OSINT FAQ: Common Questions about Open-Source Intelligence, Answered


The world of open-source intelligence is sophisticated and consists of many tiny details that form a complete puzzle. And despite the growing popularity of OSINT solutions and the demand among cybersecurity experts and beginners, there are still a lot of questions about the topic. So, it's time to bridge the gap.
In this OSINT FAQ, we shed some light on the sphere and answer the most commonly asked questions we have encountered through the years in the open-source intelligence field. We covered everything from the legitimacy of open data and the first steps in investigations to deanonymization on the Dark Web and revealing hidden information. All in a short, digestible format.
So, let’s get to the point!
Yes, it is. Open-source intelligence (OSINT) is a process of collecting, extracting, and analyzing publicly available information for various investigative goals (we covered the term in detail in our article 'What is OSINT').
Let’s quickly clarify what an open source is to avoid any confusion. If it’s possible to access any piece of information without a login (meaning anyone online can look at it), it’s in the domain of OSINT. To give more context, the data gathered by open-source intelligence tools are shared mainly by the users or organizations without force.
Statistics speak louder than words. According to DOMO’s annual report, people generate an enormous amount of data per minute, including 500 hours of uploaded videos on YouTube, 347K tweets on Twitter, 2.43M snaps on Snapchat, and more. Considering that users spend, on average, 147 minutes a day on social media platforms, these numbers are not surprising. Another fact is that more and more businesses are becoming transparent and sharing their data online. As a result, the scope of publicly available information for OSINT investigations is snowballing.
In a nutshell, it saves time and lets you focus on what’s really important: decision-making rather than data collecting. Think of it this way: every online activity, from posting a tweet or updating a profile on LinkedIn to leaving a review on Tripadvisor or Google, creates a digital trace of a specific person.
In such circumstances, manually collecting all the information needed to find a clue can be challenging and time-consuming. With AI-powered OSINT tools, scanning and analyzing vast amounts of data from open sources in real time becomes possible. It helps to expand the scope of research and verify hypotheses at speed as well as to boost the progress of the whole investigation.
As in all new activities, mastering an unfamiliar instrument might take a while and highly depends on a specific person. The good news is you’re not alone in this.
One of the biggest obstacles to learning is your existing skillset and know-how. If you have no prior background in open-source intelligence, the interface may initially seem complex (this is especially true for intelligence software). But remember the main rule— practice makes perfect. Learning about OSINT basics (no surprise there) and trying them out within the tool’s interface is essential to drive progress. The more you use the open-source intelligence tool, the better you’ll get at using it.
Number one is an analytical mindset. Namely, investigators must be good at critical thinking, establishing relationships, and drawing conclusions from available data. Other vital skills include proficiency in online research, information gathering, and data analysis.
Sure, having a STEM (science, technology, engineering, mathematics) background can be handy, but it’s not a requirement. Besides the applied skills, working in a team and effectively communicating are important. Still, the norm in each case can be different. Keeping that in mind, it’s fair to say that another valuable skill is adaptability.
You just need OSINT software and primary input data to get you going.
You can start investigating once you have an installed tool like SL Professional. The first step is selecting a subject to examine. While you can use various data inputs in the software, a simple Google search is a straightforward way to begin. The great thing is that many open-source intelligence tools have built-in search engine functionality, so you can start from within the interface without needing to navigate elsewhere.
Let’s say you want to collect all publicly available data about yourself. All it takes is running a search by your name. You can find further information from this entity, such as a phone number, email address, social media profiles, public reviews, etc. All in all, getting your entire digital footprint and publicly available information requires only a few clicks.
Yes. Those are excellent starting points, as email addresses and phone numbers are generally required when signing up for social platforms like LinkedIn or Twitter. Using this prerequisite to your advantage, you can get additional information about your subject with just a bit of data.
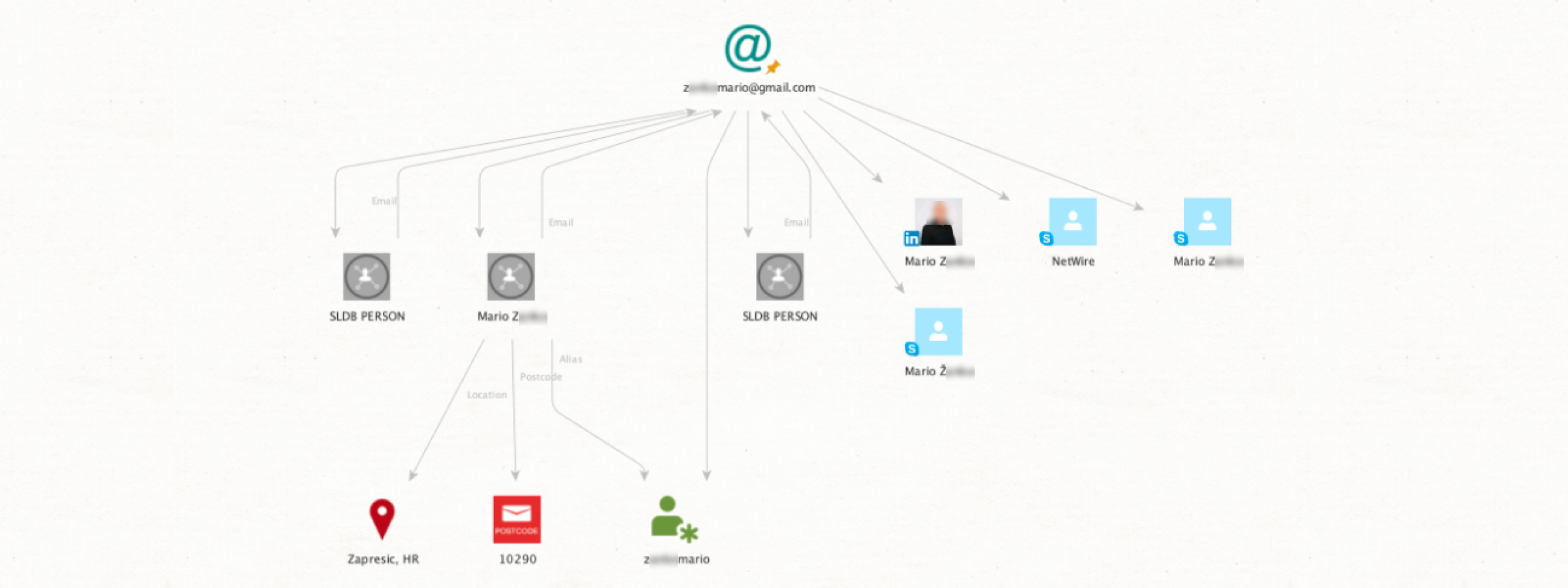
Let’s put things into practice with an example using SL Professional. Our input is an email address (zankomario) linked to a Trojan virus called NetWire. We use the [Skype] Get Profile transform, which provides the associated account (labeled NetWire). Next, the [LinkedIn] Get Profile transform reveals that the subject's registered location is Zapresic in Croatia. Finally, the [SL ISE] Search yields three entities with the same postal code in Zapresic. Furthermore, the alias from the last transform matches our original email address. This provides enough data to investigate a suspect's social media accounts.
First things first, it’s improbable that a suspect won’t have any online social presence. In fact, according to a recent report, Gen Z and Millenials hold around 8.5 social media accounts across various platforms. However, closed profiles are a strong possibility. But it’s still feasible to investigate them. Let’s see how.
Option 1
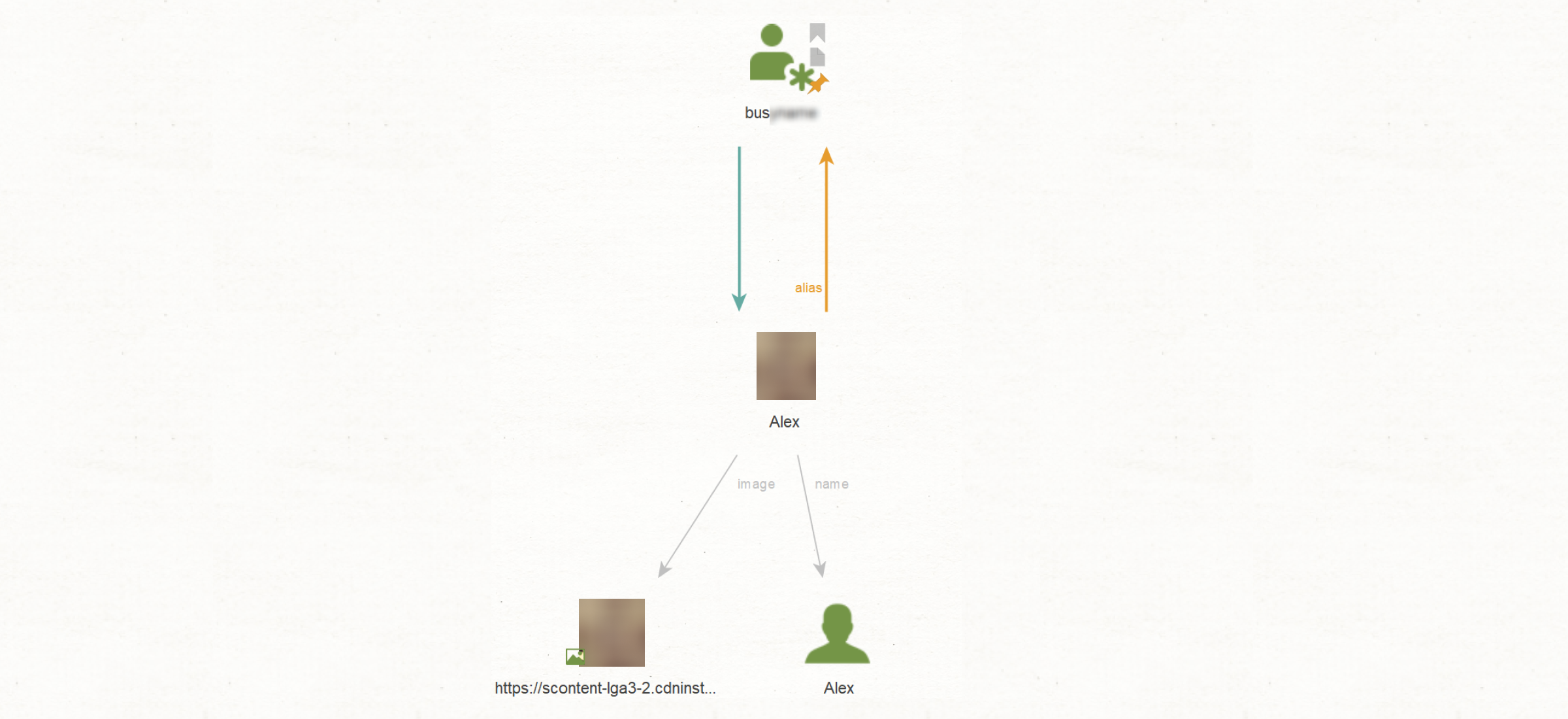
Many OSINT tools (such as SL Professional) feature powerful facial recognition capabilities that allow you to find additional information on a suspect. Let's say we have just an alias. From this input, we can find a person on different social media. As illustrated in the example below, we found one closed profile. It may seem like a problem, but actually, it's not.
We run a group search 'Profile in Other Networks and Messengers' to extend our research. It allows us to get a user's profile on another social media and messengers with a similar photo and name. Then we apply [Convert] To Entities From Profile, and we now have a suspect's profile picture and name. With this information, it's now possible to significantly enrich further investigation and find other needed details.
Option 2
In an alternative approach, we are facing a challenge: we only have our subject's alias and want to gather more information about them. We use the Get Profiles transform to retrieve the associated social media account. Unfortunately, the account is closed, restricting our access. We use the Search by Face and Name transform to gather additional data. Finally, we apply the [LinkedIn] Search by Face and Name transform, which gives us the person’s professional history through their LinkedIn account.
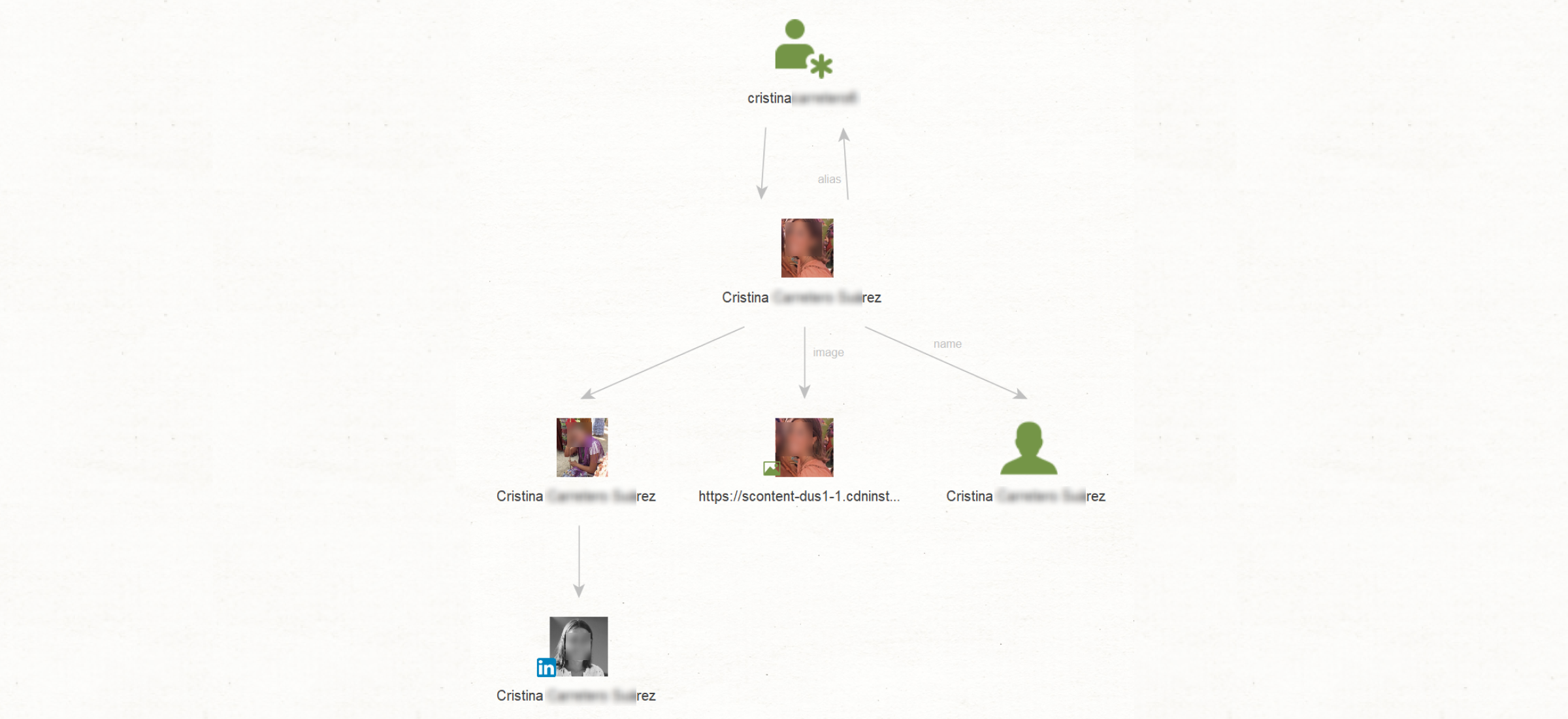
By employing these transforms, we could use a closed profile to discover additional social media accounts and retrieve details regarding the subject's location and employment history.
Sure. There are a few ways of doing that.
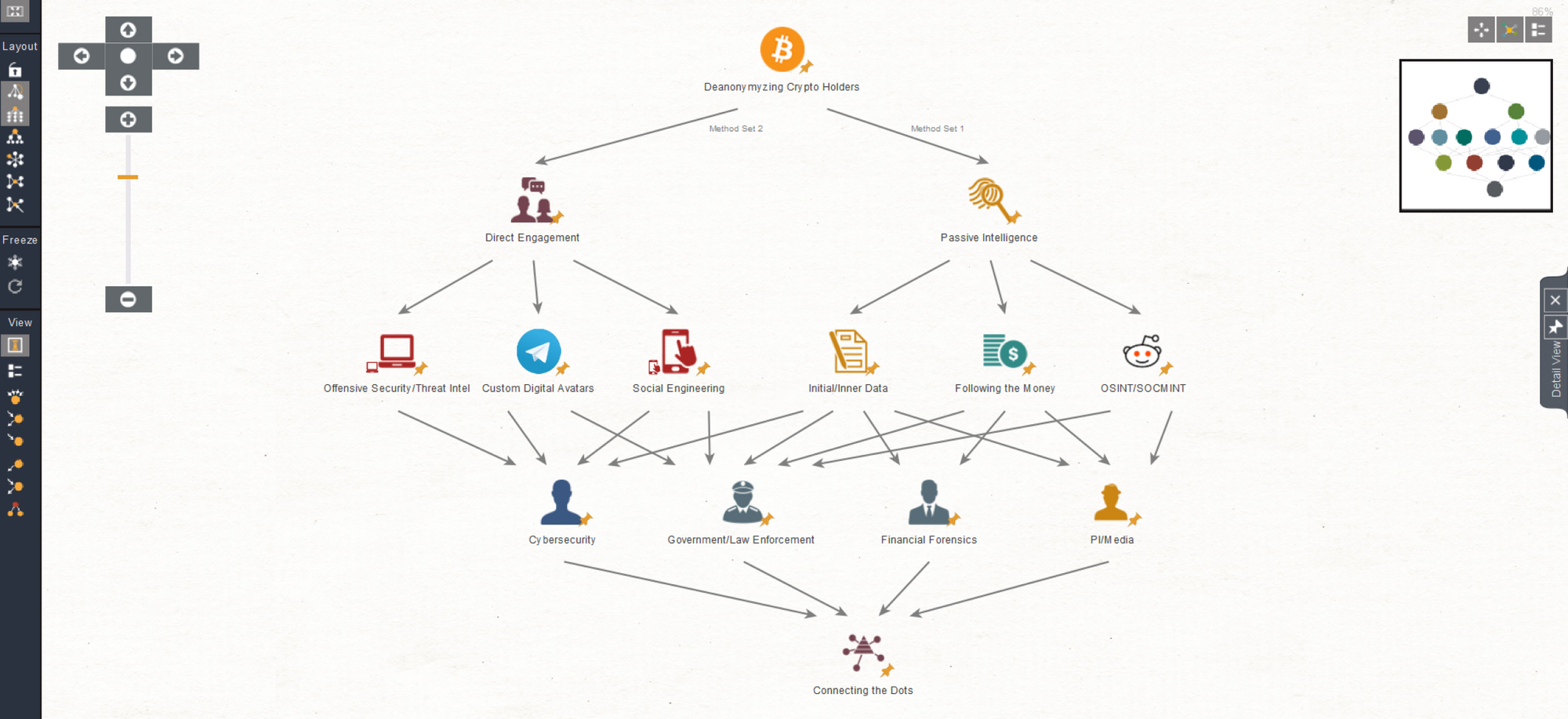
Passive Intelligence, or the traditional “follow the money” approach. It combines social media intelligence and financial data sources. The process begins with investigators tracing transactions and linking them to bank accounts. They can then use Cryptocurrency Pack transforms to include additional parameters in the search, such as location or social media data. Through cross-referencing results, investigators can reveal the identity of the wallet owner.
Direct Engagement requires more social engineering. Investigators create fictitious identities (known as 'sock puppets') and adopt a proactive approach. The specialist engages the wallet owner through a sock puppet account. Agents can gain trust and extract actionable information by interacting directly with the suspect.
As a result, social media plays a very active role in deanonymization because crypto wallets are usually directly tied to specific accounts. For example, Twitter has a very active non-fungible token (NFT) community, and user profiles display the crypto wallet addresses. Such open information can become valuable input data during investigations.
Yes, it is. This process comes down to pattern detection and behavior analysis. But first, you need to understand the purpose of the fake profiles.
For example, troll farms (groups of internet trolls with a political agenda) create dummy accounts for online social or political influence. Usually, these phony accounts will repost each other’s content to fabricate a sense of credibility. This means it’s possible to scrutinize the text to identify similarities between writing styles and word choices. It can quickly unravel the whole web and reveal connections between accounts, emails, and phone numbers. Such links can point to the real identities of fake profile holders.
It can be tricky, but pulling this off is still possible. The Dark Web has around 2.5M daily active users. As this shady part of the Internet is usually used for criminal purposes, people tend to be paranoid about security and the threat of deanonymization. However, investigators can track specific footprints, no matter the situation.
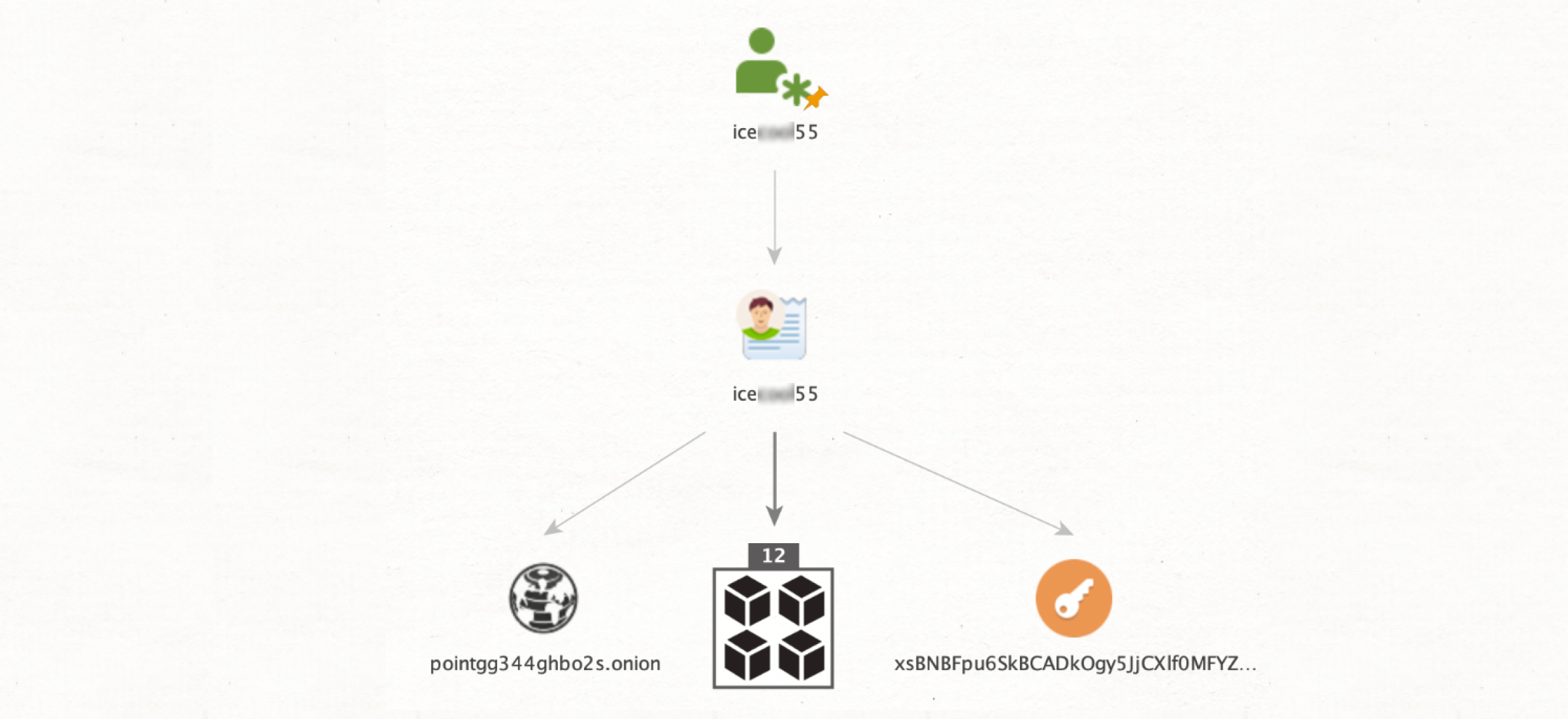
Let’s see a real example. Imagine we found a user selling drugs through a darknet marketplace. All we have is the alias 'icecool55'. We run a [Darknet] Search Users transform to see if any users match this handle. Through [Convert] to Darknet Domain we get a result that links this user to a Dark Web marketplace. We extract the PGP key with [Convert] to PGP Open Key transform. From there, we finally apply [Darknet] Search Products to find the locations they shipped drugs to, giving us valuable insight into the criminal operation.
It all comes down to discovering reliable links. Social media is an excellent indicator for this type of investigation.
Let’s say we have two individuals and want to see if they are connected. First, we need to check if they have any online association with one another. There are several ways of verifying links, such as interactions (reposting content, likes, tags, etc.), location proximity, or overlaps in their social or professional circles. If one or more of these is true, there’s a strong chance that the individuals are connected somehow. In a real investigation, social media is one of the first places specialists look at to get an idea of how people are connected.
There are several applications.
A major benefit OSINT provides to businesses is brand security. According to Mimecast, corporate impersonation cases increased by 170% in 2021. This presents a serious challenge as such cases can easily result in reputational damage or threaten the firm’s cybersecurity through phishing scams.
However, all is not lost. Specialists can use open-source intelligence to scan social media and the web to find posts and websites using your company’s name, trademark, or aesthetic style without permission. At this point, a detailed digital footprint of the fraudsters can be created by following phone numbers, email addresses, and aliases. Finally, investigators can uncover the identities and motives (displeased ex-employees, e-commerce fraud, etc.) of the threat actors by analyzing the online traces revealed throughout the investigation.
The other approach is to test out an organization’s security proactively. This is called penetration testing (pen test), involving specialists trying to break into their own systems. OSINT can be very valuable in this area because it can help identify weaknesses within the infrastructure. Pen tests should be conducted regularly to ensure no vulnerabilities remain in security structures.
OSINT is a great addition to any investigation because it doesn’t clash with established frameworks. Open-source intelligence is there to enrich the existing data by expanding the scope of research. The result is a more comprehensive view of the whole case, which in a digitized world is very valuable.
For example, a Law Enforcement Agency (LEA) is investigating a suspect tied to narcotics. The officers might be looking for information in the field, but an OSINT specialist can take the suspect’s name and start looking into social media. Through online friends lists, analysts can narrow down potential leads that can help the squad by giving them valuable information such as addresses, meeting spots, and even other persons of interest. Such insights can impact the decision-making process during investigations and potentially save the whole team plenty of time by prioritizing actionable leads.
And that’s a wrap on our OSINT FAQ. We hope we shed some light on your burning questions about open-source intelligence and you found new ideas for implementing the solution to speed up your investigations. In the meantime, stay tuned for more articles, and keep investigating!