Profiling in CTI: Turning Open Data into Identity Intelligence


Every cyberattack leaves digital traces. And much of Cyber Threat Intelligence (CTI) work centers around mapping such traces to build a coherent footprint. This allows analysts to reveal those behind an attack as well as how they operate and what they’re trying to achieve. And at the heart of this process is the discipline of profiling—turning scattered indicators of compromise (IoCs) into a clear picture of behavior, infrastructure, and intent.
This article explores how CTI professionals use data to transform anonymous technical signals into insightful profiles of people. We look at how by combining open-source intelligence (OSINT), behavioral analysis, and technical investigation, analysts can identify threat actors, trace their online activities, and understand the social networks that sustain their operations.
In CTI, publicly available data refers to any legally accessible information that can be collected without intrusive methods. Examples include:
Yet these sources don’t just contain technical artifacts—they provide human context. Instead of merely viewing an IP or domain as a standalone entity, the CTI analysts can link it to owners, collaborators, or previous campaigns. Channeled correctly, open data can shape infrastructure into coherent intelligence.
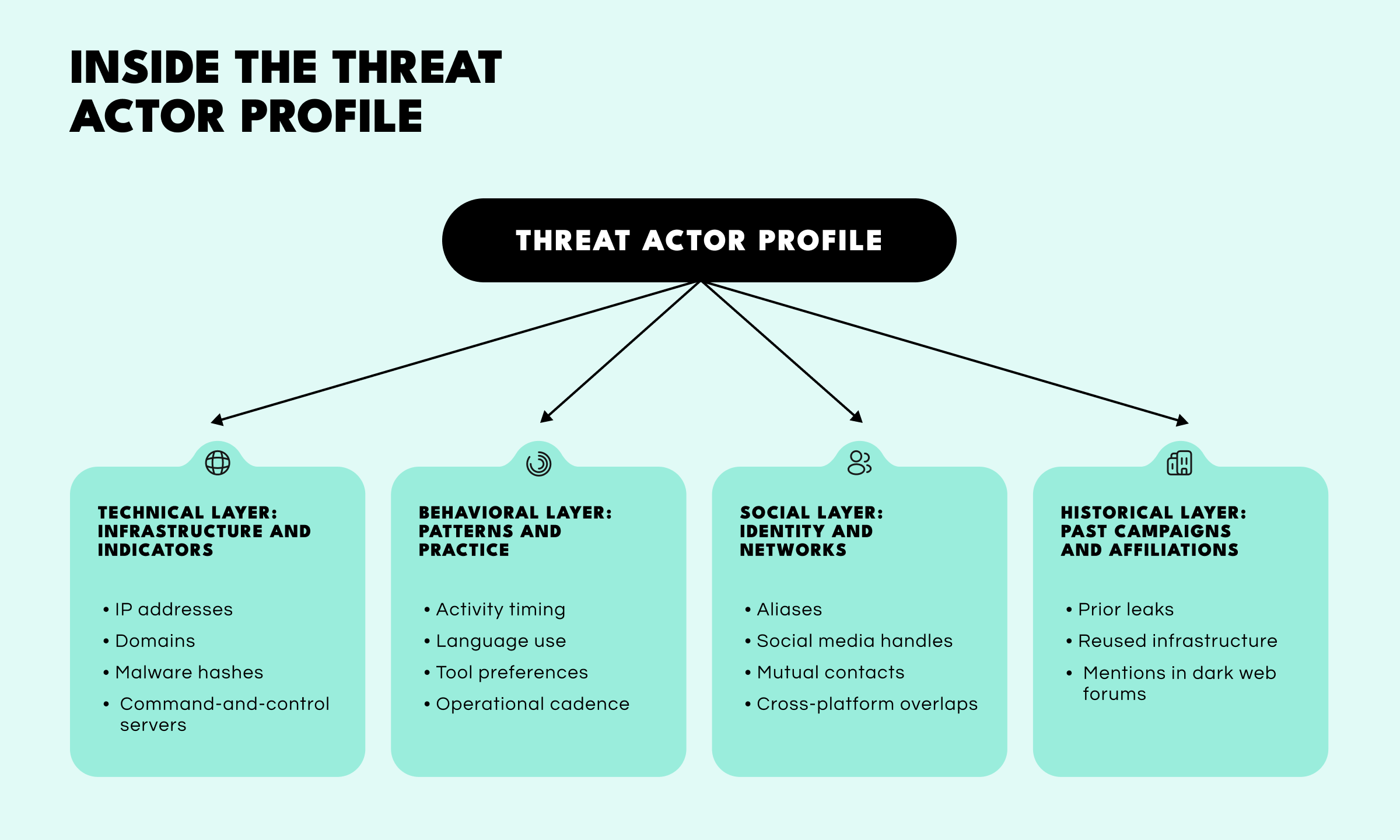
Modern profiling in CTI unfolds across four interconnected layers of analysis:
Technical. Mapping IoCs, TTPs (Tactics, Techniques, and Procedures), and infrastructure such as IPs, domains, and malware.
Behavioral. Studying time zones, communication style, tool usage, and linguistic patterns to identify operational habits.
Social. Connecting aliases, contact details, and relationships to real identities.
Historical. Tracing past campaigns, reused infrastructure, and affiliations to understand an actor’s evolution and long-term objectives.
And these layers build upon the other. The first two explain how an attacker operates, while the social and historical dimensions reveal who they are and how they’ve evolved. By combining technical, behavioral, personal, and historical data, analysts can construct a coherent digital identity that links tactics, motives, and individuals across time and activity.
Social networking platforms remain one of the richest and most dynamic sources of profiling data. They capture human behavior in real time and reveal subtle cues about motivation, trust, and collaboration.
Threat actors often leave behind contact details—Telegram handles, Discord tags, or email addresses—whether intentionally or not. These become pivots for discovering other accounts or operations.
Followers, shared posts, or group memberships can expose communication structures. Social graphs visualize clusters of interaction and pinpoint key organizers or intermediaries.
Attackers frequently reuse usernames, avatars, or PGP keys across platforms. Correlating these identifiers links infrastructure and aliases across Telegram, forums, and repositories.
Community reputation is a strong signal of trust and hierarchy. Posting times, tone, and slang help infer geography, seniority, and cultural alignment within threat ecosystems.
Integrating social and open data into CTI profiling enables analysts to:
However, the method isn’t without risk:
To get reliable results, CTI analysts should:
With the Social Links API, analysts can collect, enrich, and cross-reference open data at scale. By automating link analysis, pattern detection, and entity extraction, the solution enables analysts to gain deep insight into attacker networks while maintaining full transparency and auditability.
Profiling is shifting toward individual-level digital forensics. Going forward, it’s likely that AI-driven link analysis will increasingly identify relationships across accounts and platforms, while expanding public databases will feed richer intelligence graphs.
It’s also extremely probable that social media will remain both a tool and a vulnerability for cybercriminals—a space where they must balance visibility with anonymity. In light of this, analysts who master this balance will gain unprecedented foresight into the structure and behavior of threat ecosystems.
Profiling in CTI is evolving from infrastructure tracking to identity intelligence. By fusing open data, behavioral analysis, and automated enrichment through the Social Links API, analysts can transform IoCs into cohesive stories about who threat actors are and how they operate.
By incorporating OSINT into CTI workflows organizations can not only respond to threats, but anticipate, attribute, and understand them—bridging the gap between technical indicators and human intent.
Profiling in Cyber Threat Intelligence identifies how threat actors operate and who they are, combining technical, behavioral, and open-source data to link infrastructure with individuals.
Publicly available information—from social media, registries, and leaks—provides context that connects technical evidence to people and groups, enriching IoCs with human insight.
The SL API automates data collection and correlation across multiple platforms, helping analysts build comprehensive profiles faster while maintaining investigative accuracy.
Analysts must handle misinformation, disappearing content, and privacy boundaries carefully. Verification across independent sources is essential to avoid false attribution.
AI-enhanced link analysis is accelerating identity resolution and behavioral mapping, enabling CTI professionals to detect patterns and connections in real time.
Want to see how integrated OSINT tools enhance threat actor profiling in CTI? Book a personalized demo with one of our specialists and explore how SL API automates identity correlation, enriches threat data, and combines cross-platform connections in a single environment.