OSINT Tips: 5 Ways to Deanonymize Users on Telegram


In an era marked by rapid technological advancements and many digital platforms, efficient investigative methods have become more crucial than ever. Within this dynamic landscape, Telegram emerges as a vital source of information due to its status as a privacy-focused messaging app with strong encryption. The platform attracts a diverse user base, including law-abiding citizens and, regrettably, individuals with criminal intent, such as extremist threat actors.
In our article, created in collaboration with the Social Links Center of Excellence and Product Team, we offer practical examples of using OSINT for Telegram investigations. The messenger provides plenty of insights to enhance ongoing research, and our aim is to equip professionals with the tools and knowledge to navigate this platform effectively and leverage the data to advance their current workflows.
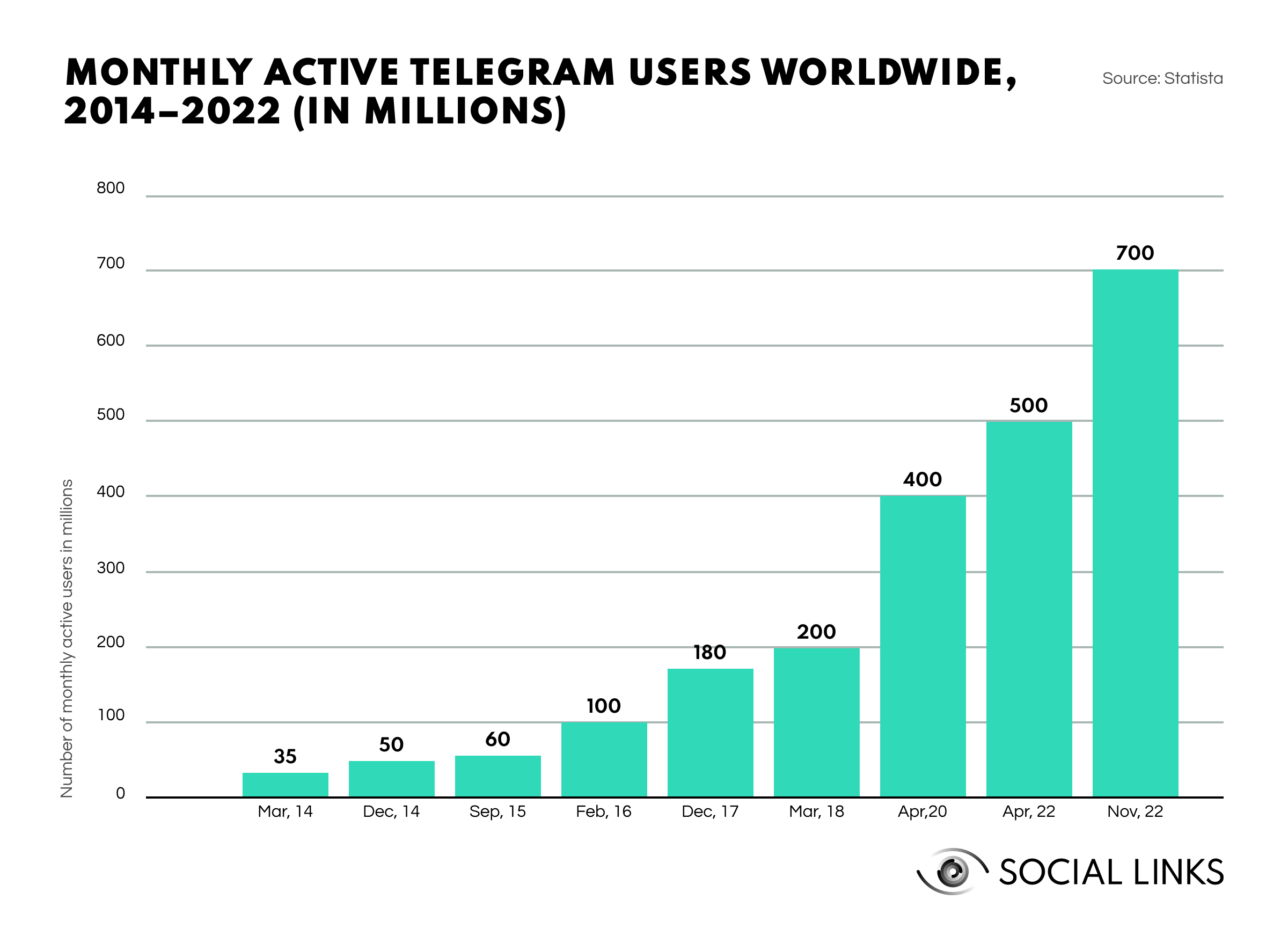
In today's evolving communication landscape, Telegram has experienced a significant surge in popularity, amassing 700M active users in 2022. This rapid growth stems from the genuine concerns of the general population. One compelling factor is Telegram's anonymity and freedom of speech policies. With the escalating frequency of data breaches, there's an increasing demand for more robust security measures, which Telegram appears to meet. However, this heightened privacy also benefits criminals.
Telegram's relaxed moderation policies make it an appealing choice for numerous extremist groups. The platform's hands-off approach to political motivations and content delivery has made it increasingly popular among fringe ideological groups. Telegram allows the formation of groups as channels, simplifying the sharing of extremist literature, manifestos, violent videos, and instructions for 3D printing weapons.
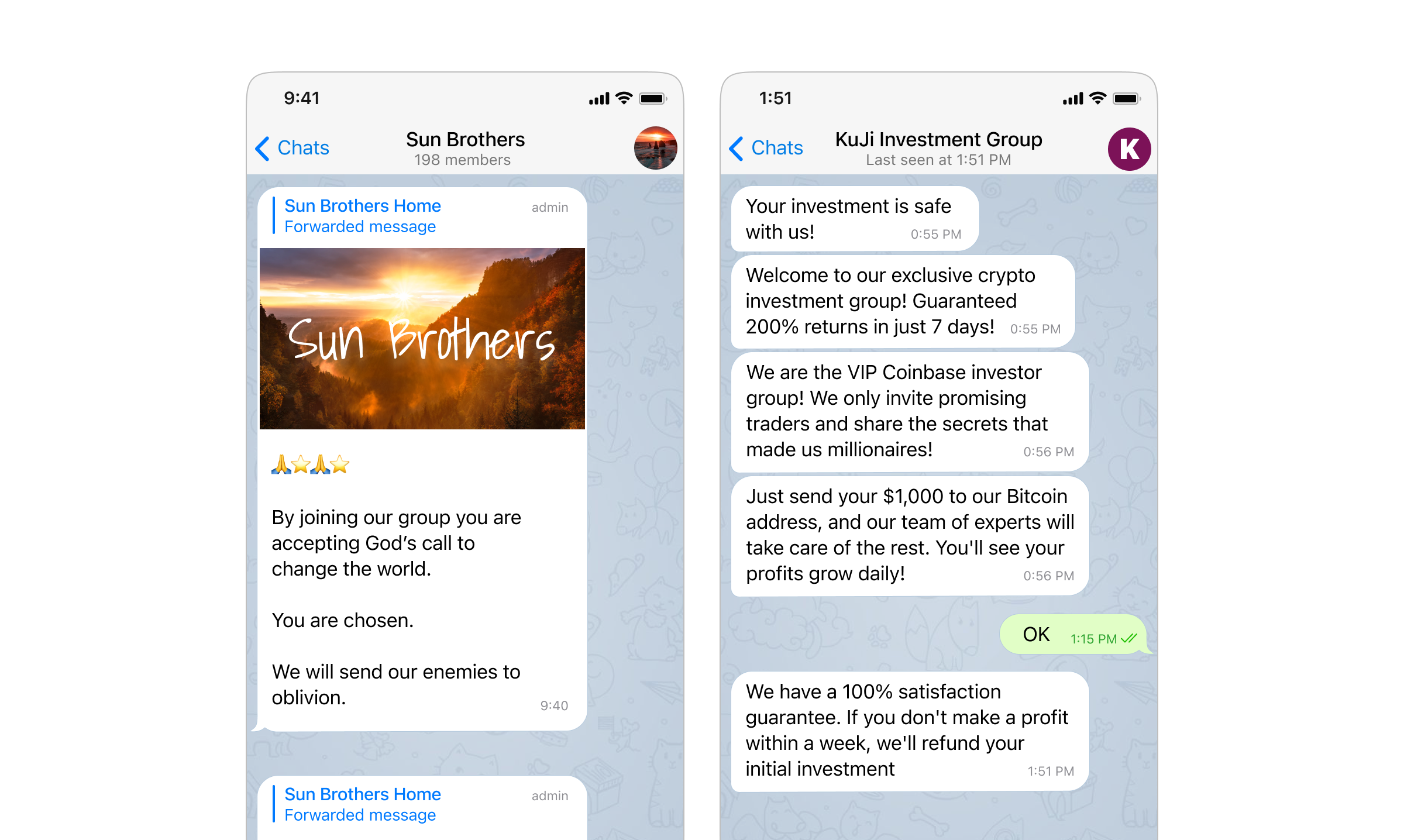
Beyond extremist content, scams are thriving on Telegram as well. Threat actors create fake listings for items like phones, laptops, or cameras, prompting users to contact them via the app to discuss the deals. When users engage with fraudsters, they unknowingly interact with automated bots designed to steal sensitive information, resulting in losses of $6.5M in recent years. Such scams operate like a regular phishing scheme, with the bot requesting personal data, such as addresses or credit card details, to “finalize the deal.”
Good news: despite Telegram's user anonymity, the mission of uncovering dark affairs is still possible. Open-source intelligence provides various methods to leverage accessible messenger data, taking inquiries to the next level. So, without further ado, let’s see how OSINT analysts can use SL Professional to reveal the identities of threat actors on Telegram.
Disclaimer: SL Professional’s Telegram Pack is available only for government entities.
Telegram allows users to select an alias—a nickname or username that serves as the person’s online identity, as all sorts of information (messages, posts, interactions, etc.) is tied to it. While the Telegram app features plenty of privacy options, the username is always publicly accessible. So, investigators can look into aliases to see if the suspect is also using the same name on different social platforms.
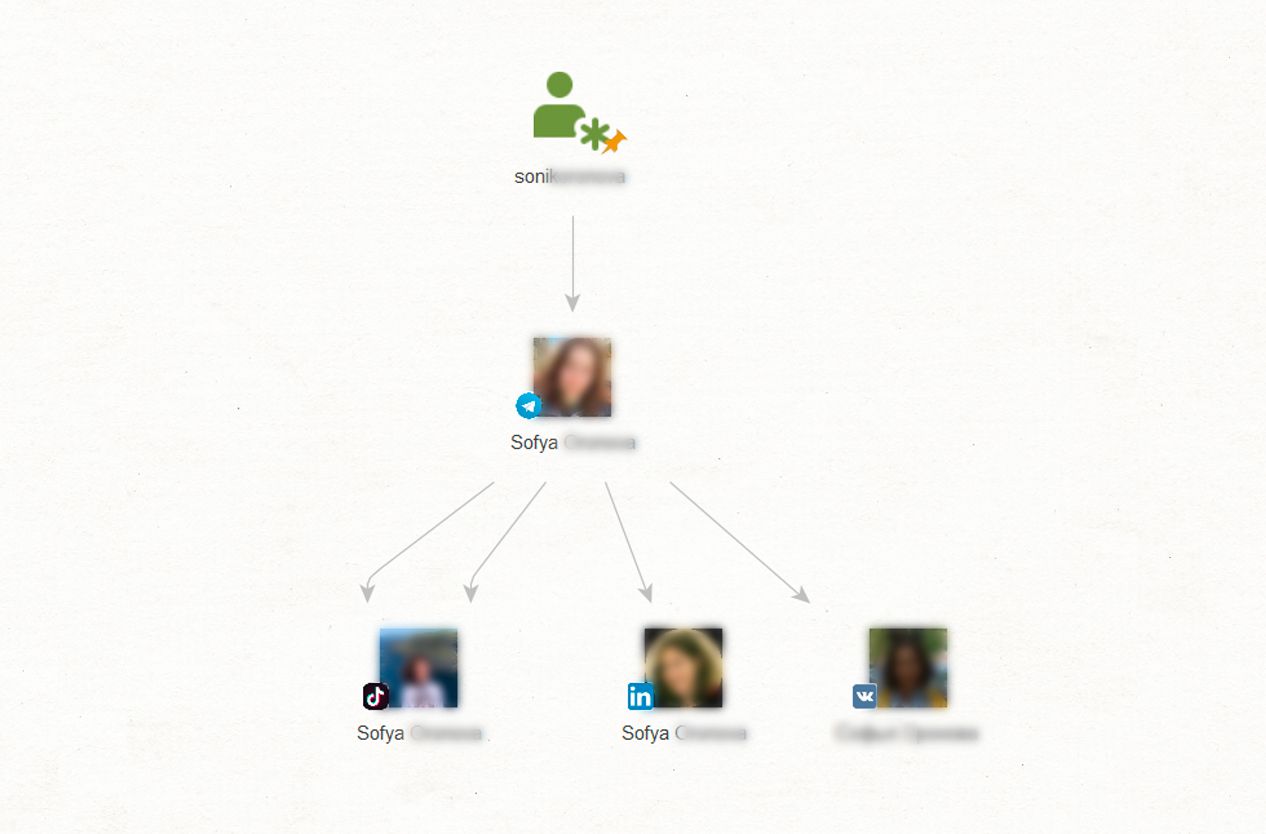
Let’s imagine we only have a person’s alias (sofyaexplorer), and we want to check if they appear on any other social media accounts. We start by running the [Telegram] Get Profile/Group/Channel transform to get the exact match of the username to use as input. Then, we need to find the subject’s other accounts. For that, we use specific search transforms—[TikTok] Search by Face and Name, [VK] Search by Face and Name, [LinkedIn] Search by Face and Name—which scan other social networks for exact matches.
Voila! We now have several accounts that we can further investigate, all belonging to a single suspect.
It's not a secret that Telegram requires a phone number to sign up. However, the user still decides whether to make their information publicly accessible. Contact details provide investigators with a way to enrich the inquiry significantly. Since phone numbers are typically a requirement for most services nowadays, they can serve as valuable links to other platforms, location data, follower lists, and more.
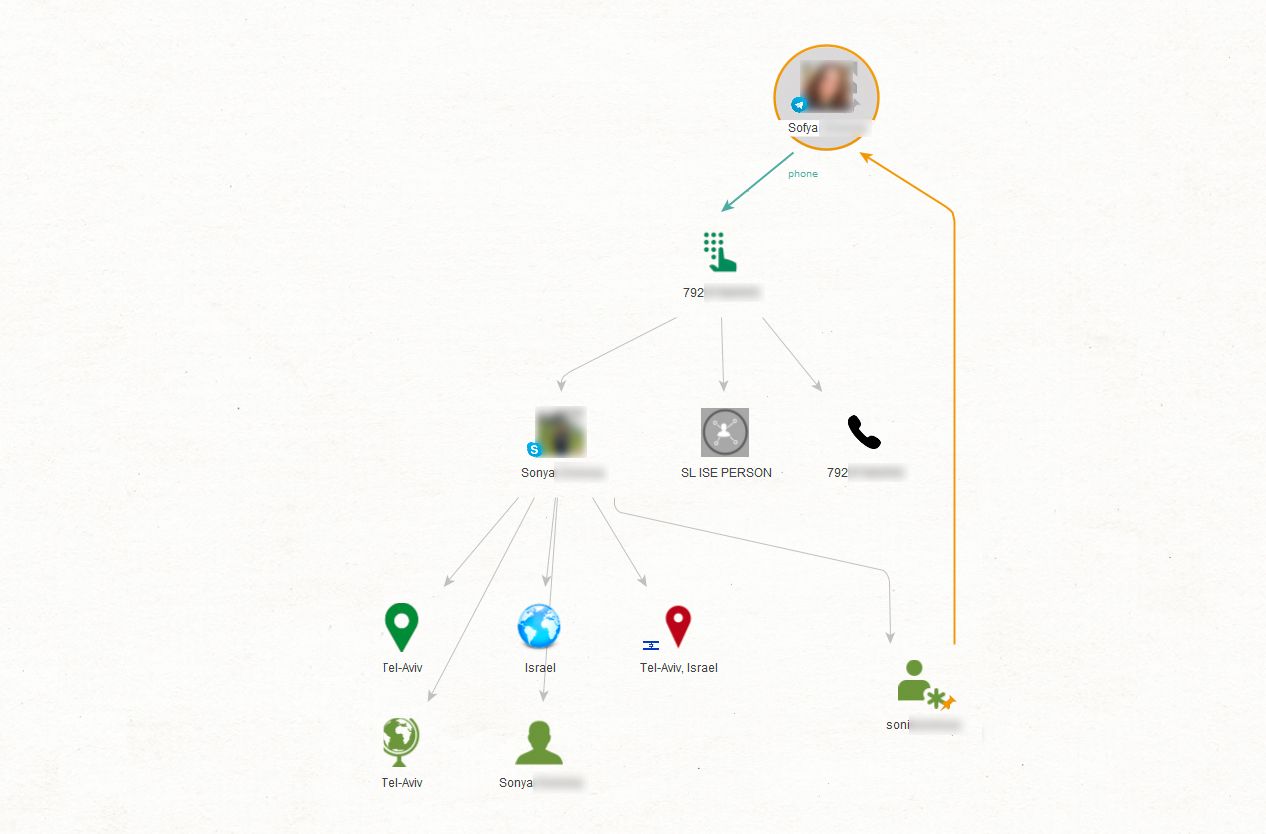
Let’s say we have an account (sofyabrown) with a public phone number and are looking for further information about the subject. First, we run the [Telegram Pack T4] Get Phone Number transform to use the contact data as input. Then, with [Skype] Get Profile, we match the phone number with an existing Skype account. Finally, we run the [Skype] Get Details transform to learn where our suspect lives.
Armed with location information and a proper name, we can start narrowing down our search using extra parameters.
Group discussions on Telegram are usually filled with links to other websites. Analyzing the shared web addresses gives valuable information about the person and their interests (or even reveals personal details). Hence, shared links can allow for the construction of a complete digital footprint for a specific individual.
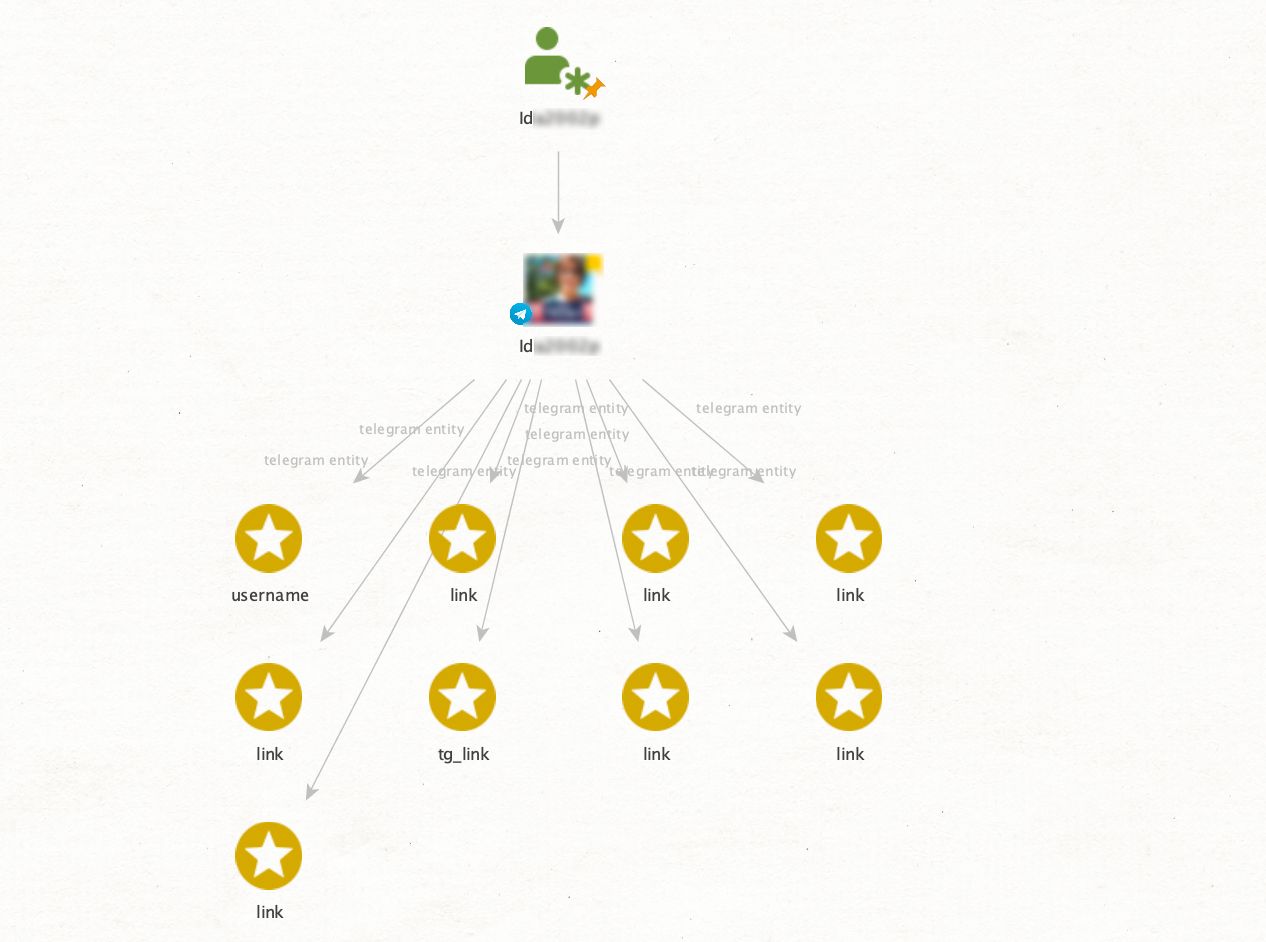
Let's imagine we have an alias (IRLMonster), and we want to get a sense of this person's interests. First, we have to run the [Telegram] Get Profile/Group/Channel transform to get the user account in order to utilize it as input for our inquiry. From this point, we can use the [Telegram Pack T3] Get Entities transform to access all the links shared by the person (see starred entities on the graph).
By exploring these shared links, we gain a deeper understanding of our suspect’s online presence and preferences, which we can use to enhance our investigation.
The photos users choose for their accounts are usually the first things people see when they look at a profile. Many people tend to use the same picture across different websites, causing search engines to log the image multiple times. Using account images helps build a digital trail, showing all the platforms where the picture appears online.
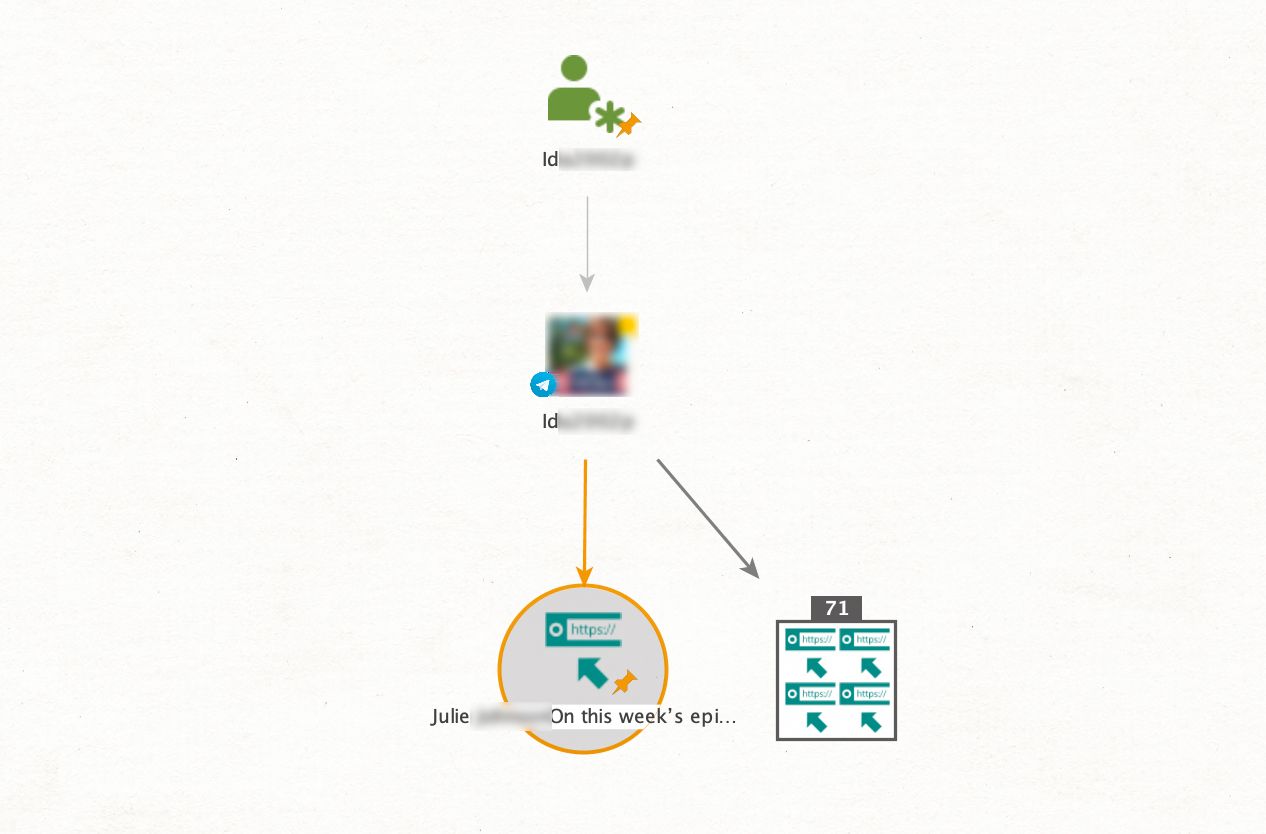
Now, let's put image search into action. Suppose we have an alias (IbuRanger) and are interested in uncovering more about this person through their profile picture. We first run the [Telegram] Get Profile/Group/Channel transform to access the profile. Next, we use the [Image] Reverse Search function to conduct an image search across the Internet.
This lookup results in plenty of websites featuring IbuRanger’s profile picture. With this information, we can obtain more evidence by checking the links to find links to blogs, employment history, etc.
What people write often reveals a lot about their identity and interests, whether on social media platforms or in messenger conversations. Investigators can piece together messages from publicly accessible groups, including responses, follow-ups, group themes, etc., to create a reliable picture of the person.
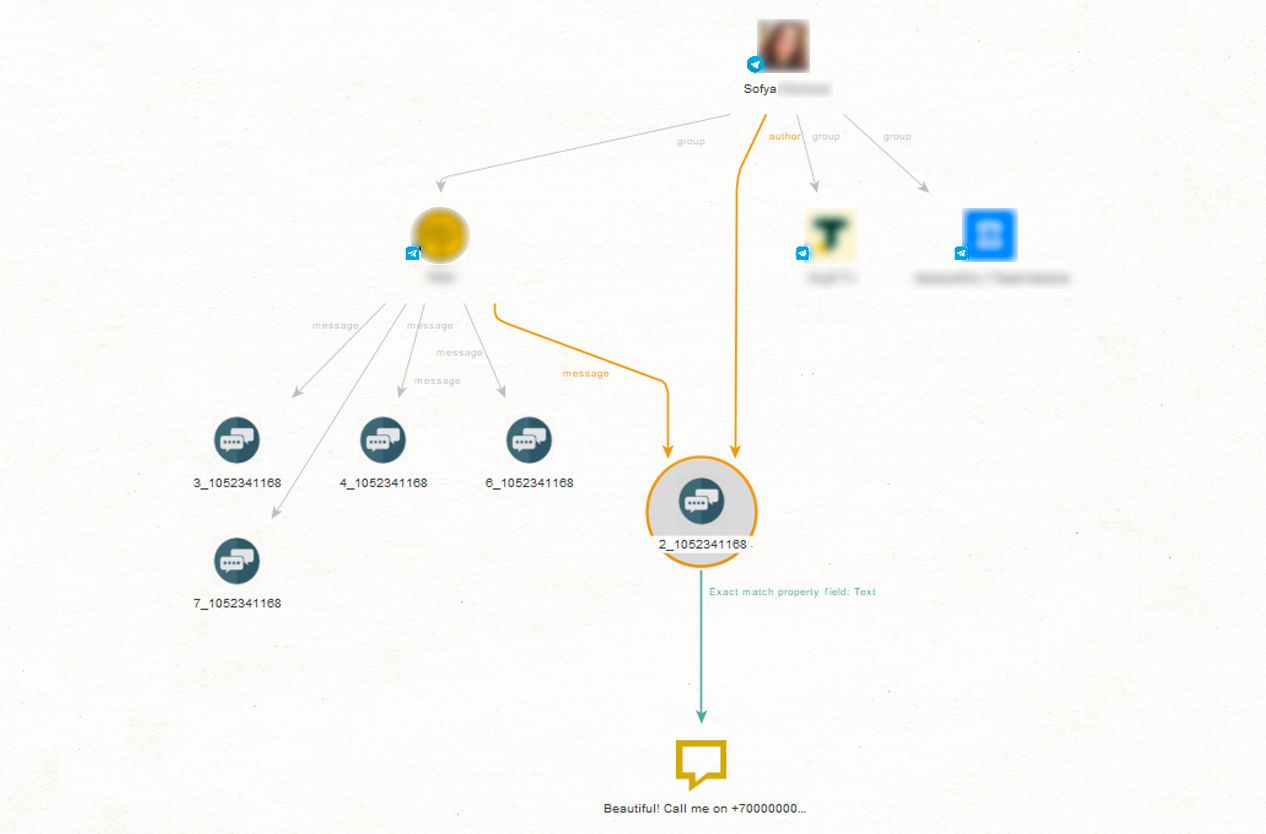
Let’s say that we have a profile (soflex). However, our subject’s privacy settings prevent us from seeing their phone number. No big deal. We first run the [Telegram Pack T2] Get Groups Messaged In transform to find all the groups where the suspect posted at least one message. Once we have the group chats, we run [Telegram Pack T1] Get Messages. Then we use [Telegram Pack T1] Get Author to identify which messages our suspect wrote before finally using the Extract Property to Phrase transform to get the text content from the correspondence.
Within this communication, we uncover a phone number. To continue our investigation, we can cross-reference the contact information with other sources and see who the owner is.
That’s all for our article about conducting OSINT investigations on Telegram! As you can see, the perception of privacy does not equal actual privacy. Hence, even on a service such as Telegram, OSINT investigators can gather plenty of information by just looking at a profile.