Social Links’ OSINT Landscape for 2022


Open-source intelligence technologies have grown into something far more wide-reaching than a collection of niche applications. Today, they are garnering tremendous attention, not only among security specialists and investigators but across the business sector as well. The handful of companies who used to dominate the OSINT market in its early days can now boast a tenfold market capitalization.
The role of OSINT continues to grow at breakneck speed. Spiraling digital threats have made cyber security solutions a corporate necessity, while issues of national and social security rely heavily on open-source intelligence. To ignore these technologies and techniques is to miss opportunities for streamlining processes, as well as leaving yourself vulnerable to threats such as data breaches.
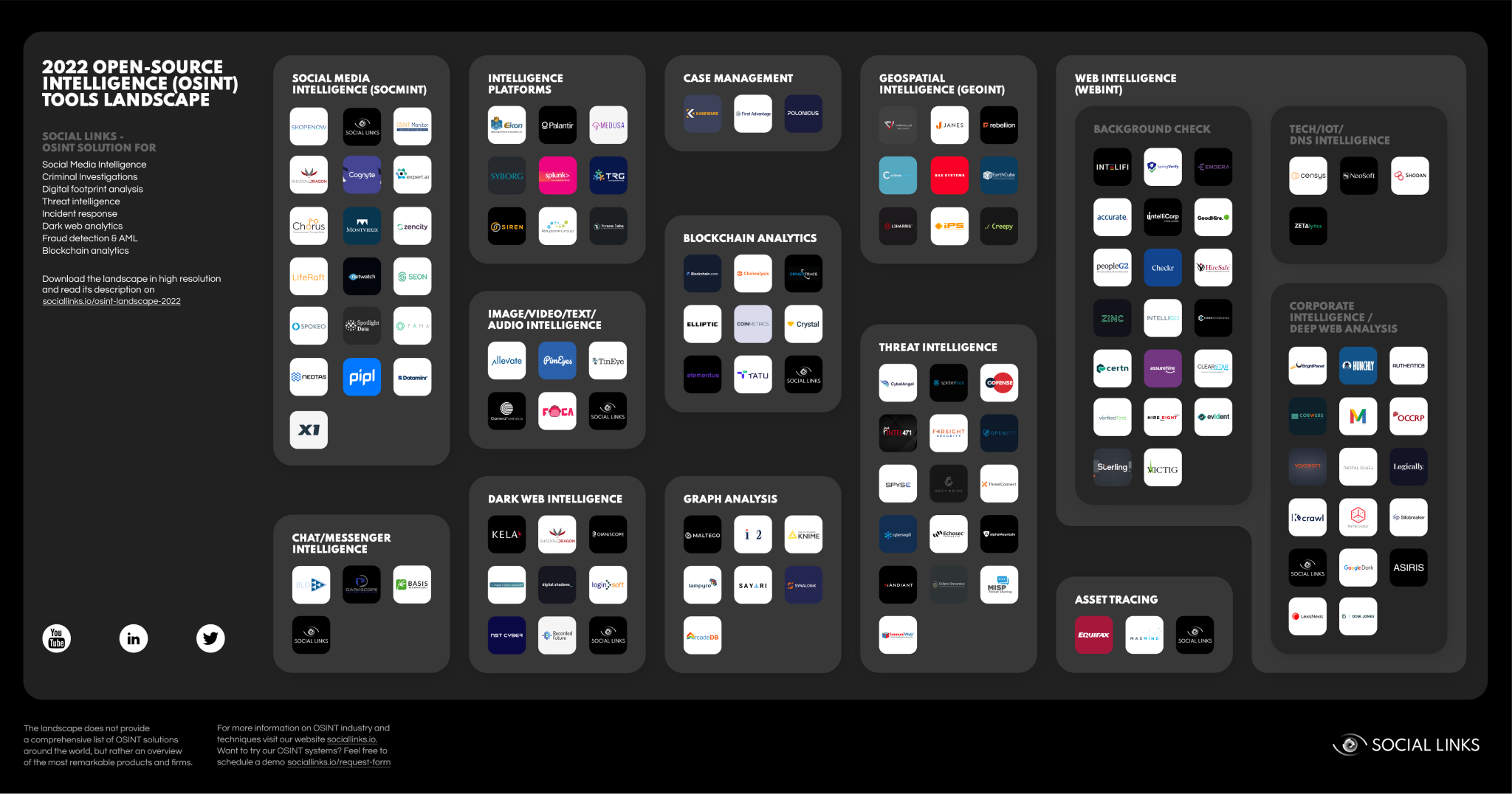
To help establish a picture of the OSINT landscape in 2022, The Social Links team has mapped out the various components that comprise this emergent sphere, complete with our commentary on the multiple ways open-source intelligence tools can be applied in bolstering security across sectors. With over 120 solutions out there, guidance is handy in understanding the lay of the land. So let’s get into the details!
Disclaimer: This guide is not intended to be exhaustive and certainly does not cover all products on the market. Instead, we have made a selection which we think gives a serviceable description of the current OSINT sphere. While we have completed our picture with companies that excel in the given area, the versatile application of open-source technologies means that one product may appear in various domains.
Data analysis is a crucial factor for maintaining both national and commercial security, and thus the widespread adoption of OSINT reflects advances in the intelligence sphere at large. Tools for gathering intel are now available to private users, and not the exclusive domain of governments and law enforcement agencies. As we explore below, OSINT has become central in countering the prominent challenges of the digital age, as well as providing remarkable opportunities.
Our 2022 OSINT product map provides a snapshot of the technological ecosystem underpinning online intelligence. This spans from simple background checking tools to sophisticated, multi-purpose data gathering and analysis platforms.
As a ‘field’ or ‘sphere’, the concept of OSINT might feel a little abstract. So, to illustrate the needs and purposes of open-source intelligence tools, here are three prominent areas in which such technologies are changing the game right now.
The Dark Web is widely known to have become host to an array of black markets, where purveyors of drugs, weaponry, and illegal services can plug their trade. With such marketplaces gaining ever more custom, products which can monitor such activities are increasingly in demand. And as LEAs ramp up their surveillance of the Dark Web, integrated OSINT solutions are providing the technical tools they require.
However, countering anonymity is a huge and ongoing task because criminal actors find ever more sophisticated ways to cloak themselves and erase their tracks. While popular protocols such as Onion routing are dying out due to the pervasive powers of modern OSINT tools, newer, more advanced techniques are entering the game.
As leading banks start to trade Bitcoin futures and crypto ETFs, cryptocurrencies are becoming increasingly common in fiat financial systems. Although cryptos were long considered the preoccupation of geeks, they have now entered the mainstream, with a multitude of people trading daily on large exchanges such as Binance, Bitfinex, and Coinbase.
This soaring popularity has attracted the attention of various scammers and fraudsters, who want to make a fast buck from those who are new to the crypto game and generally rather green. As a result, we have seen new firms emerging to provide OSINT tools for cryptocurrency analysis. With losses amounting to $14 billion, crypto crime hit record highs in 2021, and we believe that blockchain analysis will be among the most valuable applications of OSINT tools moving forward.
The colossal rise of cyber security breaches and hacking activity is impossible to ignore. In 2021 alone, cybercrime cost the world $6 trillion. By 2025, this figure is expected to hit $10.5 trillion. The COVID-19 pandemic triggered a huge rise in internet dependency, with organizations moving to an online format and e-commerce and teleconferencing rocketing in demand.
While an increase in cybercrime was probably anticipated to some degree, the extent of it has a tendency to raise eyebrows – cybercrime is up by 600% compared to pre-pandemic levels. Furthermore, according to a PurpleSec report, only 5% of corporate data is properly secured. With their remarkable efficiency in threat intelligence and cybercrime investigations, OSINT tools will be key in combating this issue, which will be reflected in and a rise in popularity of open-source intelligence.
In organizing our picture of the commercial OSINT landscape, selective decisions had to be made for clarity. These involved separating the global field into areas of application, and grouping what we consider to be the leading technologies for each domain accordingly. Here’s how we’ve broken it down.
Social media is an immense resource of open data. SOCMINT encompasses the techniques and technologies whereby users extract and analyze information on social networking platforms to monitor, and ultimately reacto to, activities that pose threats.
This refers to the analysis of geolocation data, often in combination with AI-powered image recognition, to determine, survey and assess human activity in connection to the geographical and temporal location of subjects and events.
Graphs, or link analysis, are a very intuitive and visual way to interpret data. In fact, the scale of data being used in OSINT would be very difficult to make sense of without such tools. ‘Digital footprints’ are a good example of link analysis graphs, and they enable a wide range of inferences to be made about individuals, companies, and various other entities.
This pertains to the process of inspecting, identifying, clustering, modeling, and visually representing the data on cryptographically distributed ledgers known – or blockchains. The goal of blockchain analysis is to gain valuable information on actors who transact in cryptocurrencies, and determine the legitimacy of their financial operations.
Messenger apps such as WhatsApp and Telegram, are also OSINT sources. This form of intel harnesses accessible data from groups, chats and other forums to gain a picture of human activities.
A broader form of open data extraction, WEBINT leverages digital analytics to examine how visitors view and interact with a website’s pages and features.
A process of collecting, analyzing, and using information on competitors or clients to improve strategic awareness and gain a competitive advantage.
A process a person or company uses to verify that an individual is who they claim to be. This provides the opportunity to check and confirm the validity of someone's criminal record, education, employment history, and other credentials.
Analysis of part of the Deep Web which is inaccessible through ordinary search engines. The Dark Web relies on multiple anonymous proxy servers which can hide the identity and origin of a client or host. Additionally, all traffic and activity is encrypted so that users can remain anonymous and untraceable.
These processes involve the analysis of online data derived from technical systems and surfaces.
A core aspect of cybersecurity, threat intelligence concerns the methods and processes through which an organization can determine its vulnerabilities to cyber threats. The information gathered is crucial for implementing effective counter-breach measures.
Software that enables users to visually organize and analyze vast quantities of data so that information can be cross-checked in building a more reliable and holistic picture of subjects and their environments.
A form of analysis which often relies on machine learning to match or connect different forms of media including images, video, text, and audio, which are scattered throughout the internet.
The processes and techniques used to locate financial assets. Such funds may be legitimate but need to be identified or verified, or they may be illegitimate such as assets derived from fraud, theft, or illegal trading.
Solutions which facilitate and centralize the varied work involved in conducting OSINT investigations, from data extraction and organization, to analysis and report generation.