Link Analysis: Lifeblood of the Modern Investigation


Imagine the classic police-room evidence board covered in photos and documents, and interconnected by strings, with the detectives sitting back trying to identify patterns, establish connections, and so on. This technique, in essence, is link analysis—only, with today’s tech, the data involved can be scaled up to a mind-boggling degree, opening the door to remarkable possibilities.
So today we’re taking a detailed look at this indispensable technique that lies at the very heart of almost all modern investigative work, from OSINT and intelligence work to journalism and beyond. Read on to get your head around the workings of this all-important discipline, the tools involved, its range of applications, future developments, and more. Let’s jump in…
Link analysis (also known as connection analysis or network analysis) is the modern, computer-assisted version of “connecting the dots” in investigative data. It involves modeling information as a network of entities (people, accounts, places, events, etc.) and relationships (the links between those entities).
Having data represented as the nodes and links of a graph is a major part of how link analysis works—it enables investigators to visualize complex webs of interconnections and spot patterns that would’ve stayed hidden in other formats such as spreadsheets or reports. In short, link analysis transforms disparate data points into a visual map of relationships, making it far easier to follow chains of associations across vast datasets.
Major benefits of link analysis are that it allows an investigator to ask questions like: Who is linked to this suspect? How are these bank accounts related? Which events might be part of the same scheme? For example, analysts might graph a fraud investigation by linking individuals to companies, bank transactions, and addresses—revealing that several people share a phone number or that funds flow through the same offshore entity. Link analysis shares many principles with broader OSINT methodologies for criminal investigations, where network-centric intelligence is essential for mapping fraud, tracing cybercriminal ecosystems, and correlating identity data across platforms.
The visual “link graph” that results can illuminate a hidden structure: perhaps a hub-and-spoke network of shell companies or a chain reaction of events leading from a minor incident to a major crime. Instead of sifting through endless records, an investigator using link analysis sees a clear picture of the network behind the data. This human-friendly visual approach is at the heart of many modern investigative platforms.
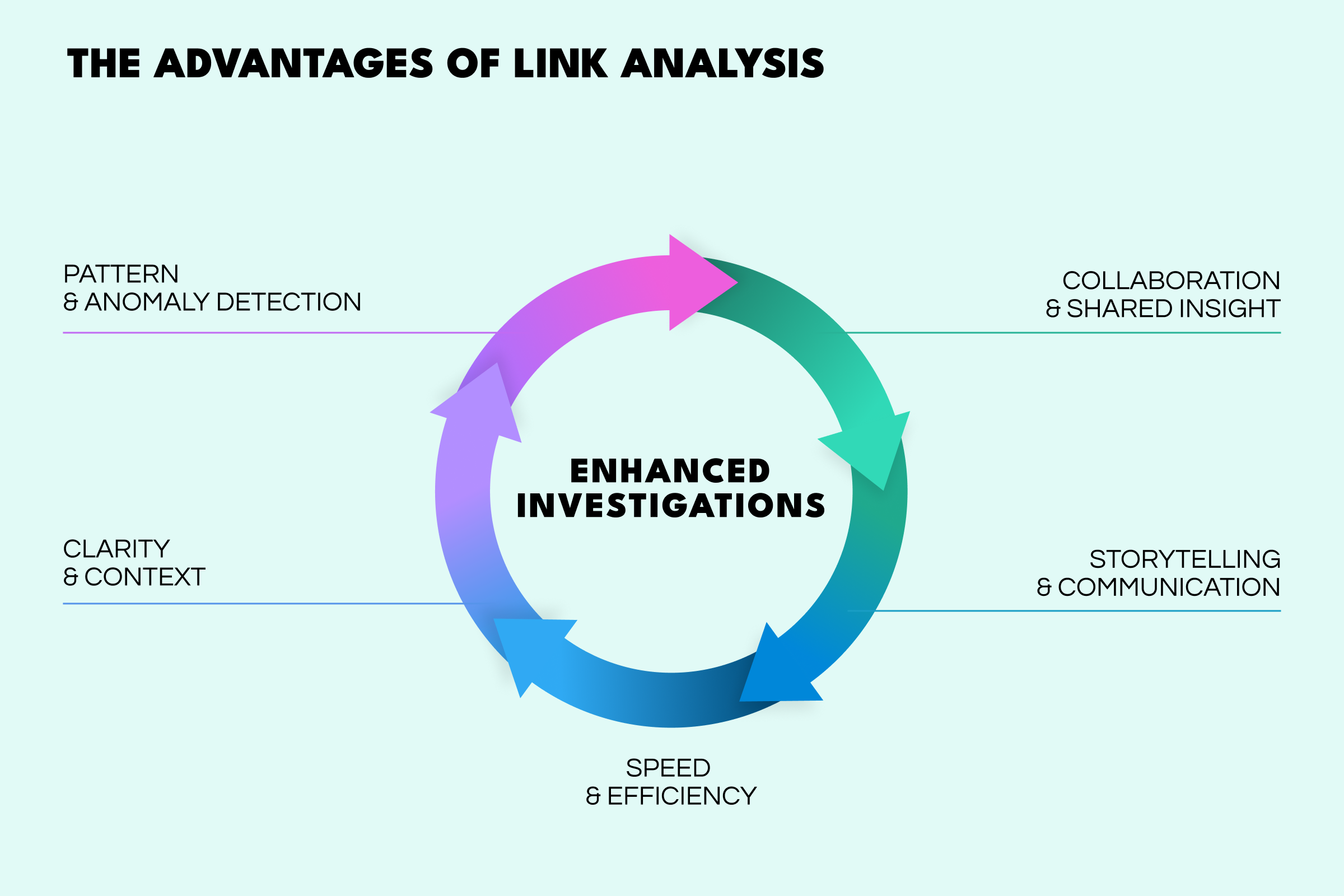
In an era of information overload, link analysis has moved from a niche technique to a must-have in investigative workflows. It offers several compelling advantages that empower investigators to work smarter and faster:
Modern link analysis tools can ingest and correlate huge volumes of data in seconds—a task that would take humans weeks by hand. By automating the collation of who-is-connected-to-whom, it speeds up casework significantly, improving investigative efficiency and accuracy. The result? Faster connection identification, quicker breakthroughs, and higher case clearance rates.
Link analysis brings order to chaos—it simplifies complex investigations by visually showing relationships and degrees of involvement among entities. Rather than reading pages of reports in isolation, analysts see context at a glance—for example, how a person of interest is related to others, or how events sequence over time. In short, link analysis turns raw data into an intelligible story, giving crucial context that prevents tunnel vision.
Visual network maps allow investigators to tell the story of a case in a compelling, straightforward way. For instance, prosecutors and analysts often use link graphs to present findings to decision-makers or juries, because the diagrams make complex relationships easier to follow than a technical report. This storytelling aspect ensures that crucial insights aren’t lost in translation—the connections speak for themselves.
By seeing connections laid out graphically, investigators can quickly spot patterns, clusters, or outliers that would be otherwise invisible. Link analysis excels at highlighting anomalous relationships—suspicious links that “don’t fit” the normal pattern. For example, this may be an email address that’s the only link between two criminal groups, or a set of transactions that form a loop inconsistent with legitimate business. Such insights are invaluable for detecting fraud, cyber intrusions, or terrorist networks, where finding the one strange connection can crack the case.
Modern investigations are team efforts, often spanning multiple agencies or disciplines. Link analysis provides a common visual language that everyone on a task force can understand and contribute to. By mapping out the investigation on a shared platform, multi-agency teams can collaborate in real time, each adding data or insights to the graph, ensuring that critical pieces of information are not siloed. A detective, a financial analyst, and an intelligence officer, for example, can literally see how their information intersects on the graph turning investigation into a team sport, with a unified map as the playing field.
Link analysis isn’t a merely abstract concept—it has repeatedly proven its value in real investigative scenarios. Here are a few prominent use cases where mapping connections has transformed the investigation outcome:
Law enforcement agencies use link analysis to map criminal networks, from street gangs to mafia syndicates. For example, police analysts might graph gang members, their associates, and certain incidents to identify key players and underlying feuds. By mapping relationships and measuring network “centrality”, analysts have found that interpersonal conflict is often the root cause of a gang war—an insight that has helped police intervene more effectively.
Past cases show that such network maps help pinpoint influential figures or chokepoints in criminal organizations—a claim that is also backed up by academic studies. By identifying who the hubs and connectors are, authorities can dismantle networks more surgically, and even predict how the network might rewire itself if a key player is removed.
In complex financial crimes, the challenge is often following a trail that zigzags across many accounts and entities. Link analysis has become a go-to technique for “following the money”, where graphs of transactions, shell companies, phone records, and more are elaborated to expose hidden relationships that indicate laundering or fraud.
Link analysis was instrumental in the famous Panama Papers investigation, where journalists used graph databases and visualization tools to connect people and offshore companies across dozens of jurisdictions, exposing a global web of hidden money. Such graph-driven analysis makes it far easier to spot unusual links between accounts and entities, flagging possible fraud or sanctions evasion much faster than traditional ledgers.
Link analysis is used to track terror cells, extremist networks, and espionage rings—it provides intelligence teams with the clarity and focus needed to effectively prioritize targets and delegate resources. By linking suspects to known associates, communication records, travel data, and OSINT, intelligence analysts can build a map of terrorist networks to identify leaders and uncover support structures.
For example, plotting connections between individuals involved in terrorist activities might reveal an intermediary (perhaps a financier or recruiter) connecting two seemingly separate extremist cells—a critical discovery for prevention. What’s more, by analyzing communications and social media links, agencies can detect early-warning signs of radicalization or coordinated plans, allowing units to stamp out threats before they become public disasters.
Outside of government, investigative journalists have embraced link analysis to tackle massive data leaks and complex stories. A striking example is the Panama Papers where journalists had to deal with an “offshore data tsunami”—tens of millions of leaked files from offshore financial service firms.
By using an advanced link analysis platform, journalists extrapolated names, companies, and connections into an interactive network, allowing hidden partnerships and money trails to be exposed far more efficiently than would’ve been possible through traditional investigative methods.
And similar techniques have been deployed in various public-interest investigations, from election interference campaigns to public procurement scandals. In each case, link analysis added speed and rigor, allowing truth-seekers to derive meaning from mountains of disparate data and to present their findings in compelling visual ways. This analytical approach closely aligns with advanced SOCMINT methodologies, where cross-platform metadata, behavioral patterns, and digital footprint mapping enrich network analysis, making investigative journalism significantly more efficient and accurate.
To power these capabilities, modern link analysis platforms employ a suite of techniques and analytical methods. Some of the most important include:
Real-world data is messy—the same person might be referred to by different names, usernames, or IDs across sources. Entity resolution is the process of stitching together multiple records referring to the same real entity (person, company, etc.) so that they appear as a single node on the graph.
By unifying duplicate or alias records, investigators get a concise, accurate view of each entity’s involvement. Effective entity resolution uses matching algorithms and domain knowledge to merge these references, ensuring that connections aren’t missed or misattributed. This is foundational—it gives investigators confidence they’re connecting the right dots (and not accidentally connecting the wrong ones).
Once a network is built, algorithms can calculate centrality measures to quantify the importance of each node. Centrality metrics (like betweenness, degree, and closeness) reveal who the key connectors or influencers are in the network. In graph-based investigations, these metrics help answer questions like “Who is the most influential actor here? Who connects otherwise separate clusters?”.
As the FBI has noted, the centrality of nodes identifies the prominence of persons to the overall functioning of the network—their level of control, access to information, or broker role. Using centrality, an analyst might discover that a supposedly low-level individual is actually the hub linking multiple fraud cells, for instance. What’s more, graph algorithms can rank nodes by these measures automatically, giving investigators an objective way to prioritize targets or persons of interest.
Connections gain meaning from when interactions happen, so advanced tools incorporate time as a crucial dimension. Temporal analysis in link analysis means integrating timelines with network visualization to understand the sequence and timing of events. For example, with visual link analysis software, investigators can layer communications or transactions onto a timeline and see that suspicious payments clustered just before and after a specific event.
A combined link-and-timeline view lets one see cause-and-effect patterns—for example, a spike in calls between certain associates right after a major incident might hint at coordination. By revealing what happened when, temporal analysis provides context that purely static networks might miss. It helps distinguish coincidental connections from causally relevant ones, which is often vital in incident or conspiracy investigations. These temporal insights multiply in value when combined with cross-platform identity attribution, where OSINT analysts correlate usernames, aliases, communication timing, and behavioral cues to unify fragments of digital exhaust across multiple platforms.
Link analysis doesn’t begin and end with “who is connected to whom”. Enriching the nodes and links with additional attributes can add powerful context. This might include geolocation data, so that investigators can see connections on a map alongside the network, or sentiment or tone analysis, so links between people might be colored or weighted by whether their interaction was friendly, neutral, or adversarial.
The idea is to combine network topology with other analytics—for instance, merging a social network graph with phone metadata and keyword analysis could highlight not just that two suspects spoke, but that their conversation had a high anger sentiment or occurred near a particular location. Enrichment transforms a plain link graph into a rich knowledge graph, layering in the “who, what, where, when, and how” details that give a fuller investigative picture.
While link analysis is a powerful approach, using it effectively requires care. There are a few common pitfalls that investigators and analysts must watch out for:
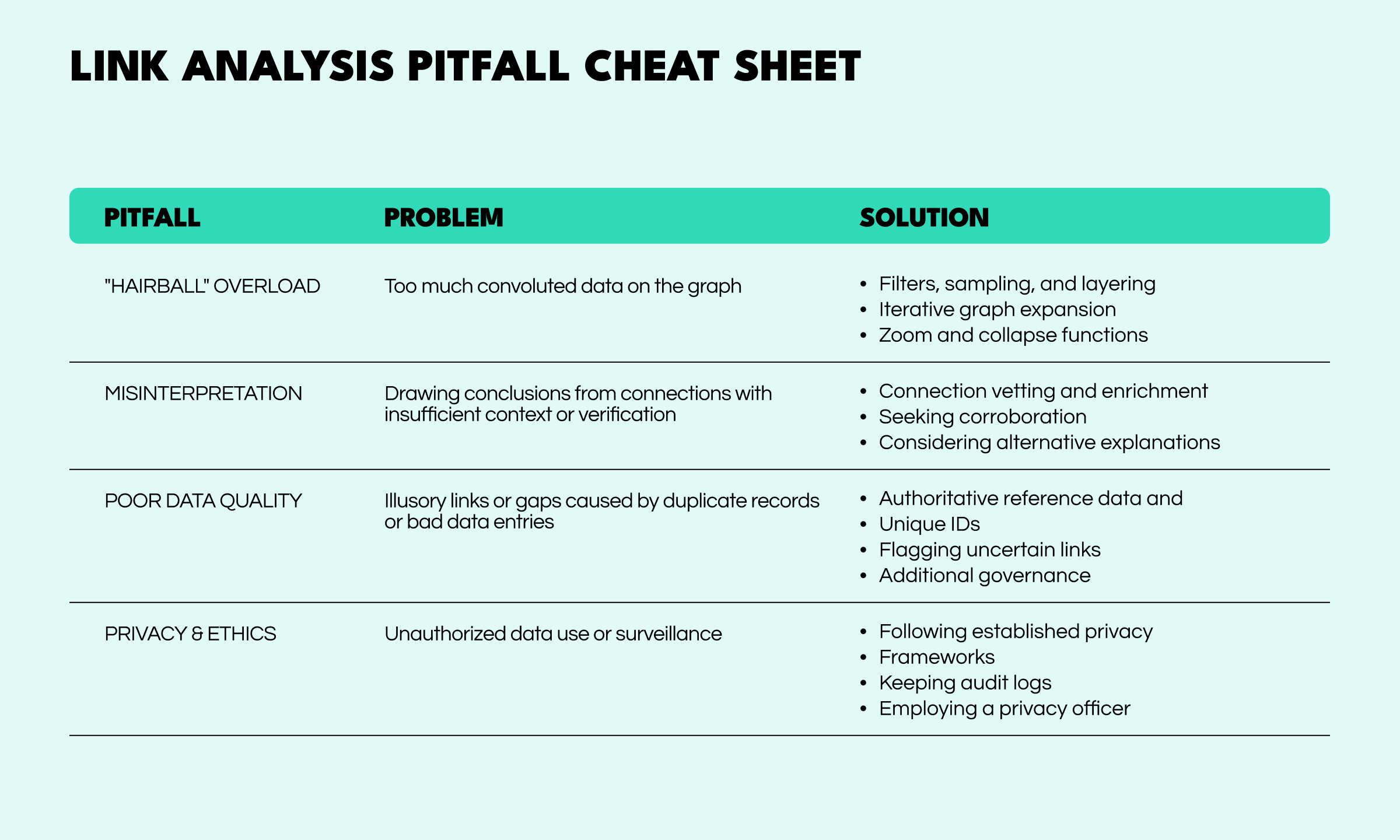
Sometimes less really is more. Cramming too many nodes and connections can turn the visualization into an indecipherable hairball. An overly cluttered network not only fails to yield insight, it can mislead by obscuring real structure in a sea of lines. The pitfall here is thinking that a giant graph is automatically insightful.
To avoid this, analysts should use filters, sampling, or layering to focus on the most pertinent connections. Good tools allow one to zoom into sub-networks of interest or collapse trivial nodes. In short, scope management is key: define the question or hypothesis, and include just the data needed to explore it. By iteratively expanding the graph rather than dumping everything at once, you can prevent information overload and extract meaningful signals from the noise.
A link in a network suggests a relationship, but correlation is not causation. One pitfall is reading too much into a connection without sufficient context or verification. For example, just because two people show up in the same social network doesn’t mean one is guilty by association—the link could be coincidental or indirect. Investigators must be careful not to let a pretty graph oversimplify reality or create false narratives.
The mitigation here is to vet and enrich connections: check what the link actually signifies (e.g. shared address vs. direct communication), seek corroborating evidence, and consider alternate explanations. Remember that a link graph is a tool to guide thinking, not an automatic truth. Maintaining healthy skepticism and continuously cross-referencing the network against source data can prevent analytical overreach.
Link analysis outputs are only as reliable as the underlying data. Errors like duplicate records, bad data entries, or mistaken entity matches can create illusory links or gaps. A common pitfall is when poor entity resolution causes one real person to appear as two separate nodes (missing a link), or conversely merges two different people into one (creating a link that shouldn’t exist).
To mitigate this, teams should invest time in data cleaning and entity resolution up front—ensuring names, dates, and identifiers are normalized and verified. We recommend: using authoritative reference data and unique IDs where possible, flagging uncertain links clearly on the graph rather than treating them as confirmed, and (for large projects) implementing a governance step where critical connections are double-checked. By acknowledging and addressing data imperfections, analysts can avoid chasing false leads and keep the network analysis credible.
As highlighted, the misuse of link analysis—such as including data one isn’t authorized to use, or surveilling people without cause—can lead to legal and ethical trouble. One pitfall is the “if we can connect it, we will” mentality. Investigators must remember that there are policy guardrails on using personal or sensitive data in analysis. Skirting these rules can taint an investigation or violate rights.
The mitigation is straightforward: follow established privacy frameworks and get necessary approvals when incorporating certain data. Anonymize personal data in early exploratory stages if possible, and reveal identities only when a clear need is established. Keep audit logs of how data is connected and accessed. Many agencies now have privacy officers or counsel involved in big data analytics who ensure that link analysis doesn’t cross lines. By building a culture of compliance and ethics, investigative teams can harness link analysis confidently, without casting doubt on their methods or findings.
Link analysis is continually evolving, and its future is poised to further empower investigators in various ways:
We are already seeing experimental use of graph neural networks and pattern-recognition algorithms that can trawl through connection data to suggest non-obvious links or predict emerging networks. For instance, advanced systems might learn the typical structure of a fraud ring or terror cell and then automatically flag networks in new data that fit those patterns.
As data volumes grow, such AI helpers will be essential in highlighting where humans should look next. Knowledge graph technologies are revolutionizing how AI systems understand complex relationships, making it easier for machines to traverse networks and gain insights. In practical terms, tomorrow’s investigative platforms might automatically identify clusters of concern or generate hypotheses for analysts to verify.
The Internet of Things, ubiquitous sensors, and ever more online data mean that investigative link mapping could soon incorporate streams like vehicle GPS data, communications metadata, and beyond. Investigators will not only be able to visualize past connections but also monitor networks as they evolve in real time—for example, watching the spread of a cyberattack through networks moment by moment, or updating a criminal association graph as new intelligence comes in. This dynamic, live aspect will turn link analysis graphs into continually updated “living” maps.
We can also anticipate more seamless user experiences and collaboration features. As the technology matures, even non-technical investigators will conduct link analysis through smart interfaces (for example, using natural language queries like “show me how Person A is connected to Company B and Event C”).
Visualization techniques will also improve, possibly incorporating 3D or augmented reality for very large networks to help teams literally see the forest for the trees. What’s more, collaborative graph databases in secure cloud environments will allow agencies across the world to contribute to the same network (with proper access controls), enhancing international cooperation against crimes that are increasingly transnational.
Lastly, the future of link analysis will grapple with the balance between power and responsibility. Expect continued refinements in privacy-preserving analytics, such as the ability to run pattern-matching on encrypted data or using differential privacy techniques to flag risks without exposing individuals unnecessarily. These innovations aim to reconcile the need to “connect the dots” with the mandate to do so ethically and legally.
Link analysis has become an indispensable pillar of modern investigative work—from police precincts and corporate fraud units to journalistic newsrooms. Its strength lies in making sense of complexity at speed, illuminating context and hidden links, and enabling collaborative problem-solving. As data continues to proliferate, the ability to connect disparate fragments of information into a coherent whole will only grow in importance.
By investing in advanced connection analysis capabilities (and using them wisely), investigators equip themselves with a powerful lens on the truth—one that turns sprawling data into actionable intelligence. The dots are out there, and they’re multiplying; connection analysis is how we will continue to join them, revealing the bigger picture lurking in the shadows.