Online Brand Protection and OSINT: Modern Digital Threats


Online brand protection has become a critical priority for organizations operating in digital environments. As brands expand across social media platforms, online marketplaces, app stores, and mobile apps, they are increasingly exposed to counterfeit goods, impersonation, and other digital threats that directly impact customer trust and revenue. What once relied on basic monitoring now requires a clearer understanding of how brand abuse moves across interconnected online ecosystems.
This article explores what online brand protection means today and why surface-level monitoring is no longer enough. By examining common digital brand threats alongside the OSINT methods used to address them, it shows how investigation-led approaches help organizations protect brand assets, enforce violations more effectively, and reduce long-term digital risks.
Online brand abuse rarely happens in isolation. Counterfeit sellers, impersonators, and infringing actors do not rely on a single platform or account. Instead, they distribute activity across online marketplaces, social media platforms, and app stores, reuse brand assets, and shift identities when enforcement actions occur.
This behavior exposes the limits of traditional brand protection services that focus primarily on monitoring. Alerts and takedowns can identify individual violations, but they do not explain how those violations are connected or who is behind them. Without that context, enforcement remains reactive and short-lived.
As a result:
Effective digital brand protection depends on investigation-led workflows that connect repeat violations, uncover patterns, and focus enforcement on the actors driving abuse—not just the listings they publish.
Digital brand threats are best understood as part of a broader ecosystem. Counterfeits, impersonation, trademark misuse, and dark web activity often reinforce one another. OSINT makes it possible to connect these signals and understand how abuse operates across platforms.
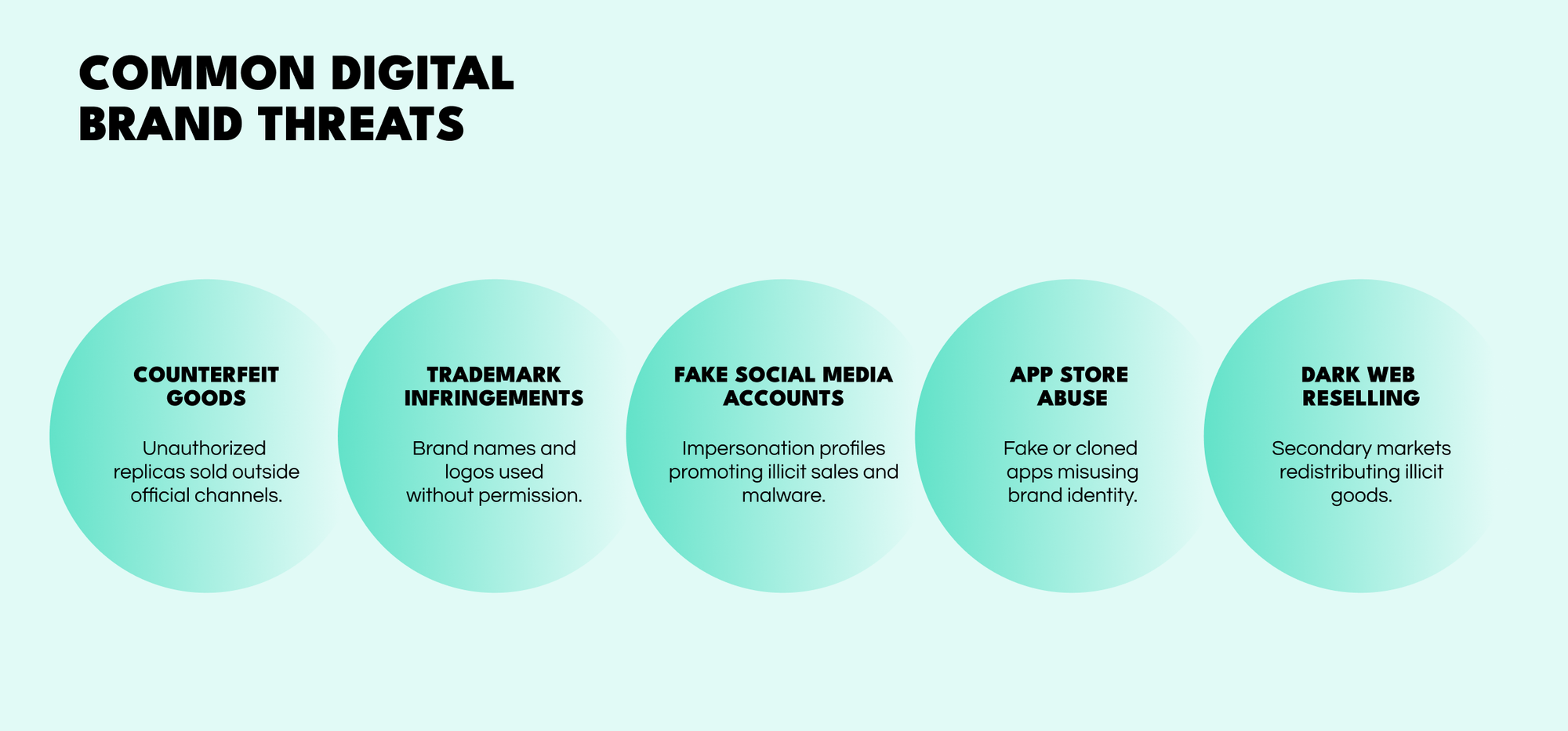
Across online marketplaces, social media platforms, and private groups, counterfeit products circulate under the appearance of legitimate goods. Sellers frequently reuse official images and descriptions, making replicas difficult for customers to distinguish from genuine products and eroding brand trust.
How OSINT helps: OSINT correlates listings across platforms using shared images, text patterns, seller behavior, and contact details, revealing distribution networks rather than isolated sellers.
Brand names, logos, and product identifiers are often reused without authorization in usernames, listings, ads, or domain names. This misuse blurs the line between official and unofficial channels, complicating enforcement efforts.
How OSINT helps: OSINT tracks repeated misuse of brand assets across platforms and links infringing entities that monitoring tools typically treat as separate incidents.
On social media platforms, impersonation profiles pose as brands, resellers, or customer support. These accounts promote counterfeit goods, redirect customers to fraudulent channels, or disappear after collecting payments.
How OSINT helps: Behavioral patterns, reused content, and shared infrastructure allow investigators to link accounts and identify repeat impersonators even after takedowns.
Within app stores, cloned or fake mobile applications misuse brand identity to distribute counterfeit goods, redirect payments, or harvest user credentials. This form of abuse exposes users to both financial loss and security risks.
How OSINT helps: OSINT connects app listings to developer metadata, external promotion channels, and associated social accounts, exposing abuse that spans both app stores and social platforms.
Beyond public platforms, secondary markets redistribute counterfeit goods, stolen brand assets, and supplier information. Activity in these environments often supports larger operations that later reappear on surface platforms.
How OSINT helps: OSINT links dark web activity to surface-web listings, social media profiles, and logistics indicators, supporting escalation and long-term enforcement.
Online brand protection is no longer just a monitoring challenge—it is an investigative one. Digital threats are coordinated, adaptive, and persistent, making alerts and takedowns insufficient on their own.
By applying OSINT, brands gain visibility into how abuse connects across platforms, who is responsible for repeat violations, and where enforcement efforts can have lasting impact. Investigation-led brand protection replaces endless reaction with clarity, continuity, and evidence.
Online brand protection involves identifying, investigating, and addressing misuse of brand assets across digital channels, including social media platforms, online marketplaces, app stores, and the dark web.
Monitoring detects individual violations, but it does not explain how they are connected or who is behind them. Without investigation, takedowns often lead to repeat abuse under new accounts.
OSINT connects publicly available data—accounts, listings, images, and contact details—to reveal patterns and actors behind digital threats, enabling stronger and more durable enforcement.
Key threats include counterfeit goods, trademark infringements, fake social media accounts, app store abuse, and dark web reselling, all of which often overlap.
Organizations should prioritize investigation capabilities, evidence preservation, continuous monitoring, and the ability to connect abuse across platforms rather than treating violations in isolation.
Want to protect your brand against coordinated digital abuse—not just isolated violations? Book a personalized demo to see how SL Crimewall supports investigation-led online brand protection by connecting counterfeit activity, impersonation, trademark misuse, and dark web signals into one unified investigative environment.