Facial Recognition: A Pillar of Modern OSINT

Facial recognition has become one of the most powerful analytical capabilities in modern investigations. As digital platforms expand and images circulate across the open web, the ability to identify people in photos has reshaped how OSINT analysts verify identities, expose fake accounts, and connect digital footprints across platforms.
In this article, we break down how facial recognition works within OSINT workflows, what distinguishes it from everyday image matching, and how investigators use facial recognition software to support identity verification, fraud detection, and threat intelligence. We also look at real-world applications, legal considerations, and how this biometric capability is evolving.
Traditional OSINT relies on text-based inputs such as usernames, emails, domains, or phone numbers. But as anonymization tools grow ever more sophisticated, investigators are increasingly depending on facial recognition technology to establish cross-platform identity correlation.
Facial recognition enables OSINT analysts to:
And unlike document-based verification, facial signals are inherently harder to fake, making them a powerful resource for identity intelligence.
Modern OSINT investigations use a multi-stage workflow that transforms raw images into structured intelligence. The process typically follows four stages:
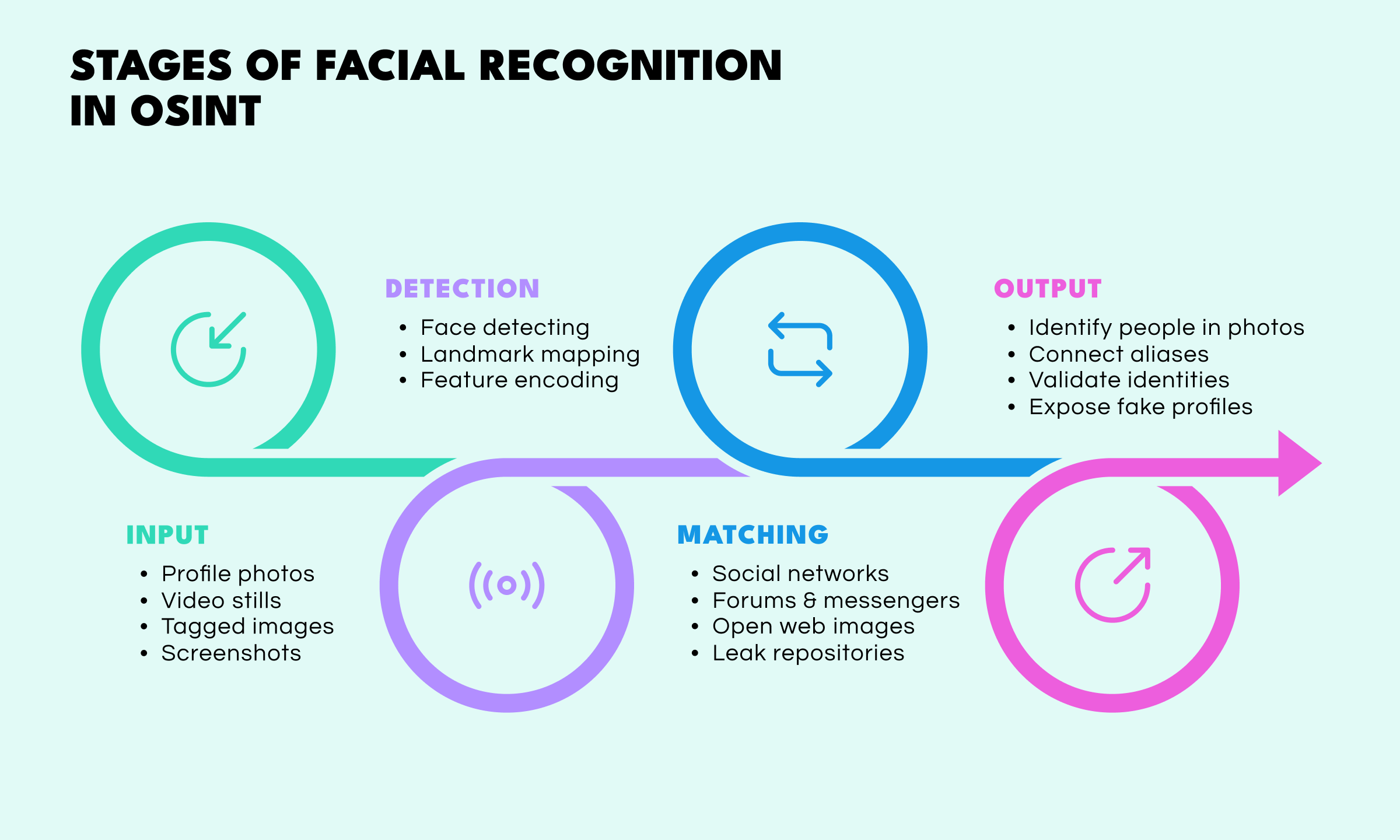
Every investigation begins with the gathering of visual inputs where a detected face may appear. These may include:
Even a single image is enough to initiate a full cross-platform analysis.
Facial recognition software can analyze each image and convert facial patterns into machine-readable signatures. This includes:
This step turns a human face into a structured data point suitable for large-scale matching.
Through in-built facial recognition technology, OSINT systems can run comparisons across open platforms to find where the same person appears. This allows analysts to:
This is where recognition techniques for identification are most effective.
Finally, OSINT analysts review the results to perform identity verification:
By combining facial recognition with metadata, social graphs, timestamps, and corporate records, investigators build a full identity profile—not just a match.
Facial recognition is not just a matching tool; it's a force multiplier for several types of OSINT-driven investigations.
Scammers, impersonators, and social-engineering actors often reuse stolen images or maintain multiple aliases. Facial recognition helps analysts:
This makes it especially valuable in fraud, harassment, or misinformation cases.
Images frequently reveal relational context, including:
This helps analysts construct social graphs more accurately than text alone allows.
Threat actors sometimes leak photos unintentionally—profile avatars, marketplace images, stolen ID scans, livestream captures. Analysts can use facial recognition software to:
This is critical in deanonymization operations.
Facial recognition supports high-assurance identity checks when documents may be forged or inconsistent. It enhances:
In regulated environments, biometric analysis adds an extra layer of certainty to identity verification.
Facial recognition is a powerful capability—and must be handled responsibly.
Key considerations include:
When used lawfully and ethically, facial recognition becomes a trusted and defensible investigative method.
Facial recognition is rapidly merging with other biometric and forensic signals, including:
This convergence is creating a form of multi-layer identity intelligence that’s more accurate, more resilient to deception, and better suited to emerging threats.
Facial recognition is now a core component of modern OSINT, giving investigators the ability to cut through digital noise, expose fraudulent identities, and connect scattered visual clues into coherent intelligence. By transforming images into structured biometric signals, analysts can correlate profiles, uncover deception, and validate identities with a level of confidence that text-based inputs alone can’t provide.
As anonymity tools evolve and threat actors become harder to track, the responsible use of facial recognition offers a critical advantage, strengthening fraud detection, cyber investigations, due diligence, and security workflows across industries. And when combined with metadata, behavioral context, and broader OSINT methods, it becomes a powerful and defensible way to reveal truth in an increasingly opaque digital environment.
The terms are often used interchangeably, though facial recognition typically refers to advanced biometric systems, while face recognition can include simpler image-matching techniques. Both are essential components of OSINT workflows.
Facial recognition software analyzes biometric patterns, compares them across open-web sources, and helps analysts perform identity verification and digital footprint mapping. This allows investigators to recognize and correlate individuals across unconnected platforms.
Modern algorithms are capable of delivering extremely high accuracy, even in challenging conditions. However, effectiveness depends on image quality, lighting, and whether manipulated media (like deepfakes) are present.
It’s used to detect fake profiles, identify people in photos, track suspects across platforms, support cyber investigations, and provide evidence for legal and compliance processes.
Legality depends on jurisdiction. Law enforcement and intelligence agencies may use it under defined frameworks, while private organizations must comply with privacy laws such as GDPR. OSINT methods rely solely on publicly available data.
Yes. Many systems combine deepfake-detection, media forensics, and anomaly detection to help analysts avoid deception and ensure reliable attribution.
Future developments include multi-modal biometrics, more privacy-preserving algorithms, and deeper integration with cyber-investigative workflows. This is set to enhance accuracy while maintaining legal and ethical standards.
Want to see how facial recognition fits into real investigative workflows? Book a personalized demo with our specialists and explore how Social Links solutions combine biometric analysis, entity correlation, and open-source intelligence into a single, investigator-ready environment.