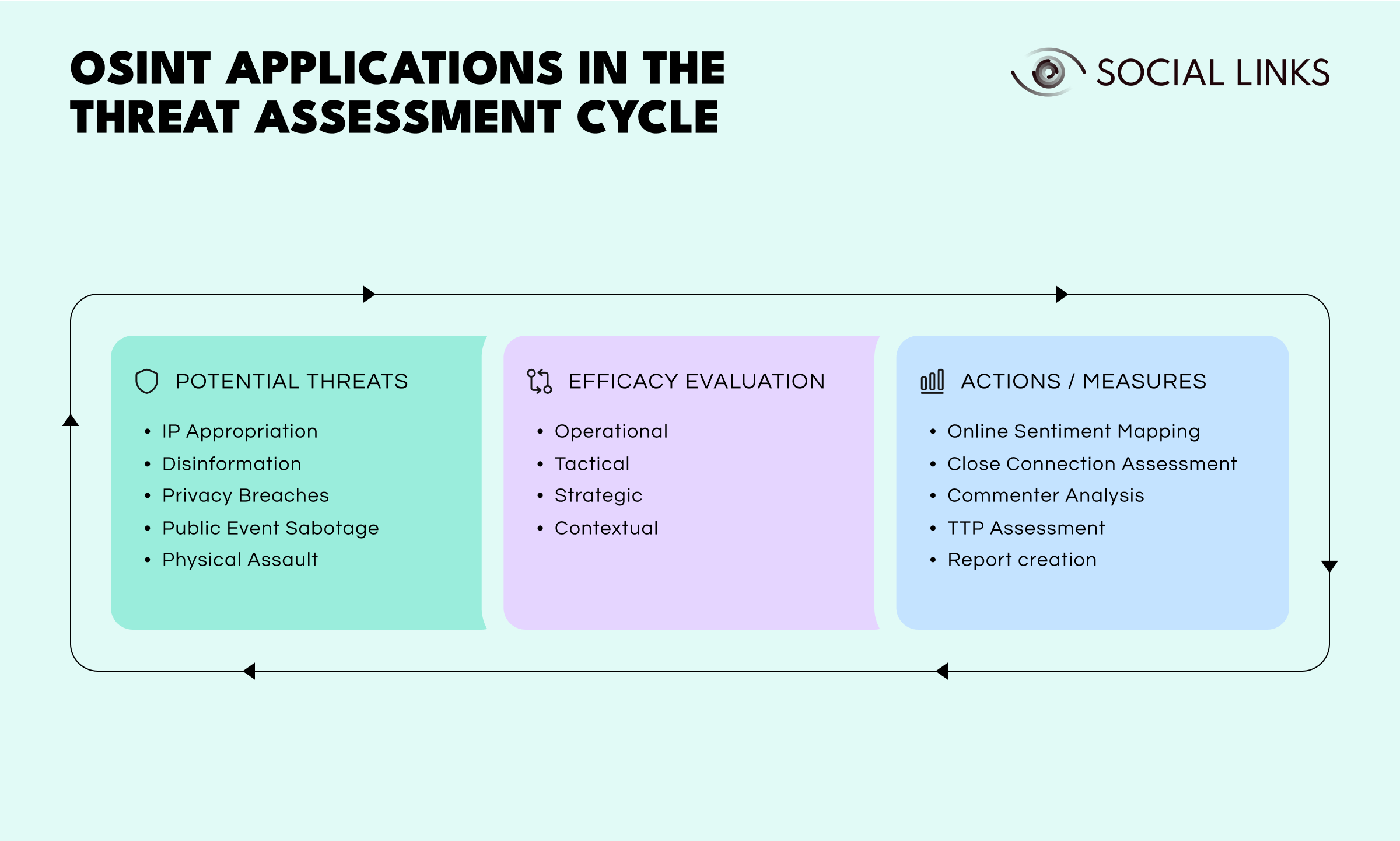
OSINT can be relevant for the assessment of a range of HNWI security threats including:
Intellectual Property Appropriation. Patent, trademark, or copyright infringement such as the unauthorized use of a brand or design, the copying and reuse of content, etc.
Targeted Disinformation. False claims, slander, smear campaigns, unfair commentary, and other forms of informational attack.
Privacy Breaches. Personal details or device compromise through leaks, unauthorized photo or video content, personal intrusions in public or private places.
Public Event Sabotage. Organized attempts to disrupt or undermine a public event, resulting in financial loss.
Physical Assault. Deliberate attempts to cause bodily harm or assassinate a given individual.
Various OSINT practices and techniques can be deployed to counteract the dangers outlined above. These include:
Online Sentiment Mapping. Determining and assessing all online sentiment indicators and statements from the last one to three years. These should cover both the major social media platforms, as well as mainstream or industry-focused media.
Close Connection Assessment. Looking into verifiable familial and business ties, elaborating graphs with two nodes outwards at minimum.
Commenter Analysis. Profile all users participating in or facilitating active discussion around the client, with a focus on those that can be plausibly categorized as holding extreme or obsessive tendencies.
TTP Assessment. Assessing the tactics, techniques, and procedures of potential threat actors.
Report Creation. Exporting a structured analytical report documenting all findings to ultimately inform possible security recommendations and provide clear focuses for discussions with the client.
At each iteration of the threat assessment, the extent to which the employed countermeasures were effective need to be evaluated. Such assessment should be approached from a number of standpoints including operational, tactical, and strategic ones, as well as a contextual analysis that factors in the nature of the case in question and the specific goals of every iteration influenced by the adopted threat model.
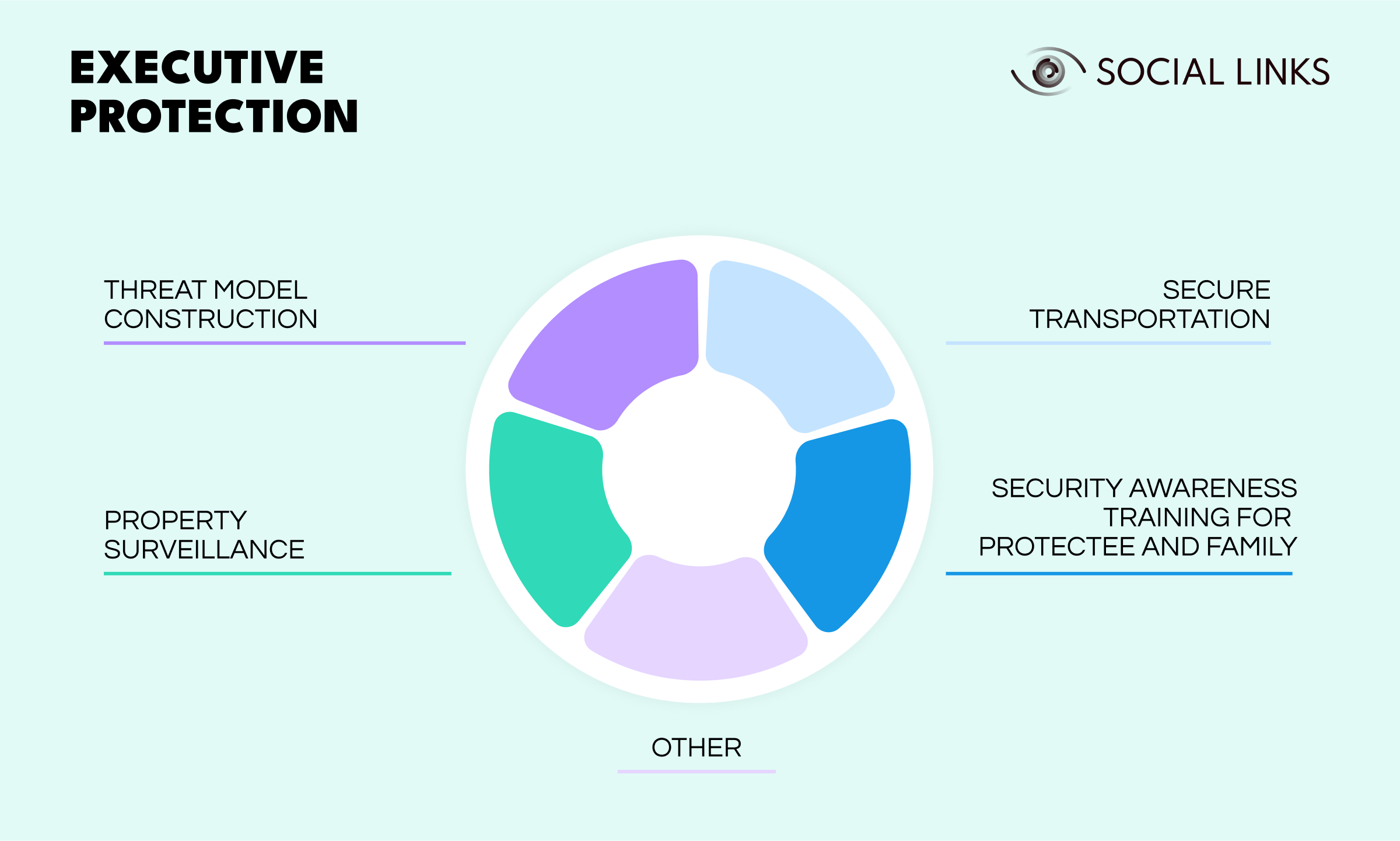
Any team or specialist charged with creating threat models with a view to protecting a HNWI needs to not only be aware of, but actively employ, OSINT approaches if they want to ensure their threat assessments are truly thoroughgoing and watertight. This could apply to all manner of security apparatus, including:
If you’d like to learn more about how OSINT tools and techniques can bring a game-changing level of strength and effectiveness to threat models, get in touch! Just follow the link below and we’ll set up a personalized session, where we’ll demonstrate how our products can revolutionize your threat modeling.