Elevating Background Checks with OSINT


In today’s climate, background checks have become a staple of verification, and open-source intelligence has risen to the fore as an indispensable element of this widespread practice. Anyone who’s applied for a job may be aware of basic screening checks. But, in fact, the world of background checks goes way beyond this.
The depth of the background checks may range from the superficial to the profound. Although it's sometimes possible to find and verify data in registries, the truth is that risks often run far deeper than public records. In many cases, crucial information that will lead to a breakthrough is generally different from the sort that has been stored away in public access for years. This type of information can only really surface through in-depth, enhanced checks.
In this article, we’ll explore the full anatomy of background checks, including their different types and purposes. We'll also discuss various difficulties that can prevent checks from succeeding and how OSINT tools can address these issues to deliver next-level results across the board.
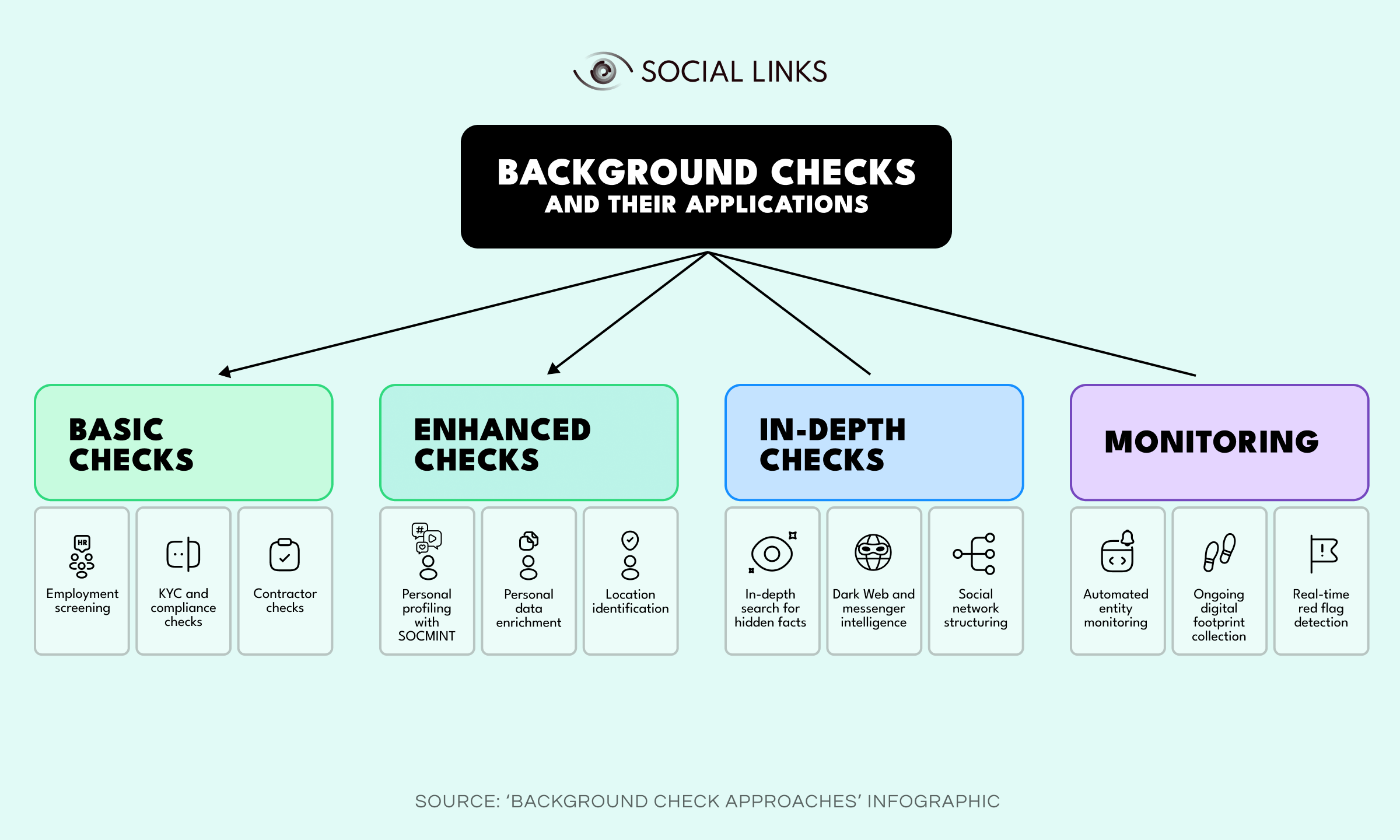
Although employment checks (or pre-employment screening) may be the type of checks that most people are acquainted with, they really are just the tip of the iceberg. Background checks come in various forms, which vary greatly in their thoroughness, remit of investigation, and areas of application. Here’s our breakdown:
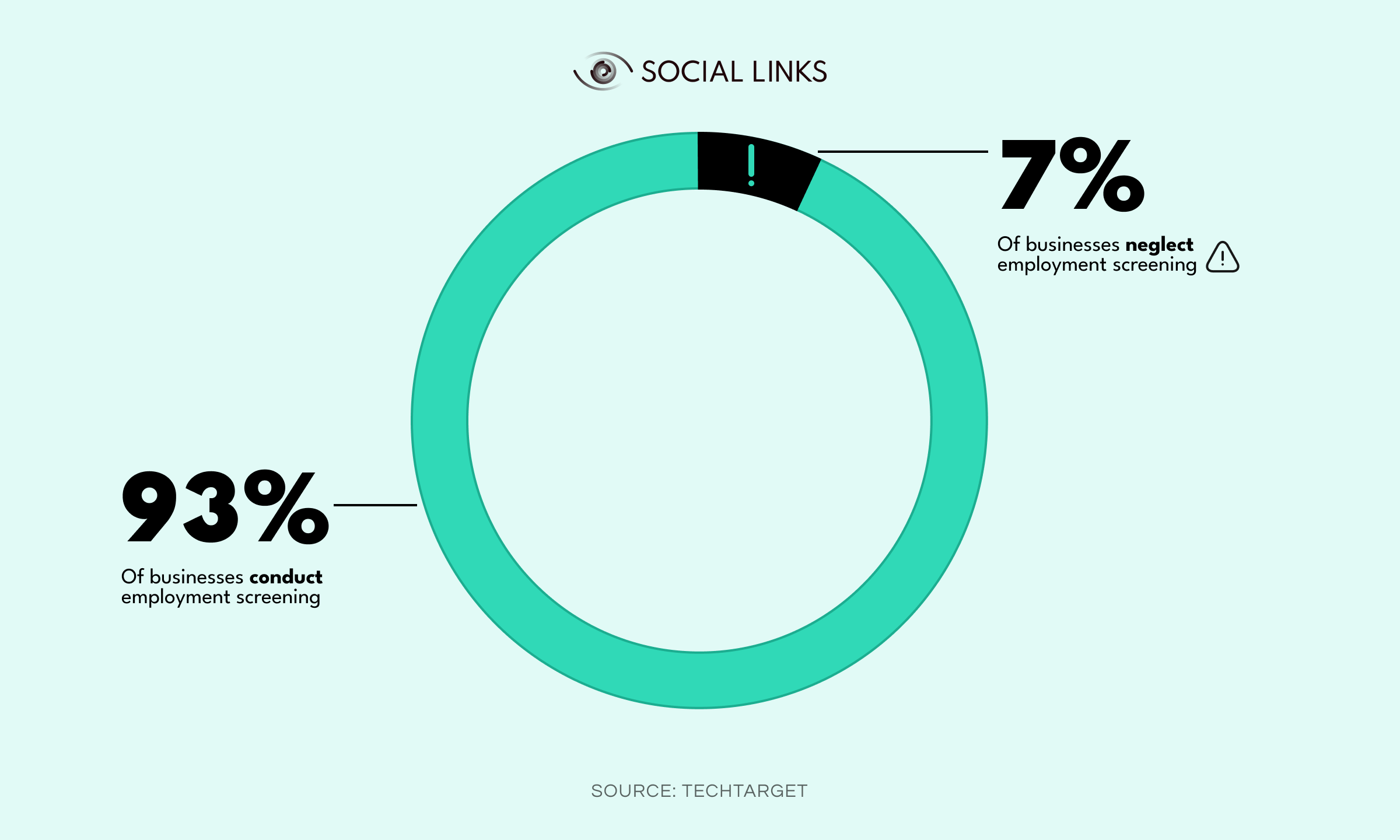
Despite not requiring much technical expertise to conduct, these checks are considered very important and have a widespread application, especially in the corporate world. For instance, standard background checks are used for employment screening and minimal compliance criteria evaluations. In fact, 93% of companies conduct background checks on potential employees.
Standard background checks predominantly center around data accessed via public registries that can disclose financial and criminal records. These relatively superficial sweeps will, of course, uncover certain serious red flags but nonetheless leave a number of stones unturned.
This type of check reaches beyond public registries, incorporating social media intelligence (SOCMINT) to identify social ties, create psychological profiles, and carry out lifestyle assessments. The social media remit also helps verify stated facts such as educational background and employment history.
At the same time, enhanced checks may also employ web intelligence (WEBINT) to collect any other data of note that may be floating around the online space in news outlets, forums, and other sites. Enhanced checks are often carried out for Know Your Customer (KYC) processes, contractor checks, or vetting for sensitive positions.
When the stakes are high, and investigators can’t afford to overlook a scrap of data or leave any stone unturned, in-depth background checks are the way to go. By probing deeper, facts and content, the subject has intentionally kept secret can come to light, ultimately giving an accurate portrait—warts and all.
So, where do investigators turn to this new level of depth? The Dark Web can be a treasure trove of hidden indicators if the subject’s activities have drifted onto darknet marketplaces and forums. Furthermore, if a subject’s data has been compromised, indicators of this can often be found in the digital underground.
Meanwhile, messenger intelligence can shed light on someone’s more hidden interests through group memberships and chats. Combining such research with WEBINT and SOCMINT can provide a remarkably detailed and comprehensive picture of the person of interest. These types of checks often play a part in criminal investigations and enhanced due diligence.
The above types of checks are all great for assessments that run up to a certain point in time. However, sometimes, it’s crucial to keep constant track of a subject so that you are wise to anything dubious that crops up in the ever-unfolding present. The ongoing development of a digital footprint in real-time is often an essential practice for stakeholders who need to know as soon as any kind of red flag shows itself.
To carry out such continuous checks, automated scripts are applied to a given subject. These can include any sources and search parameters in one-time checks and can be custom-built or selected from pre-designed scripts. Once a script has been applied, investigators and analysts can gain vast amounts of time and headspace while the system does much of the research legwork for them.
Like any type of investigation, background checks are not all plain sailing—and many circumstances can get in the way of comprehensive or accurate results. These include:
People are generally wise to the information they broadcast on social media and other platforms. As such, they take steps to ensure that undesirable or illicit activities are suitably pruned from their public personas. Moreover, it can't be assumed that someone is squeaky clean just because no past misdeeds surface in public records.
Furthermore, when input data is fragmentary, and subjects are willfully operating under aliases, the amount of actionable intelligence that can be elaborated on from the initial details may be insufficient for the purposes of the check.
Of course, taking any information drawn from social media at face value would be negligent. What guarantees do we have that anything people publish on social networks is true? Practically none. When cases are pursued based on false data, investigators will inevitably find themselves at a dead end or in a blind alley. Data really needs to be validated if real progress is to be made.
It’s not uncommon for people to have a range of profiles for different scenarios—in fact, it may speak to a certain amount of savviness on the part of the subject. For example, someone may have different profiles to communicate with different associates and create fake personas for activities they recognize to be dubious.
This is a serious challenge for investigators as it erodes the interconnections that are so crucial to building an effective digital footprint. Such actions can also operate like a type of digital camouflage—subjects can hide their personas among a flood of false positives, like needles in haystacks.
The guidelines set out by a given industry regarding compliance or employment screening may not always be sufficient. Meeting the minimum requirements may feel like the easy option—that is until a costly oversight occurs. Resources saved in the present could end up costing a lot more in the future.
OSINT tools are proving essential for a range of investigative work. Likewise, in the area of background checks, investigators and analysts stand to gain a huge amount from employing intelligence platforms. With the judicious application of such tools, many of the difficulties outlined above can be effectively overcome.
Creating digital footprints has become standard for a very good reason—it provides structure and focus to data swamps, allowing productive analysis. However, it also confers reliability on the data extracted because profiles, usernames, connections, and activities that tally across a range of platforms will only reinforce each other in terms of veracity.
However, creating a fully-fledged digital footprint comes with its own challenges. Open data is extremely diverse. First, it comes in a variety of formats, including text (name, alias, phone number, email, posts, documents, etc.), imagery (photos, videos, metadata), geo (GPS coordinates), and more. Second, the data itself needs to be extracted from a dizzying array of sources.
Dealing with these factors in delivering an actionable footprint requires a centralized system capable of bringing together data of varying formats and origin, all in a single work area. Investigators and analysts require a unifying platform to elaborate the structures they need to progress in their research. This is precisely what advanced OSINT tools provide.
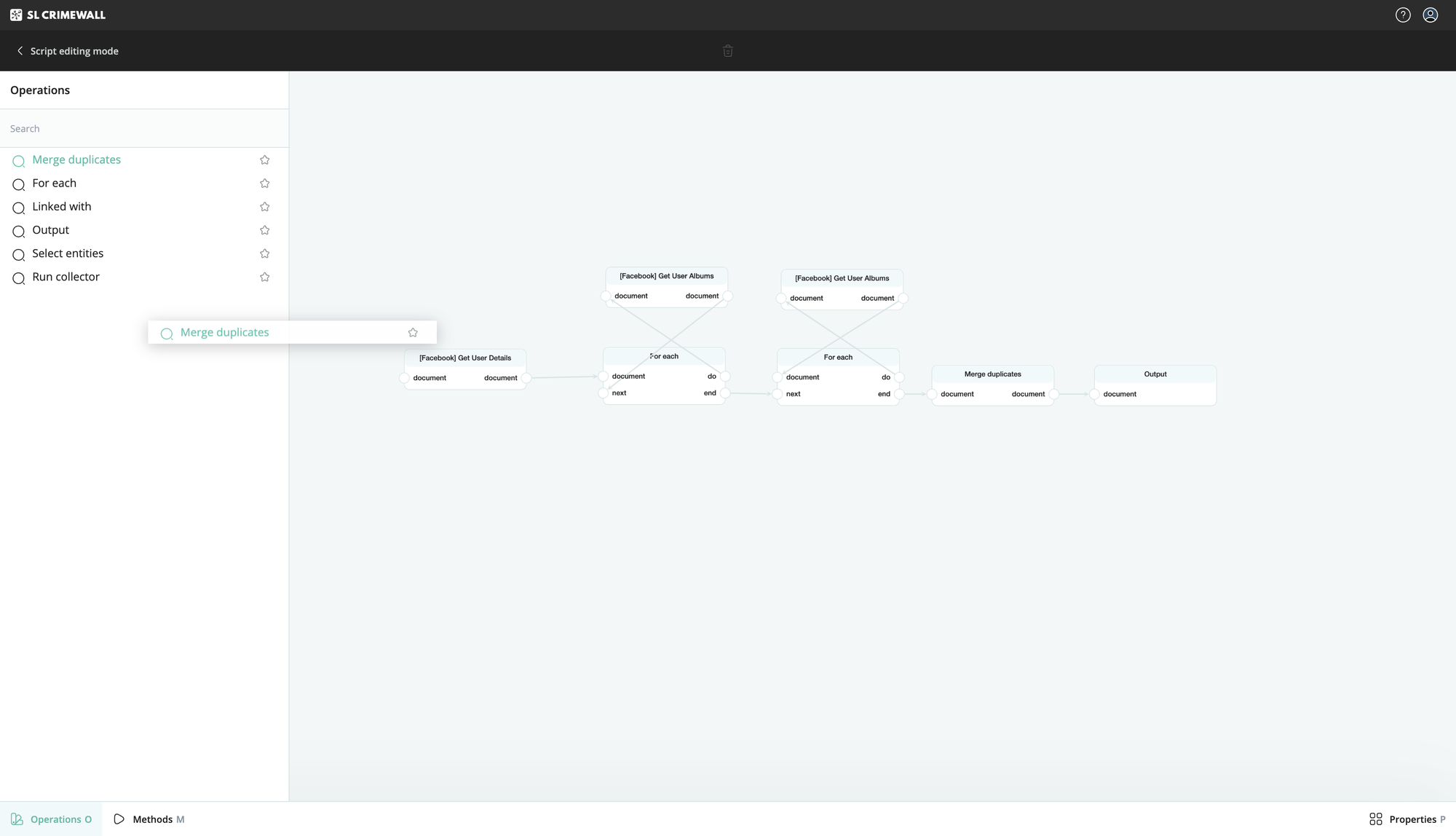
While background check approaches may differ from case to case, certain procedures emerge that are productive for most subjects. When a string of searches and data expansion techniques come together effectively, it makes eminent sense to find a way to combine these things into a set cluster or group that can be initiated in a single step, as opposed to a time-consuming, multi-step procedure.
This is what SL Crimewall’s Script Builder feature allows users to achieve. Designed as an intuitive drag-and-drop interface, users can quickly custom-design their own search and extraction amalgams and build up a toolbox of automated processes that can be deployed in a single click. This practice saves huge amounts of routine work and time without compromising one iota in the quality of results.
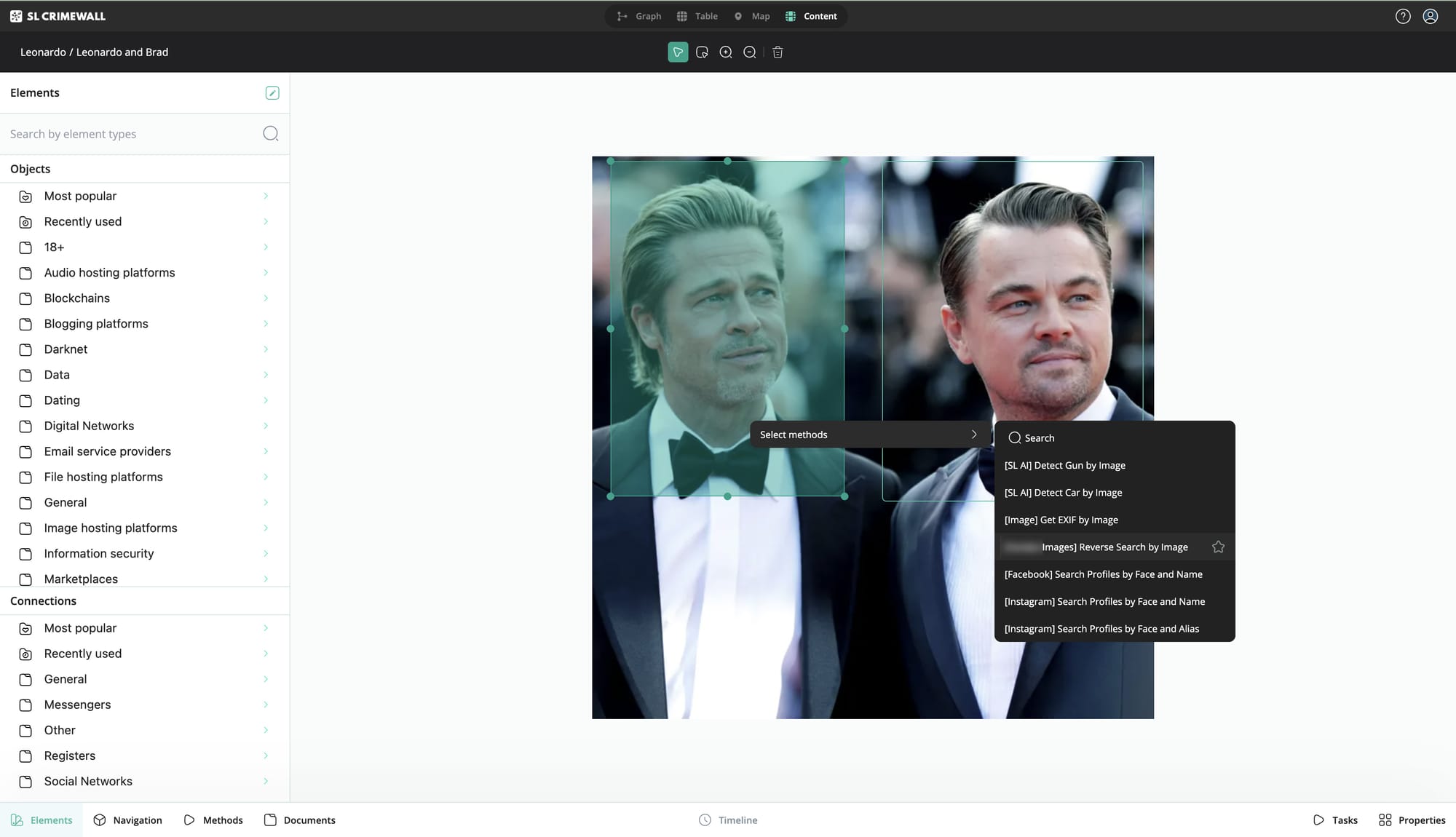
Through search engines, everyone’s familiar with text-based queries. But in some cases, inputting an image as your point of departure can yield much more valuable results. For example, if a subject has several social media profiles under different personas, mere text-based searches may be insufficient to connect them. Or, what if a subject has concealed a connection on their friend list?
Advanced open-source intelligence systems such as SL Crimewall provide workarounds to these issues through reverse image search features. This capability allows investigators to achieve all kinds of breakthroughs. For instance, they may find subject accounts that would’ve otherwise remained hidden, connections that were intended to be clandestine, and generally be able to create a far more comprehensive digital footprint and, by extension, effective background check.
When your input data is fragmentary—and this is a common occurrence—your chances of developing actionable intelligence from what you have grown under the number of resources you can draw from and how you can structure the data. This is where OSINT tools undoubtedly excel.
By allowing users to combine data from almost every conceivable domain of the internet, including the Deep and Dark Web, intelligence tools can work miracles with even the sparsest scraps of data. From an isolated email address, a whole range of investigative paths open up, allowing investigators to pursue fruitful leads that would be otherwise invisible.
Companies may be tempted to cut corners on background checks for the simple motivation of saving some cash. However, as discussed above, such policies could end up being costly. For the level of research depth, they can provide open-source intelligence solutions at a very reasonable price. A small OSINT investment could revolutionize a company’s screening and compliance processes and ultimately deliver huge savings by avoiding fines and internal fraud.
Modern OSINT tools such as SL Crimewall can greatly enhance any background check. With minimal investment, companies and other organizations can conduct more comprehensive background research that delivers an in-depth understanding of the subject, a detailed map of connections, accurate and reliable data, and more effective, actionable results. With ever-better research results, organizations can make informed decisions that circumvent all kinds of risks and potential costs.