Inside the Modern OSINT Toolkit


Open-Source Intelligence (OSINT) has become a core pillar of modern investigations. Yet the success of a given case depends not only on the analyst’s skill but also on the strength and synergy of their tools. If the internet is an ocean of data, the right OSINT toolkit is the vessel, sonar, and net that makes it navigable. Manual data collection is no longer realistic. Automation, analytics, and visualization are now essential for turning raw data into actionable intelligence.
This guide explores the key categories of OSINT software tools, including how they fit into an analyst’s workflow, and why integrated investigation platforms are shaping the future of intelligence work.
No single OSINT tool can handle everything. A well-rounded toolkit combines multiple capabilities, each suited to a specific task. The goal is to create an ecosystem that scales with the complexity of the mission. Below are the main categories of tools that make up a modern analyst’s arsenal.
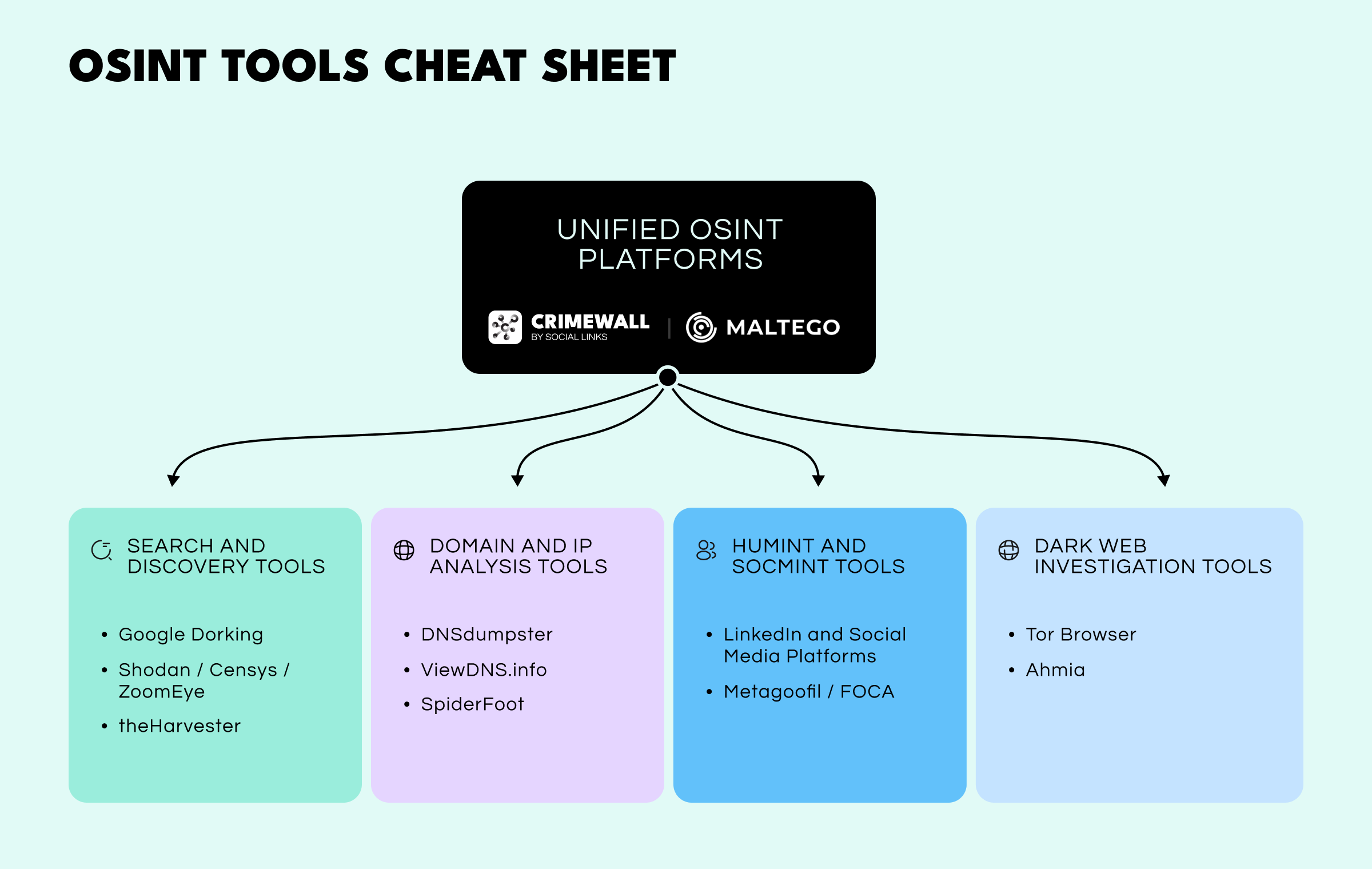
These are the starting points for most investigations—they’re broadly used to map the digital footprint of a target.
The most fundamental of OSINT techniques. Analysts don’t just search—they query with precision. A penetration tester might use filetype:xls site:targetcompany.com "password" to find exposed spreadsheets containing credentials. Or they might try intext:"Powered by vBulletin" site:targetcompany.com to locate outdated and vulnerable forum software.
These search engines index internet infrastructure. A CTI analyst can track a threat actor’s servers by locating those that use a specific self-signed SSL certificate, potentially exposing an entire command-and-control (C2) network. Similarly, a red teamer can scan an organization’s IP ranges for exposed services such as RDP (port 3389) or unsecured databases, revealing entry points.
A classic open-source reconnaissance tool. Given a domain like targetcompany.com, it automatically queries public sources (Google, Bing, Baidu) and returns a list of employee emails, subdomains (e.g., dev.targetcompany.com, vpn.targetcompany.com), and IP addresses, providing an instant map of potential assets.
Once assets are identified, these tools help analysts investigate the underlying infrastructure.
This allows you to create a visual map of a domain’s DNS structure. Entering a company domain reveals mail servers, subdomains, and name servers, offering a snapshot of the network and its dependencies. Analysts can identify misconfigurations, such as a development server sharing a subnet with production databases.
Useful for reverse IP lookups. For example, if targetcompany.com is hosted on a shared server, the lookup might reveal other domains on the same host, such as outdated-wordpress-blog.net. A pentester could exploit the weaker site to gain access to the shared server and pivot toward the primary target.
An automated OSINT framework with over 200 modules. Feed it a target (like a corporate domain) and it will run for hours, collecting associated domains, employee names, exposed cloud storage (AWS S3, Azure Blob), and mentions in data-breach corpuses—work that would take days to perform manually.
This category focuses on the human element—the most unpredictable and often most valuable target for an adversary. The goal of OSINT in this context is to gather intelligence that can be used to manipulate, deceive, or impersonate individuals to gain access or information.
Adversaries preparing a targeted spear-phishing campaign treat professional and social media platforms as goldmines for reconnaissance. Let’s say an adversary discovers an IT administrator who has publicly posted about their excitement to attend the upcoming "Global Cyber Conference”.
The threat actor can now craft a highly convincing spear-phishing email, appearing to be from the conference organizers, complete with a malicious attachment disguised as a "session agenda". The employee, anticipating such communication, is far more likely to trust the email and open the payload, unwittingly granting the adversary initial access.
Adversaries also exploit the seemingly harmless “digital exhaust” of corporate documents. Consider a threat actor who downloads a publicly available PDF presentation from a target’s website. Using metadata extraction tools such as FOCA or Metagoofil, they can uncover sensitive details embedded within the file, such as the author’s internal username (e.g., jsmith), the software used to create it (e.g., Microsoft PowerPoint 2019), or even internal file paths (e.g., C:\Users\jsmith\Documents\Final_Draft.pptx).
For an adversary, this is actionable intelligence. It confirms the company’s username convention (first initial + last name), generates a list of potential targets, and reveals software versions that can be checked against known vulnerabilities for precise, targeted exploitation.
The Dark Web is critical for modern threat intelligence and exposure assessments, requiring secure access and proper OPSEC.
The entry point for anonymous access to .onion sites, this is essential for monitoring criminal marketplaces or leak forums without exposing your identity or IP address.
A search engine for the Tor network. Analysts can search for mentions of a target organization alongside keywords like “breach,” “leak,” or “RDP access for sale” to identify compromised assets or credentials being traded.
Switching between dozens of tools slows investigations and increases the chance of losing context. Integrated OSINT platforms address this by combining data collection, analysis, and visualization in one environment.
A long-standing data-mining and visualization tool. It maps entities as nodes on a graph, showing relationships between emails, domains, and IPs. However, users often need to purchase and manage additional data connectors (“Transforms”) for broader coverage.
A next-generation OSINT platform designed for complete investigation workflows.
While Maltego only provides you with the canvas, SL Crimewall gives you the canvas, paints, and brushes, all ready to go.
There’s no universal “best” OSINT tool—only the right one for the job. Lightweight scripts like theHarvester are perfect for quick reconnaissance, while complex CTI or financial-crime investigations benefit from platforms that can ingest and correlate massive datasets.
As investigations grow from targeted penetration tests to tracing state-sponsored threat groups, analysts need scalable systems that combine open-source agility with enterprise-level power. The goal is to transform scattered data into a cohesive, actionable intelligence picture.
An effective OSINT toolkit is more than a collection of apps. It’s a connected ecosystem that transforms data into insight. The tools you choose determine how efficiently you can navigate the ocean of information and uncover what truly matters.
OSINT Tools are software applications and platforms that help investigators and analysts collect, process, and analyze publicly available information. They are essential for transforming open data into actionable intelligence.
OSINT Tools play a critical role in cybersecurity by enabling attack surface mapping, identifying exposed assets, monitoring the dark web, enriching threat intelligence, and supporting incident response.
Some of the most widely used OSINT Tools include Shodan, Censys, ZoomEye, SpiderFoot, theHarvester, Maltego, FOCA, Metagoofil, and integrated platforms like SL Crimewall. Each serves different functions, from infrastructure mapping to social media analysis.
They allow analysts to discover adversary infrastructure, monitor dark web marketplaces, track leaked credentials, and correlate technical indicators with human activity. This helps organizations anticipate attacks rather than simply react to them.
Many OSINT Tools are open-source and free, such as theHarvester or DNSdumpster. However, commercial platforms like Maltego or SL Crimewall provide advanced features, integrated data sources, and collaborative environments designed for large-scale investigations.
Most OSINT Tools operate on publicly available data, making them legal in many jurisdictions. However, legality depends on how they are used—scraping private data or unauthorized access can cross legal boundaries. Always comply with local laws and ethical guidelines.
OSINT Tools are used by cybersecurity analysts, penetration testers, red teams, law enforcement agencies, threat intelligence units, journalists, and researchers to uncover risks, verify identities, and investigate adversary behavior.
Want to learn more about how Social Links’ integrated OSINT platform can transform your investigative workflow? Follow the button below to book a personalized demo with one of our specialists and see how Crimewall can streamline data collection, analysis, and visualization within a single, unified environment.