Social Links Product Updates Q1, 2024

It’s time for our quarterly OSINT product updates where we bring everyone up to speed on what we’ve added to our functionality over the last few months. And so far, the first quarter of 2024 has been hugely productive, seeing us introduce some major new features connected to darknet data and the popular search-and-discovery app Foursquare, plus a tweak for our NER function.
Here’s the lowdown.
Having received our focused work and attention for an entire quarter, our darknet functionality has seen a major expansion and now boasts three completely new features built from the ground up, which can revolutionize all kinds of investigation:
This hugely innovative transform is part of a new plug-in and an industry first—nowhere else can you combine these forms of data in a single investigative space. [SL Darknet] Search in Stealer Logs will be a game-changer for exposure checks and regular surface web investigations.
The data provided is derived from stealer logs, meaning that if a subject’s device has been infected by infostealer malware, it’s possible to view a remarkable amount of key information. These include browser history, device serial number, linked emails, passwords, and more. Such results can also be far-reaching, opening the door to subject relatives or an entire organization department.
[SL Darknet] Search in Stealer Logs can be run from alias (username), person (name), email, device serial number, URL, or email domain entities. Once the transform has been run, apply [Extract] Entities for your results, which will appear in structured form on the graph.
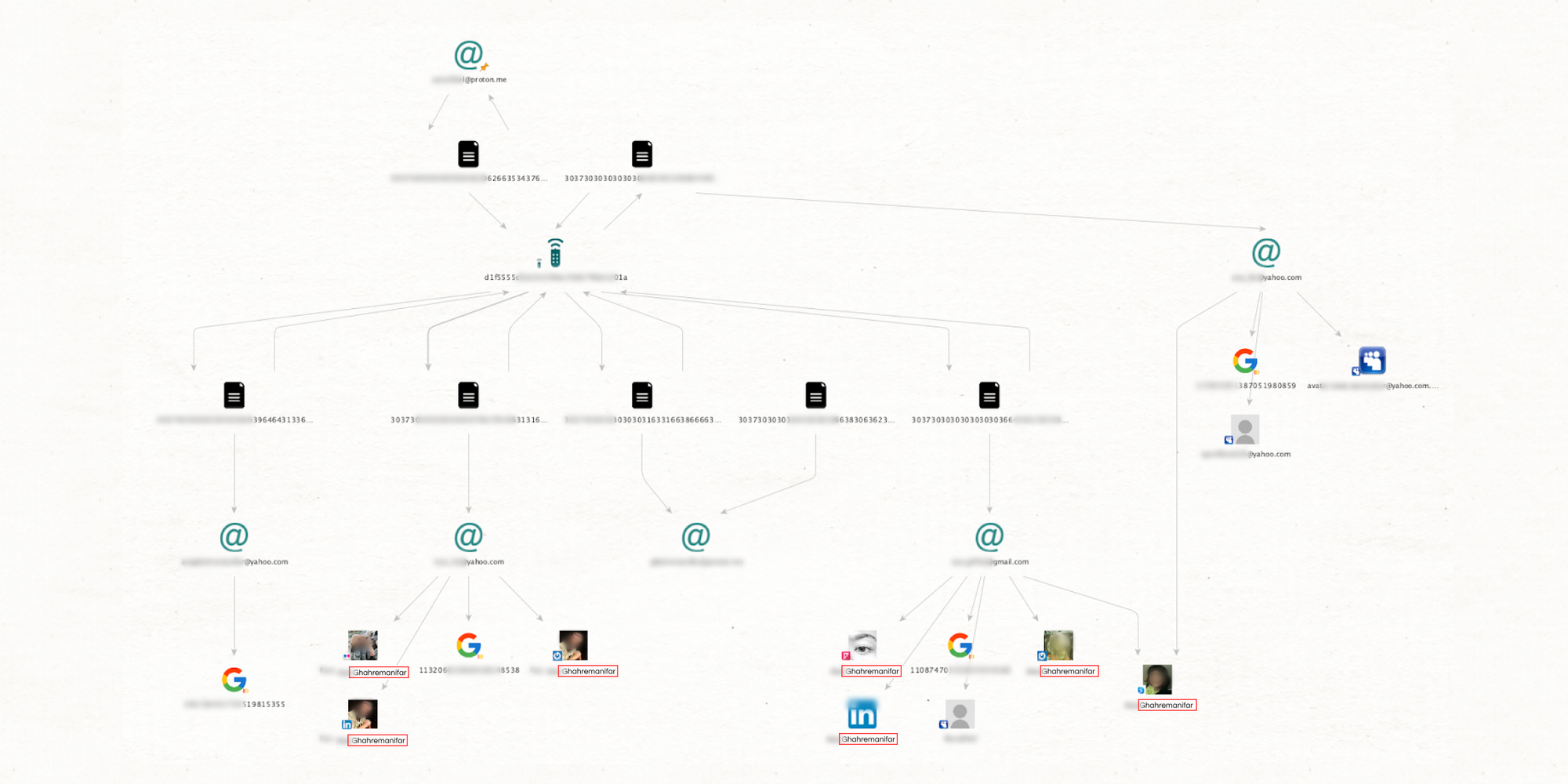
Another new transform that could revolutionize exposure checks and surface web cases—even when the subject isn’t a darknet user.
Compared to stealer logs that can only provide information when the subject’s device has been infected, almost everyone’s data is involved in a leak at some point. Sometimes, a small leak from a food delivery service, for example, provides the very link you need to resolve a case.
The data for this transform comes from a provider specializing in data leaks. This means the data is extensive and well-structured, significantly raising the chances of finding the information you need to wrap up a case.
[SL Darknet] Search in Leaks can be run from phone number, alias (username), email, cryptocurrency, IP address, person (name), and email domain entities. You then need to run [Extract] Entities to view your results.
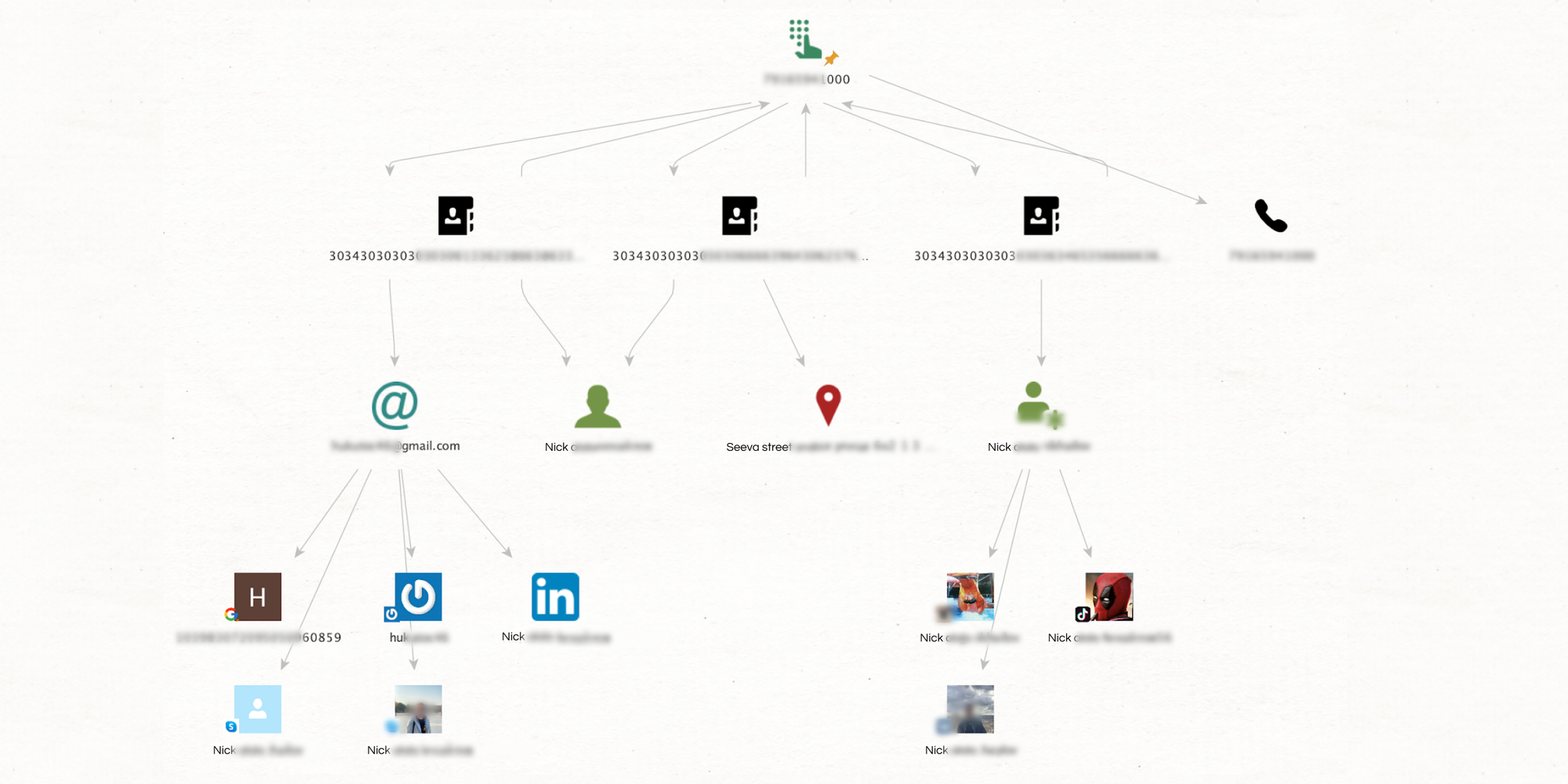
This is another transform that utilizes specialized data, but is more geared towards conducting in-depth searches throughout the Deep and Dark Web, as well as other recesses of the internet, largely associated with criminal activity.
The transform allows you to investigate various sources, including darknet marketplaces, Deep Web (password-protected/invite-only) forums, paste sites, alternative social media platforms, and more. This can be done like you would investigate Surface Web forums and marketplaces—view topics, discussions, listings, sellers, etc., and anlayze the data further.
Simply run [SL Darknet] Search in Deep Web from your entity of choice (alias, phrase, email, phone number, cryptocurrency, or email domain) and explore the results!
Once the social media darling of local spot exploration, Foursquare remains a goldmine for open-source intelligence investigations. We've significantly enhanced our Foursquare functionality to help you dig deeper and uncover your needed connections. Here’s what we’ve added:
This transform lets you extract profiles directly from phone numbers and email addresses. This directness is particularly useful considering the sheer quantity of Foursquare accounts out there, where searching by name would be very time-consuming. Plus! This feature also works for Facebook and Twitter/X accounts linked to a Foursquare profile.
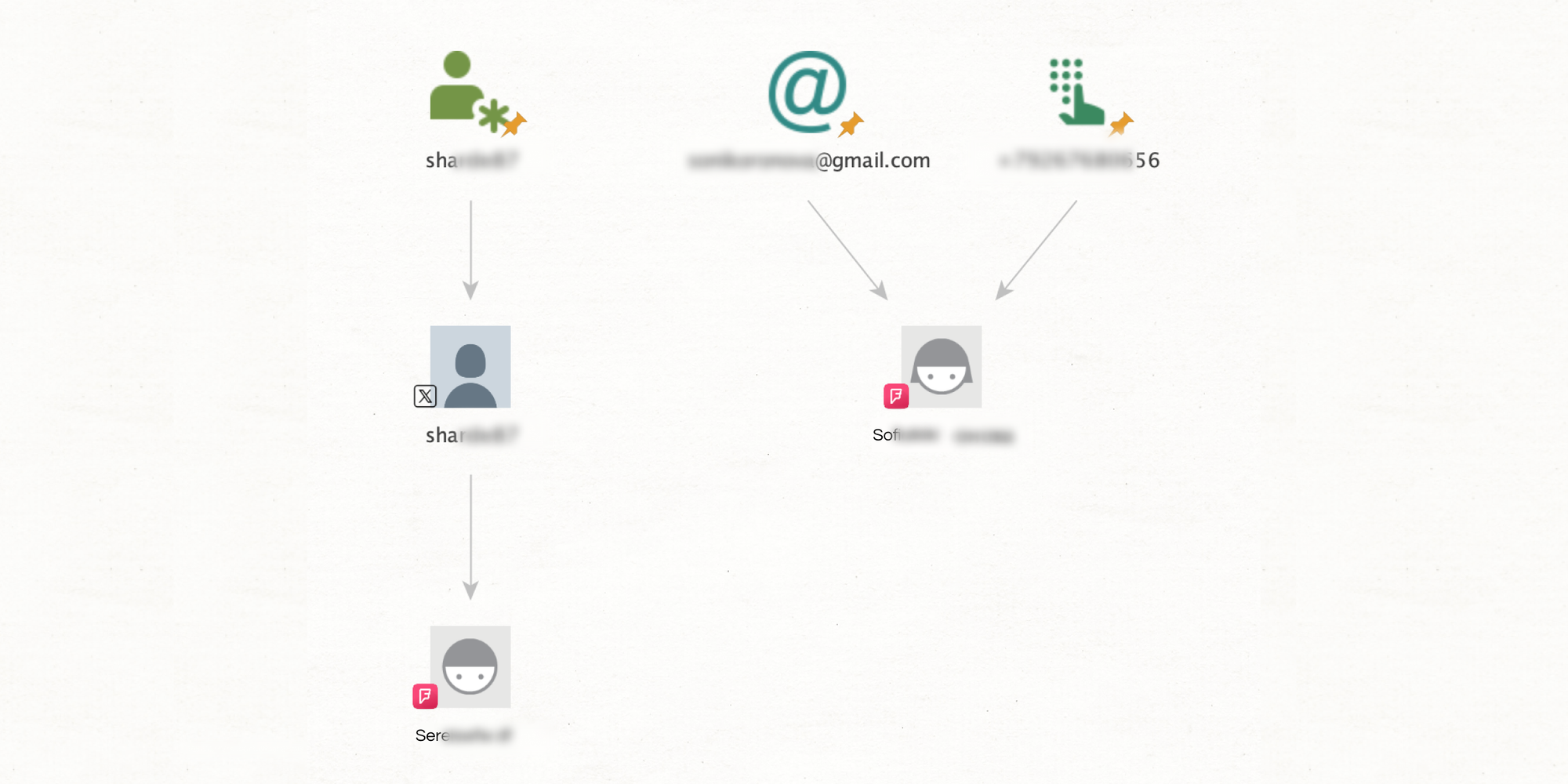
With this feature, you can search for a person's name directly on Foursquare, setting the stage for the next steps in your investigation.
This transform reveals a user's current location as well as any social media profiles connected to the account. Transforms such as this are great springboards, allowing you to pivot to other platforms and expand your investigation.
Dive into a subject's social circle. These features reveal a user's Foursquare connections, which may contain more varied and perhaps forgotten contacts, offering valuable insights into the subject’s network.
As you may know, this is one of our ML-driven features for deconstructing text. So what’s new? We’ve been working hard to improve the algorithm to break down text more efficiently and with a greater number of composite entities.
Simply run [Extract] Entities from Fields from any entity with text—this could be a phrase, a LinkedIn post, or a Telegram message.
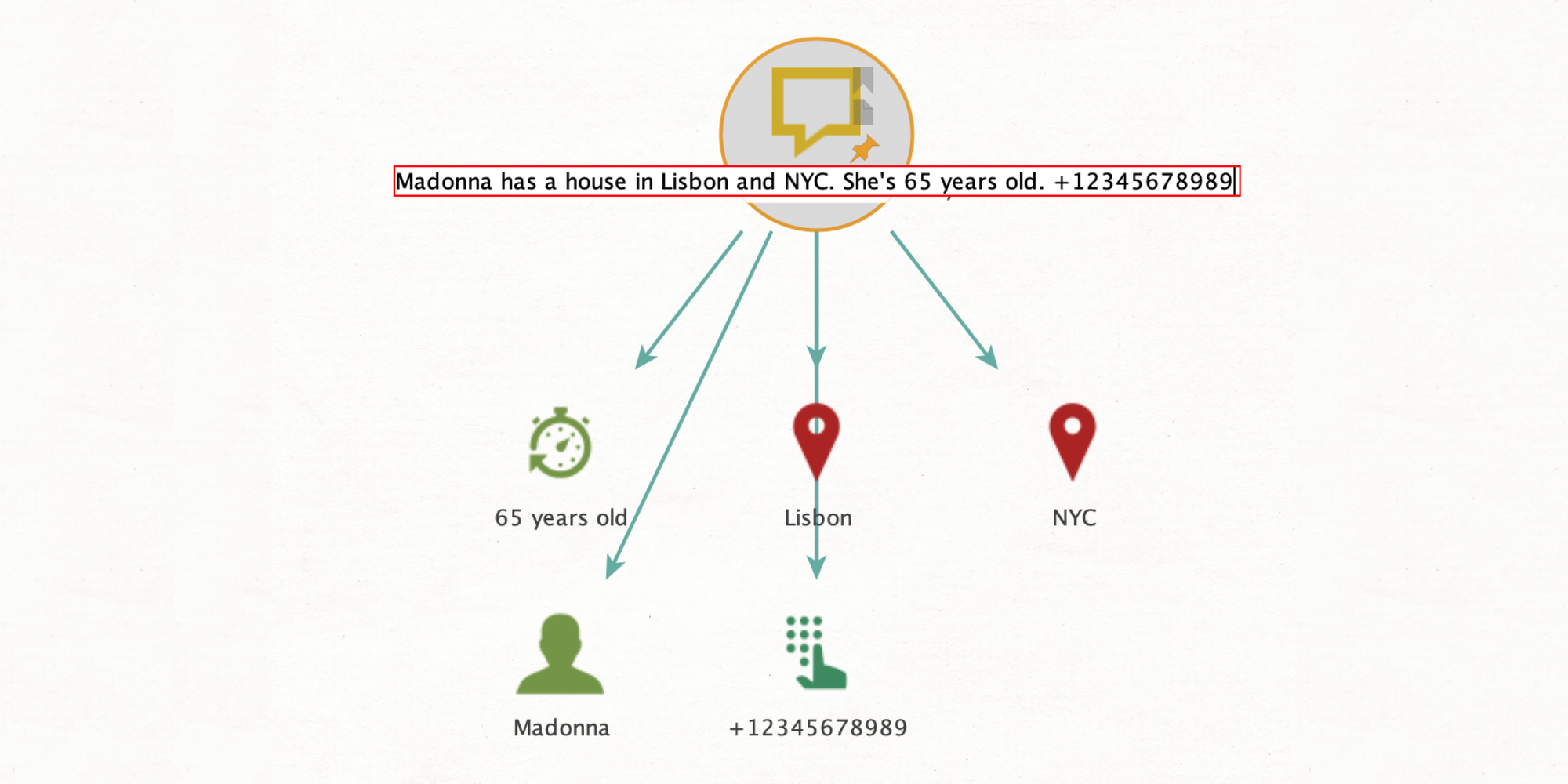
And that wraps up our OSINT product updates for Q1, 2024. We just want to reiterate that the darknet updates, particularly, are huge. And that you’ll also find the Foursquare additions and NER update very useful. Try them!
If you have any questions about how any of these features work, follow the link below and set up a meeting with one of our specialists.