OSINT Investigations: Tools, Techniques, and Use Cases


Open-source intelligence has become a critical part of modern security work. As online footprints expand across social platforms, forums, infrastructures, and public records, organizations rely on OSINT to make informed decisions—from fraud detection and cybersecurity to due diligence, threat monitoring, and corporate protection.
This article breaks down how OSINT investigations work in practice, from the tools and techniques analysts rely on to the investigative approaches that transform open data into actionable intelligence. Whether you’re an experienced OSINT investigator or a security professional strengthening your investigative workflows, this guide will give you a practical, real-world understanding of the topic.
OSINT refers to the collection and analysis of publicly available data—social media content, search engines, public records, leaked datasets, infrastructure data, and even elements of the Dark Web. What makes OSINT powerful is that, when structured properly, it turns fragmented information into actionable intelligence that can support security operations, compliance checks, incident response, or long-term monitoring.
In real-world investigations, OSINT helps teams:
Unlike closed intelligence sources, OSINT is transparent, scalable, and fast, making it an indispensable component of modern intelligence frameworks.
A strong investigation follows a clear workflow in which goals are defined, data is collected, datasets are expanded through pivoting, and connections are analyzed. Below, we outline each stage in practical terms.
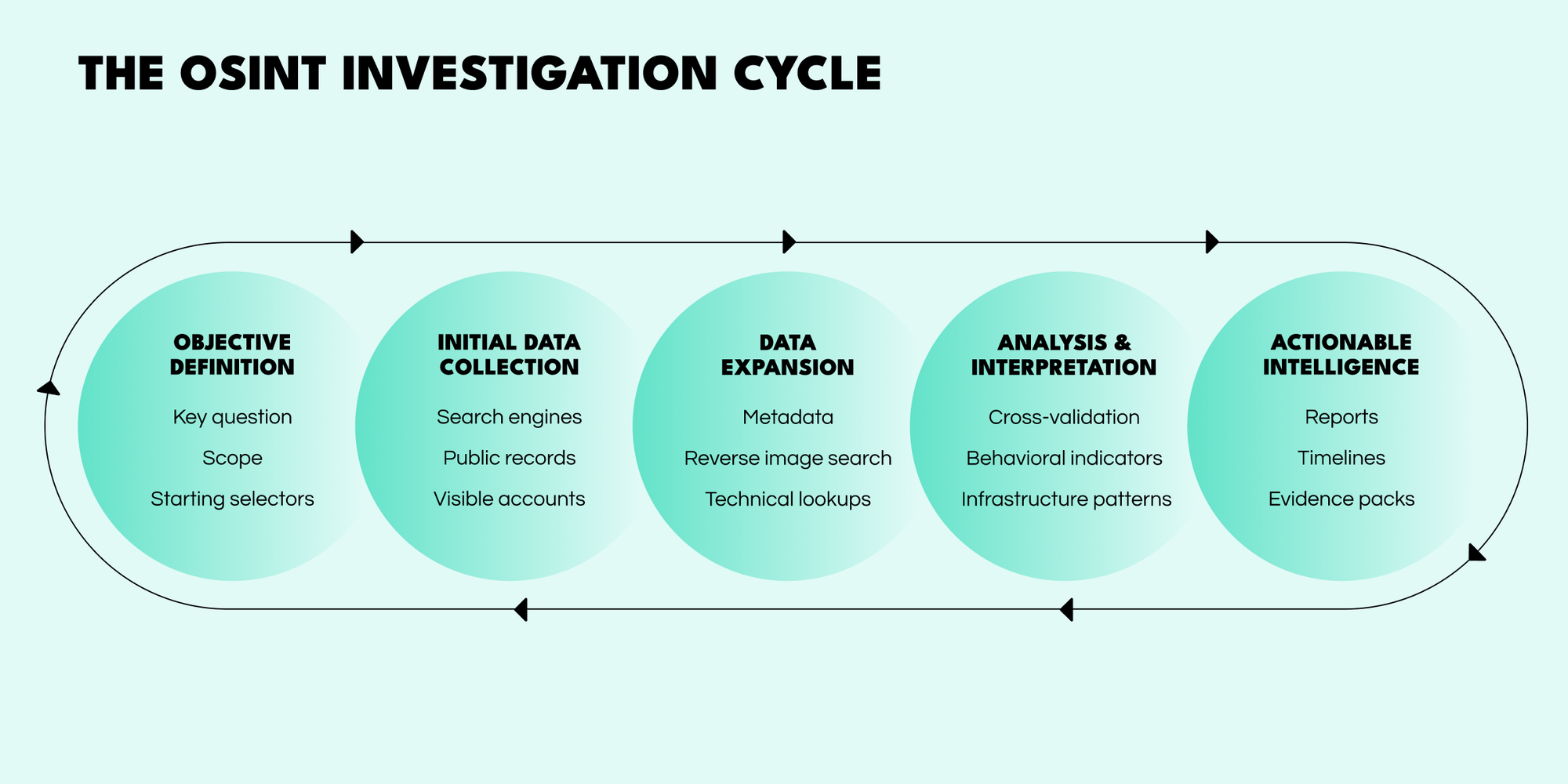
Every investigation begins with intent. Rather than collecting data blindly, analysts start by establishing one clear question the investigation must answer. This foundational step prevents scope creep and ensures the workflow remains efficient.
Common OSINT objectives:
A well-defined objective determines which sources matter, which do not, and which OSINT tools will meaningfully advance the case.
With the investigative target set, analysts gather initial selectors—the anchor data points that guide the rest of the investigation. These selectors may include identifiers like email addresses, usernames, domains, phone numbers, social media handles, IP ranges, or corporate records.
Typical OSINT collection surfaces:
This stage is not about collecting “everything”—it’s about identifying the right entry points into the broader investigation.
Once anchor selectors are identified, analysts begin pivoting—using each data point to discover new, related information. This is where OSINT tools and techniques enrich the investigation, revealing networks, hidden relationships, and unexpected connections.
High-impact techniques:
This phase turns isolated clues into a structured dataset that can be meaningfully analyzed.
The analysis phase is where raw data becomes insight. Here, analysts evaluate the credibility, context, and relationships within the dataset, ensuring that conclusions are evidence-based and defensible.
Core analytical tasks:
This stage often loops back into Stage three, because new clues may require additional pivots or deeper exploration.
The final step in the cycle is that of transforming analysis into a digestible product—one aligned with the needs of HR, legal, cybersecurity, fraud teams, or executive decision-makers.
Typical OSINT intelligence outputs:
The goal here is not volume—it’s clarity. Decision-makers must be able to act on the insights without needing to review raw data.
OSINT supports a broad range of industries and operational needs. Below are the most common scenarios where businesses apply open-source intelligence.
Fraudsters rarely operate in a vacuum—OSINT exposes the reused emails, recycled usernames, shared devices, duplicate images, and behavioral fingerprints that tie separate scams together. Instead of treating each incident as isolated, analysts can uncover the broader network, identify the operators behind it, and trace how fraudulent campaigns evolve across platforms.
OSINT helps uncover:
Correlation of usernames, emails, and activity footprints is especially effective here.
When an intrusion occurs, OSINT fills in the external blind spots that internal logs can’t—such as attacker infrastructure, leaked credentials, chatter on Dark Web forums, or previously unknown IP clusters. This outside-in perspective often reveals the whys and hows behind an attack, helping security teams enrich IOCs (Indicators of Compromise), uncover attribution clues, and anticipate follow-up activity.
Security professionals rely on OSINT to:
OSINT provides context that internal logs alone can’t.
Corporate structures can hide risk behind layers of subsidiaries, offshore entities, or dormant companies—OSINT cuts through that opacity. By aggregating state records, historical filings, executive footprints, sanctions lists, and web infrastructure links, investigators can uncover relationships that would never appear in a standard database check.
Investigators look for:
OSINT supports both compliance and strategic decision-making.
People leave traces across the internet—OSINT connects them. Cross-platform usernames, old forum posts, résumé claims, public records, metadata, and behavioral patterns form a digital footprint that allows investigators to confirm identity, detect inconsistencies, or spot risk indicators long before a decision is made.
Analysts investigate:
Cross-platform matching is particularly powerful in these use cases.
OSINT investigations succeed when tools, techniques, and investigative approaches work together in a disciplined, repeatable workflow. Rather than collecting data for its own sake, analysts use OSINT to create clarity—mapping identities, revealing infrastructure, exposing fraud networks, and identifying risks that traditional methods often miss. The real value lies not in volume but in transforming the right data points into a coherent intelligence picture.
As digital ecosystems expand across social platforms, decentralized networks, and distributed infrastructure, organizations that invest in strong OSINT capabilities—supported by reliable tools, rigorous methodology, and intelligence-driven analysis—gain a measurable advantage. In an era where nearly every action leaves a trace, OSINT provides the framework to detect threats earlier, respond faster, and make confident decisions based on verifiable evidence.
An OSINT investigation is a structured process for collecting and analyzing publicly available data—from social media profiles and clearnet content to domains, records, and darknet sources—to produce actionable intelligence. They help investigators map identities, uncover risks, and understand digital behavior across multiple surfaces.
Analysts rely on a mix of tools for Surface Web discovery, social media intelligence, infrastructure analysis, Dark Web monitoring, breach-data correlation, and link analysis. These OSINT tools help collect data, expand selectors, and visualize relationships between people, organizations, and digital assets.
Core OSINT techniques include pivoting, metadata extraction, reverse image search, Google Dorking, username correlation, breach-data matching, graph modeling, and more. These techniques allow investigators to expand datasets, validate identities, and uncover relationships that are not immediately visible.
Approaches such as selector-driven investigation, network mapping, infrastructure-first analysis, and behavioral pattern analysis shape how data is interpreted. These frameworks help analysts avoid noise, prioritize high-confidence connections, and create defensible intelligence outputs.
Organizations use OSINT for fraud detection, cybersecurity enrichment, due diligence, insider-risk monitoring, identity verification, and corporate intelligence. OSINT provides visibility into digital footprints and relationships that complement internal logs and proprietary databases.
Want to enhance your OSINT investigations with unified data collection, intelligent pivots, and powerful link analysis? Book a personalized demo and see how SL Crimewall brings every stage of the investigative workflow into a single, intuitive platform.