SOCMINT: A Pillar of the Modern Investigation and Next-Gen Security


In the current era of hyperconnectivity, the digital footprints left by individuals and organizations are a critical intelligence source for security professionals. As publicly available data has swelled and evolved, social media intelligence (SOCMINT) has emerged as a go-to discipline for transforming vast amounts of raw data into actionable intelligence. For readers new to the broader intelligence context, it may help to first explore how open-source intelligence works in 2025, providing the methodological foundation on which SOCMINT techniques naturally expand.
So in today’s Centre of Excellence article, we’re taking a look at how SOCMINT tools and techniques are revolutionizing global operations essential to societal and national security, such as counter-terrorism, organized crime investigations, and anti-money laundering and (AML/CFT investigations).
The explosion of social media platforms and subscribers has created unprecedented opportunities for digital intelligence gathering and open-source intelligence deployment. For investigators across law enforcement intelligence units, corporate security teams, and private investigation firms, SOCMINT offers distinct advantages, including:
A 2024 UNODC training program for conducting counter-terrorism investigations highlights how social media intelligence has become indispensable, with participants learning advanced techniques to detect terrorist recruitment, propaganda, and coordination activities online. This underscores how SOCMINT has evolved from a supplementary tool to a core intelligence discipline.
Much like the broader discipline of OSINT, SOCMINT is developing at breakneck speed, incorporating all manner of emerging technologies and techniques across its methodolgical landscape.
One cornerstone of modern open-source intelligence and SOCMINT operations is the ability to carry out sophisticated network and link analysis. A deeper practical overview of how link analysis supports real-world investigative workflows is explored in our guide to link-based intelligence methodologies, demonstrating how relationship mapping strengthens investigative accuracy and attribution. By providing intuitive network analysis tools for uncovering ties, command structures, and financial flows that would at times be less obvious when using traditional investigation methods, tools such as SL Crimewall have transformed how security professionals visualize connections between persons of interest (POIs).
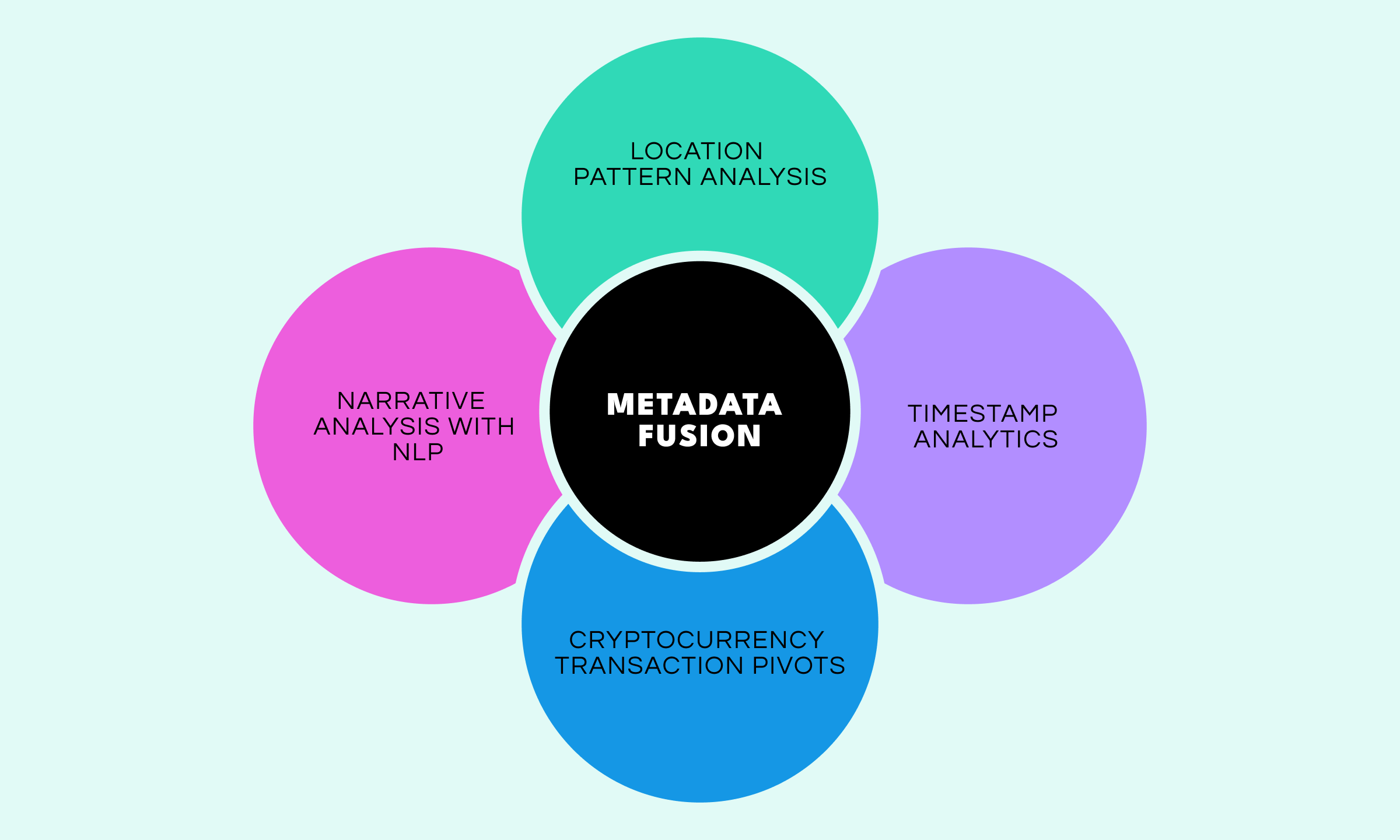
Modern investigations rarely remain confined to a single platform. On the contrary, advanced SOCMINT methodologies often include fusion techniques that combine metadata analysis spanning location patterns and timestamps, pivots into cryptocurrency transactions, and narrative analysis through the application of natural language processing (NLP). This multi-pronged approach delivers a holistic picture of a POI’s digital footprint, which can provide investigators with court-admissible evidence chains.
While AI has become something of a buzzword, sometimes smacking more of marketing strategy than actual utility, in the case of SOCMINT tools, machine learning has brought real and dramatically enhanced capabilities for threat detection, including:
With its powerful suite of AI features, Social Links Products underscore the huge effectiveness of such tools, allowing investigators to process vast sets of data that would not be doable manually within a reasonable timeframe.
Social media intelligence has repeatedly reinforced its critical role in incident prevention and investigation, in the aftermath of major terror attacks. Following the 2017 Manchester bombing, intelligence teams used sophisticated SOCMINT techniques to monitor extremist-linked accounts, identifying radicalization patterns and potential pre-attack warning signs.
What’s more, terrorist networks are increasingly operating through social channels for financial purposes, using crowdfunding campaigns and conducting transactions in crypto. Social media intelligence tools like SL Crimewall have proven invaluable in mapping these financing structures, advancing counter-terrorism units’ capabilities to disrupt resource flows before they reach operational cells.
The "764" child exploitation network case demonstrates SOCMINT's power against organized criminal enterprises. Investigators tracked communication patterns across Discord and Telegram, ultimately leading to the arrest and 30-year sentencing of network leader Richard Densmore. The investigation's success hinged on metadata analysis that connected seemingly anonymous accounts across multiple platforms.
This approach has profound implications for all organized crime investigations, allowing security professionals to:
For a broader picture of how SOCMINT integrates with traditional criminal investigation methodologies, see our detailed overview of OSINT in criminal investigations, where social intelligence, network mapping, and digital evidence validation are combined into defensible investigative processes.
Financial intelligence units worldwide are increasingly incorporating social media intelligence into their AML and CFT operations. Case studies from Shadow Investigations Ltd. demonstrate how SOCMINT techniques have successfully traced illicit transactions linked to darknet markets.
By mapping money-laundering networks through social media chatter, investigators can identify:
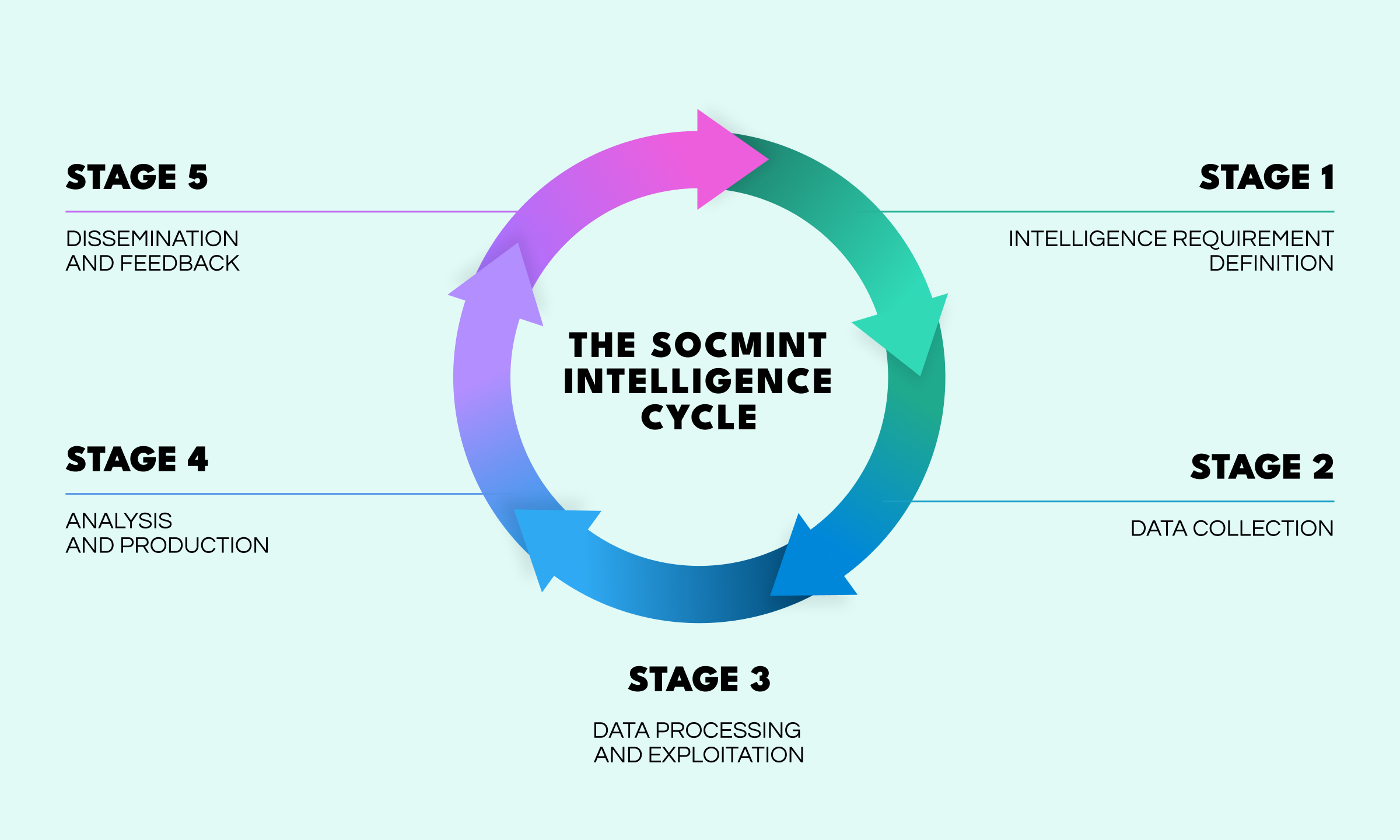
Effective social media intelligence should follow the standard and classic intelligence cycle, consisting of:
This method ensures SOCMINT activities remain focused on addressing specific security challenges, rather than drifting into monitoring of an unfocused nature.
While there are numerous social media intelligence tools on the market, security professionals are increasingly turning to comprehensive solutions that offer end-to-end investigation capabilities. Social Links solutions are proven to excel in this regard, with the company being recognized by Frost & Sullivan as market leaders in SOCMINT tools for law enforcement intelligence.
The products available address the full spectrum of SOCMINT requirements:
A distinguishing quality of SL Cimewall in particular is its focus on user-friendly interfaces that allow investigators to focus on conducting productive analysis rather than overcoming technical hurdles. These solutions significantly reduce the time between drafting initial intelligence requirements and actionable insights.
As the reach of social media intelligence tools and techniques becomes ever greater, responsible implementation becomes increasingly important. In such a climate, security professionals must conduct their work while navigating complex ethical and legal considerations, including:
Industry leaders like Social Links are aware of these issues, to the extent that their compliance is actually worked into their platform designs, ensuring investigations remain both effective and ethically sound.
Moving forward, several trends are set to shape SOCMINT's evolution over the next couple of years:
As more and more users migrate to decentralized and encrypted platforms, SOCMINT tools will evolve to overcome new technical challenges. We anticipate significant advances in the ability to correlate identities across increasingly fragmented digital landscapes.
The proliferation of AI-generated content presents new challenges for intelligence verification. Advanced SOCMINT platforms will start incorporating sophisticated detection algorithms to distinguish authentic content from synthetic material.
Shifting privacy frameworks will reshape SOCMINT methodologies, demanding a greater emphasis on transparency, proportionality, and necessary access. Security professionals should prepare for this changing landscape by adopting solutions designed with compliance in mind.
The window between digital intelligence gathering and operational response will continue to narrow. Next-generation SOCMINT tools will offer near-instantaneous analysis capabilities, allowing security teams to respond to emerging threats as they develop.
Social media intelligence has evolved from a niche discipline to an essential component of modern security operations. For professionals generating law enforcement intelligence, or conducting corporate security or private investigations, mastery of SOCMINT methodologies is no longer optional—it's a fundamental requirement, bringing the power of next-gen tech such as AI, to deliver ever more effective threat detection and response.
By adopting comprehensive solutions such as those offered by Social Links, security teams can transform overwhelming volumes of social data into precise, actionable intelligence. As digital landscapes continue to evolve, SOCMINT capabilities will remain at the forefront of security innovation and data analysis, offering unprecedented insights into threat actors and their activities.
The future belongs to organizations that effectively leverage these powerful intelligence sources while maintaining a responsible approach to their implementation.
If you'd like to learn more about Social Links industry-leading solutions and how they can revolutionize a wide range of SOCMINT processes, get in touch. Just follow the button below and we can set up a free, personalized demonstration with one of our specialists, and show you first hand the difference our tools can make in your workflows.