Preventing Data Breaches with OSINT Tools


Data breaches are becoming commonplace in today's digitalized world. In such a climate, the question is not if violations will happen but rather when. As businesses store our personal information more, their security flaws start impacting outside the corporate world. With the increasing number of system vulnerabilities, malicious actors are becoming more tenacious in finding new ways to exploit digital infrastructure.
In this article, we'll focus on the nature of data breaches. We will discuss the distinction between breaches and leaks, explore the damage they can do, see where the data goes following a violation, and discover how OSINT can help prevent such incidents.
So, let's take a closer look!
First things first, let's clarify the difference between both terms. While breaches and leaks are often used interchangeably, they actually don’t mean the same thing. So let’s clear things up.
Data leaks occur when private data becomes unintentionally publicly available. Most often, information leakage happens because of human error. Examples include databases without password protection (allowing anyone to access the files) or an employee sending confidential data to the wrong recipient. A door left unlocked is a perfect metaphor for a data leak.
Data breaches happen when sensitive information is exposed due to a cyberattack. In this case, the incident is more malicious than a data leak since the hacker exploits infrastructure weaknesses to gain access (passwords like “qwerty” contribute to such situations). If we use the same metaphor again, a data breach would be like someone breaking down a locked door.
Speaking of contents, compromised data include the following information:
Whether it's a data leak or breach, the result is the same: sensitive data is made public. Data leakage can be prevented by practicing cybersecurity hygiene. On the other hand, breaches require a company to restructure its whole infrastructure and continue to maintain its systems to prevent cyberattacks.
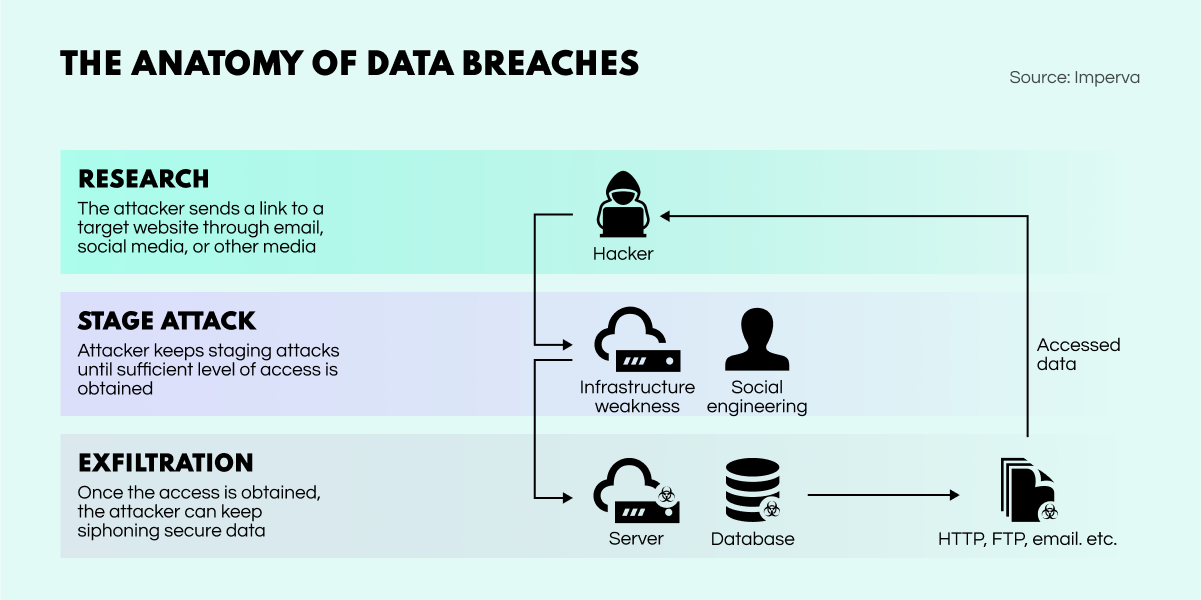
Before we go into more detail, let’s take a look at how a data breach occurs.
In the first step, a threat actor conducts extensive research to identify any flaws in the target system (which can range from an individual to a multi-national corporation). The hacker may look at human vulnerabilities — for example, to select an employee who has a weak password. Additionally, the criminal can reveal any vulnerabilities within the system, which may provide easy access to it. After the malicious actor figures out the optimal way to attack, the infiltration begins.
The second step is the cyberattack process. If the hacker targets specific people, social engineering tactics such as impersonation (where the criminal assumes someone else's identity to get private information) or emails with malicious links might prove successful. In case of a systems-oriented attack, the malicious actor can hack the system directly, gaining unauthorized access to company information.
The last step of the data breach cycle occurs once the server or database (or both) is successfully compromised. The cybercriminal copies all the information they seek to a drive they control. Following the attack, data such as PII, secret knowledge, login credentials, etc., are all compiled in a spreadsheet. Finally, the hacker erases all signs of infiltration, and voila, a crime is committed.
According to Statista, in 2022, the average cost of a data breach worldwide was $4.35M, which is an increase of $1M since the start of COVID-19. There are several reasons why incidents have started costing more, but the main one was the sudden transition to remote work, challenging companies' existing infrastructure. However, it is not all. Next, we will unpack other factors that impact why breaches cause devastating financial losses.
When dealing with data breaches, discovering that a company’s system has been compromised is the trickiest aspect. The way time affects cost is straightforward: the longer an incident goes unattended, the more it will cost the firm. However, identifying an infiltration is not immediately noticeable most of the time. On average, finding and containing a data breach takes 277 days. Furthermore, the time frame of incidents can vary significantly depending on how the system was compromised.
To put things into perspective, let's remember the case of the Shangai police, who fell victim to one of history’s biggest private information leakages. It was revealed that over 1 billion governmental records of civilians with names, ID numbers, phone numbers, and incident reports were compromised. The saddest part about this situation is that it took authorities over an entire year to notice that their data was leaked. And it all happened simply because… the staff forgot to secure their database with a password.
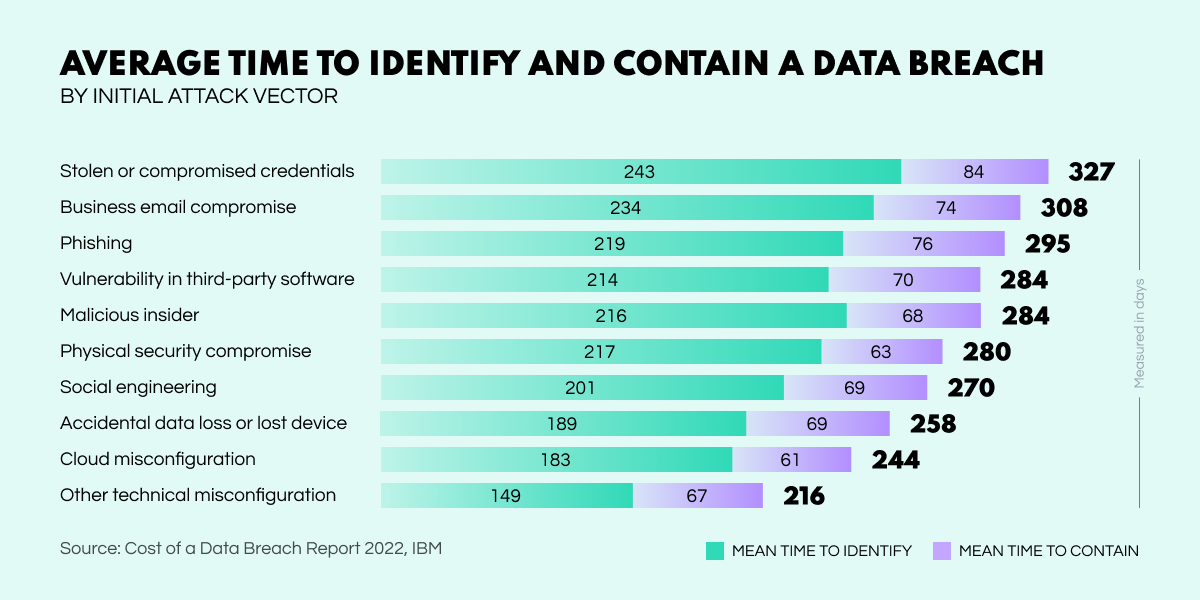
One reason why detecting breaches becomes very difficult is the massive level of data traffic security specialists need to track. With most of the work being routine monitoring to ensure that no information is compromised and the servers are secure, the process can significantly strain the IT personnel. Furthermore, since hackers operate at odd hours, noticing a violation during a shift is not a realistic way of looking at cybersecurity.
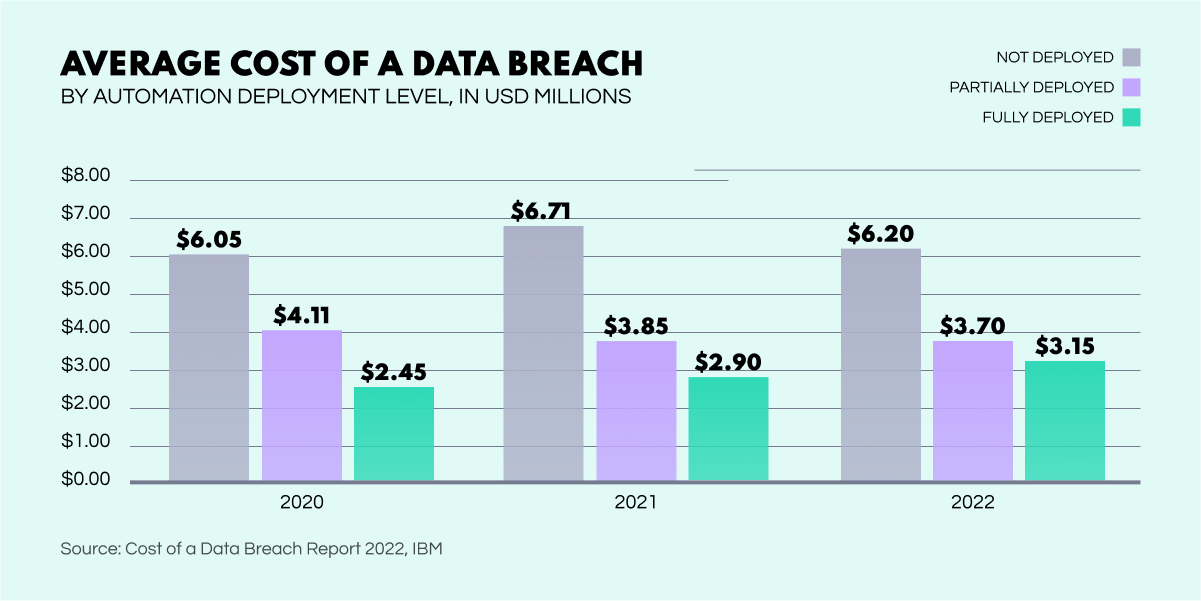
Luckily, AI automation provides a way forward when dealing with vast amounts of data. Through machine learning, it is possible to monitor user interactions, flag suspicious activities, and patch any security vulnerabilities promptly. Data breach costs can visibly decrease with even a partial artificial intelligence deployment. Moreover, a fully integrated system can result in reductions of up to 65%.
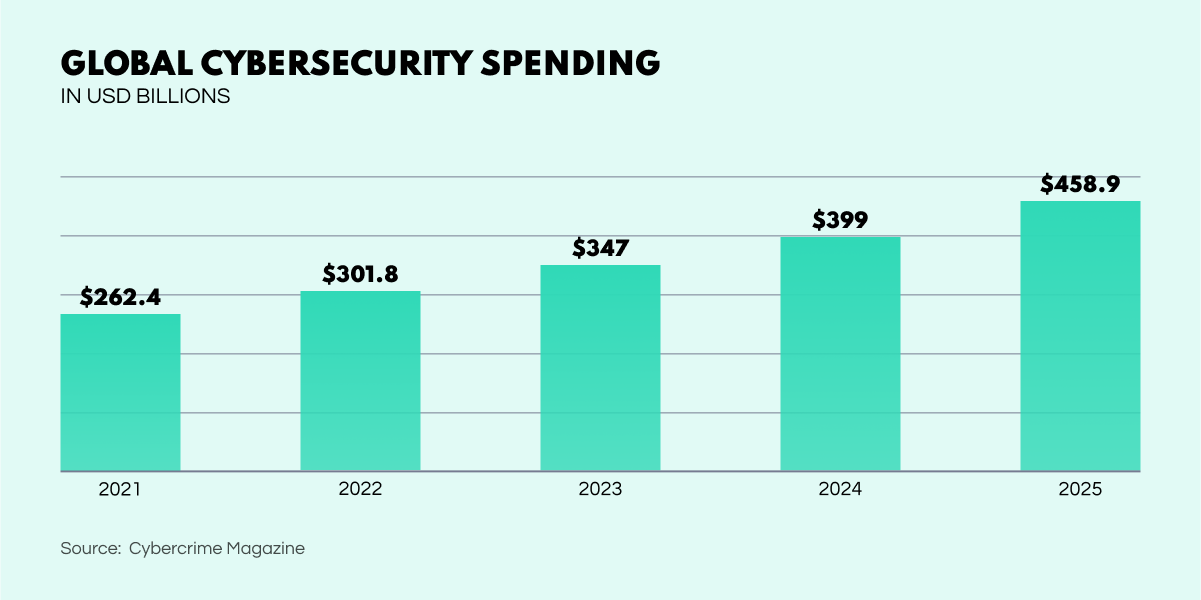
Digitalization has become a non-negotiable element of life and business. And despite the importance of cybersecurity being common knowledge, many companies are reluctant to set aside proper funds for data security. According to the IDC report, in 2020, 50% of organizations allocated only 6-15% of their security budgets to information protection.
The cybersecurity industry is worried about companies spending money on unnecessary security measures instead of what's essential. Even though businesses are expected to invest $267.3 billion in cybersecurity by 2026, a recent survey found that over 70% of companies think they're wasting their money because they can't fix the security risks they identify. The problem is that these organizations don't have a complete cybersecurity plan, which makes it hard to detect and respond to threats reliably.
During a breach, hackers may steal information for various reasons. While some criminals are driven by a political agenda, others are after making money through selling stolen data. Understanding the threat actors' behavior behind a cyberattack can affect the necessary actions that must be taken. Following a breach, these are the most significant destinations for the compromised information:
An increasingly popular space for hackers is Dark Web forums that position themselves as "data leak marketplaces" — e-commerce sites for stolen data. With over 30 active platforms and a combined revenue of $140M, these online exchanges have become dominant players in the extortion economy. Since such marketplaces operate outside of the Surface Web, shutting them down becomes a very time-consuming task, requiring multiple countries to work together.
Such was the case with the invitation-only Genesis Marketplace. The platform sold digital identities in the form of bots. Buyers would get all the information required in order to impersonate the victims. Over the course of four years, 17 countries worked together, and the FBI took down the illegal marketplace along with its infrastructure.
Malicious states actively finance the infiltration of companies and foreign nations to enhance their intelligence strategies. Through coordinated attacks carried out by hackers trained and employed by the state, supply chains can be disrupted and top-secret information compromised. Because the existence of such threat actor groups is often denied, governments can’t bring these cybercriminals to justice.
For example, the North Korean government actively sponsors a hacker collective named the Lazarus Group. Between August and November 2022, the cybercriminal group was involved in an extensive hacking campaign. Infiltrating private and public sector organizations worldwide, the malicious actors stole over 100 GB of confidential data relating to medical research, healthcare, chemical engineering, energy, defense, etc.
Sometimes companies resort to hacking their competitors' systems to gain an edge. While such activities are highly illegal and thankfully not commonplace, there are still cases where firms steal trade secrets and confidential information of rivals to enhance their own strategies. When legal proceedings reveal such misconduct, the criminals can face significant fines.
In 2017, concert discovery service Songkick sued Ticketmaster for allegedly hacking their databases to obtain confidential strategies. Using the login information of a former Songkick employee, Ticketmaster was revealed to have adjusted their strategy to put the plaintiff out of business. The company admitted to the charges and agreed to pay $10 million in damages. However, Songkick still went out of business shortly after and was acquired by the Warner Music Company a few months later.
Some hackers steal data for political reasons rather than financial gain. Calling themselves "hacktivists," their motivation is usually ideological, often targeting organizations they view as a threat. Unlike other criminals, they don't usually sell the information they obtain but instead release it online on public platforms to draw attention to perceived wrongdoing.
Such was the case In 2021 when Anonymous, a hacktivist collective, hacked into the system of Epik, a domain registrar, and exposed 180GB of data and 15 million e-mail addresses. The group claims that it breached the company because of its involvement with far-right organizations, which was revealed in the leaked information. However, the hack also affected users whose data was purchased by the company, compromising many individuals who were not even aware of the registrar.
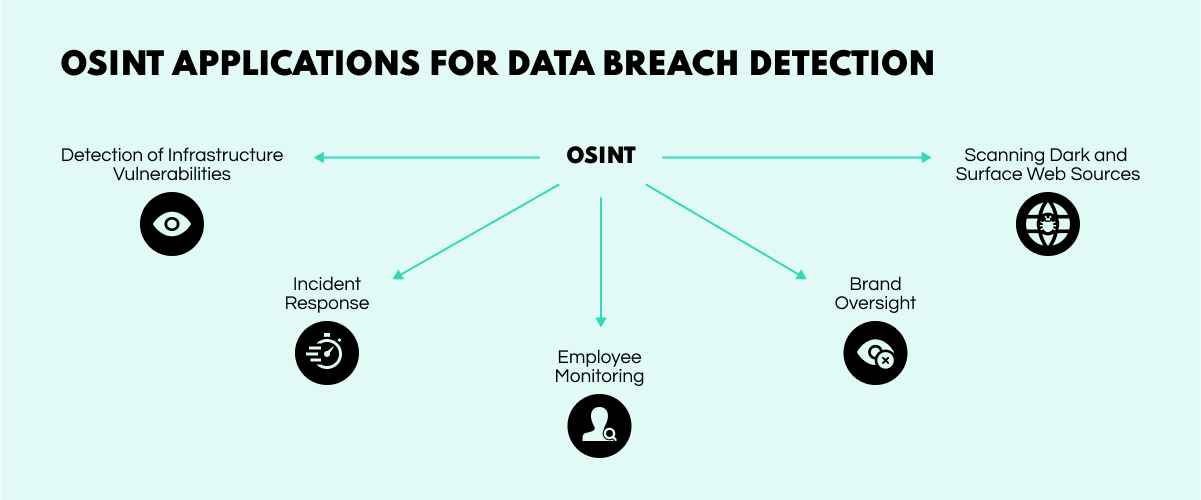
Data breaches are not limited to their immediate impact but have wider consequences. These incidents affect the online environment, creating opportunities to detect and stop them from happening again. Scanning the diverse range of sources needed to remediate data breaches can be overwhelming, but open-source intelligence can help. This is how.
After a data breach, hackers often announce their intention to sell the stolen information to third parties. These statements are often made on Telegram channels and Dark Web forums, which are the preferred platforms for advertising data breaches. Monitoring these messages can provide investigators with valuable insights.
However, doing this manually can be a time-consuming task. OSINT software can be used to quickly find out about violations by scanning both the Internet and the Dark Web as well as analyzing open sources to expand their search.
For cybersecurity professionals, waiting for a data breach to test the company’s security infrastructure is a risky bet. Instead, proactive specialists can use OSINT technologies to perform penetration testing in various ways. One example is using specialized Google searches (dorking) to identify weaknesses.
Scanning open sources for leaked information is another effective method. These tactics can help identify security flaws before they become a problem and also allow for perimeter monitoring to prevent threat actors from initiating an attack.
One major factor behind many violations is hackers targeting employees of a specific company. To help prevent this, open-source intelligence tools can be used to monitor key staff and identify any attempts to compromise their accounts.
Additionally, businesses can raise cybersecurity awareness by sending phishing emails to their own workers. By taking these proactive measures, employers can keep their personnel up-to-date and better protected against common security vulnerabilities.
After a company is hacked and its data is leaked, reports of the breach are often spread through news, messengers, and social media. Usually, it's done by hackers, and then the media picks up such news with great pleasure. In this case, OSINT can give analysts an edge, so they can go to the original source of the story and analyze where the information came from.
Thus, organizations can understand all the risks and consequences of the violation for their customers. By investigating the incident and publishing a public review of it, it becomes possible to restore the trust and loyalty of the user base.
When a company experiences a data breach, it can be very stressful and hard to make the right decision and figure out the next steps that should be taken. However, through OSINT solutions, actionable insights such as the severity of the data breach, the affected systems, and the hackers involved can be identified. Such knowledge can be the determining factor between a containment protocol and significant monetary losses for a company.
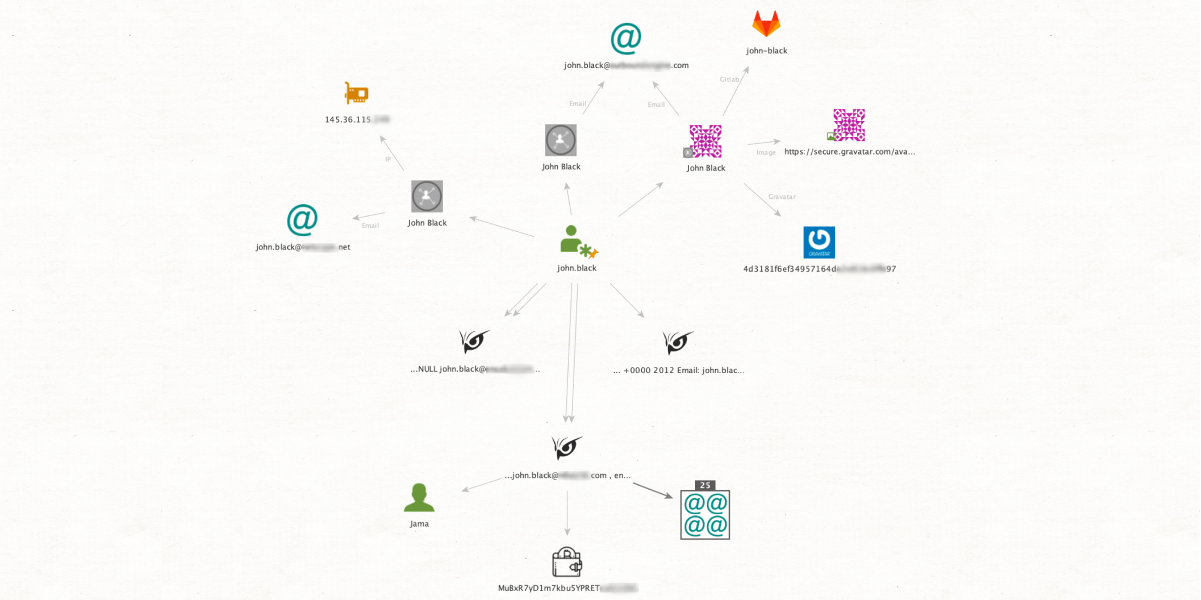
Let's put this into a practical scenario. Imagine that John Black, who used to work in cybersecurity and is now the CEO of a tech startup, comes to the office one day and finds his employees in a panic. The system administrator tells him there has been a data breach, and they are trying to contain it. While John's analysts are working hard on the situation, he turns to SL Professional to see what he can find out.
John Black discovers that his personal data has been compromised using the [SL ISE] Search transform with his online alias "john.black" as input data. With the help of the powerful Dark Web-focused [DarkOwl] Search (exact) and [DarkOwl] Leaks Search (exact) transforms, John finds out that his email account is being shared in data leak forums.
This is a serious problem for John Black's company, as he has sent numerous emails to the product team with sensitive data about the future of the business. If this information falls into the hands of competitors, it could be disastrous. Thanks to the insights gained through SL Professional, John quickly decides on his next steps. His first priority is securing his compromised accounts, then assessing the extent of the breach across the company.
As a result, John Black easily and quickly obtained crucial information through SL Professional. This insight allowed him to contain the breach and prevent further damage in time. By using the platform's automated scanning features, he was able to get practical insights rapidly, which was essential in a time-sensitive situation.
This concludes our introduction to the nature of data breaches and leaks. We hope you understand how serious data compromises can become and why including OSINT can massively reduce problems when dealing with them.