OSINT in Cyber Threat Intelligence


Cyber threat intelligence (CTI) exists to turn technical security signals into meaningful understanding of who is operating, how attacks evolve, and where real risk persists over time. Modern environments generate massive volumes of alerts and indicators, but detection alone rarely explains intent, coordination, or continuity. Without that context, organizations respond to incidents in isolation and struggle to build durable defensive insight.
In this article, we examine how open-source intelligence (OSINT) fills this gap by connecting fragmented technical signals to public infrastructure, behavioral patterns, and actor activity. This approach enables investigations to move beyond isolated alerts toward attribution, continuity, and informed decision-making.
Most security systems generate enormous volumes of alerts, logs, and indicators. An indicator might be a suspicious IP address, a malicious file hash, or a domain name linked to phishing. These signals confirm that something happened, but they rarely explain why it happened or who was responsible.
For example, knowing that an IP address delivered malware does not reveal who owns that server, whether it has been used in previous attacks, or if it belongs to a larger campaign. Each signal exists in isolation unless additional context is added.
Without external visibility, investigations remain fragmented and repetitive. Teams spend time validating the same indicators again and again, often without building a broader picture of attacker behavior. This is the gap OSINT solves.
By analyzing the public footprint of attacker operations, such as reused infrastructure, domain registrations, leaked tools, and online activity, intelligence teams can move from reactive indicator handling toward understanding actors and long-term patterns.
Once teams gain external visibility, they can connect technical telemetry, which shows what touches their systems, with OSINT, which shows what exists outside them. This correlation allows analysts to see how campaigns evolve and how identities persist even when technical assets change.
Public sources often reveal:
On their own, these signals may seem insignificant. When teams correlate them over time, they create a clearer picture of how an operation functions and who may be behind it.
To prevent intelligence from becoming disorganized or outdated, CTI follows a structured lifecycle. This cycle turns scattered data into reliable understanding. OSINT strengthens every stage of this process.
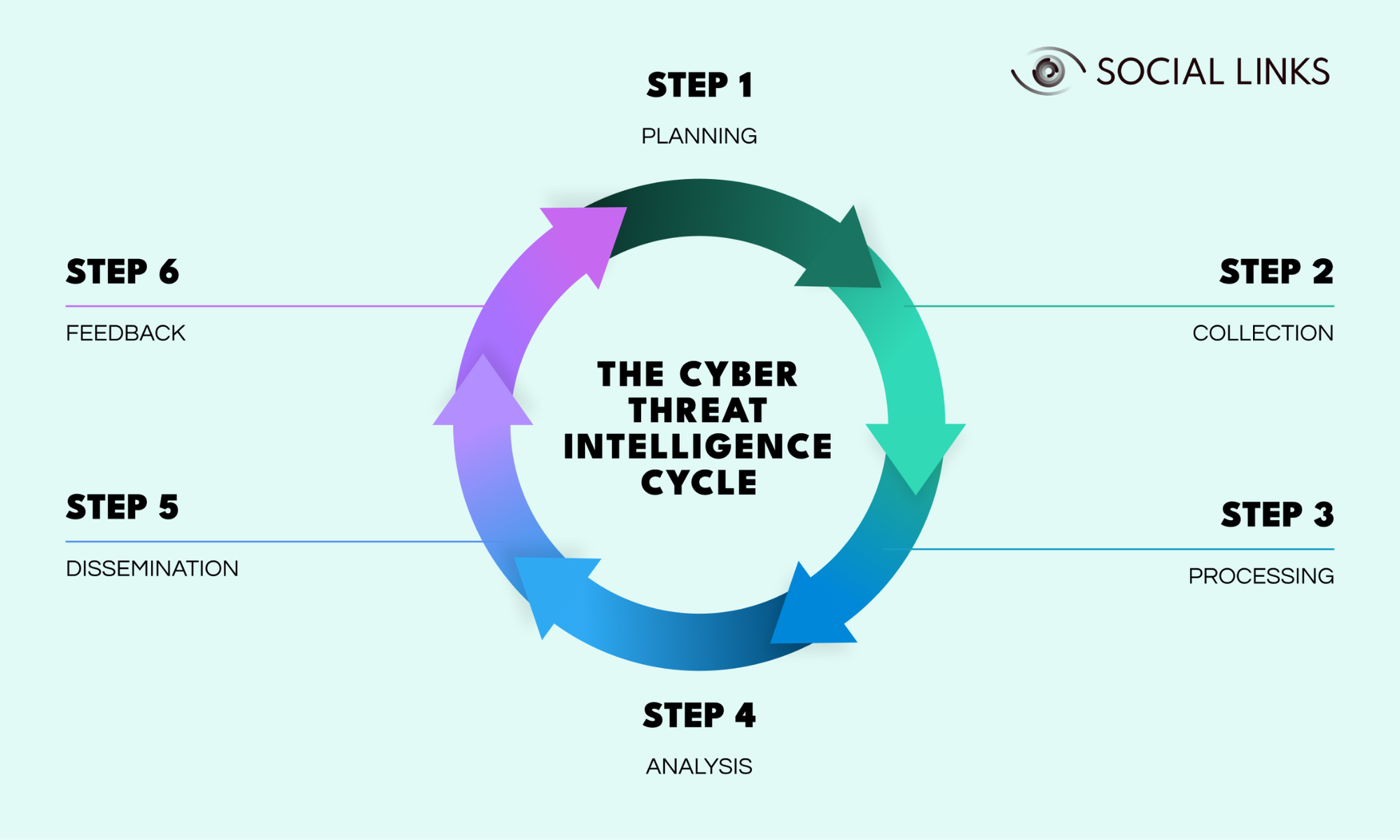
This cycle ensures that OSINT does not become disconnected from operational needs and that intelligence remains relevant and actionable.
As automation increases the number of attacks, purely technical monitoring struggles to maintain continuity. Attackers frequently rotate IP addresses, domains, and tools. This makes it difficult to track activity using technical indicators alone.
OSINT counterbalances this churn by following the human and organizational layer that tends to persist even when infrastructure changes. People reuse language, tools, networks, and more. These patterns are often visible in public data.
This allows teams to:
Cyber threat intelligence is effective only when it connects technical signals to people, behavior, and intent. OSINT provides the visibility needed to make those connections.
When embedded throughout the intelligence lifecycle, OSINT transforms scattered data into structured understanding. This enables stronger attribution, better prioritization, and more resilient security decisions.
Alerts show that something happened, such as a suspicious connection or a malicious file. They do not explain who controls the activity, how it relates to previous attacks, or whether it represents an ongoing risk. Without external context, investigations remain fragmented and reactive.
OSINT draws from publicly available sources such as websites, domain records, technical metadata, online forums, code repositories, and social platforms. These sources often reveal infrastructure reuse, operator behavior, and coordination patterns that do not appear in internal security logs.
OSINT strengthens every stage of the intelligence cycle by expanding collection, improving validation during analysis, and enriching reporting with context. This keeps intelligence aligned with real-world activity instead of becoming a static list of indicators.
By linking technical signals to known behavior, infrastructure history, and campaign patterns, OSINT helps distinguish meaningful threats from background noise. Teams can focus resources on activity that shows continuity or intent rather than reacting equally to every alert.
As attackers rotate infrastructure and automate attacks, technical indicators change rapidly. OSINT tracks the human and operational patterns that persist over time, allowing intelligence teams to maintain continuity and long-term visibility.
Want to strengthen cyber threat intelligence with real-world context and attribution? Book a personalized demo to see how SL Crimewall helps teams correlate open-source intelligence with technical signals, map actor infrastructure and behavior, and accelerate investigations within a unified intelligence environment.