Speed up your investigations in the world of digital human traces


There is a byproduct of social media culture which is sometimes overlooked: while we are busy broadcasting our lives, sharing anything and everything to whoever will listen, we fail to remember that our activities are not as transient as our thoughts. The world is becoming increasingly public, and what users of social media lose in privacy, the investigator gains in case material.
In the online realm, very little vanishes without a trace. While following footprints may seem like a detective trope consigned to history, it is still a process which is central to the investigators work, only the imprints which provide case threads today are digital and exist on servers rather than physical surfaces. In the modern age of technology with hundreds of social media outlets, FaceTime and Zoom are bridging distances between people and making remote relationships a business-standard. When one graduates from university or starts a new position – this news is instantly added to our online “persona.” We share our personal information without a second thought on Facebook, LinkedIn, VK, GitHub, etc. A new boyfriend or girlfriend? We tag them on one of our social media profiles and disclose their personal information to everyone. Looking for a partner on Tinder? We disclose a lot of personal information we would not think of doing otherwise. But today all these users are pouring all this information onto the web worldwide.
A question that is not often asked is – is the internet safe? Multiple features and face-filters are available for people to alter and hide their identity, meaning people are no longer sure whether they are talking to that blond girl in Australia or a tech-savvy hacker sitting in Asia and looking to break into your system. Your neighbor finds out that someone has used their identity to set up a bank account or take out a mortgage for foreign property. Today, big business has to protect itself against fraud, in particular because organizations have more potential targets using computers and going online, and such businesses have more to lose.
Let us say you represent an insurance company that is supposed to pay out a large sum under an insurance policy it has written, but you feel that something does not add up. Or you are one of the managing directors of an international bank, and your revenues have started leaking due to fraudulent transactions. The question becomes – what do you do next to protect yourself and your company?
The answer to the safety question is OSINT (Open-Source Intelligence) and SOCMINT (Social Media Intelligence) tools and methods. In this article, we explain the process of online investigation that identifies and locates the targeted persons in social media with ease. The SL Pro product integrates into IBM i2 and is a reliable tool for searching all social media services and open-source data to identify and locate a particular individual.
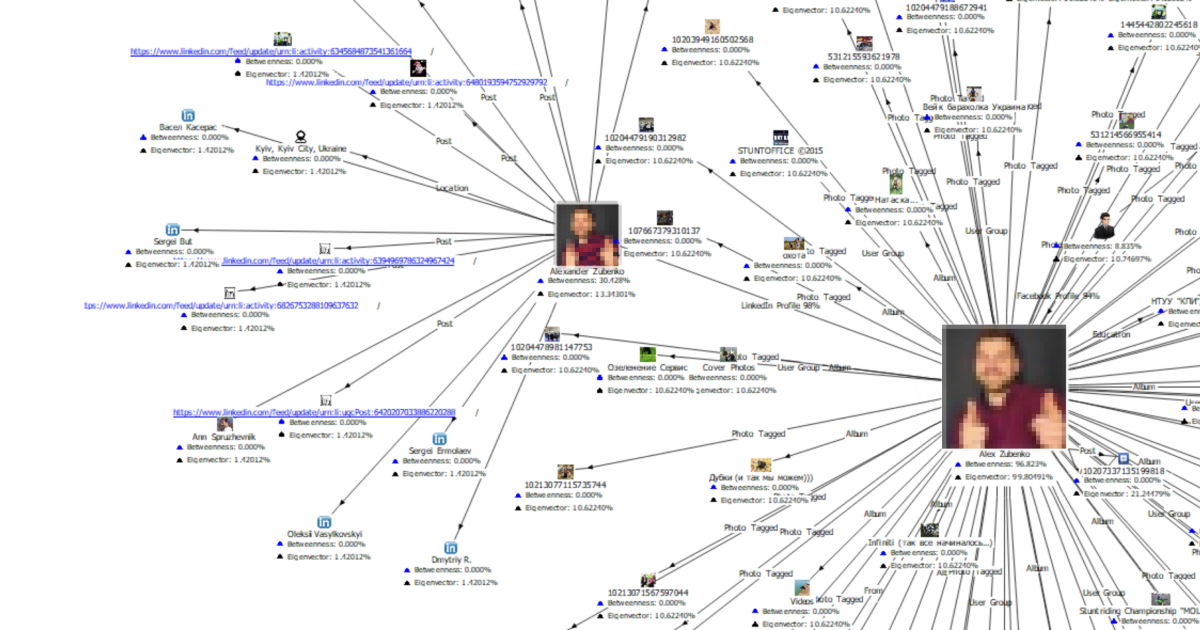
Let us see SL Pro in action. If you have an alias that is of interest, you can use this as a starting point. SL Pro finds an old GitHub account, and through its repositories all interconnected accounts and email addresses are shown. The search with Github details allowed us to delve deeper by giving us the email our target used to register on the platform. This led us to identify additional platforms that he had joined with that email address. In this particular case, a Skype profile with an avatar target’s full name subject and the initial geopositioning was retrieved.
The next milestone utilized one of our most powerful set of search methods: the AI-based facial recognition tool, which provided us with other accounts that shared the same name and picture on avatar. This retrieved a Facebook and LinkedIn accounts that confirmed that the target was based in Kiev. After collecting all of the information listed above, we collate a complete picture of the user’s activity on both platforms. Although we only had an alias as a starting point, the result was evidence of the subject’s social media presence.
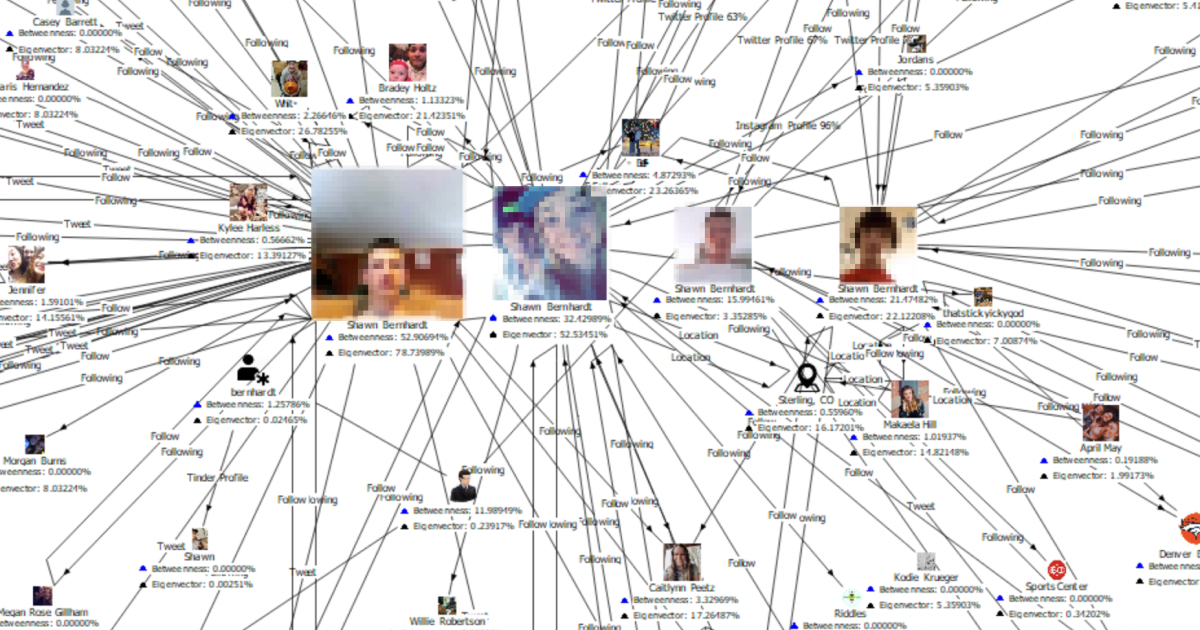
We start with an alias including a surname. SL Pro takes us to a Tinder account that contains eight photos, a graduation location, and an employer name. With the help of facial recognition we can retrieve accounts from Instagram, Facebook, TikTok, and four more Twitter accounts – all belonging to the same person. From Twitter accounts, we pick all tweets, retweets, subscribers and who they are subscribed to, information from password recovery pages, etc. We got posts from TikTok and Facebook activity and the SL ISE (Identity Search Engine) gave us Facebook profiles which in turn provided us with two phone numbers, the initial geopositioning, and an email address.
Since its founding in 2015, Social Links has been honored to be the solution of choice of law enforcement agencies in 55+ countries, as well as a variety of ministries and businesses in various industries. IBM i2 is trusted by law enforcement agencies around the world, from defending national security and defense to fighting fraud and financial crime.
We hope that SL Pro for IBM i2 will open up opportunities for investigators to solve cases and make the world a safer place! As always, we are more than happy to show our solutions to prospective partners. Feel free to reach out to our team via request form below, so we can reach you shortly.