Beyond the Blockchain: OSINT in Crypto Investigations


Cryptocurrency investigations have become a core function for law enforcement, compliance teams, and financial intelligence units. While blockchain networks offer unprecedented transparency, they also enable fraud, money laundering, and sanctions evasion at scale. As the crypto ecosystem expands across platforms and jurisdictions, the challenge has shifted. It is no longer about achieving visibility, but about establishing attribution that connects activity to real actors.
In our first article of 2026, we examine the role of open-source intelligence in modern crypto investigations. We look at why blockchain analysis alone is insufficient and how off-chain data connects pseudonymous wallets to infrastructure, coordination, and human behavior.
Most crypto investigations begin with blockchain analysis. Analysts map wallet interactions and trace fund flows across addresses and services. This establishes a financial footprint and highlights suspicious movement.
At the same time, blockchain analysis remains largely descriptive. Public ledgers make transactions observable, not self-explanatory. A single actor can control hundreds of wallets, while mixers, cross-chain bridges, and decentralized exchanges are designed to reduce traceability.
This creates an investigative gap. Blockchain data shows what happened, but it rarely reveals who organized the activity or how it was coordinated. Closing this gap requires visibility beyond the ledger.
Every crypto crime depends on activity outside the blockchain. Websites are used to attract victims, social platforms amplify campaigns, messaging channels coordinate participants, and infrastructure supports ongoing operations. These elements are often publicly observable.
OSINT enables systematic collection and correlation of this off-chain activity. When combined with blockchain analysis, it allows investigations to shift from transaction mapping to actor identification and operational reconstruction.
This becomes clearer when examining how different categories of crypto crime expose different public signals.
Different forms of crypto crime rely on different operational models, but all depend on off-chain behavior that can be observed and linked. The table below summarizes what OSINT enables across common crypto crime categories.
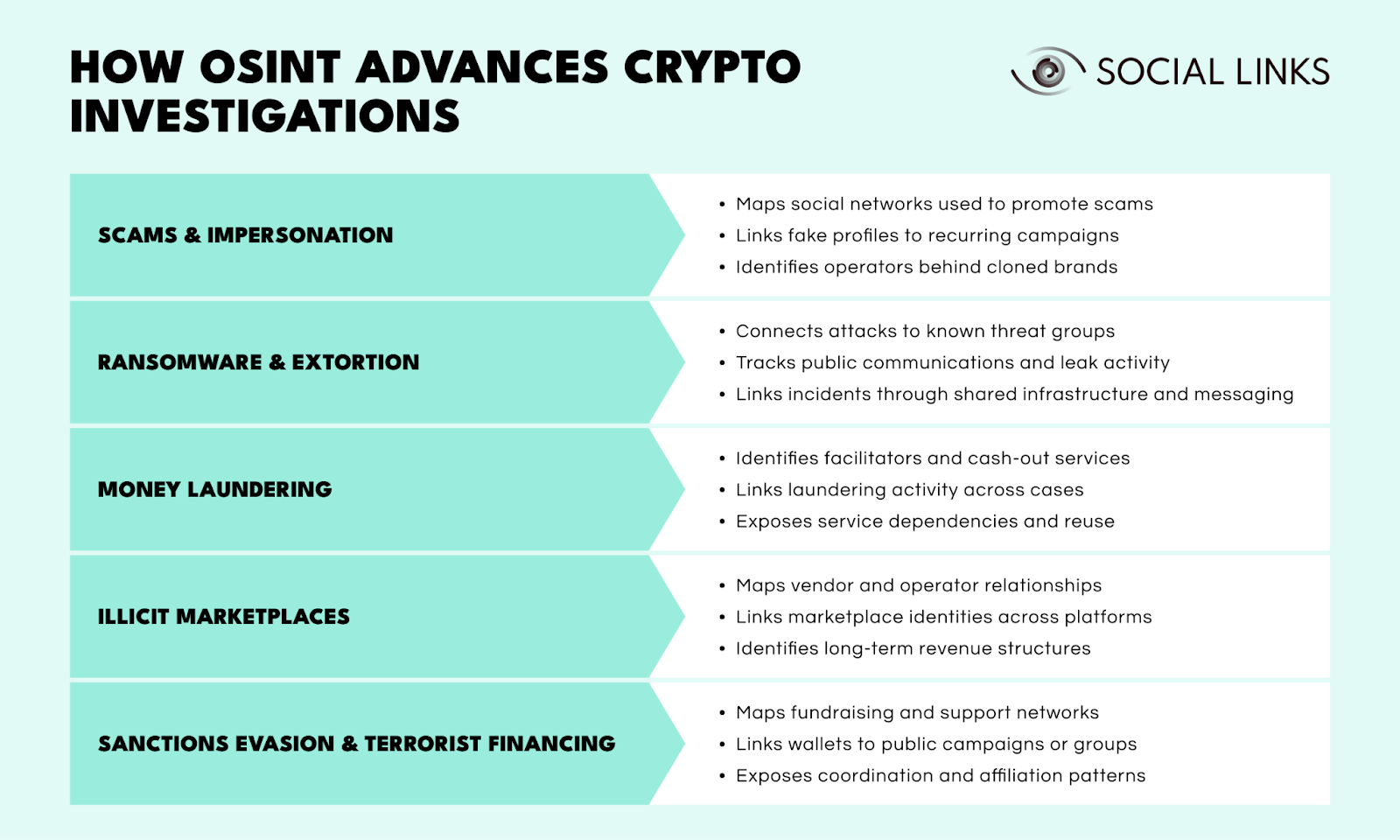
These schemes involve deceiving victims into sending cryptocurrency by posing as legitimate companies, individuals, or investment platforms. They rely on visibility and trust, using public channels to distribute links and redirect victims toward controlled sites or wallets.
OSINT makes it possible to map promotion networks, link repeated identity reuse across campaigns, and identify operators behind cloned brands. Over time, patterns emerge that reveal coordination and scale beyond individual incidents.
These operations involve encrypting or stealing data and demanding cryptocurrency payments to restore access or prevent disclosure. Payment pressure is created through public breach claims, leak sites, and controlled negotiation channels.
OSINT connects incidents to known groups by tracking public claims, recurring communication behavior, and operational branding. This allows campaigns to be linked even when wallet infrastructure changes.
These activities aim to conceal the origin of illicit cryptocurrency and convert it into usable assets through exchanges, brokers, or intermediary services. Laundering depends on repeated interaction with services that advertise liquidity, speed, or anonymity.
OSINT identifies service operators, links repeated laundering behavior across cases, and exposes dependencies that persist despite wallet rotation.
These platforms sell illegal goods or services in exchange for cryptocurrency and rely on reputation systems to maintain buyer trust. Vendors and operators maintain persistent identities and off-platform communication to sustain operations.
OSINT maps these identities, links activity across platforms, and reconstructs operational structures that remain stable even as marketplaces migrate or disappear.
These activities use cryptocurrency to bypass financial restrictions or raise funds for prohibited organizations and causes. Fundraising campaigns, ideological messaging, and public promotion often operate openly to mobilize support.
OSINT maps fundraising networks, links wallets to public campaigns, and exposes coordination structures behind organizational activity.
Across all categories, blockchain analysis describes transaction movement. OSINT enables attribution, campaign linkage, and actor identification.
Transaction tracing capabilities are becoming increasingly standardized. The ability to follow funds is no longer rare. What remains difficult is linking financial activity to responsible actors in a defensible way.
As crypto activity continues to fragment across platforms and jurisdictions, investigations that remain transaction-centric will struggle to produce enforceable outcomes. Hybrid approaches that integrate blockchain analysis with open-source intelligence provide the structure needed to move from visibility to accountability.
Crypto investigations rarely fail because information is missing. They stall because transaction data alone cannot explain responsibility, coordination, or intent.
Blockchain analysis establishes how assets move. OSINT establishes who operates, promotes, and benefits from that movement. Together, they enable investigations to progress from tracing funds toward identifying actors and producing intelligence that supports real-world enforcement and disruption.
Blockchain analysis shows fund movement but not ownership or coordination. OSINT links wallets to off-chain behavior, enabling attribution.
Scams, ransomware, money laundering, illicit marketplaces, and sanctions evasion all rely on public-facing activity. OSINT exposes these operational signals.
Actors rotate wallets and infrastructure to avoid attribution. Without off-chain visibility, tracing remains descriptive.
OSINT correlates domains, profiles, messaging activity, and campaign patterns with blockchain data. Reuse and coordination reveal operational identities.
Combining blockchain analysis with OSINT connects transactions to real actors. This improves enforcement outcomes and investigative confidence.
Want to see how OSINT strengthens crypto investigations in practice? Book a personalized demo with one of our specialists and discover how SL Crimewall helps teams connect blockchain activity to real-world actors, map operational networks, and accelerate attribution within a single, compliant intelligence platform.