Structuring the Unstructured: Exploring the OSINT Framework

In the vast, chaotic ocean of publicly available information, an investigator without a process is adrift. The sheer volume of data sources can be overwhelming. Even a powerful toolkit is useless without a methodology to guide their application. This is the critical role of an OSINT framework: to provide the blueprint, the structured methodology that transforms the raw, unstructured data of the open-source world into coherent, actionable intelligence.
For the seasoned professional, a framework is not merely a checklist or a list of websites. It is a cognitive model for deconstructing a problem, organizing an investigation, and ensuring that all avenues are explored with rigor and efficiency. This article delves into the concept of the OSINT framework, its practical application, and how modern intelligence platforms are evolving from simple toolkits into fully operationalized investigative environments.
At its most fundamental level, an OSINT framework addresses a core problem: how to systematically navigate the digital world to find, collect, and analyze information relevant to a specific intelligence requirement. It provides the "how" that complements the "what" of an investigation.
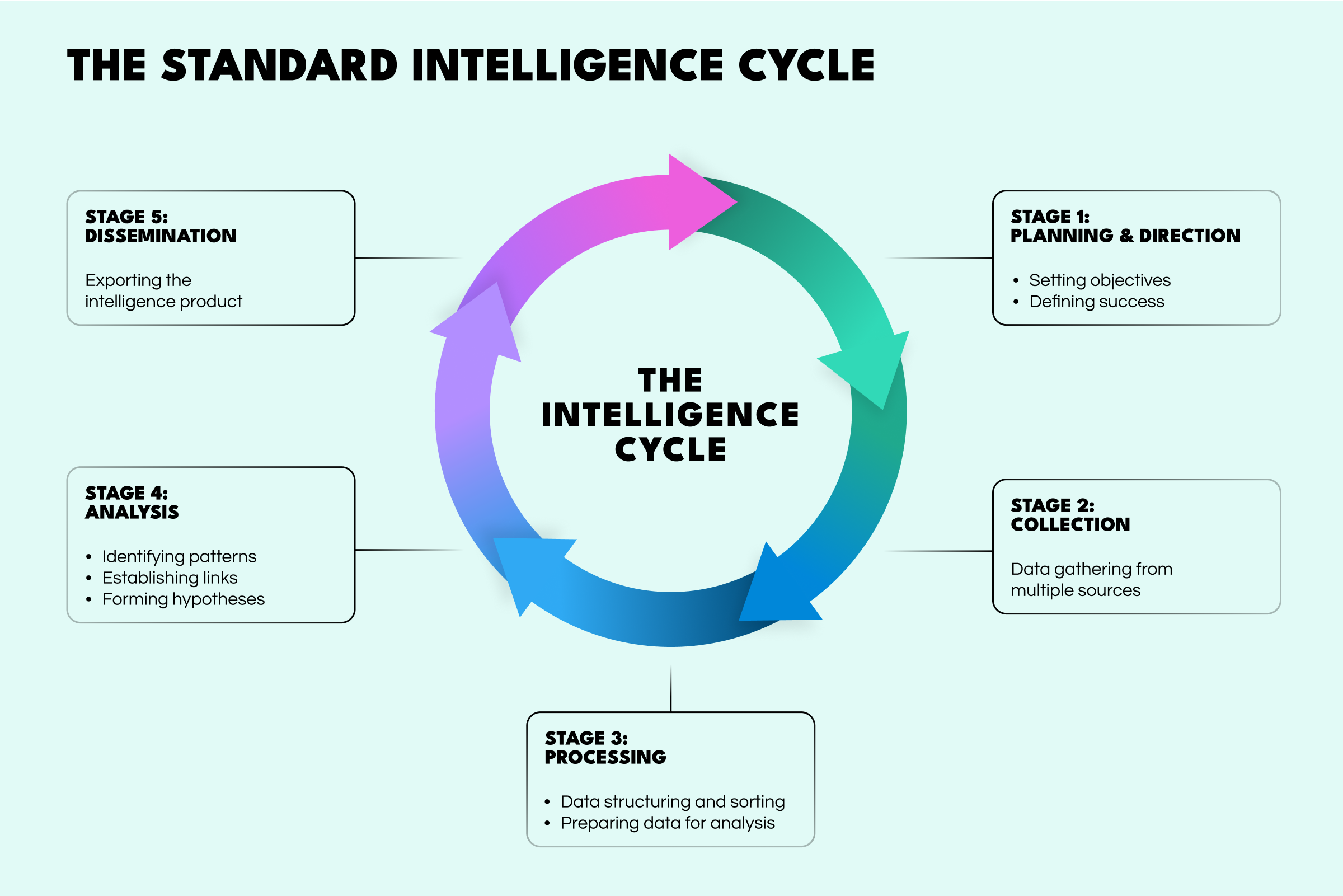
Most effective frameworks, whether formal or informal, are built upon the classic intelligence cycle:
A framework provides the structure for executing this cycle in a repeatable, comprehensive, and defensible manner.
When practitioners discuss the "OSINT Framework," they are often referring to the invaluable resource created by Justin Nordine, found at osintframework.com. This tool is a perfect embodiment of a resource-based framework. It presents a massive, interactive mind map that categorizes hundreds of OSINT tools and resources.
From an initial query point like a username, email address, or domain name, the framework branches out into every conceivable category of investigation: social media, public records, transportation, geolocation, the Dark Web, and more. For an analyst, the resource has immense utility for a range of purposes, including:
Tool Discovery. It serves as a comprehensive, constantly updated directory of the best tools for a specific task.
Methodological Prompting. It acts as a mental checklist, reminding an investigator of potential avenues they might have overlooked. Investigating a person? The framework prompts you to consider not just their social media, but also public records, past data breaches, and even their online forum activity.
Training and Development. For junior analysts, it is an interactive curriculum for learning the landscape of open-source intelligence. The OSINT Framework also becomes more powerful when paired with graph-based methodologies. By moving from static tool listings to visual network intelligence, investigators can uncover hidden relationships between entities at scale. If you're unfamiliar with graph-driven investigation workflows, explore Link Analysis — Lifeblood of the Modern Investigation, which demonstrates how structured mapping turns raw OSINT data into actionable intelligence.
That said, it's crucial to understand what this framework is and what it is not. In traversing the OSINT landscape, a framework is your map, not your vehicle—it shows you where to go, but it does not take you there or analyze what you find. The manual application of this framework can still be a painstaking process of navigating to dozens of different sites, running individual queries, and attempting to collate the results.
Imagine a corporate security team investigating a series of anonymous, targeted threats against a high-level executive. The only starting point is a single, pseudonymous username from a niche forum.
While this manual process is effective, it’s also slow and creates data silos—the analyst is drowning in browser tabs, and the operational tempo is dictated by how fast they can copy and paste.
The primary limitation of a manual framework approach is its lack of integration and automation. The future of OSINT lies in platforms that internalize the logic of a framework and execute it at machine speed.
SL Professional is a prime example of a platform that operationalizes the collection phase of the framework. It acts as a force multiplier within an analysis environment like Maltego. Instead of the analyst manually visiting a dozen sites to search for a username, they can run a single SL Professional "transform". This action automatically queries hundreds of sources—social media, messengers, forums, the Dark Web, and even data breach corpuses—and brings the results directly into the analysis graph.
In our scenario, the analyst would input the username into Maltego and let SL Pro automatically discover the associated X and GitHub accounts, along with any other linked profiles, emails, or crypto wallets. This transforms the framework from a static map into a dynamic, automated collection engine, drastically reducing the time from question to data. And crucially, operationalizing an OSINT framework requires a solid grasp of the discipline itself — from attribution to digital footprinting to multi-source enrichment. For foundational context on how modern OSINT workflows operate and evolve, review What Is Open Source Intelligence (OSINT) in 2025, which explains how structured methodologies elevate raw data into verified, defensible intelligence.
Yet it’s possible to go even further, and SL Crimewall represents the next logical step—it’s a platform that operationalizes the entire intelligence cycle. It is a complete investigative workbench that embodies the full spirit of a framework. To illustrate this, we can revisit the scenario set out above in the context of applying Crimewall to the case:
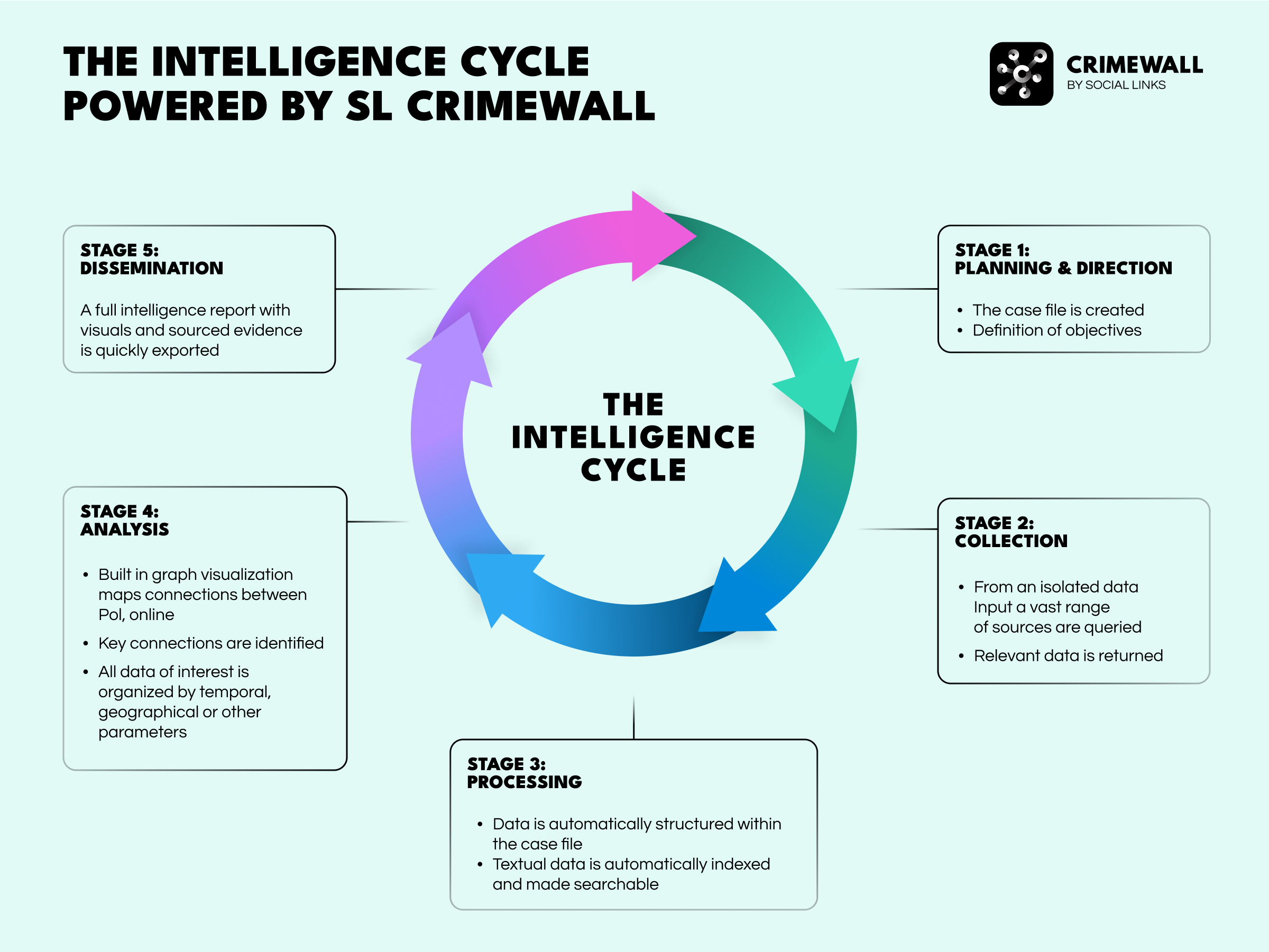
An OSINT framework is, ultimately, a discipline. It is the methodological rigor that separates professional intelligence work from casual online searching. Resource-based tools like osintframework.com are indispensable guides in this discipline, providing the map needed to navigate an ever-expanding digital universe.
However, as the speed and complexity of threats increase, the future belongs to those who can operationalize this discipline most effectively. The true power of a framework is unleashed when its systematic logic is embedded into the core of an investigative platform.
By automating collection, integrating analysis, and streamlining collaboration, advanced solutions like SL Professional and SL Crimewall are transforming the conceptual blueprint of the OSINT framework into a tangible, powerful, and decisive advantage for the modern investigator. They allow the analyst to focus on the most critical task: thinking.