August’s OSINT News: U.N. Peacekeepers Hit by Disinformation, Non-State Actors Rule the Cyber Landscape, and Investment Scams Sweep across Europe


The digital sphere is evolving dramatically from day to day, to the extent that every month we can see historic shifts that are liable to affect us all as we march towards greater integration with the online realm. In this month’s news round-up we discuss how disinformation is disrupting the peacekeeping efforts of the U.N., the complex mutations and variations that now comprise the world of cybercrime, and a recent flood of investment scams that have been causing a significant fuss in Europe.
The U.N. Security Council has made a call for the implementation of drastic measures to safeguard their twelve global peacekeeping missions against disinformation and misinformation campaigns spreading throughout social media.
In a recent statement, the organization emphasized the need to “improve the culture of strategic communications across civilian, military and police components,” in order to protect both the civilians and 90,000 peacekeepers connected with the operations. Addressing the council, U.N. Secretary-General Antonio Guterres stated that modern criminals, guerrillas, and terrorists are not only using weapons to undermine regional stability, but also misinformation, disinformation and hate speech tactics.
One example of how corrosive disinformation can easily spread occurred recently in Mali, where a fabricated letter claiming that U.N. peacekeepers were in league with local armed groups went viral on WhatsApp before feeding into the national media. This fomented a widespread hostile sentiment against the peacekeepers, making their work more problematic.
The emerging picture is that modern peacekeeping missions are in a dire need for tools that will help them to automatically flag up misinformation and disinformation at an early stage to prevent them spreading further.
We tend to think of disinformation in terms of spin - a media phenomenon that can sway public opinion and affect politics, but not dissolve law and order to any meaningful extent. But in the wrong circumstances, disinformation can spark civil unrest and even cost lives. It is certainly a time for governmental and intergovernmental organizations to take the issue seriously and implement the necessary measures to keep social threats to a minimum.
Rooting out the source of misinformation is often complicated and time-consuming, however some of the more sophisticated OSINT systems are able to automatically identify the origin soon after dissemination. This enables authorities and organizations to monitor and control the quality of information in circulation. Whatsmore, OSINT tools can conduct continual sentiment analysis to gauge the social impact of the information being consumed.
News items abound about cyberattacks being carried out by groups such as hacking enthusiasts, small extortion organizations or national cyber command. However, a recent study from the Center for Cyber Security and International Relations Studies (CCSIRS) suggests that the landscape of cyber actors operating outside of state control is more diverse than we are inclined to believe.
Here is a shortlist of some of the most prominent forms of non-state actors currently in action:
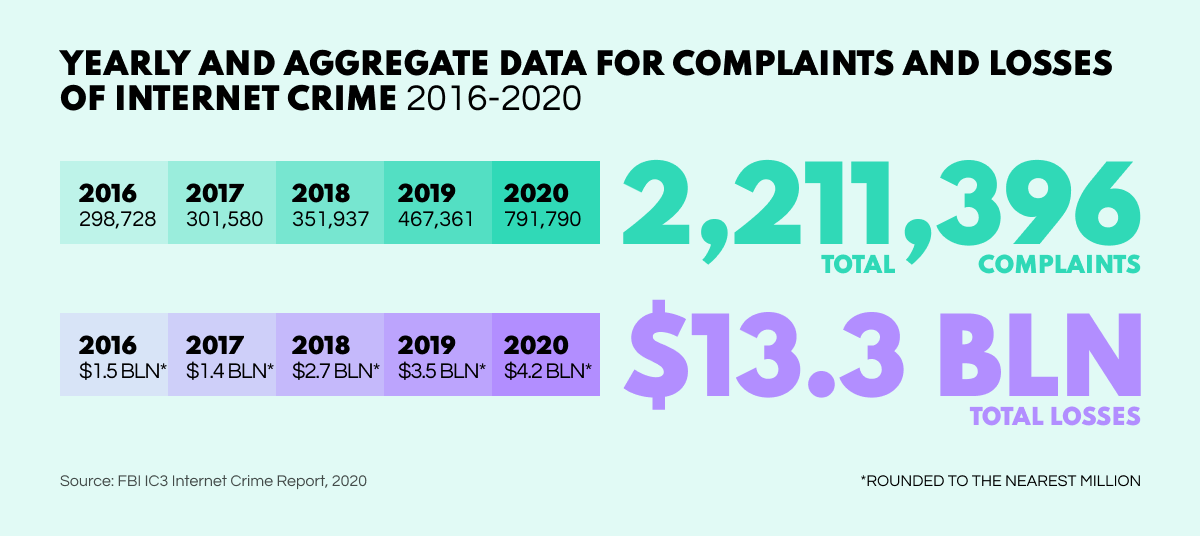
According to the FBI, if cybercrime represented an economy, it would rank third largest in the world following the US and China, with a loss cost of nearly $4.2 billion in 2020 and a projected $10.5 trillion in 2025. Little wonder then that commercial cybercrime organizations have now appeared on the scene just as they would in any other booming sphere. Cybercrime syndicates have something new to commerce: cybercrime-as-a-service (CaaS). At a time when the datasphere has no political boundaries, this pernicious new commodity has grossly fueled cyberattack proliferation all over the world.
In the past, hacktivists mostly acted as lone wolves, meaning that the threat they posed was relatively minimal. Today, however, they have become more interconnected: organized semblances which retain a decentralized structure that frequently eludes the efforts of the law. Unlike cyber syndicates, they act out of patriotic or ideological motivations, which can be harder to distinguish from state-affiliated operatives.
As the name suggests, these are professional hackers that carry out operations on a paid basis. They can act alone or as a part of organized groups which resemble private military companies in the IT realm. Such mercenaries can conduct both reconnaissance and offensive operations but are not tied to any particular state or syndicate.
These are more ‘traditional’ threat groups that are state-sponsored to conduct sabotage, theft, or espionage against adversary nations. For example, many North Korean hacker groups that regularly appear in news headlines are suspected of having ties with the state.
Cybersecurity professionals have their work cut out. Not only do they have to continually combat incoming threats but also spot malicious actors at the reconnaissance stage. OSINT tools enable blue teams to effectively identify hackers and suppress future attacks, but security specialists need to be aware of the multifarious forms modern threats can take in coming from such a diverse landscape.
Researchers from cyber security developers Group-IB have unearthed a colossal network of financial scams across Europe. Encompassing 11,000 fake sites, the scheme tricks people into making ‘investments’ that appear to be bringing big returns.
Lured in by fake celebrity endorsements, the unwitting would-be investor is tricked into making a light ‘entry-level’ deposit of €250. Pretty soon, the new ‘investment portfolio’ boasts steady growth on a fake investment dashboard showing quasi daily gains. After this, ‘account managers’ get in touch and, using social engineering techniques, urge the clients to create an account and invest even more. The bubble finally bursts when the victims eventually attempt to cash in their earnings, only to realize there is no such option.
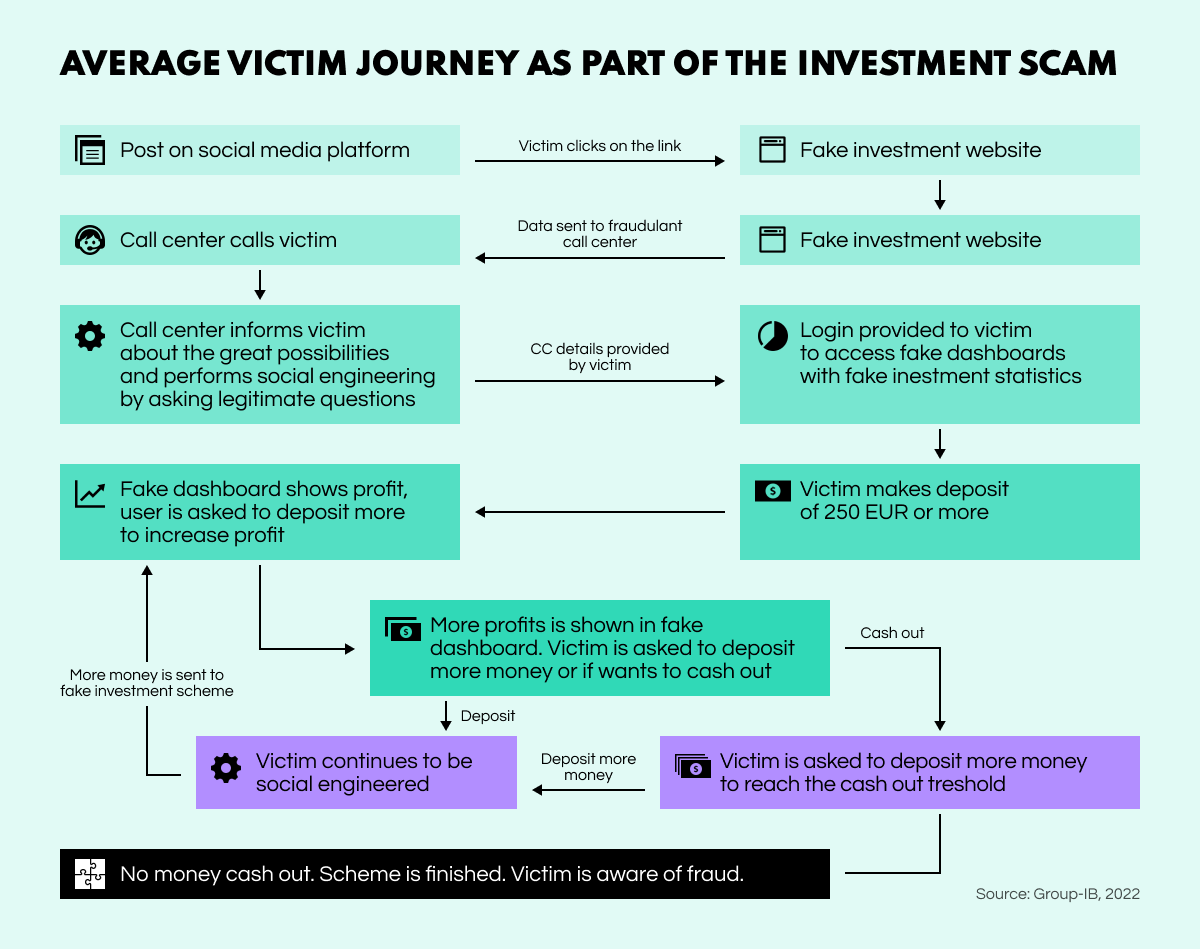
Such large-scale fraud operations take a significant financial and social toll, which will eventually lead to a crying need for devoted policing or costly private solutions to combat this escalating issue. OSINT systems can help uncover such networks with their complete group structure, and identify the criminal actors behind them.
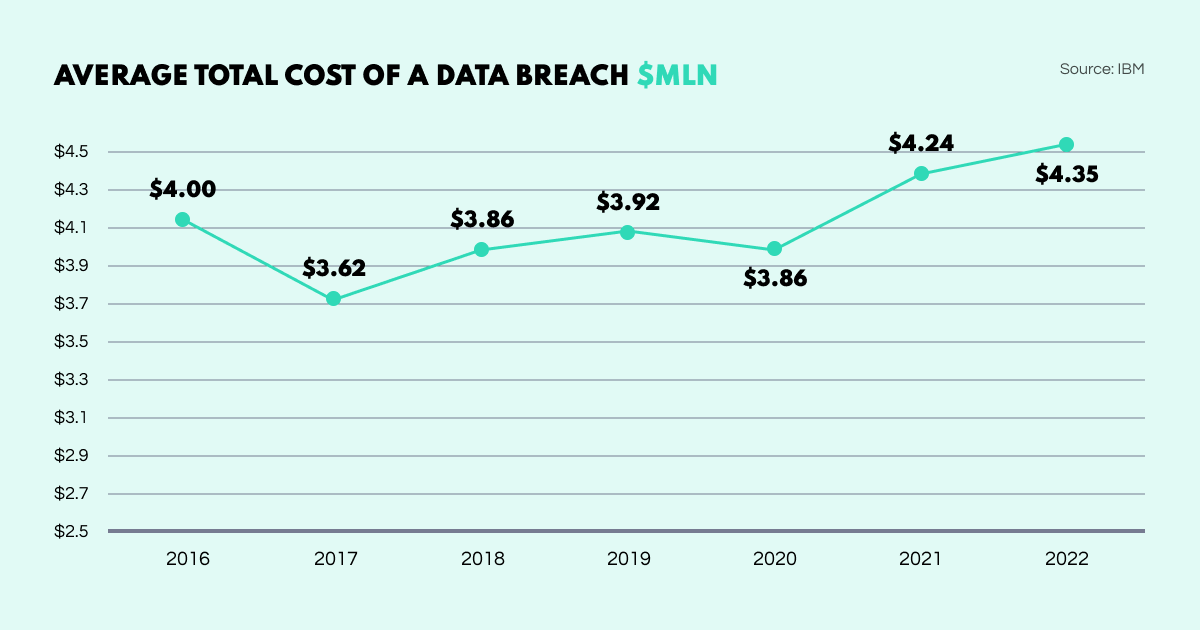
Cybersecurity concerns are on the rise: 2022 saw another all-time record data breaches. The sectors hit hardest were healthcare at $10.10 mln, finance at $5.97 mln, pharma at $5.01 mln, and tech at $4.97 mln. Meanwhile, the public sector was the least affected at $2.07 mln.
Social Links latest blog article covers all the most fundamental questions about OSINT from who uses it and why, as well as the techniques involved. Essential reading for anyone trying to get to grips with the topic, and what the OSINT landscape looks like in 2022.
Researchers have found a malicious website that can effectively hack into a user identity via social media and website logs. The hack analyzes features of someone’s browser activity to determine whether they are logged into service accounts including YouTube, Facebook, Dropbox, and Twitter.
A fraud epidemic in Egypt has exposed more than half the population to phishing scams through using online banking or digital wallets. A survey found that 54% of users were directed to fake sites, and 57% experienced social engineering fraud attempts through text messages or phone calls.
Dark Web business still booms for card detail vendors who have learned to steal the necessary data despite embedded security chips that encrypt transactions and are more difficult to clone.
Instagram has become a hotbed for financial scams, especially crypto pyramids. WIRED introduces their guide to staying secure on the social media platform by being wary of all the competitions, fake sellers, and crypto scams that you can easily encounter.
And that draws our August digest to a close. Stay tuned to our blog for devoted articles on a whole variety of OSINT topics.