June’s OSINT News: Open geodata meets sustainable development, North Korean hackers target HR, and the future of voice biometrics


As digitization spills into almost every nook of our everyday life, developers are hard at work, churning out AI algorithms on industrial levels to address any UX inconvenience you’d care to imagine. With reverse image searches and text analyses now at the fingertips of anyone with a smartphone, it begs the question: what’s next?
An issue coming to the forefront concerns biometrics. While voice recognition has great potential for authentication, it also comes with its downsides, with biometric data providing ever more opportunities for exploitation. But it’s not all doom and gloom. The rise of data analytics is empowering us to use OSINT for public good through the detection and monitoring of deforestation and arable land.
Once mainly the purview of government bureaus and military services, geospatial intelligence has been working its way into the private sector for years now. Today, the public have access to satellite image databases such as LandSat by NASA or Sentinel by the European Space Agency, which renew their contents on a daily basis, providing up-to-date global geodata to anyone who’s interested.
Meanwhile, the ever-increasing fleet of commercial satellites in our orbit are delivering a daily influx of hi-res geospatial photos, and driving the cost of geodata down year by year.
For data science enthusiasts this represents a world of possibilities, and this incredible resource of data is already being put to good use. According to a UNESCO report, there are already more than a hundred ML models aimed at solving sustainable development problems with data analysis.
Satellite imagery analysis helps ecologists define deforestation patterns, especially in cases of human causes such as the building of roads across the Amazon rainforest. With an accuracy rate at around 70-90%, modern models allow decision makers to evaluate the potential ramifications of projects, and make plans which better serve the interests of ecosystem conservation.
Unauthorized fishing is a global problem that is not considered strictly criminal, but is nevertheless a huge hazard to the marine ecosystem. When vessels have their trackers turned off, it is usually a sign that some questionable activity is on the cards - most probably poaching. By combining open-source GPS vessel tracking data with satellite imagery, maritime police can track ‘hidden’ vessels and reign in activities that are environmentally detrimental.
Hunger is one of the most dangerous threats to the world population. With most of Europe’s arable land in Europe either occupied or protected, the world is now looking to Africa and its untapped tracts of fertile land. Although finding good arable land in underdeveloped regions is an onerous task, open-source satellite imagery helps to detect the territories that are best-suited for farming, helping to fight global food shortages.
While this is a non-issue for most in the first world, many people in developing countries suffer from the lack of a serviceable address. This causes significant problems for logistics and communication, negatively impacting the quality of life. Using geospatial data, analysts from public organizations can generate city and village maps and automatically assign addresses so that all the populated areas will be covered by governmental services.
We tend to think of data security in terms of digital safeguards, but by overlooking the human element corporations are leaving themselves vulnerable to infiltration and theft from inside the organization. It has recently been discovered that a lot of Western companies have been hacked through HR departments insufficiently screening job candidates.
Having been under severe sanctions for many years, the North Korean government has been hard pushed to up the country’s inflow of dollars into and finance various state programs. In such a fix, hacking has become a common offshoot by which North Korea can pursue its own interests. While the West is perfectly aware of this, it doesn’t seem to have been wise to all of the tactics being employed.
A ploy which seemed to have slipped the net involved North Korean agents simply posing as casual IT professionals from China, South Korea, Japan and even Russia seeking work, thereby gaining access to sensitive company data. In response, the FBI recently issued instructions for businesses on how to detect scam workers from the DPRK applying for freelance contracts.
According to the FBI, North Koreans earn more than $3M each year for their government via this scheme, the proceeds of which could be used to finance the national weapons development program. And such infiltration is not limited to theft, but can also include sabotage such as the deployment of malware into corporate systems. However, detecting such agents is no mean feat and HR departments need all the advice they can get.
Voice recognition is a new hit on the data analysis market. However, few seem to understand how powerful and dangerous voice recon may be for open-source intelligence.
Utilizing over a hundred muscles, human speech is a hugely complex phenomenon that has huge potential for biometrics. And with each individual possessing a totally unique vocal signature, the uses of such data are not lost on major tech companies. Siri and Alexa already use voice analysis for authentication while the voice recognition market is booming and projected to reach $21B by 2026.
Such technologies tend to be embraced as progressive, but a question which tends to be overlooked is: How might such data be used for cynical and exploitative ends? Afterall, the human voice can reveal a wealth of information on its owner including the speaker’s age, gender, ethnicity, native language, health, emotional state, cultural background and behavioral patterns.
Spoofing techniques are already being adopted to imitate a speaker in fraudulent payment authentications, and vocal deepfake models are being developed which could carry out even more complicated biometric scams. In such a climate, researchers are predicting that without the development of voice anonymization tools, personal data will be at a greater risk than ever before.
But another relevant question might be: Are people ready to sacrifice the naturalistic character of their online voice to secure their vocal data against misuse?
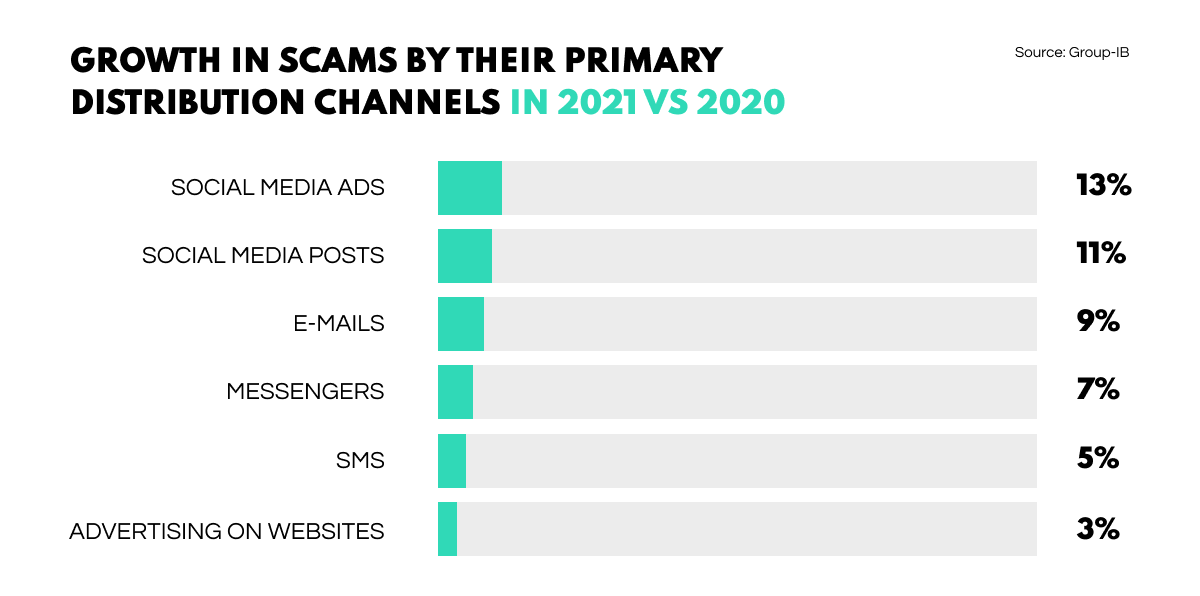
According to a Group-IB report, scams are the most widespread type of cyber criminal activity in 2021, with the number of connected criminal groups rising by a factor of 3.5 to 390 against 110 in 2020.
With the open-source intelligence market expanding by the day, Social Links has shared their top-10 OSINT tools in the 2022 landscape. In a readable, useful, and up-to-date guide, you can get a handle on the main functionalities for each OSINT product on the list to see what sets them apart from each other, all without getting bogged down in technical details.
The US Army has created a new Cyber Military Intelligence Group - an intelligence unit established to support Cyber Command. The Group will combine conventional military intelligence activities with the analysis of commercial and open data (OSINT) for both defensive and offensive cyber operations. The primary goal of the group is the ‘establishment of information advantage.’
The social media platform is offering up to $18K of reward for those who manage to root out genuine security weaknesses. This campaign will not only make it harder for hackers to gain unauthorized access and leak data, but a chance for OSINT tools to shine by automatically scouring social media data as well.
This is yet another argument as to why modern law enforcement agencies desperately need to apply OSINT systems in deepfake detection. While a recent crypto platform scam was recently nipped in the bud, an Elon Musk crypto giveaway scam swindled $580K in just a week back in 2021.
It turns out that stolen data marketplace Industrial Spy has been delivering ransomware to its clients and encrypting their devices. Unless users pay the ransom, their data will be leaked and sold on the very marketplace they are exploiting - a scheme ensuring that the Industrial Spy admin wins out one way or the other.
And that brings our June digest to a close. We hope you enjoyed this edition and will be back next month for more.