Top-10 OSINT and Cyber Security Stories of 2022


It seems there’s never a dull moment in the world of cyber security and OSINT, and 2022 has been no exception. Throughout the year, we’ve been collecting the most important stories that touch upon the sphere of data security and analysis, and sharing them in our monthly digest.
Now, at the year’s end, we’ve brought together the most discussed articles in one bumper edition. This round-up digest is a great way to catch up on the year’s biggest OSINT events, and is an ideal read for the upcoming holidays. So, let’s dive in!
According to a United Nations report, North Korean hackers targeted crypto firms, exchanges, and other institutions in stealing $400M worth of cryptocurrencies to fund the state arms program. Sanctions monitors connected a "marked acceleration" of missile testing by Pyongyang, with revenue streams derived from cyberattacks, which have been particularly focussed on cryptocurrency assets.

It’s easy to imagine that most darknet marketplaces are lawless and unregulated by definition. However, in recent developments, these platforms have begun adopting dispute resolution procedures to oversee proceedings and penalize users who do not trade fairly. Curiously, it seems like black markets are cultivating a taste for fair play and client-oriented trade approaches.
The primary objective of such arbitration is to de-dramatize open disputes over ‘rip-off merchants’ because it can attract the unwanted attention of the law (e.g., a disappointed customer can anonymously draw the police’s attention to a marketplace as a means of ‘retaliation’). For instance, on the Hydra marketplace, buyers on cybercrime forums can turn to administrators to start a dispute resolution.
Once a formal complaint has been lodged, proceedings unfold like quasi-court hearings with other members of the forums contributing testimony before a final ruling is made. Verdicts may result in temporary or permanent bans. For wary customers, administrators also offer voluntary escrow options, whereby a ‘neutral’ third party holds funds until both payments have been assured and goods received.
According to the US Federal Trade Commission, financial losses through romance-framed social engineering scams hit a record high of $547 million in 2021. No security system or privacy setting can rule out the human element. And where the online world meets the interpersonal, credulity is the name of the game. Dating apps and social networks have become vast arenas where users can be defrauded by the irresistible lure of a potential sweetheart.
Romance scammers rely on social engineering to trick their targets into sharing money or sensitive information. In nearly 30% of reported cases, initial contact is made through a direct message on Tinder, Facebook or Instagram, with the tricksters then elaborating communication over months to lull their targets. Eventually, a message is sent about some crisis situation such as a sick relative or robbery, accompanied by – of course – an urgent plea for financial help.
There are also alternative scenarios where victims are asked to transfer money or deliver some goods, and unwittingly become smugglers or money launderers. But scammers don’t always use the ‘crisis’ angle. Sometimes people are lured into making investments into crypto Ponzi schemes – a type of fraud where a non-existent enterprise keeps the illusion alive by bouncing money and returns between investors. Such approaches made a staggering $139M for fraudsters in 2021 alone.

The servers of the Hydra marketplace – a prominent drug-selling marketplace on the dark web – have been shut down by the German police. The government also confiscated 543 bitcoins of profit from the platform – a sum amounting to $25 mln.
At the time of the seizure, Hydra managed 19,000 drug sellers supplying 17 million customers from all over the world. The Central Office for Combating Cybercrime (ZIT) and Germany's Federal Criminal Police Office (BKA) report that Hydra had a turnover of $1.35 billion in 2020, making them the largest drug marketplace in the world.

The UK government has implemented a secondary school program that includes the teaching of open-source intelligence. The course is called Cyber Explorers, and aims to educate some 30 thousand secondary school pupils between the ages of 11 and 14 in a range of cybersecurity skills, including open-source intelligence (OSINT), digital forensics, and social engineering.
The program is being carried out in an online format with pupils learning the basics of cybersecurity, recognizing potential career paths in the digital sphere, such as social media marketing and analytics. The initiative is a part of a national cyber strategy geared towards developing cybersecurity competence and skill sets among UK citizens in the cybersecurity sphere to the UK citizens, and was launched on 23 February, 2022.
The City of London Police has reported a surge in street robberies where muggers combine threats or phone theft with crypto know-how to steal large sums of money from their victims. The incidents vary in detail but essentially share a basic premise: people are forced to hand over their phone – or have it stolen – then, by using forced facial recognition or shoulder-surfed login details, the muggers transfer money to their own accounts.

Having been under severe sanctions for many years, the North Korean government has been hard-pushed to up the country’s inflow of dollars and finance various state programs. In such a fix, hacking has become a common offshoot by which North Korea can pursue its own interests. While the West is perfectly aware of this, it doesn’t seem to have been wise to all of the tactics being employed.
One ploy which seemed to have slipped the net involves North Korean agents simply posing as casual IT professionals from China, South Korea, Japan and even Russia seeking work, thereby gaining access to sensitive company data. In response, the FBI recently issued instructions for businesses on how to detect scam workers from the DPRK applying for freelance contracts.
According to the FBI, North Koreans earn over $3 million each year for their government via this scheme, the proceeds of which could be used to finance the national weapons development program. And such infiltration is not limited to theft, but can also include sabotage such as the deployment of malware into corporate systems. However, detecting such agents is no mean feat and HR departments need all the advice they can get.
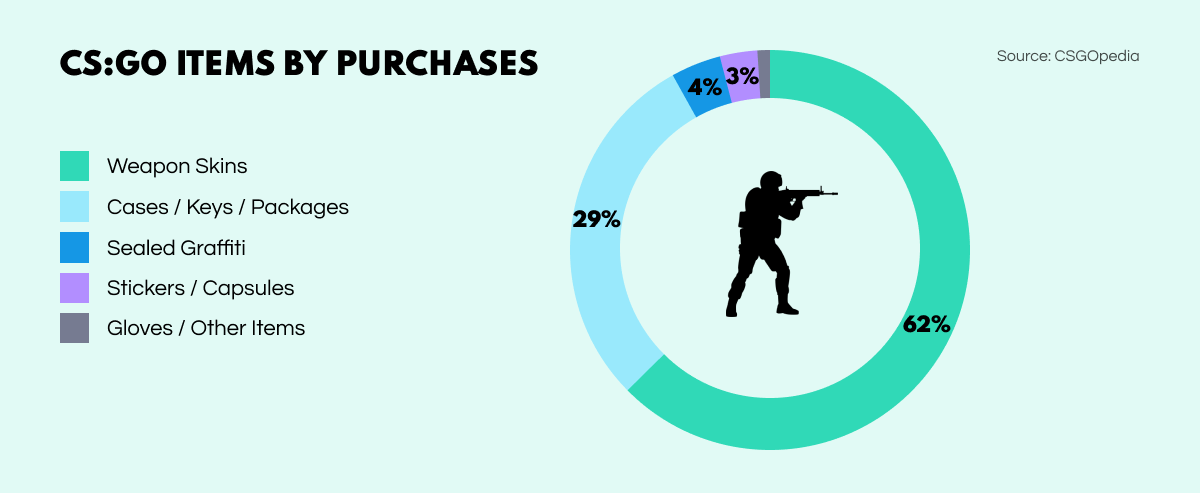
While people are still getting used to news about stolen NFTs and emerging niches of crypto investigation, cybercriminals are exploring an even more bizarre way of getting rich quick – stealing in-game modifications. CS.MONEY, the largest platform for trading Counter-Strike: Global Offensive skins has recently been taken offline after hackers looted 20,000 items amounting to an astonishing $6 million!
Most popular online games have developed sophisticated economies, complete with internal currencies as well as virtual arms, avatar and equipment trade, and much more. For highly popular games such as CS:GO, selling platforms represent huge marketplaces, subject to intense supply and demand among gaming enthusiasts, who are willing to fork out significant sums for these in-game commodities.
However, this sphere of digital trade has a murky underbelly, since these gaming commodities can be used as digital tokens for making illicit transactions in a manner that law enforcement bodies are hard-pushed to trace effectively. Such trade can include sizable drug or weapon sales, and even bribery payments can be made in-game assets that go unsupervised by the regulators.
Helped along by the Covid-19 pandemic, platforms such as YouTube are now awash with videos of talking heads shot from webcams. From gaming tutorials and presentations to interviews and discussion groups, such content is proliferating at a rate of knots. However, content creators may well be totally unaware that, to the canny analyst, these videos can yield more data about the on-screen subjects than they would care to broadcast.
It seems that people tend to overlook the capacity for betrayal held by reflective surfaces. Mirrors lurking in the background, or attire such as spectacles and watches can provide windows into the computer screen facing the presenter. With the help of image processing tools and techniques, OSINT analysts can view texts and images from the off-screen screen to derive all kinds of useful insights and inferences.
Even though OSINT specialists have been using manual reflected image inspection for a long time, it is still impossible to process large amounts of video material this way, due to human factors. However, according to a recent study, an algorithm has now been developed, which should be able to take care of most of the legwork and greatly accelerate the process through automation.

One of the craziest darknet promotion campaigns has recently been conducted by the marketplace BidenCash, which has allowed users to download the details of 1,221,551 stolen credit cards for free. The marketplace first opened in June 2022 with a similar promo campaign, featuring several thousand stolen credit cards. Such details are mainly used by cybercriminals to carry out financial fraud.
Darknet data dumps such as this usually turn out to be scams: recycled data repackaged as fresh, or simply hordes of fake information. However, analysts have confirmed that a proportion of the data – around 30% – is indeed authentic, and that much of it relates to real card holders at various Italian banks. Considering the size of the dump, this equates to approximately 350,000 valid cards.
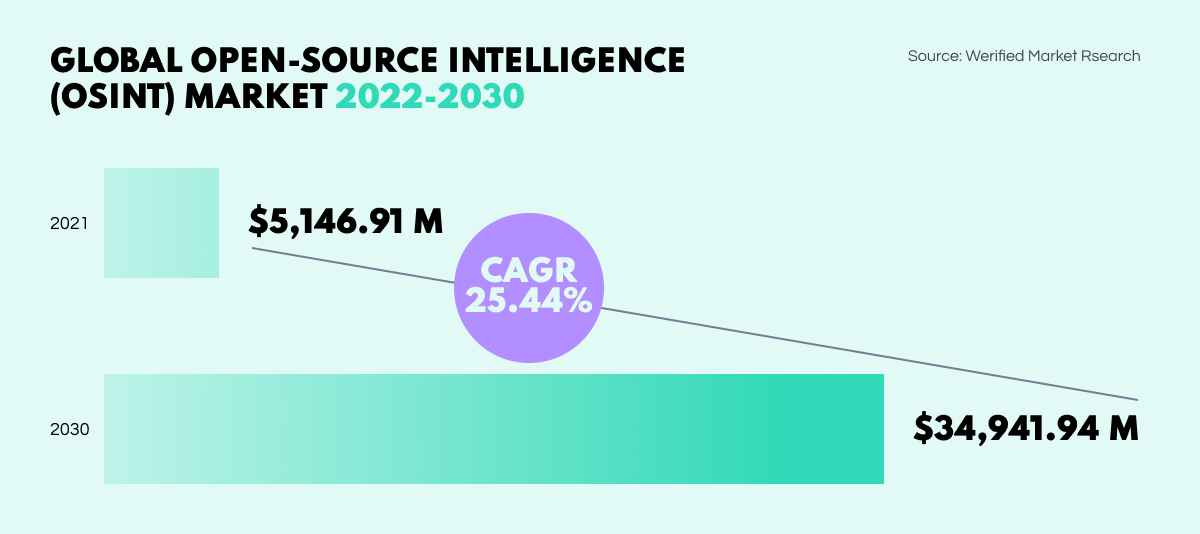
According to a study by the Verified Market Research agency, the global OSINT market growth has exceeded earlier expectations, and is now set to reach just under $35B by the year 2030. 2023 promises to bring new records for the OSINT industry.
And that concludes our yearly round-up. Happy New Year from everyone on the Social Links team!