The Wide-Ranging Uses of OSINT in Military Intelligence


As its name suggests, open-source intelligence has its roots in interstate reconnaissance. Emerging during WWII, OSINT techniques were initially adopted for military intelligence by the US Office of Strategic Services (OSS) – now the CIA – in an attempt to discern enemy strategies and objectives through the detailed study of newspapers, magazines, radio broadcasts, photos and other media.
Of course the world has undergone significant developments since then. The flood of open data accompanying the colossal rise of social media has resulted in OSINT taking on a broader meaning. While open-source intelligence techniques are now indispensable across a range of sectors from cyber and corporate security to law enforcement, its reconnaissance uses are still very much in play, and more pervasive than ever.
Intelligence officers have stated that the vast majority of valuable intelligence comes from open sources, suggesting that the role of open-source intelligence in the field is truly significant. So, in this article we’ll discuss why OSINT in military intelligence is becoming so important and how it is being used.
Whether or not a nation is engaged in direct conflict, military intelligence is perennially being carried out. In times of armed engagement, its uses are explicit – to gain a clear and up-to-date picture of what is unfolding in the troubled territories for informing strategy and deployment. Taking place in waters and the air as well as on the ground, these objectives demand costly, sophisticated technologies and incur a high risk of recon squads being drawn into armed engagement.
However, military intelligence is not solely gathered in warzones. In the aftermath of natural disasters such as hurricanes, typhoons, wildfires, etc., on-the-ground reconnaissance is often of crucial importance for deploying effective civilian rescue operations or aid relief. Furthermore, policies of national security frequently depend on military intelligence taken from the borders between competing or hostile states.
OSINT is now coming into its own, and the prominent driver behind this is unmistakable. The seismic rise of social media and its pervasive presence throughout societies around the globe has led to the production of an unprecedented amount of open data. The world of blog posts, Instagram stories, Tweets, Facebook comments, and Telegram channels is clearly not one where privacy reigns. In playing out a larger proportion of our lives online, we are broadcasting data which analysts can use to profile individuals and groups with unnerving accuracy.
And abstention from online culture can even be an indicator. US intelligence authorities are well aware that the conspicuous absence of a Facebook account could lead to the exposure of an intelligence agent. It has also been claimed that social media paved the way for the Arab Spring. At that time, only a small number of Egyptian citizens were active online. However, of those who were, 84% were engaged in political discourse during the uprising. A decade later on, we are dealing with a vastly expanded range of data sources and seemingly endless amounts of publicly accessible digital information.
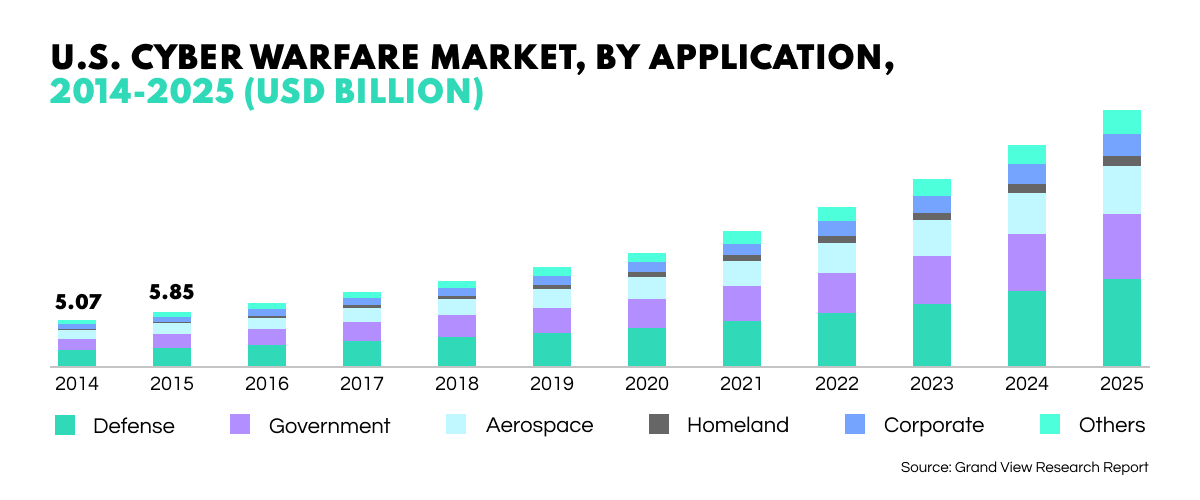
With societies migrating to the online realm, it is perhaps unsurprising that interstate hostilities also play out in a digital format. The term ‘cyber warfare’ has a very real meaning and includes various concepts including cyber espionage between states and companies, as well as cyber sabotage on adversary infrastructures. Governments and companies do not underestimate the importance of these technologies and invest heavily in them every year, with budgets rising steeply.
While traditional intelligence disciplines remain valuable, OSINT has been proven to drastically enhance conventional methods by adding a scope and breadth which would otherwise be impossible or prohibitively impractical. Also, as an intelligence branch in its own right, OSINT is a force to be reckoned with, with analysts understanding its crucial importance in their work and overall military capabilities. So what are these benefits?
The wide-ranging data and analysis approaches comprising OSINT mean that threats which would remain ill-defined through standard intelligence methods can gain a distinct shape. By mapping behavioral and decision-making patterns, analysts can assess information through the broader lenses of culture and socio-economics. This can often be far more effective in defining modern threats of a more nebulous and asymmetrical nature such as terrorism, radicalism, and gray zone activities such as the spread of misinformation.
By providing a context to the actions and decisions discovered via classified materials, military OSINT tools can often be hugely effective in bolstering intelligence derived from other disciplines such as HUMINT (Human Intelligence) and SIGINT (Signals Intelligence). One drawback of classified intelligence is that, due to the constraints of covert intelligence, data is often only collected around a single, narrow topic of interest.
Of course, intelligence units need not exclusively rely on open-source information, but analysts can gain a bigger, more detailed picture through combining intelligence approaches. This, in turn, helps to determine underlying patterns and motives. By forming bridges between fragmented intelligence, OSINT tools can help intelligence officers to understand the means by which adversarial actions are being carried out, as well as plans and possible future targets.
The classified nature of traditional intelligence means that it cannot be subjected to so much objective scrutiny – their contents reside behind closed doors and can be faulty. Errors can stem from simple human error or oversights made by the operatives, or it could be the result of counterintelligence laying decoys to mislead the opposition.
By contrast, the open qualities of OSINT enable thoroughgoing verification. Isolated data items can be cross-checked through parallel analyses where independent lines of enquiry line up. In a more global sense, intelligence can be supported by amassing weak indicators – fragmentary information of a cumulative force – around a particular inference.
Intelligence tends to be delivered in dribs and drabs. Even when intelligence is amassed over time, reports often deliver a static snapshot of events, which can soon be outdated and erroneous as a result. Conversely, OSINT allows for a continually evolving dynamic overview which is updated in real time and almost always up-to-date. By studying open data in a temporal framework, analysts can understand how processes and sentiments change over time, and provide a military reconnaissance which is always up to speed.
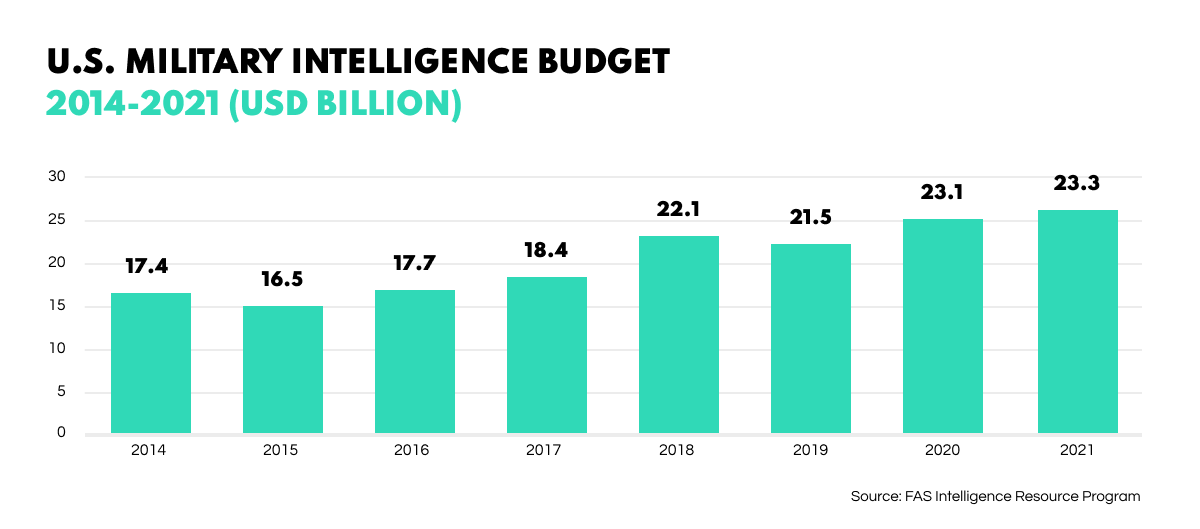
Military intelligence is anything but cheap. The employment of state-of-the-art technologies comes at a cost that has made effective global intelligence possible for only countries with the largest military budgets. For instance, in 2021 the US spent over $23 billion on military intelligence – a figure which has been part of a generally rising trend from year to year.
OSINT, on the other hand, is affordable. By investing in systems for open data analysis, countries can gain reliable and penetrating information at a fraction of the cost of closed forms of intelligence. In getting more bang for their buck, lower tier intelligence services such as North Korea and Iran have been able to develop into more powerful entities.
Intelligence analysts are prone to the so-called ‘expertise bias’. This is a paradoxical phenomenon where a high level of proficiency in a given area can lead to more significant oversights, especially in connection with paradigmatic shifts or broad changes in the grander scheme of things. In other words, by being too set in their ways, experts can stubbornly cling to outmoded practices, which can be dramatically counterproductive.
Using AI algorithms, modern OSINT solutions can extract, analyze and order masses of raw data to deliver a holistic, contextualized picture of events. The dynamic power of such intelligence helps to mitigate the expertise bias – analysts with access to a greater context are less likely to have their blinkers on.
In practical terms, OSINT tools and techniques are central to a range of military use cases and scenarios.
Operational Security (OPSEC) is a branch of intelligence dealing with the assessment of accessible data to determine how strategically valuable this may be to an enemy and take the necessary measures to mitigate vulnerabilities. The digital presence of military personnel is clearly sensitive information of value to an adversary. Geodata, photographs and videos can be subjected to reverse engineering and public discussion, and have serious sway on public perception and even the operational outcome of a conflict.
While military specialists are continually working to enhance OPSEC in the sphere of communications security, social media remains the weak link in security operations. Modern OSINT systems allow OPSEC specialists to monitor the digital footprint of their military personnel for the detection and removal of potentially sensitive information and close up sources which appear to be susceptible to giving away such data.
During ground operations, it is extremely important for commanders and units to understand the sentiment dynamics of a given area. The residents and authorities of a particular rural or urban location may be hostile or friendly to the deployed forces. The monitoring of local population mood can help law enforcement and military organizations prevent upheavals and inform the commandment about possible risks in a timely manner.
This is work that open-source intelligence excels at. OSINT tools can read the meaning and intent of online activities, whether they are comments on Facebook or retweets, and establish the overall attitude of a particular population. Such cumulative pictures can be absolutely essential for effective decision-making.
Today, terrorist and extremist groups largely use decentralized organizational systems in order to stay under the radar of government defense systems. Most of such groups make extensive use of the internet for recruitment, training and financing, the last of which depends heavily on cryptocurrencies. In this climate we are seeing a wider use of OSINT in state defense.
Advanced OSINT tools can help analysts trace crypto routes, make connections between the Dark and Surface Web, and delineate entire network structures. These can be further analyzed at a compositional level by elaborating digital footprints for each group member and affiliate. Such analyses can not only identify suspect networks and organizations but also anticipate how and when they might act.
Natural disasters have a chaotic dynamic all of their own with each incident being totally unique. As a result, it’s difficult to formulate response protocols which are reliably effective across the board. Inaccurate or out-dated information can lead to ineffective responses that can put people at serious risk or even cost lives.
The earliest signs and reports of natural disasters appear and evolve promptly and quickly online, meaning social media is often a more up-to-date resource than the in-house detection systems of authorities. OSINT tools can monitor events in real time keeping relevant departments informed on breaking information and specific geolocations.
Psychological Operations (PSYOPS) are campaigns of information dissemination aimed at influencing an audience’s opinion, reasoning, and emotions to control the actions of individuals, groups, and even governments. Fake news and misinformation can be very disruptive and significantly affect policies and election outcomes.
OSINT technologies with AI-powered detection functions offer highly efficient ways to counteract the dissemination of misinformation. Using bespoke algorithms, such tools can sweep through oceans of open data and flag up a multitude of false information and their sources. And this can be carried out on a low budget saving valuable time and human resources.
In our contemporary digital world, military intelligence which ignores OSINT tools and techniques will find it increasingly difficult to deal with modern threats, which are difficult to define and continually evolving. By harnessing the huge possibilities of open data, militaries can verify and contextualize traditional intelligence, understand the global picture in detail, and gain results which would simply be unattainable through conventional disciplines such as HUMINT and SIGINT.